Summary
Throughout 2022, Netskope Threat Labs found that attackers have been creating phishing pages in Google Sites and Microsoft Azure Web App to steal cryptocurrency wallets and accounts from Coinbase, MetaMask, Kraken, and Gemini.
These phishing pages are linked from the comment sections of other websites, where the attacker adds multiple links to the phishing pages, likely to boost SEO and drive victims directly to these pages. The main goal of this campaign is to steal cryptocurrency exchange accounts or recovery phrases, which allows the attacker to import existing crypto wallets.
In this blog post, we will analyze these phishing pages to demonstrate how they work.
How is it spread?
We found that most of these phishing pages are linked from the comment sections of other websites, mostly blogs. The attacker adds links to one or more phishing websites, where the URL contains elements to boost SEO.
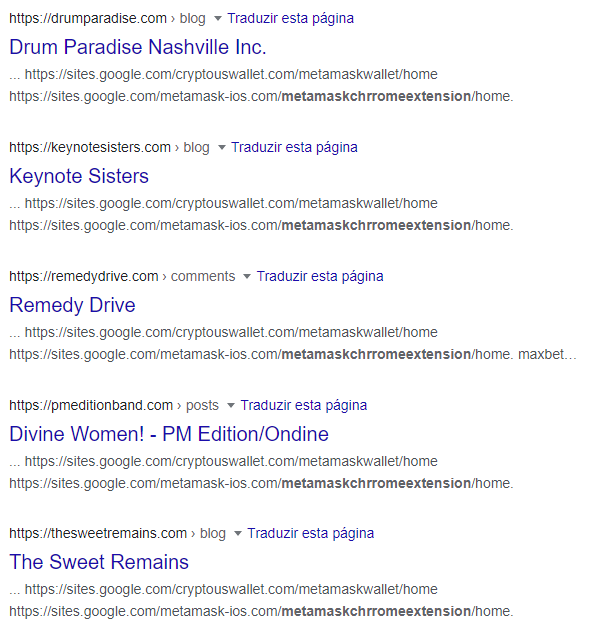
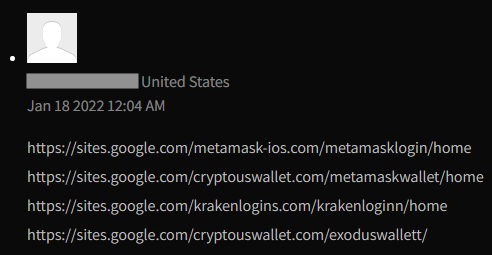
These comments are posted by random accounts, and sometimes there are multiple links leading to different phishing pages.
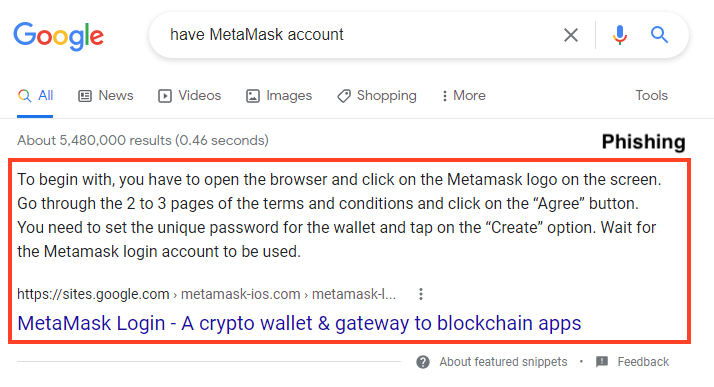
Furthermore, the attackers are using these SEO techniques to make the phishing pages appear as the first result on search engines, like Google.
How does it work?
