Summary
From January to April 2025, Netskope Threat Labs tracked a three-fold increase in traffic to phishing pages created on the Glitch platform. These phishing campaigns have affected more than 830 organizations and over 3,000 users since January 2025, primarily targeting Navy Federal Credit Union members and seeking sensitive information.
Still, they also go after data from other services, including email login credentials, credit card details, and other bank-related information. The phishing campaigns exhibit two notable characteristics. Firstly, half of the campaigns investigated abuse Telegram to exfiltrate victims’ data and capture one-time passwords, thereby circumventing multi-factor authentication. Secondly, some campaigns employ a custom-built CAPTCHA test, which prevents static scanners from accessing the phishing page payload.
Key findings
- Netskope Threat Labs observed a surge in traffic to phishing pages that are hosted on the Glitch platform.
- The phishing campaigns primarily target Navy Federal Credit union members, targeting their login credentials to potentially gain unauthorized access and perform fraudulent transactions.
- Half of the phishing campaigns abuse Telegram to siphon the victim’s sensitive data and one-time passwords.
Glitch abused to create and deploy phishing websites
Glitch is a platform that allows you to create, edit, and deploy web apps directly from your browser, supporting Node.js, static sites, and collaborative coding.
Users receive 1,000 monthly project-hours on the free tier, shared across all non-static projects. Static sites, commonly used for phishing pages, do not consume these hours and remain online 24/7.
Each project on Glitch is assigned a free, publicly accessible subdomain that typically goes live minutes after creation. These subdomains consist of three hyphenated English words.
Attackers abuse Glitch’s features to host their phishing pages for free across multiple projects, each with a unique subdomain accessible to victims. Notably, Glitch’s “Remix” feature allows them to duplicate web apps, creating new subdomains while keeping the original app active. This allows attackers to set up multiple phishing pages within minutes.
Attackers often abuse free web hosting services to create phishing pages and target victims. Our previous posts have highlighted their misuse of platforms like AWS Amplify, Webflow, CloudFlare Workers, and Microsoft Sway.
