Summary
Netskope Threat Labs is warning users to be careful of spam messages being shared via Google Docs. The spam messages come in the form of a comment on a document or presentations and are sent by [email protected]. Both the comment and the document link the user to a spam or scam website. Because the messages are sent by Google Docs, it is likely that your spam filters do not detect and block these messages. In fact, docs.google.com may be explicitly allowed by your spam filters.
Example
The spam is delivered in the form of a comment on a Google Docs document or Google Slides presentation. The email is sent by [email protected], an address used for comments added to any files hosted in Google Drive. In this Google Slides example, the sender appears as “Message Service (Google Slides).” “Message Service” is the name chosen by the spammer to make this appear official and “(Google Slides)” is appended by Google to all Google Slides comments.
In this example, the comment masquerades as a postal notification:
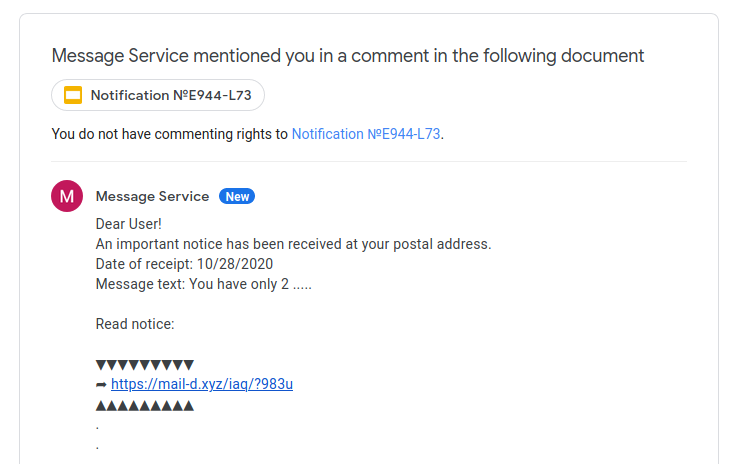
The document itself is a Google Slides presentation with a single slide containing a hyperlink that redirects the user to an adult website:
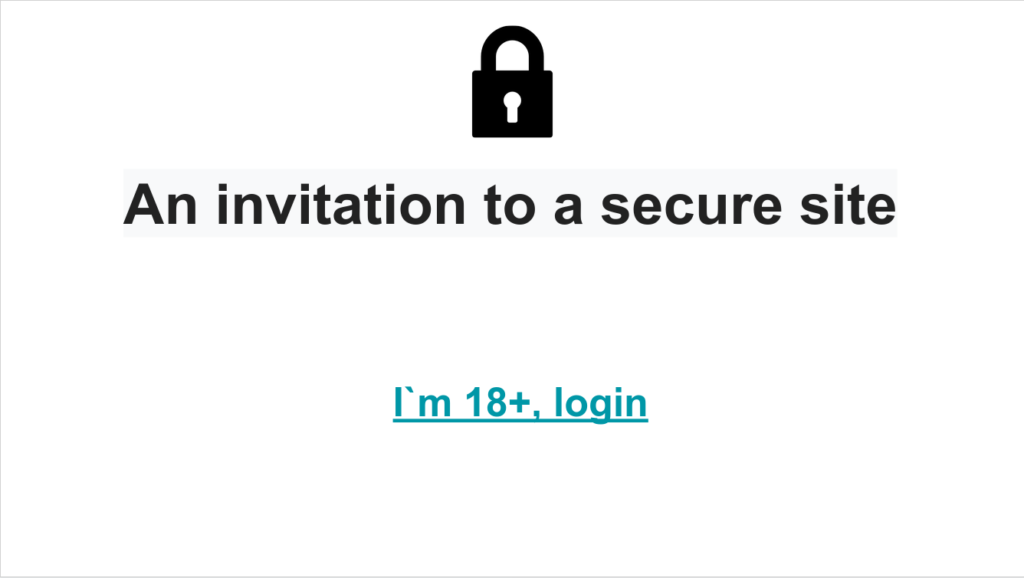
This particular spam message was targeted generally at personal gmail.com accounts and not any specific enterprises or demographics. The motive was to entice recipients to sign up for a premium adult website.
Context
Cloud apps are a popular vehicle for the distribution of malicious content. One reason for their popularity is the fact that attacks launched from cloud apps can often subvert enterprise security controls, such as email or URL filtering.
Over the past year, we have detected and blocked a variety of attacks launched by cybercriminals leveraging a variety of cloud apps, including Google Drive. In total, 17% of malicious websites we block our users from visiting come from links in cloud apps. Of those, Google Drive represents 1%.
The following figure breaks down types of attacks cybercriminals launched using Google Drive, where the goal was to get users to click on a malicious link. Over the past year, 2% of those links were spam, like in this example. The most common types of attacks linked victims to phishing pages (14%) or malware delivery points (76%).

Disclosure
The documents involved in this spam campaign were reported to Google on October 29, 2020, and promptly taken down.
Conclusions
Cybercriminals are always looking for new ways to abuse cloud apps. In this example, spammers succeeded in using comments in Google Slides to deliver spam messages that bypass common filters. We urge users to be extra careful in clicking on links in any cloud app, even if it is a cloud app that you commonly use. We expect spam like this to continue in the near to medium term, and for it to take on election, coronavirus, and holiday themes through the coming months.
The Netskope Security Cloud platform provides our customers protection against attacks like these launched from cloud apps.




 Retour
Retour 















 Lire le blog
Lire le blog