I originally planned to focus this blog post on the dark web. Many of you reading this blog may know that the dark web is a well-known part of the internet where many sites are not indexed by search engines and can only be accessed if you know the site address, making them effectively hidden. Accessing the dark web requires special software, like browsers configured with Tor. Once inside the dark web, “dark net” markets exist that sell sensitive data stolen in breaches (in addition to illegal products like drugs and firearms). The dark web’s currency of choice is the cryptocurrency Bitcoin.
I thought it would be interesting to do some research and take a tour of the dark web, providing my perspective on what activities take place and how easy it is to buy and sell sensitive data. The dark web presents a Déjà vu experience for me personally. You see, as young teenager, I was one of the many pioneers of the early dial-up BBS age in the 80s.
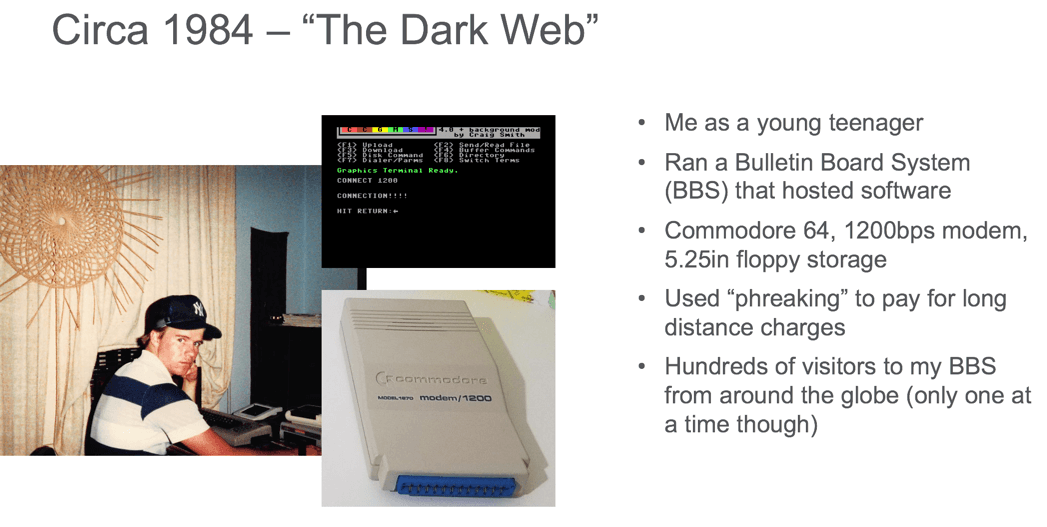
I hosted a “warez” site in my bedroom and had hundreds of visitors to my site from around the world, although only one at a time could visit in those early days. My system was a Commodore 64 computer, a 1541 disk drive, and a 300 baud modem, which I later upgraded to a 1200 baud modem. I used “phreaking” techniques to cover long distance phone charges. You could argue that what I was doing in the 80s was a form of today’s dark web although instead of drugs, firearms, etc., I was simply sharing software.
Fast forward to present day and I was eager to try out the dark web. To kick things off, I installed a VPN, configured my browser with Tor, and proceeded to spend several hours perusing a bunch of .onion sites. As part of the process, I went back and forth between the dark web and the real world, Googling in the real world to find some of the more popular dark websites. That is when it hit me. While the dark web can be scary with a variety of places where you can get access sensitive data if you look hard enough, there is a place arguably more dangerous and much more significant in scale. Thousands of public-facing sites where sensitive data can be easily uploaded and shared either with malicious intent or accidentally by unsuspecting perpetrators. This place is the opposite of the dark web because it is not hidden, but actually right in front of us in plain sight. Welcome to the “bright web.”
Researching the bright web – meet our victim Frank Altos
To help articulate what the bright web is, I enlisted the Netskope Threat Research Labs team and turned the research away from the dark web and instead focused on places on the public internet where you can easily upload and share sensitive data-in many cases anonymously without requiring you to create an account tied to a credit card. For some of you, these findings may be shocking. Many of you already know that some of these sites existed, but perhaps may not have realized how widespread and ridiculously easy it is to do some significant damage.
As part of the research, we wanted to paint a real-world scenario that involves sharing sensitive data. To support this, we created a piece of data that represents the type of data that stolen during the recent Equifax data breach. We created a fictitious customer record with personal information that includes name, address, phone number, email, and social security number. I also added a couple of credit card numbers, which we thought would be appropriate given how often these are sold on the dark web. Last, but certainly not least, we included the mother’s maiden name tied to this user, which is another piece of information that can be valuable to hackers. We packaged this sensitive data in three different formats; a PDF, a JPEG, and .pptx, which will allow us to expand our reach as we used the bright web to upload and share this data.

