Netskope nombrado Líder en el Cuadrante Mágico de Gartner® 2024™ para Security Service Edge. Obtenga el informe
-
Por qué Netskope
- Por qué Netskope
Por qué Netskope
Cambiar la forma en que las redes y la seguridad trabajan juntas.
Obtenga el informeAún más alto en ejecución.
Aún más lejos en visión.Sepa por qué 2024 Gartner® Cuadrante Mágico™ nombró a Netskope Líder para Security Service Edge por tercer año consecutivo.
- Por qué Netskope
Nuestros clientes
Netskope atiende a más de 3.000 clientes en todo el mundo, entre ellos más de 25 de las 100 empresas de Fortune
Ver nuestros clientesAyudamos a nuestros clientes a estar preparados para cualquier situación - Por qué Netskope
Nuestros Partners
Nos asociamos con líderes en seguridad para ayudarlo a asegurar su viaje a la nube.
Más información sobre los socios de NetskopeLa estrategia de venta centrada en el partner de Netskope permite a nuestros canales maximizar su expansión y rentabilidad y, al mismo tiempo, transformar la seguridad de su empresa.
-
Plataforma
- Plataforma
Plataforma Netskope One
Netskope One es una Plataforma convergente de seguridad y red como servicio.
Obtenga el whitepaperTu red del mañanaPlanifique su camino hacia una red más rápida, más segura y más resistente diseñada para las aplicaciones y los usuarios a los que da soporte.
- Plataforma
Netskope One Características de la plataforma
Netskope One potencia una mayor agilidad empresarial con la velocidad del rayo y una resistencia fiable.
Learn about Netskope OnePresentamos la Netskope One PlataformaNetskope One es una Plataforma nativa en la nube que ofrece servicios convergentes de seguridad y redes para hacer posible su transformación SASE y de confianza cero.
- Plataforma
NewEdge
NewEdge es la nube privada de seguridad más grande y de mayor rendimiento del mundo.
Más información sobre NewEdgeAdopte una arquitectura de borde de servicio de acceso seguro (SASE)Netskope NewEdge es la nube privada de seguridad más grande y de mayor rendimiento del mundo y ofrece a los clientes una cobertura de servicio, un rendimiento y una resiliencia incomparables.
- Plataforma
Partners tecnológicos e integraciones
Netskope colabora con las empresas más punteras en tecnología empresarial.
Más información sobre Cloud ExchangeNetskope Cloud ExchangeCloud Exchange (CE) de Netskope ofrece a sus clientes herramientas de integración eficaces para que saquen partido a su inversión en estrategias de seguridad.
-
Productos
- Productos
Servicio de seguridad Productos Edge
Protéjase contra las amenazas avanzadas y en la nube y salvaguarde los datos en todos los vectores.
Todos los productosLa plataforma del futuro es NetskopeIntelligent Security Service Edge (SSE), Cloud Access Security Broker (CASB), Cloud Firewall, Next Generation Secure Web Gateway (SWG) y Private Access for ZTNA integrados de forma nativa en una única solución para ayudar a todas las empresas en su camino hacia el Servicio de acceso seguro Arquitectura perimetral (SASE).
- Security service edge (SSE)
- Next Gen Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- ZTNA Next
- SkopeAI
- Seguridad de la nube pública
- Analítica avanzada
- Cloud Firewall
- Prevención de pérdida de datos (DLP)
- Digital Experience Management
- Inteligencia de dispositivos
- Remote Browser Isolation
- SaaS Security Posture Management
- Security service edge (SSE)
- Productos
Borderless SD-WAN
Proporcione con confianza un acceso seguro y de alto rendimiento a cada usuario remoto, dispositivo, sitio y nube.
Obtenga más información sobre Next Gen SASE BranchNext Gen SASE Branch es híbrida: conectada, segura y automatizadaNetskope Next Gen SASE Branch converge Context-Aware SASE Fabric, Zero-Trust Hybrid Security y SkopeAI-Powered Cloud Orchestrator en una oferta de nube unificada, marcando el comienzo de una experiencia de sucursal completamente modernizada para la empresa sin fronteras.