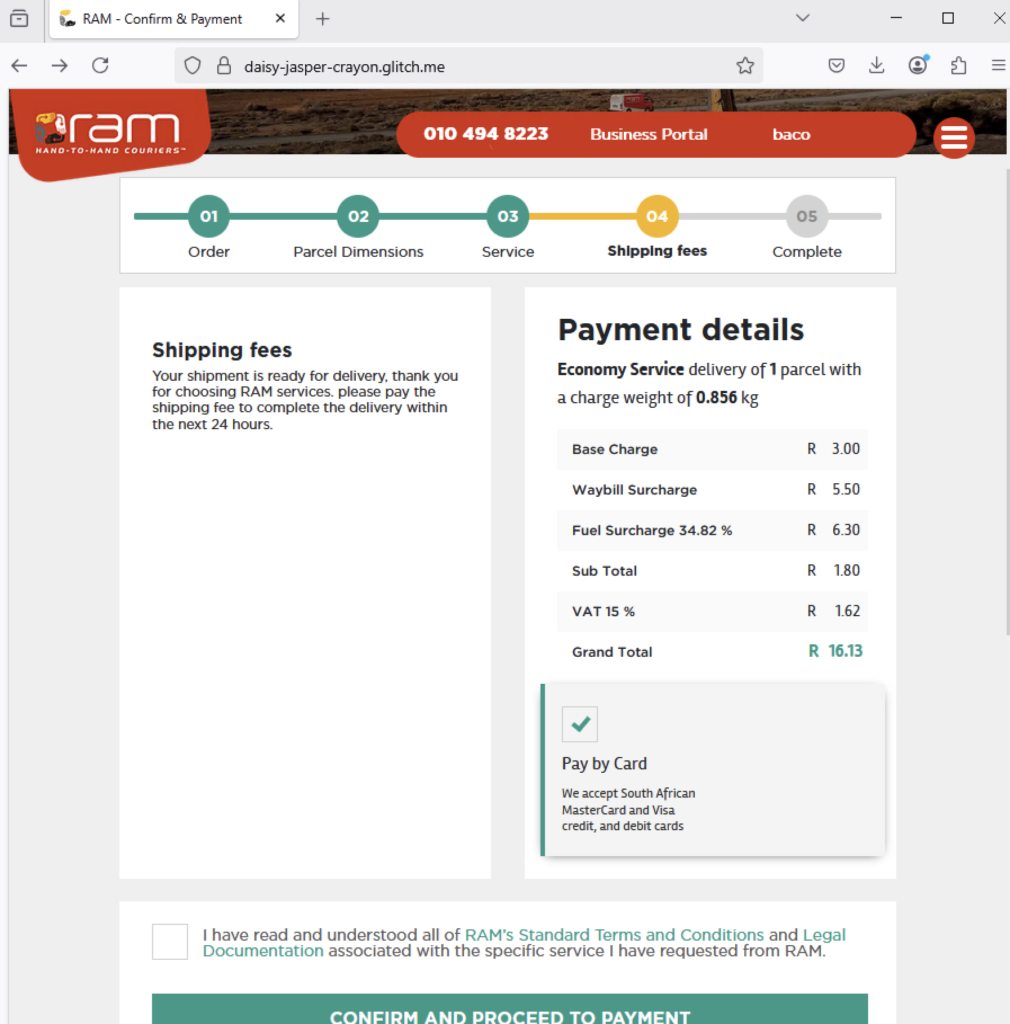
Netskope Threat Labs has observed that traffic to phishing pages hosted on Glitch has more than tripled, increasing 3.32x from January to April. These campaigns primarily target Navy Federal Credit Union customers, T-Mobile accounts, and various companies’ email credentials and credit card information. Sites hosted on Glitch can be identified by the following URL pattern. You should never enter any sensitive information on such sites.:
<projectname-projectname-projectname.glitch[.]me>
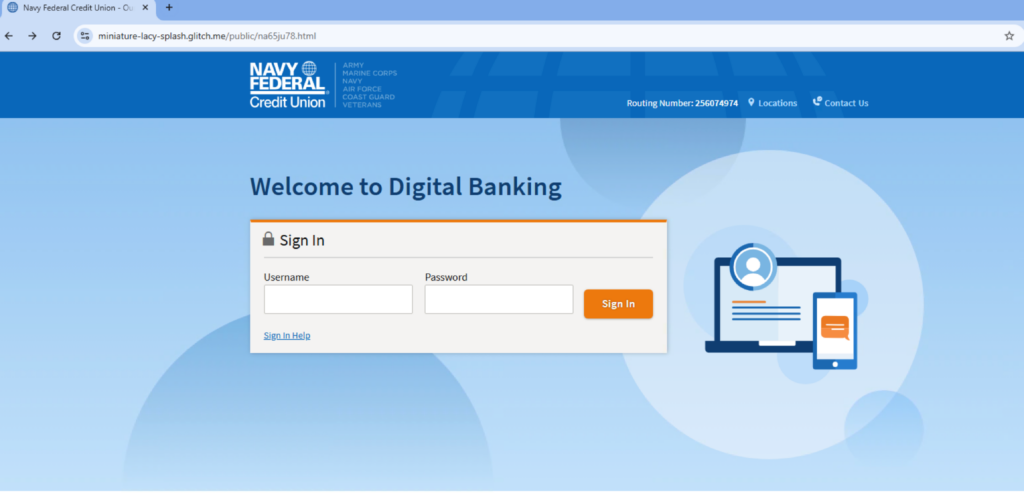
Navy Federal Credit Union
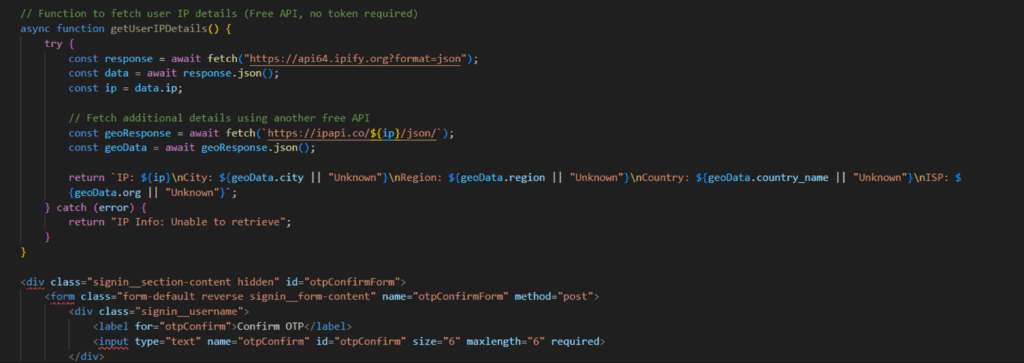
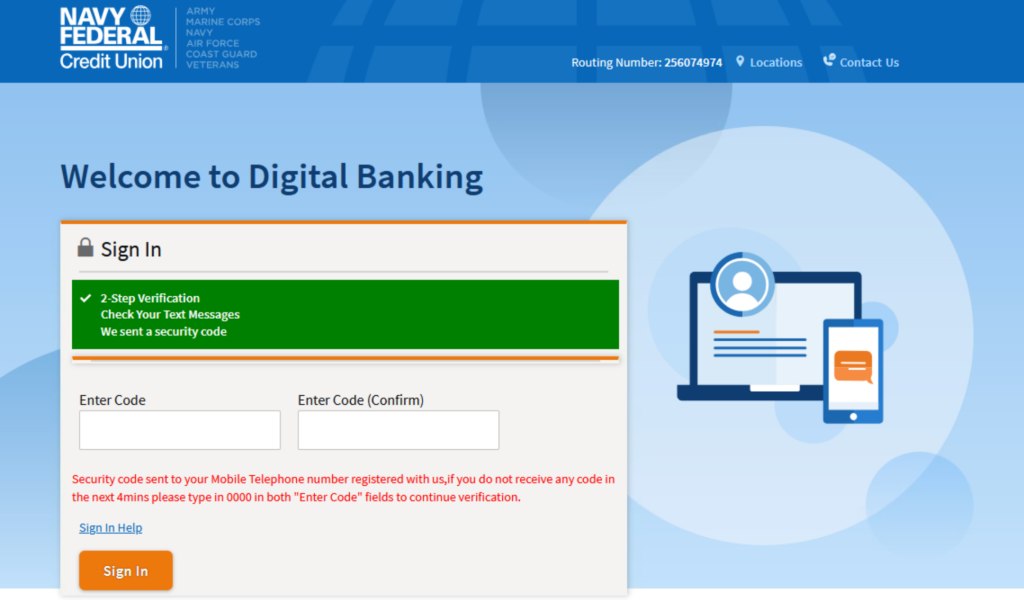
The majority of the phishing pages investigated were targeting Navy Federal Credit Union members. Attackers initially require victims to log in using the victim’s username and password. Aside from this information, the attacker also collects the victim’s public IP address and the victim’s country and city silently using JavaScript. Attackers use several services to collect the victim’s location, like I2.io, ipify, and ipinfo. All this information is sent to the attacker using Telegram’s sendMessage method from BotAPI.