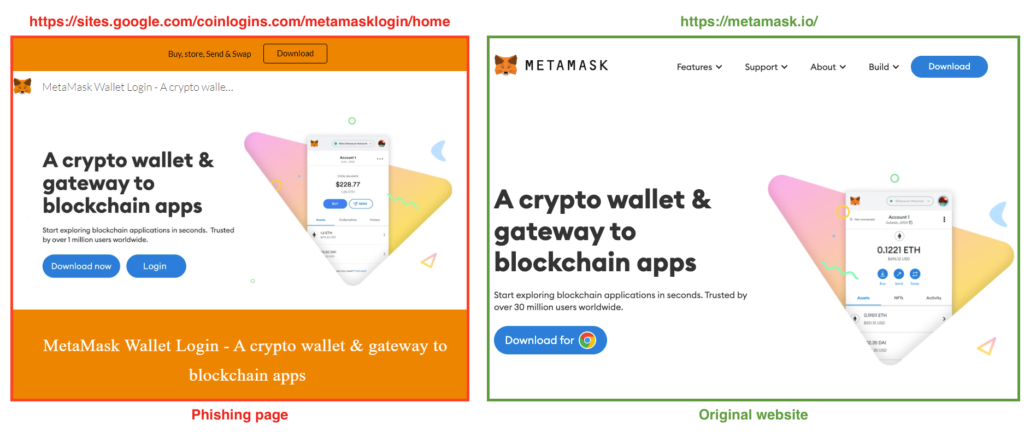
The main page is hosted with Google Sites and mimics the cryptocurrency website that it’s targeting. In the example below, we will demonstrate how the MetaMask phishing works. The landing page is very similar to the real MetaMask website.
The phishing page also contains a fake FAQ, as an additional measure to convince victims that the page is real and to improve SEO.
Once the victim clicks “Download now” or “Login”, the user is redirected to another page hosted with Azure Web Apps.
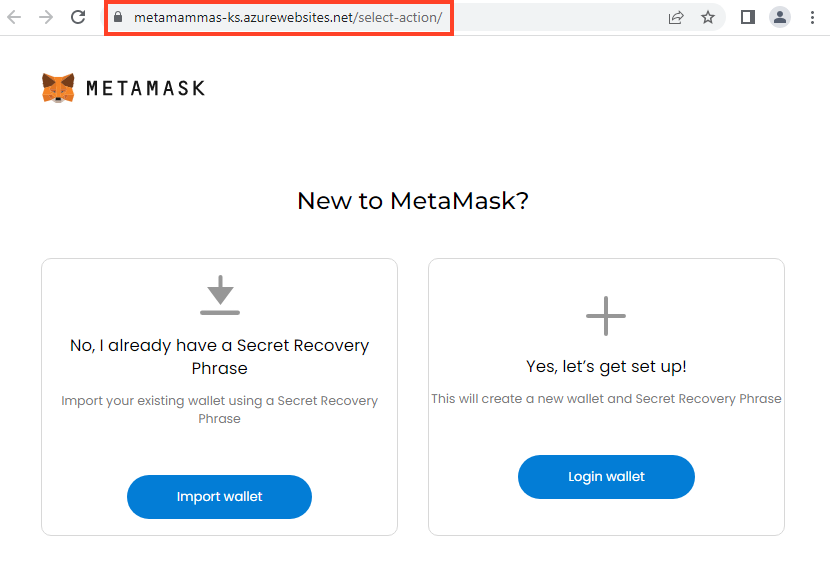
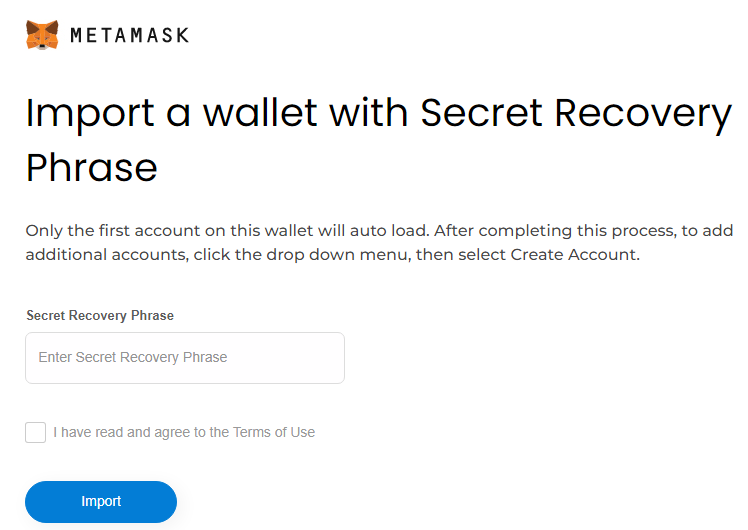
For the MetaMask phishing, there are two options. The first one is through the “Import wallet” button, which tries to steal the secret recovery phrase that can be used to steal existing wallets.