Places to upload and share Frank’s personal info
Now that we had our sensitive data, we started the process of looking for places on the internet that make it easy to share this information. As a base, we have the benefit of having more than 24,000 cloud services that are researched by the Netskope Threat Research Labs team. The Netskope research team also organizes these cloud services into categories. For this particular research, we focused on categories where it is common to facilitate sharing. This includes cloud storage, collaboration, and personal cloud apps. We took the most popular cloud services within these categories as measured by the number of user sessions across Netskope cloud tenants.
Next, we wanted to focus on cloud services that you can easily sign up for and share data without the service requiring a credit card. If a credit card is needed, this presents enough friction that anonymously sharing becomes harder. For those cloud services that don’t require a credit card, we wanted to identify the ones that you can upload and share data publicly and that data could be indexed by search engines. This the riskiest scenario given the fact that sensitive data can easily be uploaded and shared publicly. A recent example of this was when Microsoft Docs.com was shut down temporarily after complaints that data was being shared publicly by default.
We also wanted to identify cloud services that simply make it easy to upload and share sensitive data via a shared link.
In this case, the shared link is not indexed by search engines so you would have to share the link with specific people or groups or place the shared link on a website so search engines will index it. Nonetheless, the fact that you can easily upload and share data without signing up with a credit card makes it very easy to leak sensitive data.
Research findings
We researched a sample size that included 1,000 of the top cloud services in the cloud storage and collaboration categories in addition to a handful of slide sharing cloud services in the personal cloud app category. We then extrapolated the numbers based on the total number of cloud services. Here are the results:
1,200+ cloud services make it easy to share sensitive data
More than 10% (1,240) of cloud services allow you to easily sign up without a credit card, upload data, and share data. Here are links we created using a handful of these cloud services to share Frank’s personal data:
