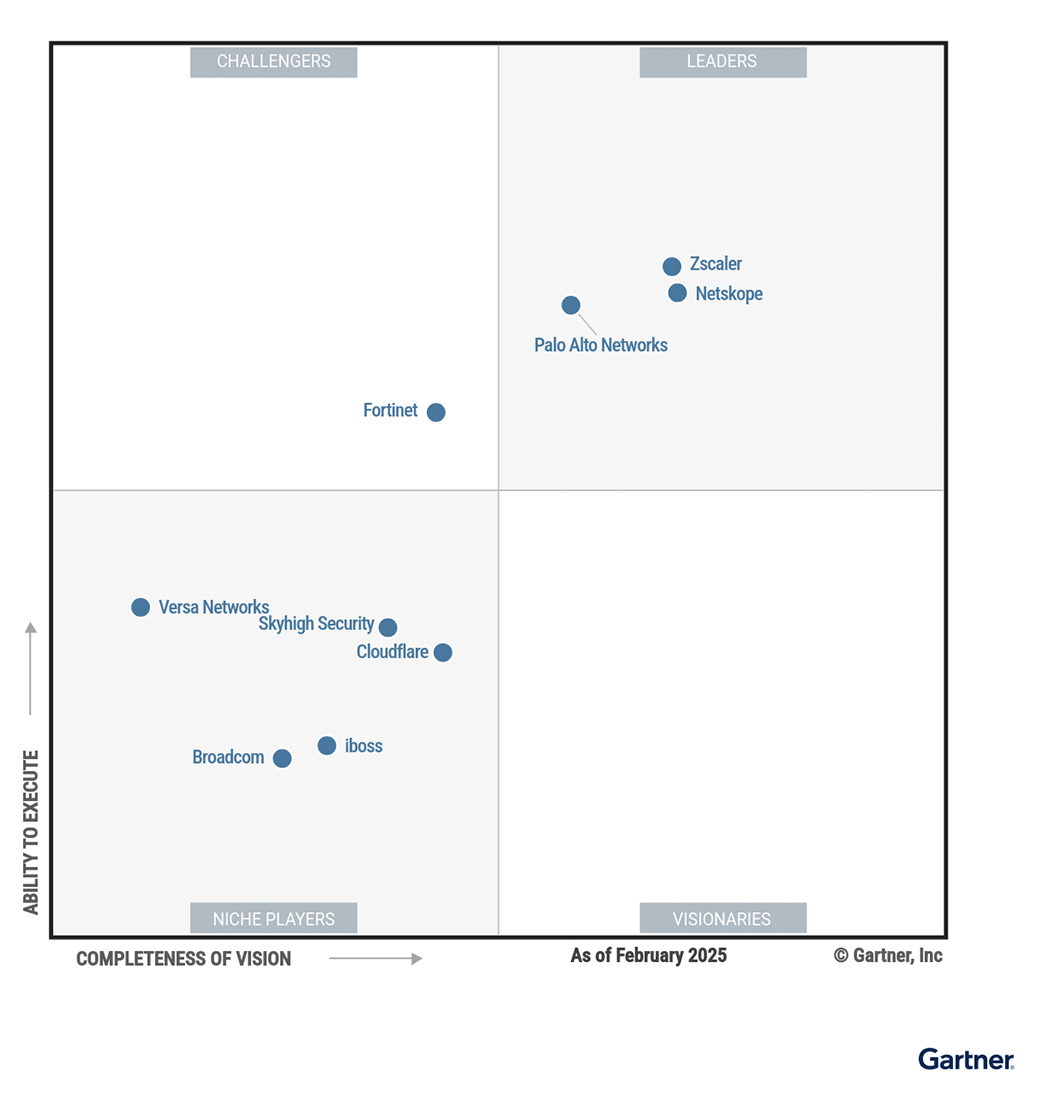
- A segurança deve rastrear dados de várias fontes
- A segurança deve poder decodificar e analisar o tráfego na nuvem
- A segurança deve proporcionar um acesso adaptável aos dados
- A segurança não pode prejudicar o desempenho da rede
A era inicial da segurança cibernética dependia de firewalls, proxies da Web no local, sandboxing, SIEMs e segurança de endpoint, todos não equipados para um espaço dominado pela nuvem. Atualmente, mais e mais dados estão se movendo para fora do perímetro da rede, além do alcance dos firewalls que não estão equipados para ler o tráfego da nuvem de qualquer maneira. Junte isso ao crescente número de endpoints que se conectam a redes corporativas que são BYOD. Na totalidade, você tem uma receita para uma supervisão extremamente não confiável dos dados da empresa.
Por exemplo, o uso seguro de IA generativa, como o popular aplicativo ChatGPT, requer um conector de aplicativo para permitir o treinamento do usuário em tempo real, proteção de dados do que é carregado e controles de atividade do aplicativo.
Se organizarmos de forma útil como a plataforma SSE resolve o que a segurança deve fazer neste novo mundo de manter os dados seguros na nuvem, vários princípios guiam nossa discussão.
Componente nº 1 da SSE: Segurança deve rastrear dados de várias fontes
Agora temos uma quantidade de tráfego que um web proxy ou firewall tradicional não consegue entender e nem mesmo ver. Temos usuários que agora podem estar em qualquer parte, aplicativos que estão em várias nuvens e dados sendo acessados de qualquer lugar. Por isso, é preciso ter um ponto de inspeção de segurança que acompanhe os dados onde quer que estejam. E se esse ponto de inspeção precisar seguir os dados de maneira inegociável, o que significa que ele deve estar na nuvem para que seus benefícios possam alcançar os usuários e os aplicativos.
Componente nº 2 da SSE: Segurança deve poder decodificar e analisar o tráfego na nuvem
Decodificar o tráfego na nuvem significa que a segurança deve ser capaz de ver e interpretar o tráfego API JSON, algo que os web proxies e firewalls não podem fazer.
Componente nº 3 da SSE: Segurança deve fornecer acesso adaptável aos dados
Devemos ir além de simplesmente controlar quem tem acesso às informações e começar a implementar controles de acesso e políticas contínuos e em tempo real que se adaptem regularmente com base em diversos fatores, como os próprios usuários, os dispositivos que usam, os aplicativos que acessam, a atividade, a instância do aplicativo (empresa ou pessoal), a confidencialidade dos dados, os sinais ambientais, como a geolocalização e a hora do dia, e as ameaças presentes. Tudo isso faz parte da compreensão, em tempo real, do contexto com o qual tentam acessar os dados.
Componente nº4 da SSE: A segurança não pode prejudicar o desempenho da rede
O usuário precisa obter seus dados rapidamente, e a rede tem que ser confiável. Se a segurança diminui o acesso ou o funcionamento, a produtividade é prejudicada e as equipes começam a trocar perigosamente os controles de segurança por velocidade e confiabilidade da rede. Pode-se pensar que isso é tão simples quanto mover os controles de segurança para a nuvem. Mas não é bem assim. Em última análise, a nuvem acaba atravessando um lugar muito perigoso, chamado internet, que pode causar uma série de problemas no roteamento e na exposição. É aqui que as redes privadas entram em ação, para que possamos garantir um caminho suave e eficiente do usuário final até seu destino e vice-versa.
Saiba mais: O que é CASB?





 Voltar
Voltar