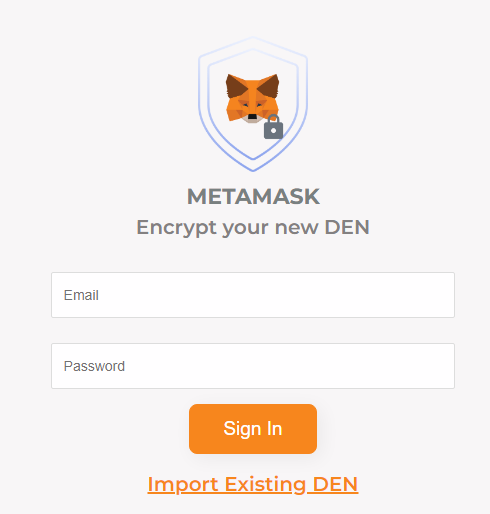
And the second tries to steal the username and password.
More targets
We also found online phishing campaigns targeting Coinbase, MetaMask, Kraken, and Gemini. All using the same attack flow, by hosting the main page with Google Sites and the second stage with Azure Web App.
Coinbase
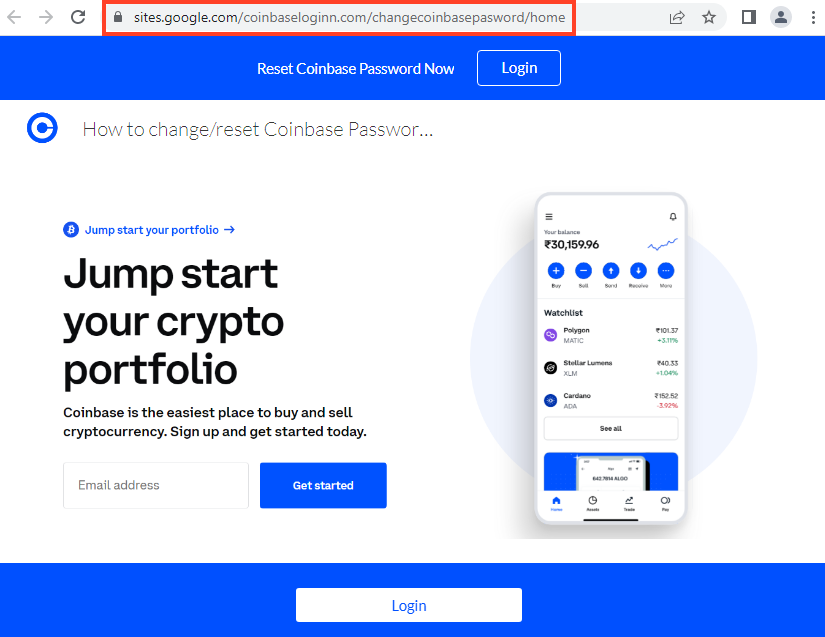
Gemini Wallet
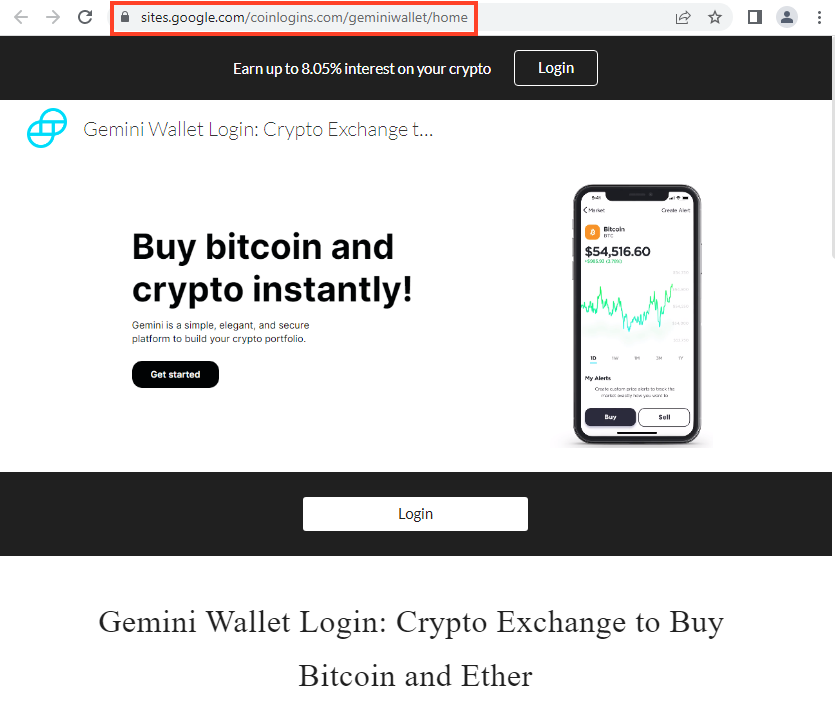
Kraken Wallet
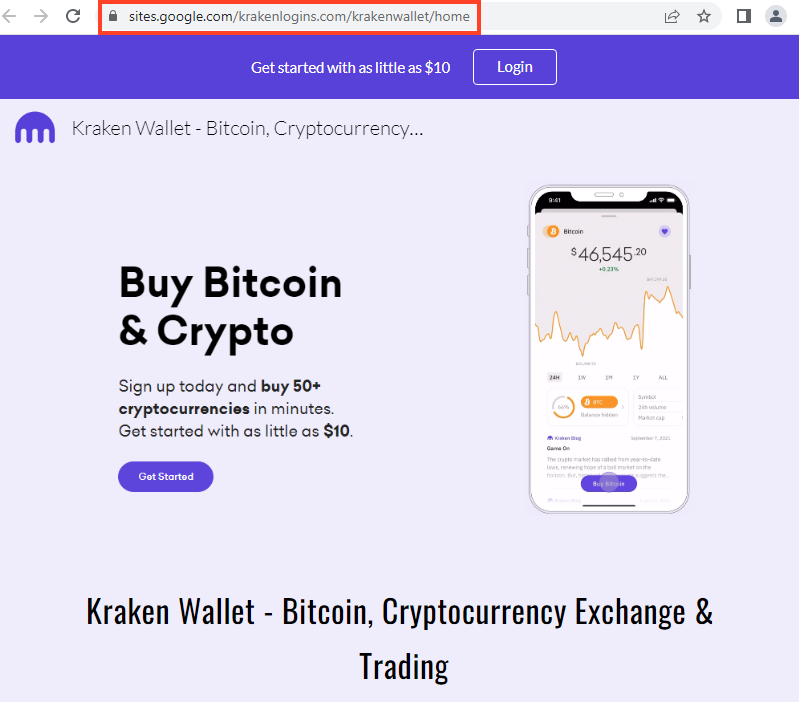