Dropbox: https://www.dropbox.com/s/lurd51qeg25feiq/Customer%20Record.pdf?dl=0
OneDrive: https://1drv.ms/b/s!AiOdtHvp9jERaX5mFYba9HF4wDw
Box: https://app.box.com/s/skyfz7wuvqig4mr27xa28xuic7cqjiqw
Citrix Share File: https://280consulting.sharefile.com/d-s5f29f174b5f4bacb
Wetransfer: https://we.tl/FEhl9Y7Nf2
Mediafire: http://www.mediafire.com/file/6l5eye4izthgf4p/Customer_Record.pdf
Hundreds of cloud services make it easy to share data publicly
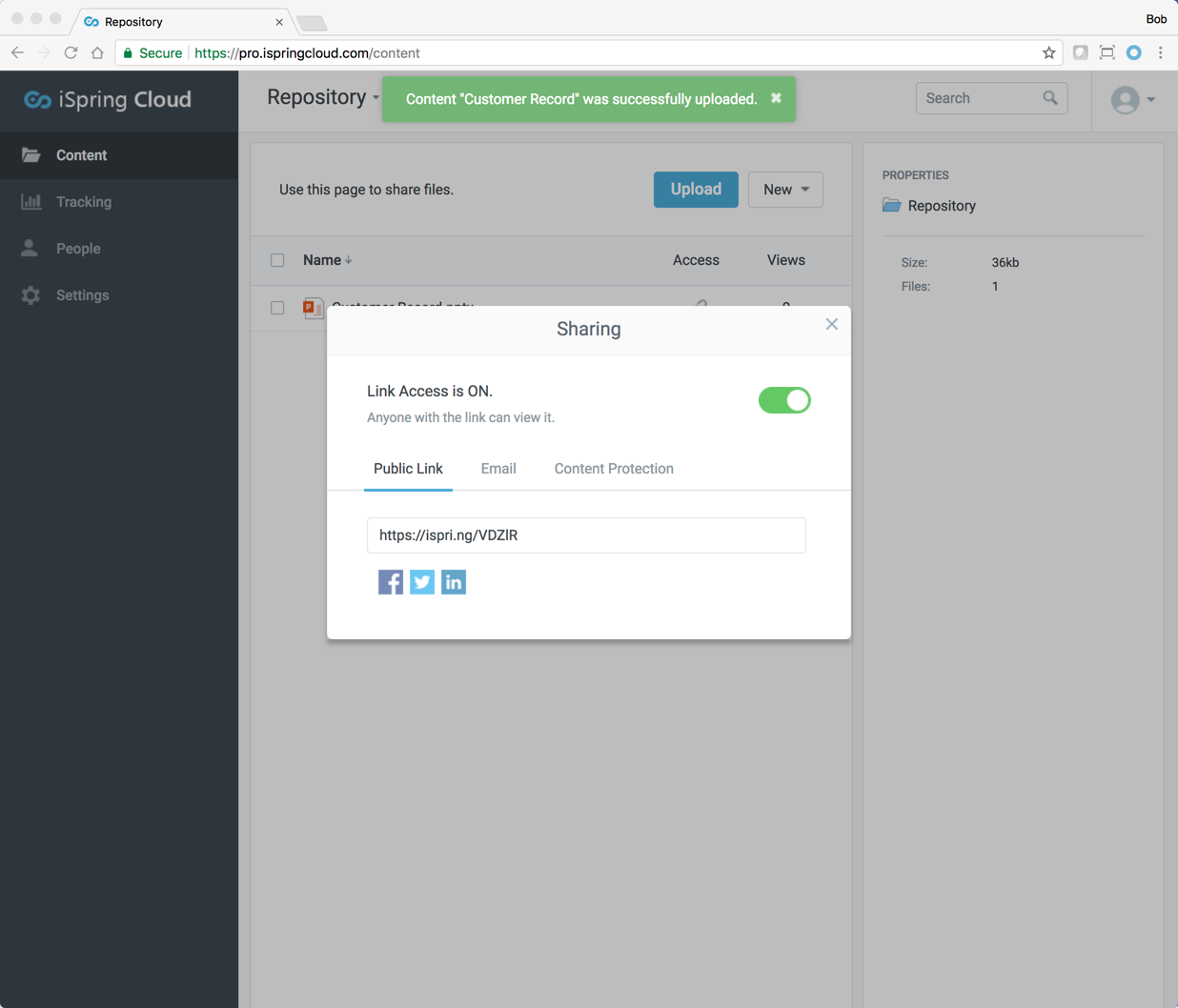
Hundreds of cloud storage and slide sharing services allow you to upload and share data publicly. This may be fine for data meant to be public, but sensitive data such as business plans, customer data, and anything confidential could easily get in the wrong hands. Google Drive is the only mainstream cloud storage service that enables users to bypass cloud storage security control by supporting the ability to share data publicly and have it indexed by search engines. Other cloud services such as OpenDrive and Jottacloud also enable public sharing. Below is a look at Google’s public sharing capability and a public link to Frank’s personal data.
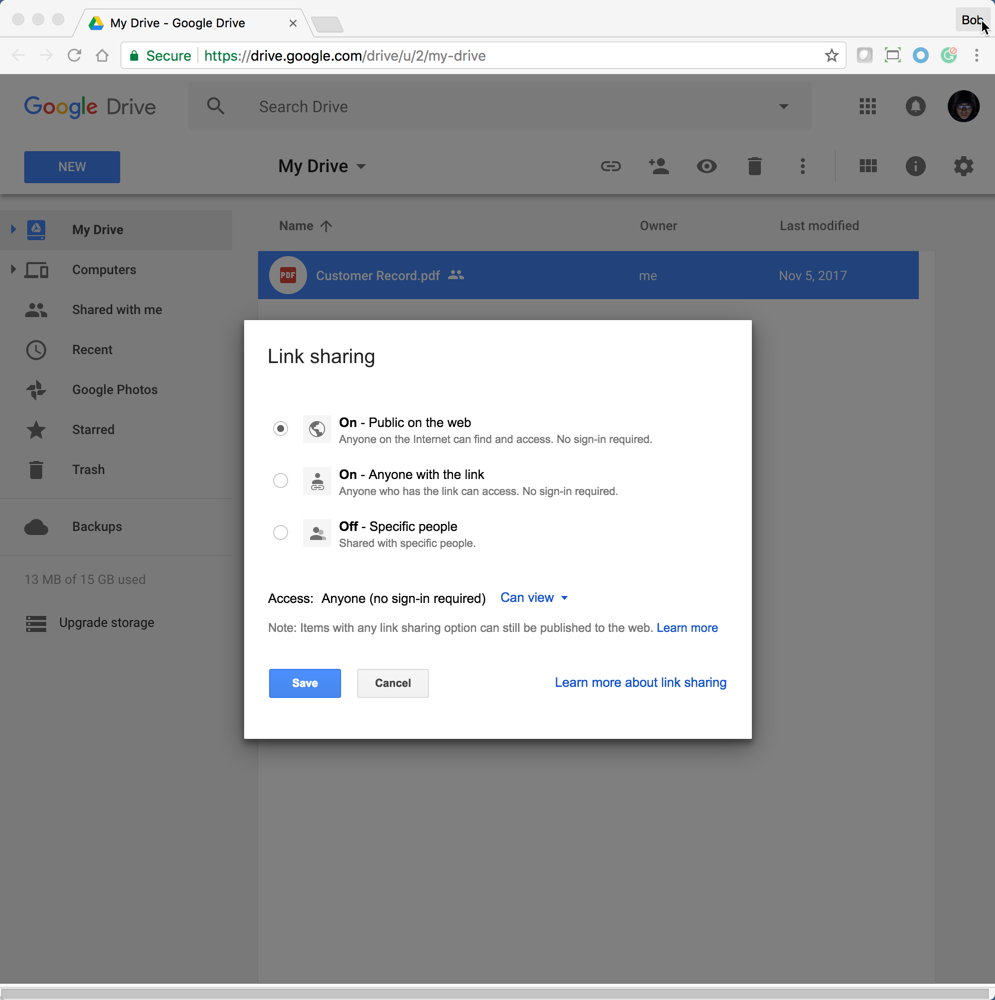
Frank’s personal data in Google can be discovered by simply searching for “Customer Record site:drive.google.com”. This tells Google to search for any mention of the search terms Customer Record in drive.google.com. Searching public-facing data that resides in Google Drive accounts is as easy as entering the following in Google: <search terms> site:drive.google.com. It turns out that there are more than 434,000 public-facing files in Google Drive accounts and more than a third appear to be sensitive by nature.
I used this technique and found a number of sensitive data in some interesting locations. For example, a city in Massachusetts hosts a large amount of public-facing data in Google Drive from the city’s police department to the Town Clerk. Google Drive is their central repository with links to the data surfaced via various websites. While most, if not all, of this data is expected to be publicly available, it was not clear if the city intended to make the central repository of Google Drive available to the public.
Sensitive data is being shared publicly via slide sharing cloud services