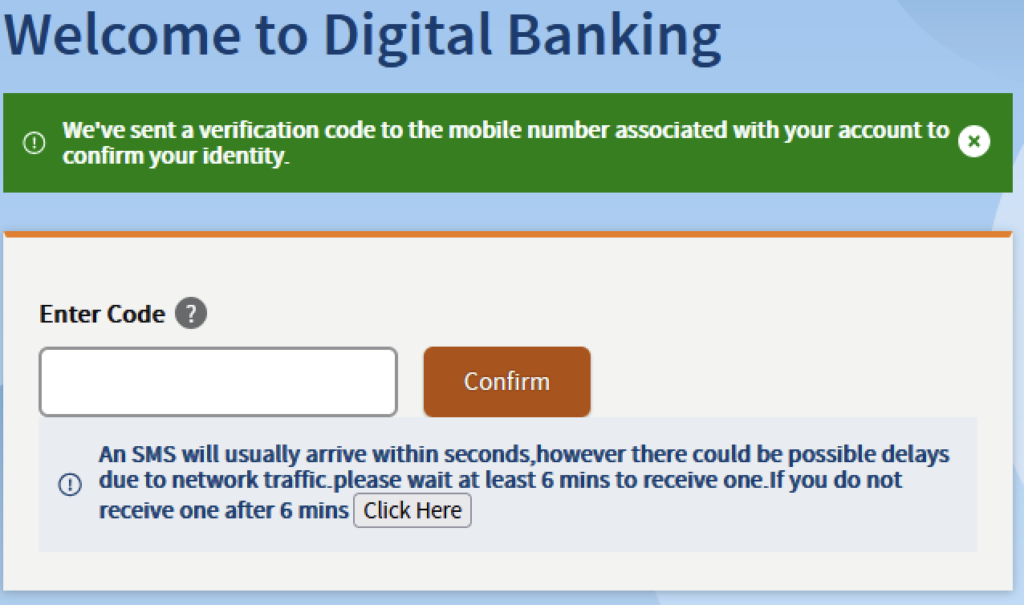
After obtaining the login information, attackers request a one-time password (OTP) sent to the victim’s phone. When the victim enters the OTP on the phishing site, it will be sent to the attacker through Telegram, which they can use to log in on the victim’s behalf, effectively giving attackers access to the victim’s account. Netskope Threat Labs has previously reported similar phishing techniques where attackers successfully circumvented multi-factor authentication using Telegram.
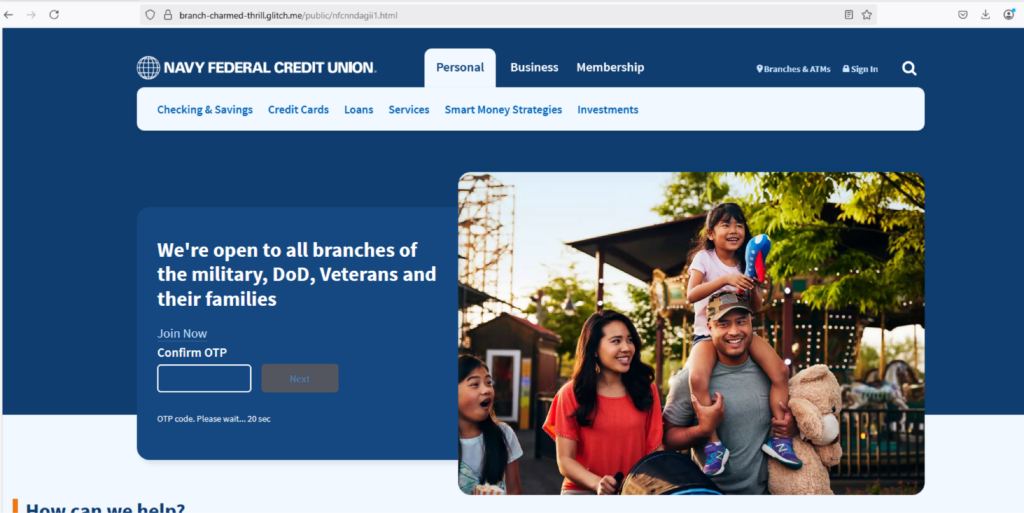

Interestingly, for victims who can’t enter the one-time password, the attacker instructs them to proceed anyway or to use a placeholder like “0000”. After this, the attackers request more sensitive information, including the user’s email address and password. This can be used by the attackers to initiate a credential reset process, potentially granting them unauthorized access to the victim’s account.
Phishing pages behind a fake CAPTCHA
Some phishing campaigns hosted in Glitch hide their phishing pages behind fake CAPTCHAs. In 2025, Netskope Threat Labs published blog posts revealing several phishing and malware campaigns that employ fake CAPTCHA to trick victims into downloading the malicious payload or enter their credentials, which can indicate that this technique is becoming increasingly prevalent among attackers.