What’s the difference between them?
The difference between these attacks is that the MetaMask phishing also tries to steal the MetaMask security recovery phrase. All of the other phishing pages only try to steal the account credentials. For example, below we have the flow for the Gemini phishing.
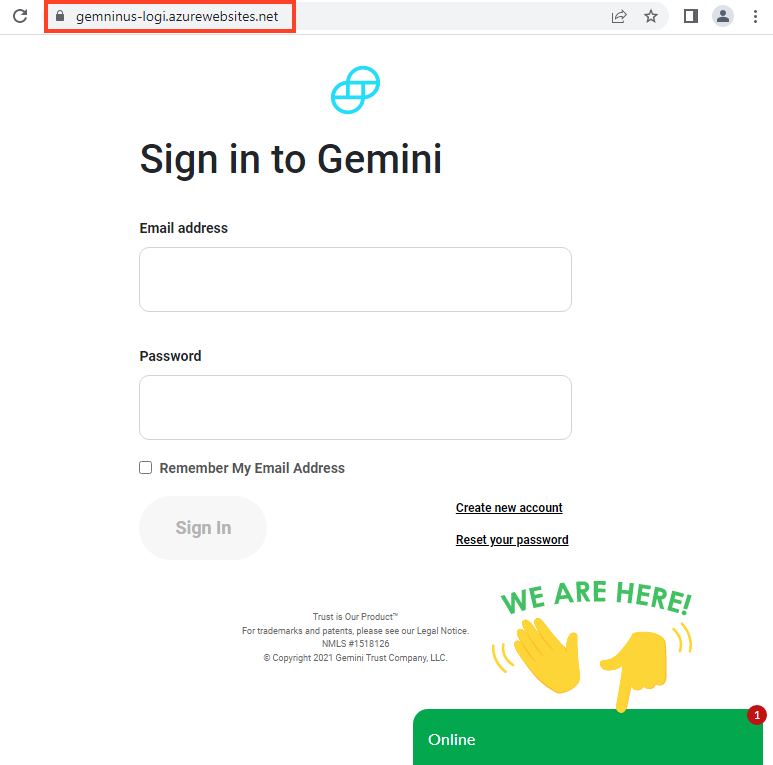
After inserting the username and password, the victim is redirected to a fake MFA page, which asks for a phone number.