- Borderless SD-WAN
- Sucursal SASE de próxima generación
- SD-WAN seguro
- Endpoint SD-WAN
- Micro Branch
- WAN inalámbrica
- Multi-cloud networking
- Acceso inteligente IoT
- Borderless SD-WAN
- Productos
Secure Access Service Edge
Netskope One SASE proporciona una solución SASE nativa en la nube, totalmente convergente y de un único proveedor.
Obtenga el eBookDiseño de una arquitectura SASE para DummiesObtenga un ejemplar gratuito del único manual que necesitará sobre diseño de una arquitectura SASE.
-
Soluciones
- Soluciones
Transformación de la red
Logre agilidad y eficiencia a través de la transformación digital.
Go to Solutions OverviewMás información sobre NewEdgeCambie a los servicios de seguridad en la nube líderes del mercado con una latencia mínima y una alta fiabilidad. - Soluciones
Modernización de la seguridad
Enfrente los desafíos de seguridad de hoy y de mañana.
Descubra cómo aseguramos el uso generativo de IAHabilite de forma segura el uso de aplicaciones de IA generativa con control de acceso a aplicaciones, capacitación de usuarios en tiempo real y la mejor protección de datos de su clase.- Protección Avanzada contra Amenazas
- Protección de datos
- Trabajo híbrido
- Riesgo interno
- Garantizar la conformidad en la nube
- Reemplazar VPN
- Habilite de forma segura ChatGPT y IA generativa
- Protección de Aplicaciones Cloud Gestionadas
- Protección de Aplicaciones Cloud No Gestionadas
- AWS, Azure y GCP
- Protección Avanzada contra Amenazas
- Soluciones
Marcos
Adopte los marcos regulatorios que dan forma a la ciberseguridad.
Go to Solutions OverviewMás información sobre Confianza CeroSoluciones de confianza cero para implementaciones de SSE y SASE - Soluciones
Gobierno e Industrias
Netskope ayuda a las agencias y empresas más grandes del mundo a asegurar su viaje a la nube.
Más información sobre Netskope GovCloudNetskope logra la alta autorización FedRAMPElija Netskope GovCloud para acelerar la transformación de su agencia.
- Servicios Financieros y Seguros
- Salud
- Alta tecnología
- Instituciones de educación superior
- Educación primaria y secundaria
- Legal
- Fabricación
- Sector público
- Retail y Hostelería
- Empresas de servicios
- Utilities
- Servicios Financieros y Seguros
-
Recursos
- Recursos
Recursos
Obtenga más información sobre cómo Netskope puede ayudarle a proteger su viaje hacia la nube.
Reproducir el pódcastPodcast Security VisionariesHow to Use a Magic Quadrant and Other Industry Research
En este episodio, Max Havey, Steve Riley y Mona Faulkner diseccionan el intrincado proceso de creación de un Cuadrante Mágico y por qué es mucho más que un gráfico. - Recursos
Blog
Descubra cómo Netskope permite la transformación de la seguridad y las redes a través del borde de servicio de seguridad (SSE)
Lea el blogÚltimos blogsLea cómo Netskope puede hacer posible el viaje hacia la Confianza Cero y SASE a través de las capacidades del borde de servicio de seguridad (SSE).
- Recursos
Eventos y Talleres
Manténgase a la vanguardia de las últimas tendencias de seguridad y conéctese con sus pares.
Explorar sesionesSASE Week 2023: ¡Su viaje SASE comienza ahora!Sesiones de repetición de la cuarta SASE Week.
- Recursos
Seguridad definida
Todo lo que necesitas saber en nuestra enciclopedia de ciberseguridad.
Más información sobre el servicio de seguridad perimetral¿Qué es Security Service Edge (SSE)?Explore el lado de la seguridad de SASE, el futuro de la red y la protección en la nube.