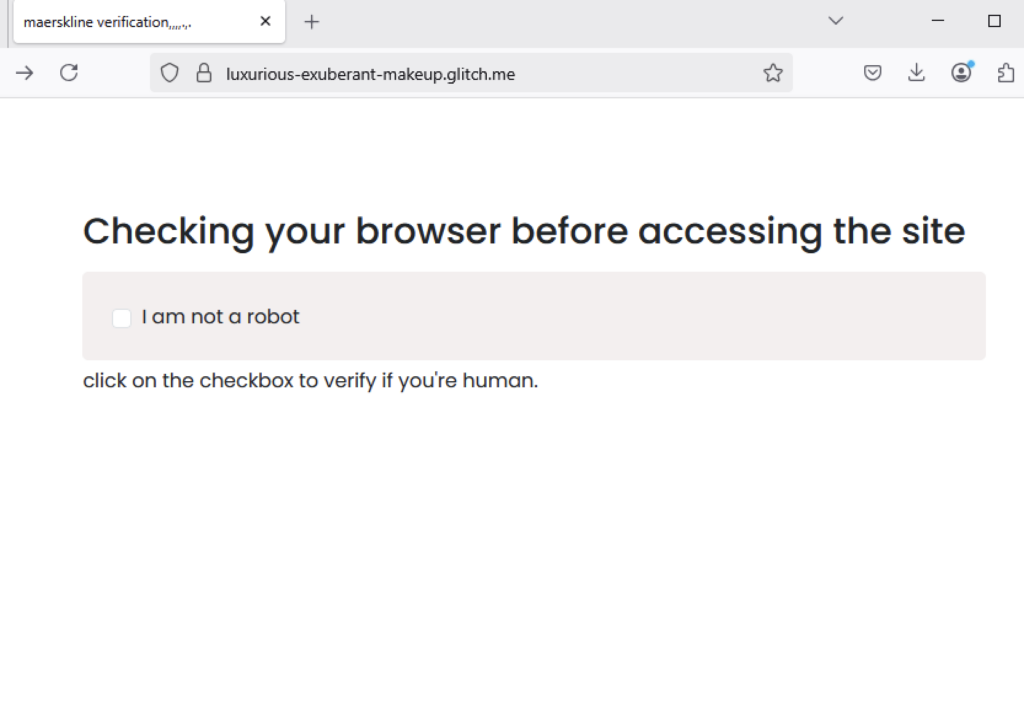
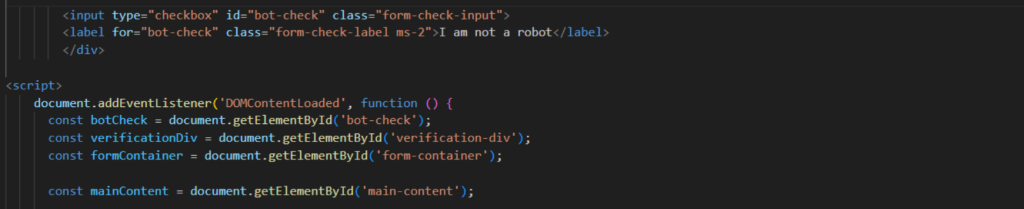
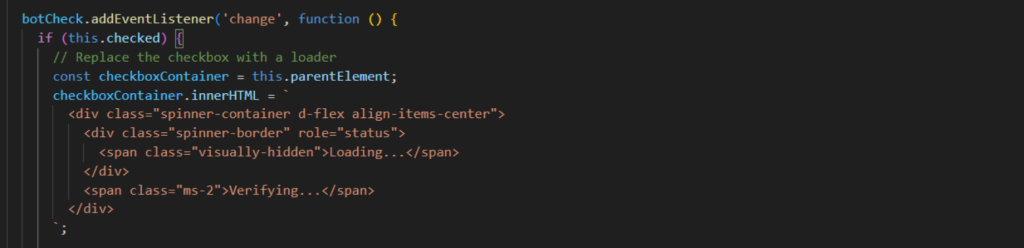
The fake CAPTCHA starts with a checkbox labeled “bot-check” and uses JavaScript to monitor changes to it. When the victim clicks to check the box, the script replaces the checkbox with a spinning loader to create the illusion of a real CAPTCHA test. In reality, the user is just redirected to the phishing site.
Telegram abused to exfiltrate credentials and bypass MFA
Half of the phishing campaigns investigated hosted in Glitch abuse Telegram to exfiltrate the collected information from the victim. Aside from fake CAPTCHAs, Netskope Threat Labs also continues to observe frequent abuse of Telegram for data exfiltration by infostealers, phishing, and for command-and-control (C2) operations.
