The widespread adoption of cloud transformation and hybrid work are increasing the attack surface while attacks get increasingly sophisticated. Attacks targeting cloud infrastructure and email-borne threats have soared to unprecedented levels, making it critical for organizations to protect sensitive data regardless of where it may be stored. Traditional security architectures were not designed to protect users, devices, and data outside the corporate network, leaving organizations vulnerable to modern day cyber attacks. In an effort to defend against new and emerging threats organizations have adopted new technologies but these siloed tools have only increased complexity, gaps and risk, adding to the heavy workloads of already over-taxed SecOps teams.
Siloed security tools make it challenging for SecOps teams to correlate information using manual processes resulting in time-consuming threat investigations, alert overload, large numbers of false positives, long attack dwell time, analyst fatigue, and the increased risk of real threats slipping by unnoticed. Enabling SecOps teams to overcome these challenges will reduce operation overhead, and improve team productivity (and morale) while boosting protection from advanced modern day cyber attacks.
Netskope and Mimecast: Advanced coordinated defenses across cloud, web, and email
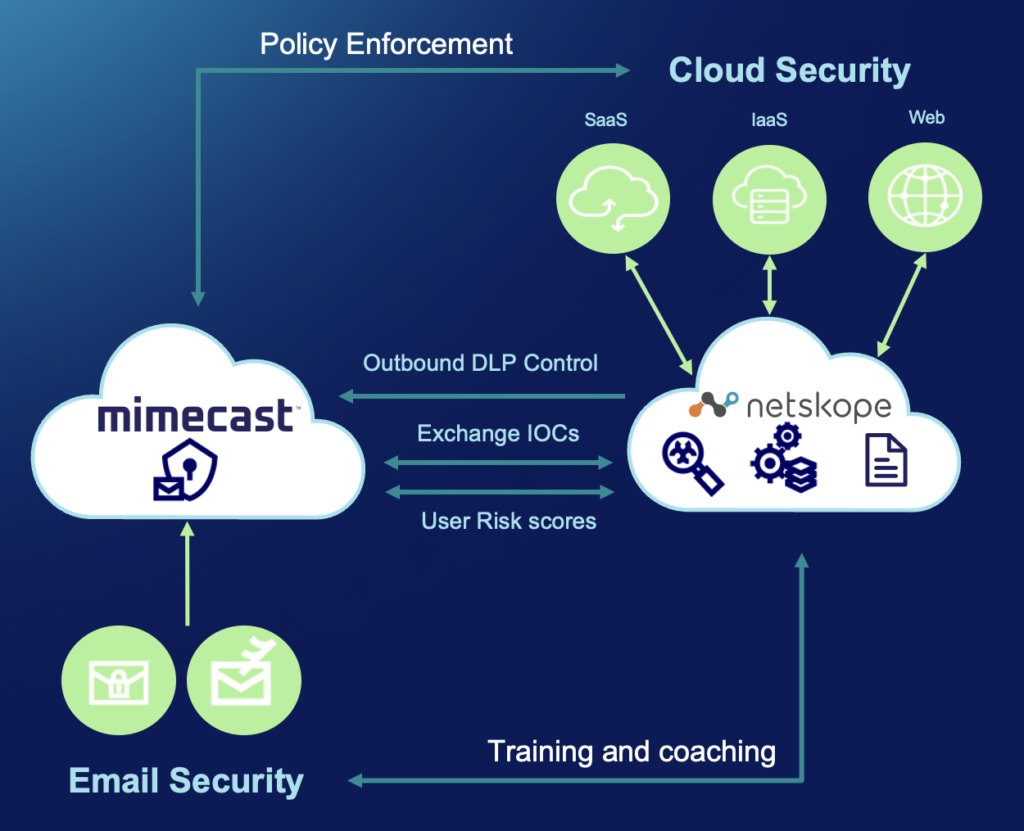
Together, Netskope and Mimecast help organizations protect data and stay one step ahead of attacks targeting modern cloud, web, and email environments with a unified, extended detection and response (XDR) approach. This is done by collecting, and automatically correlating, data across email, cloud, and web, enabling faster detection of threats and accelerating investigation and response times. Organizations get best-in-class cloud, web, and email security with AI-powered detection to defend against advanced email attacks, including phishing, ransomware, business email compromise, and multi-vector attacks enabling enterprises to boost their security posture while increasing operational efficiencies and reducing complexity with automated threat intelligence and risk sharing.