- Descripción general de la seguridad definida
- ¿Qué es SASE?
- ¿Qué es Security Service Edge (SSE)?
- ¿Qué es un Cloud Access Security Broker (CASB)?
- ¿Qué es la seguridad Zero Trust?
- ¿Qué es Next Generation Secure Web Gateway (SWG)?
- ¿Qué es Data Loss Prevention (DLP)?
- ¿Qué es SD-WAN?
- ¿Qué es la IA generativa?
- ¿Qué es Remote Browser Isolation?
- ¿Qué es SSPM?
- ¿Qué es FedRamp?
- Descripción general de la seguridad definida
-
Empresa
- Empresa
Empresa
Le ayudamos a mantenerse a la vanguardia de los desafíos de seguridad de la nube, los datos y la red.
Descubra másApoyar la sostenibilidad a través de la seguridad de los datosNetskope se enorgullece de participar en Vision 2045: una iniciativa destinada a crear conciencia sobre el papel de la industria privada en la sostenibilidad.
- Empresa
Liderazgo
Nuestro equipo de liderazgo está firmemente comprometido a hacer todo lo necesario para que nuestros clientes tengan éxito.
Conozca a nuestro equipoPensadores, constructores, soñadores, innovadores. Juntos, ofrecemos soluciones de seguridad en la nube de vanguardia para ayudar a nuestros clientes a proteger sus datos y usuarios. - Empresa
Soluciones para clientes
Le apoyamos en cada paso del camino, garantizando su éxito con Netskope.
Más información sobre servicios profesionalesEl talentoso y experimentado equipo de servicios profesionales de Netskope proporciona un enfoque prescriptivo para su exitosa implementación.- Servicios Profesionales
- Satisfacción de los Clientes
- Soporte técnico
- Socios en la prestación de servicios
- Comunidad de clientes
- Documentación del producto
- Support Portal
- Trust Portal
- Servicios Profesionales
- Empresa
Formación y certificación
La formación de Netskope le ayudará a convertirse en un experto en seguridad en la nube.
Infórmese sobre Capacitaciones y CertificacionesAsegure su viaje de transformación digital y aproveche al máximo sus aplicaciones en la nube, web y privadas con la capacitación de Netskope.- Formación técnica en línea de introducción a Netskope Security Cloud
- Operación y administración de Netskope Security Cloud (NSCO&A)
- Implementación e integración de Netskope Security Cloud (NSCI&I)
- Programa de certificación en seguridad para la nube de Netskope
- Formación técnica en línea de introducción a Netskope Security Cloud
- Por qué Netskope
Cambiar la forma en que las redes y la seguridad trabajan juntas.
- Nuestros clientes
Netskope atiende a más de 3.000 clientes en todo el mundo, entre ellos más de 25 de las 100 empresas de Fortune
- Nuestros Partners
Nos asociamos con líderes en seguridad para ayudarlo a asegurar su viaje a la nube.
Aún más lejos en visión.
Sepa por qué 2024 Gartner® Cuadrante Mágico™ nombró a Netskope Líder para Security Service Edge por tercer año consecutivo.