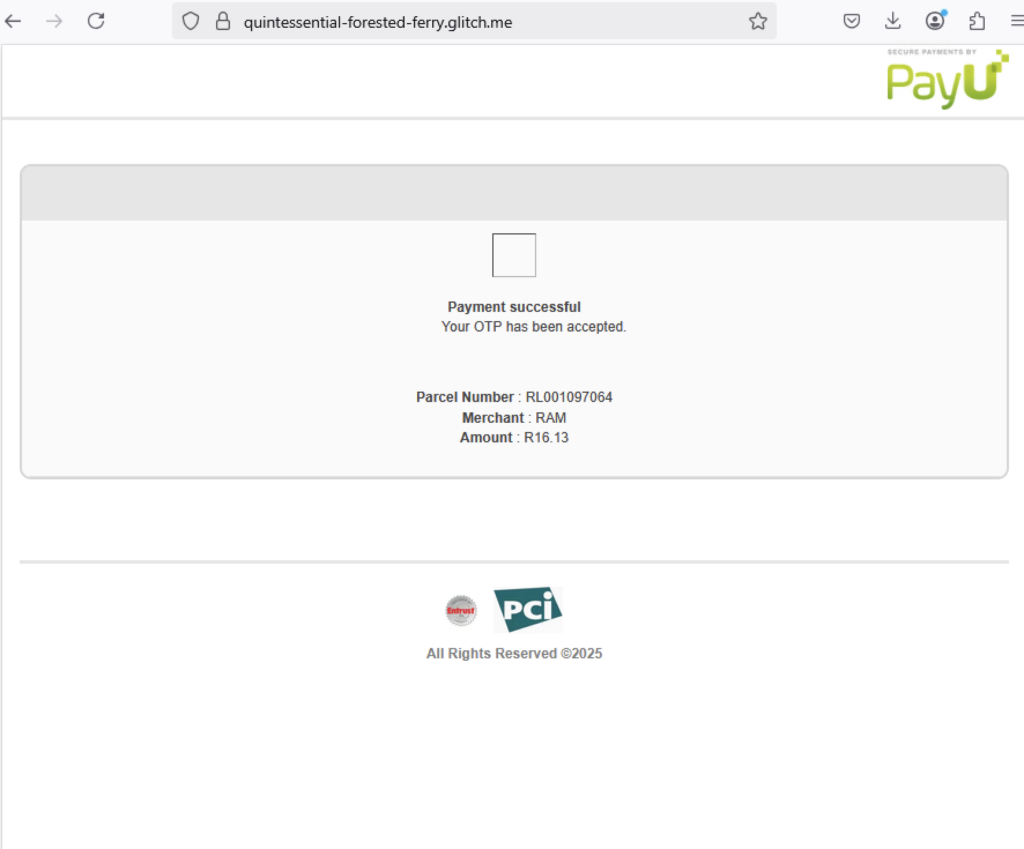
Attackers not only use Telegram to collect credentials, but also to obtain the victim’s one-time password (OTP). Some phishing campaigns mimic payment pages, prompting victims for credit card details and phone numbers. Once victims provide this information, attackers request the OTP, allowing them to bypass multi-factor authentication and carry out fraudulent actions. Some phishing pages display fake payment success messages to convince victims they are not being scammed.
Conclusion
Netskope Threat Labs is monitoring phishing campaigns and has identified several targeting Navy Federal Credit Union members and other banks, hosted on Glitch. Some campaigns abuse Telegram to collect credentials and one-time passwords, bypassing multi-factor authentication. Additionally, some use fake CAPTCHAs to deceive users while hiding the phishing page from static web scanners. Netskope Threat Labs will continue tracking and responding to this campaign set.
Disclosure
- Relevant IOCs were submitted to Glitch.
Data Analysis
The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
IOCs
All the IOCs related to this campaign can be found in our GitHub repository.




 Retour
Retour 















 Lire le blog
Lire le blog