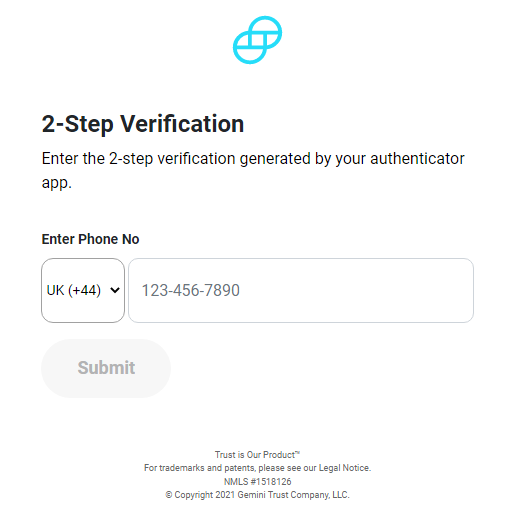
After inserting this information, the victim is redirected to a fake error page.
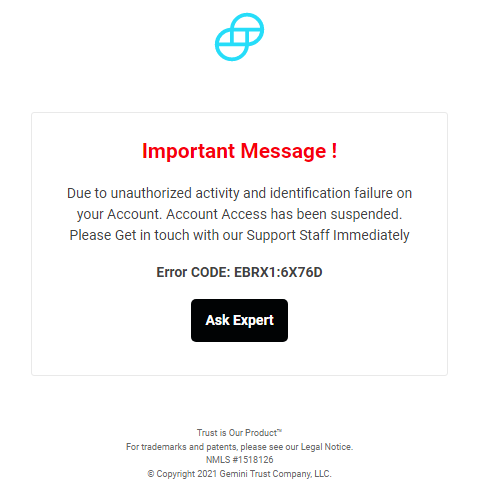
The “Ask Expert” button triggers an online chat with the attacker, which requires more information from the victim.
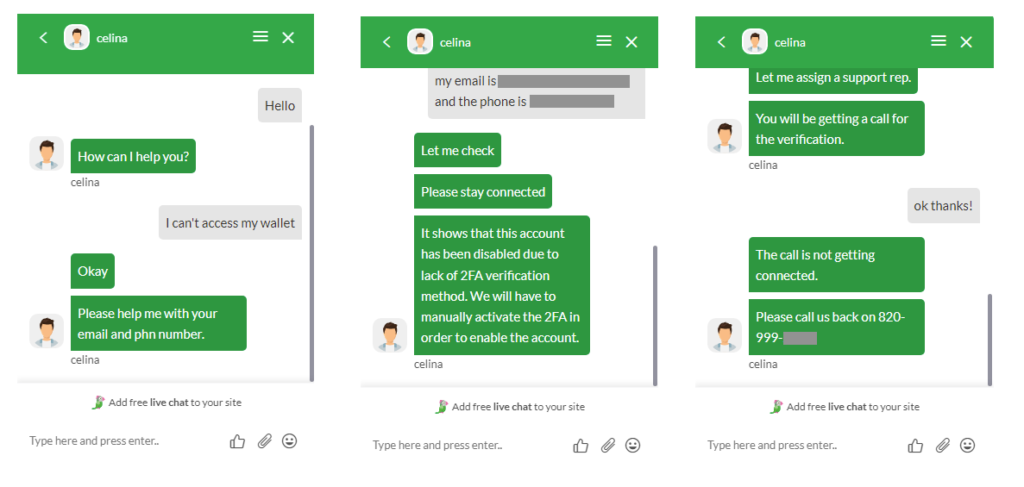
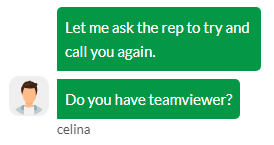
If the attacker can’t reach the victim by phone, then they ask if they can access the victim’s machine via TeamViewer.
Conclusions
Attackers are constantly trying to steal cryptocurrency wallets and accounts with elaborate phishing pages, mimicking the real websites, avoiding typos to make the page look real, and even interacting with victims through a live web chat.
