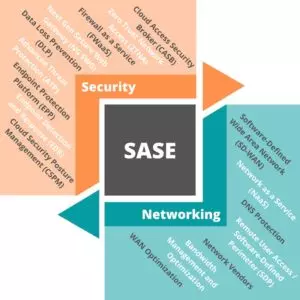
Secure Access Service Edge (SASE) est une architecture basée sur le cloud qui fournit des services de réseau et de sécurité destinés à protéger les utilisateurs, les applications et les données.
Ce terme a été inventé par Gartner en 2019 et a rapidement gravi les échelons pour devenir l’un des concepts de sécurité les plus ambitieux de la décennie actuelle jusqu’à présent. Étant donné que de nombreux utilisateurs et applications ne vivent plus et ne fonctionnent plus sur un réseau d’entreprise, les mesures d’accès et de sécurité ne peuvent pas dépendre des appliances matérielles conventionnelles dans le centre de données de l’entreprise.
SASE security promet de fournir les capacités de réseau et de sécurité nécessaires sous la forme de services fournis en nuage. Correctement mis en œuvre, un modèle SASE élimine les appareils basés sur le périmètre et les solutions existantes. Au lieu d'acheminer le trafic vers un dispositif de sécurité, les utilisateurs se connectent au service en nuage de SASE pour accéder et utiliser en toute sécurité les services web, les applications et les données, avec une application cohérente de la politique de sécurité.
Quel est l'avantage du Secure Access Service Edge ?
Le terme « edge » (ou « périphérie ») dans SASE fait référence aux systèmes globaux du fournisseur de services cloud qui existent sur son matériel (datacenters et appareils). Les utilisateurs accèdent aux services cloud en se connectant et en authentifiant leur identité, quel que soit l'endroit où ils se trouvent, et passent par cet « edge » pour accéder à l'environnement cloud.

Livre blanc : Le SASE et les sept forces qui façonnent la transformation de la sécurité
Blog : Le point de vue d'un RSSI sur les SASE




 Retour
Retour



















 Lire le blog
Lire le blog