Slide sharing services are a popular way to upload and share your presentation. These services also make it easy to share publicly and it is unbelievable the type of data you can find simply by performing a Google search. For example, if you search for “Prezi” and “QBR” you will find all public-facing QBR (quarterly business review) presentations posted on slide sharing service Prezi. This includes sensitive data such as revenue numbers, customer names, and business plans. This data is obviously not intended to be shared publicly. Here is a small sample of some of the presentations discovered with that simple search:
Q3 QBR presentation by Blake https://prezi.com/2lhek3nn6jt3/q3-qbr-presentation/
QBR presentation by Daniel https://prezi.com/g3fvjr7ipkxi/qbr-presentation/
QBR presentation by Jen https://prezi.com/ogwrzh8x5qvm/qbr/
QBR presentation by Jack https://prezi.com/jqodmmbtl04w/jack-holroyd-qbr/
QBR by Amit https://prezi.com/mgovxx61ojt0/qbr/
Here are some of additional slide sharing services along with public shares of Frank’s personal data. It is amazing how easy it is to sign up for these cloud services using a fictitious account and easily upload sensitive content, and share publicly.
Slideshare https://www.slideshare.net/FrankAltos/customer-record-81633005
Beamium https://www.beamium.com/YRBDHCFF
Slidesnack http://snack.to/b7n0o88j?UA_PHPSESSID=tsi684kd61i5iaoklpl427abc1
Slides http://slides.com/frankaltos/deck
Summary
While the bright web is a scary place, it also has a good side. On average an enterprise has more than 1,000 cloud services in use and more than 95% of those are business-led with the remaining 5% being IT-led. Lines of business rely on these cloud services to move fast, innovate, and be more productive. A sound cloud security strategy should be comprehensive and include a focus on securing the IT-led cloud services like Office 365 in addition to safely enabling the bright web with granular access control and Cloud DLP that can be applied to bright web traffic. Given the previous example, your Google Drive security best practices should include a focus on making sure sensitive data is not shared publicly.
You can learn more about the bright web by joining our upcoming webinar https://go.netskope.com/lp-webinar-can-you-see-the-bright-web.html where we will be sharing our research findings, providing a live demonstration, and walking through how Netskope can help your users safely maneuver the bright web.




 Voltar
Voltar 















 Leia o Blog
Leia o Blog