In this campaign, we found that the attackers are abusing Google Sites and Azure Web App to host the pages, likely due to cost, ease-of-use, and to slightly increase the victim’s trust. Also, attackers are using SEO techniques to increase the reach of the phishing sites, making it appear in the first result when the victim searches for the real website.
Netskope strongly recommends users to never enter credentials after clicking on a link. Instead, always navigate directly to the site you are trying to log in to. For organizations, we also recommend using a secure web gateway, capable of detecting and blocking phishing in real time.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators. Netskope Next Gen SWG inspects all HTTP and HTTPS traffic, using a combination of threat intelligence, signatures, heuristics, and machine learning to identify and block phishing pages in real time.
IOCs
First stage URLs
hxxps://sites.google[.]com/coinbaseloginn.com/changecoinbasepasword/home
hxxps://sites.google[.]com/coinbaseloginn.com/coinbasenotworking/home
hxxps://sites.google[.]com/coinlogins.com/geminiwallet/home
hxxps://sites.google[.]com/coinlogins.com/metamasklogin/home
hxxps://sites.google[.]com/cryptouswallet.com/coinbasewallet
hxxps://sites.google[.]com/cryptouswallet.com/metamaskwallet/home
hxxps://sites.google[.]com/krakenlogins.com/krakenwallet/home
hxxps://sites.google[.]com/metamask-ios.com/metamask-log-in/home
hxxps://sites.google[.]com/metamask-ios.com/metamask-loginn/home
hxxps://sites.google[.]com/metamask-ios.com/metamask-wallet/home
hxxps://sites.google[.]com/metamask-ios.com/metamaskchrromeextension/home
hxxps://sites.google[.]com/metamask-ios.com/metamasklogin/home
hxxps://web.sites.google[.]com/coinbaseloginn.com/changecoinbasepasword/home
hxxps://web.sites.google[.]com/coinbaseloginn.com/coinbasenotworking/home
hxxps://web.sites.google[.]com/coinlogins.com/geminiwallet/home
hxxps://web.sites.google[.]com/coinlogins.com/metamasklogin/home
hxxps://web.sites.google[.]com/cryptouswallet.com/coinbasewallet
hxxps://web.sites.google[.]com/cryptouswallet.com/metamaskwallet/home
hxxps://web.sites.google[.]com/krakenlogins.com/krakenwallet/home
hxxps://web.sites.google[.]com/metamask-ios.com/metamask-log-in/home
hxxps://web.sites.google[.]com/metamask-ios.com/metamask-loginn/home
hxxps://web.sites.google[.]com/metamask-ios.com/metamask-wallet/home
hxxps://web.sites.google[.]com/metamask-ios.com/metamaskchrromeextension/home
hxxps://web.sites.google[.]com/metamask-ios.com/metamasklogin/home
Second stage URLs
hxxps://coinbcaselogin.azurewebsites[.]net/coin-baselogin/
hxxps://gemninus-logi.azurewebsites[.]net/
hxxps://gemninus-logi.azurewebsites[.]net/error.html
hxxps://gemninus-logi.azurewebsites[.]net/vendor/Sender.php
hxxps://gemninus-logi.azurewebsites[.]net/verify.php
hxxps://kraakesn-log.azurewebsites[.]net/
hxxps://kraakesn-log.azurewebsites[.]net/error.html
hxxps://kraakesn-log.azurewebsites[.]net/vendor/Sender.php
hxxps://kraakesn-log.azurewebsites[.]net/verify.php
hxxps://metamammas-ks.azurewebsites[.]net/
hxxps://metamammas-ks.azurewebsites[.]net/import-with-seed-phrase/
hxxps://metamammas-ks.azurewebsites[.]net/metnna-login/
hxxps://metamammas-ks.azurewebsites[.]net/select-action/
hxxps://metattamsamsk.azurewebsites[.]net/import-with-seed-phrase/
hxxps://metattamsamsk.azurewebsites[.]net/m-error/
hxxps://metattamsamsk.azurewebsites[.]net/m-verify/
hxxps://metattamsamsk.azurewebsites[.]net/metnna-login/
hxxps://metattamsamsk.azurewebsites[.]net/select-action/




 Atrás
Atrás
















 Lea el blog
Lea el blog