Obtenga el informe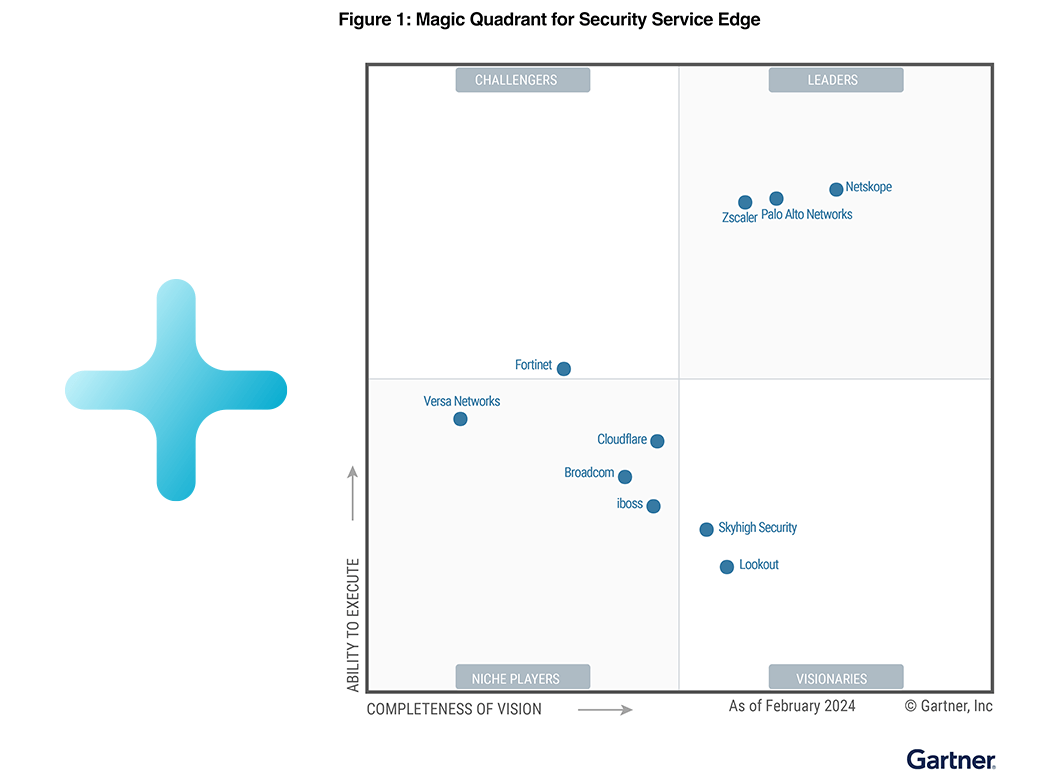

- Plataforma Netskope One
Netskope One es una Plataforma convergente de seguridad y red como servicio.
- Netskope One Características de la plataforma
Netskope One potencia una mayor agilidad empresarial con la velocidad del rayo y una resistencia fiable.
- NewEdge
NewEdge es la nube privada de seguridad más grande y de mayor rendimiento del mundo.
- Partners tecnológicos e integraciones
Netskope colabora con las empresas más punteras en tecnología empresarial.
Planifique su camino hacia una red más rápida, más segura y más resistente diseñada para las aplicaciones y los usuarios a los que da soporte.
Obtenga el whitepaper
Netskope One es una Plataforma nativa en la nube que ofrece servicios convergentes de seguridad y redes para hacer posible su transformación SASE y de confianza cero.
Learn about Netskope One
Netskope NewEdge es la nube privada de seguridad más grande y de mayor rendimiento del mundo y ofrece a los clientes una cobertura de servicio, un rendimiento y una resiliencia incomparables.
Más información sobre NewEdge
Cloud Exchange (CE) de Netskope ofrece a sus clientes herramientas de integración eficaces para que saquen partido a su inversión en estrategias de seguridad.
Más información sobre Cloud Exchange
- Servicio de seguridad Productos Edge
Protéjase contra las amenazas avanzadas y en la nube y salvaguarde los datos en todos los vectores.
- Borderless SD-WAN
Proporcione con confianza un acceso seguro y de alto rendimiento a cada usuario remoto, dispositivo, sitio y nube.
- Secure Access Service Edge
Netskope One SASE proporciona una solución SASE nativa en la nube, totalmente convergente y de un único proveedor.
- Security service edge (SSE)
- Next Gen Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- ZTNA Next
- SkopeAI
- Seguridad de la nube pública
- Analítica avanzada
- Cloud Firewall
- Prevención de pérdida de datos (DLP)
- Digital Experience Management
- Inteligencia de dispositivos
- Remote Browser Isolation
- SaaS Security Posture Management
Intelligent Security Service Edge (SSE), Cloud Access Security Broker (CASB), Cloud Firewall, Next Generation Secure Web Gateway (SWG) y Private Access for ZTNA integrados de forma nativa en una única solución para ayudar a todas las empresas en su camino hacia el Servicio de acceso seguro Arquitectura perimetral (SASE).