The joint Netskope and Mimecast solution delivers powerful features and benefits to SecOps teams, which include:
Superior threat protection with automated threat sharing across cloud, web, and email
Customers benefit from increased visibility and control across web, cloud, and email with seamless integration and automation, saving time, increasing efficiencies and accelerating threat identification, investigation, and response while eliminating gaps and human errors caused by manual processes. This approach reduces false positives and the risk of real threats slipping by unnoticed. Sharing telemetry, context, and IOCs across web, cloud, and email allows SecOps teams to detect threats earlier in the attack life cycle, reducing dwell time and improving the organization’s security posture.
Comprehensive data protection across all critical channels at cloud-scale
Customers get award-winning and comprehensive data protection across all critical channels at cloud-scale with unified policy across the entire organization. Identify and protect sensitive information across web, cloud, email, and private applications and devices across hybrid and multi-cloud environments with powerful data protection capabilities, including AI/ML for scale, efficacy, and automation critical for app discovery, data detection, and classification for enterprises with business-critical data in the cloud. Netskope AI/ML image classification quickly and accurately detects sensitive content such as passports, government IDs, credit card images, and social security cards without extracting all the text from images. The Netskope and Mimecast joint solution protects your sensitive data from unauthorized access and inadvertent exposure when communicating with business partners via email, using SaaS applications, or accessing websites.
Reduce risk by monitoring and eliminating risky behavior in real time
Customers get an integrated approach to identifying and resolving insider risk using data protection, contextual risk-based access controls, and analytics with continuous adaptive zero trust that analyze the facts of a specific situation and make real-time decisions about the level of access to grant the user based on rich context. This approach takes into account the trust or risk levels of the device, user, location, application, instance, activity, and data to continuously assess and adjust policy at a granular level with a range of actions beyond simply blocking or allowing access. Noteworthy capabilities include coaching and training to help users make better decisions by guiding them towards correct actions and behavior. These features reduce risky activities in real time without having a negative impact on user productivity while simultaneously providing the user with awareness of the issues.
Let’s look at a few key customer use cases where this joint solution plays an important role:
- Defend against advanced email-borne and cloud threats: This best of breed solution helps customers defend against advanced threats such as phishing, ransomware, and multi-vector attacks. It boosts threat detection, accelerates response time, and improves sensitive data protection across email, cloud, and web services.
- Improve SOC efficiency and reduce attack dwell time: Customers benefit from leveraging seamless integration and automation across multiple security tools to improve SecOps team productivity (and morale) by reducing alerts, accelerating investigation and response, reducing attack dwell time, and stopping threats from slipping by unnoticed.
- Prevent insider risk: Customers get increased protection from insider risk and data exfiltration/leaks by identifying at-risk users, activities, and devices and establishing granular controls to reduce risk in real time, without affecting user productivity. Users receive coaching and training to guide them to safe behavior.
- Share threat intelligence: Customers gain actionable insights to understand how their organization has been targeted, and what attacks have been blocked for better protection at the email perimeter and cloud services.
- Prevent data exfiltration: Customers can use a single policy engine to prevent the exfiltration of sensitive data through cloud, web, or email from their environment, including between business and personal email instances.
- Establish consistent enterprise-wide data protection policies: Customers can create and enforce consistent data protection policies across SaaS, IaaS, web, and email.
The Netskope and Mimecast joint solution protects data by addressing modern cloud, web, and email security challenges without degrading performance. It reduces operational complexity and risk while improving security posture with adaptive zero trust principles and delivers comprehensive data protection across email, cloud, and web services. With this integrated solution customers get best-in-class cloud, web, and email security with AI-powered detection to defend against advanced email attacks, including phishing, ransomware, and business email compromise.
Join us at Mimecast SecOps Virtual 2023 to learn more about:
- Best practices for orchestrating threat protection, detection and response
- Increasing return on existing security investments
- Building and retaining high performing teams




 Voltar
Voltar 















 Leia o Blog
Leia o Blog