Netskope Threat Research Labs has discovered a new malware campaign, which we suspect stole more than 26,000 email credentials and also monitors online banking activities. The malware, which we have named “CloudFanta,” has been in operation since July 2016 and primarily targets Brazilian users.
This blog provides a preliminary overview of CloudFanta while we wait on the command and control hosts and cloud vendor to take down the malware and servers containing the email credentials.
Similar to the CloudSquirrel malware campaign that we uncovered in July 2016, CloudFanta arrives as an attachment or a link in a spearphishing email that lures the victim to execute the file or click the link. We observed the CloudFanta malware using the SugarSync cloud storage app for delivering a JAR file that functions as a downloader. The downloader JAR file again uses SugarSync for downloading Dynamic Linked Library (DLL) files with a “.png” extension. These DLL files, which are later renamed to the extension “.twerk,” are responsible for stealing the victim’s email credentials, sending malicious emails on behalf of the victim, and also for monitoring victims’ online banking activities.
Summary Observations
A high-level visual depiction of the CloudFanta malware infection is shown in Figure 1. The CloudFanta malware campaign highlighted the use of the cloud storage app, SugarSync for hosting drive-by-download files. Using tactics like the delivery of DLL files with the “.png” extension and the use of SSL/HTTPS communication with SugarSync allow CloudFanta to stay under the radar of a number of traditional, network-based security solutions. This clearly demonstrates the effective use of cloud services for hosting malware by malicious threat actors. The use of cloud services makes the delivery of malware very easy, effectively making it easier to compromise and gain access to users’ data. This clearly signifies an urgent need for enterprises to employ a multi-layered security approach with a strong focus on cloud services.
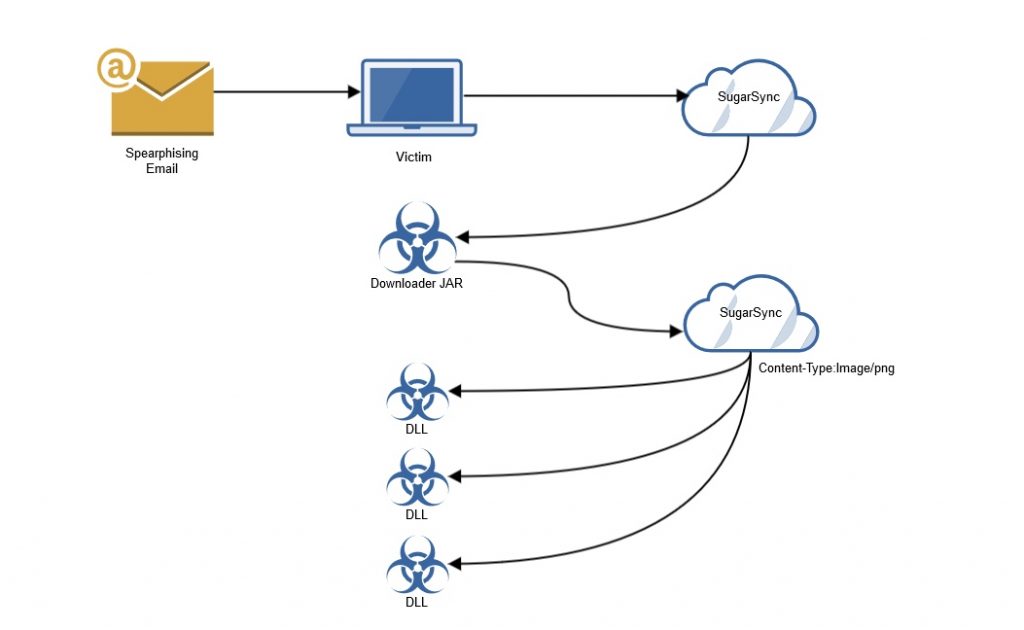
Figure 1: Visual depiction of CloudFanta malware infection
Netskope Detection and Remediation
The visual depiction of protection from CloudFanta malware with Netskope Threat Protection is shown in Figure 3. Netskope Threat Protection detects the files retrieved from the JAR downloader as Backdoor.Generckd.3549404, Backdoor.Generckd.3540808, Backdoor.Generckd.18673650, Backdoor.Generckd.3542220 and Gen:Variant.Symm.60013. Customers with the Netskope Active Platform and Netskope Introspection can set the respective malware and threat protection policies to detect and remediate against this malware. In addition to the above, Netskope Active platform customers can also block the DLL files with “.png” extension from being downloaded using a custom rule as shown in Figure 2.

Figure 2: Block policy alert for portable executable files with “.png” extensions

Figure 3: Visual depiction of protection from CloudFanta malware with Netskope Threat Protection
General Recommendations
Netskope recommends the following to combat cloud malware and threats:
- Detect and remediate all malware in sanctioned cloud services using a threat-aware solution like Netskope Introspection.
- Detect and remediate all malware being downloaded from unsanctioned cloud services using a threat-aware solution like the Netskope Active Platform.
- Actively track usage of unsanctioned cloud services and enforce DLP policies to control files and data entering and leaving your corporate environment.
- Create a security policy to block portable executable files with content type “image/png.”
- Regularly back up and turn on versioning for critical content in cloud services.
- Enable “view known file extension” options in Windows and avoid executing any file with dual extensions unless you are sure they are benign.
- Warn users to avoid opening untrusted attachments regardless of their extension or file name.
- Enable two-factor authentication for email and banking accounts as a safety measure to prevent attackers from accessing the email account even if they know the password.
- Keep systems and antivirus updated with the latest releases and patches.
We will be publishing a detailed technical blog on CloudFanta soon.




 Atrás
Atrás















 Lea el blog
Lea el blog