Todos los productos
Netskope Next Gen SASE Branch converge Context-Aware SASE Fabric, Zero-Trust Hybrid Security y SkopeAI-Powered Cloud Orchestrator en una oferta de nube unificada, marcando el comienzo de una experiencia de sucursal completamente modernizada para la empresa sin fronteras.
Obtenga más información sobre Next Gen SASE Branch
Obtenga un ejemplar gratuito del único manual que necesitará sobre diseño de una arquitectura SASE.
Obtenga el eBook
- Transformación de la red
Logre agilidad y eficiencia a través de la transformación digital.
- Modernización de la seguridad
Enfrente los desafíos de seguridad de hoy y de mañana.
- Marcos
Adopte los marcos regulatorios que dan forma a la ciberseguridad.
- Gobierno e Industrias
Netskope ayuda a las agencias y empresas más grandes del mundo a asegurar su viaje a la nube.
- Protección Avanzada contra Amenazas
- Protección de datos
- Trabajo híbrido
- Riesgo interno
- Garantizar la conformidad en la nube
- Reemplazar VPN
- Habilite de forma segura ChatGPT y IA generativa
- Protección de Aplicaciones Cloud Gestionadas
- Protección de Aplicaciones Cloud No Gestionadas
- AWS, Azure y GCP



Elija Netskope GovCloud para acelerar la transformación de su agencia.
Más información sobre Netskope GovCloud
- Recursos
Obtenga más información sobre cómo Netskope puede ayudarle a proteger su viaje hacia la nube.
- Blog
Descubra cómo Netskope permite la transformación de la seguridad y las redes a través del borde de servicio de seguridad (SSE)
- Eventos y Talleres
Manténgase a la vanguardia de las últimas tendencias de seguridad y conéctese con sus pares.
- Seguridad definida
Todo lo que necesitas saber en nuestra enciclopedia de ciberseguridad.
- Descripción general de la seguridad definida
- ¿Qué es SASE?
- ¿Qué es Security Service Edge (SSE)?
- ¿Qué es un Cloud Access Security Broker (CASB)?
- ¿Qué es la seguridad Zero Trust?
- ¿Qué es Next Generation Secure Web Gateway (SWG)?
- ¿Qué es Data Loss Prevention (DLP)?
- ¿Qué es SD-WAN?
- ¿Qué es la IA generativa?
- ¿Qué es Remote Browser Isolation?
- ¿Qué es SSPM?
- ¿Qué es FedRamp?
How to Use a Magic Quadrant and Other Industry Research
En este episodio, Max Havey, Steve Riley y Mona Faulkner diseccionan el intrincado proceso de creación de un Cuadrante Mágico y por qué es mucho más que un gráfico.

Lea cómo Netskope puede hacer posible el viaje hacia la Confianza Cero y SASE a través de las capacidades del borde de servicio de seguridad (SSE).
Lea el blog
Sesiones de repetición de la cuarta SASE Week.
Explorar sesiones
Explore el lado de la seguridad de SASE, el futuro de la red y la protección en la nube.
Más información sobre el servicio de seguridad perimetral
- Empresa
Le ayudamos a mantenerse a la vanguardia de los desafíos de seguridad de la nube, los datos y la red.
- Liderazgo
Nuestro equipo de liderazgo está firmemente comprometido a hacer todo lo necesario para que nuestros clientes tengan éxito.
- Soluciones para clientes
Le apoyamos en cada paso del camino, garantizando su éxito con Netskope.
- Formación y certificación
La formación de Netskope le ayudará a convertirse en un experto en seguridad en la nube.
Netskope se enorgullece de participar en Vision 2045: una iniciativa destinada a crear conciencia sobre el papel de la industria privada en la sostenibilidad.
Descubra más




















