Netskope Threat Research Labs has detected a browser-based coin miner named Coinhive resident in Microsoft Office 365 OneDrive for Business. The Coinhive miner was installed as a plugin in an SSL website. The tutorial webpage hosted on the website was saved to the cloud and then shared within an organization. The presence of browser-based coin miners can consume high computing power and resources without the user’s consent, thereby slowing down CPU performance. Netskope Threat Protection detects the Coinhive miner as Application.BitCoinMiner.SX
As an integral part of threat research, we constantly monitor updates and trends of coin miners. In this ongoing trend of coin mining, a website named ‘Coinhive’ launched a browser plugin script that can perform mining when a web page is loaded, without the need to install software. This coin mining method is intended to provide a new revenue stream that is similar to the ad-revenue model generated by displaying/loading ads while visiting a website.
This surreptitious install of a coin miner in a corporate environment follows with previous publication of Zminer that downloads second stage coin miners from Amazon S3 and also uses the same for data exfiltration. During the analysis of Zminer on August, the market cap of Cryptocurrency was $150 billion. It has now drastically increased to a $200 billion valuation as shown in Figure 1.
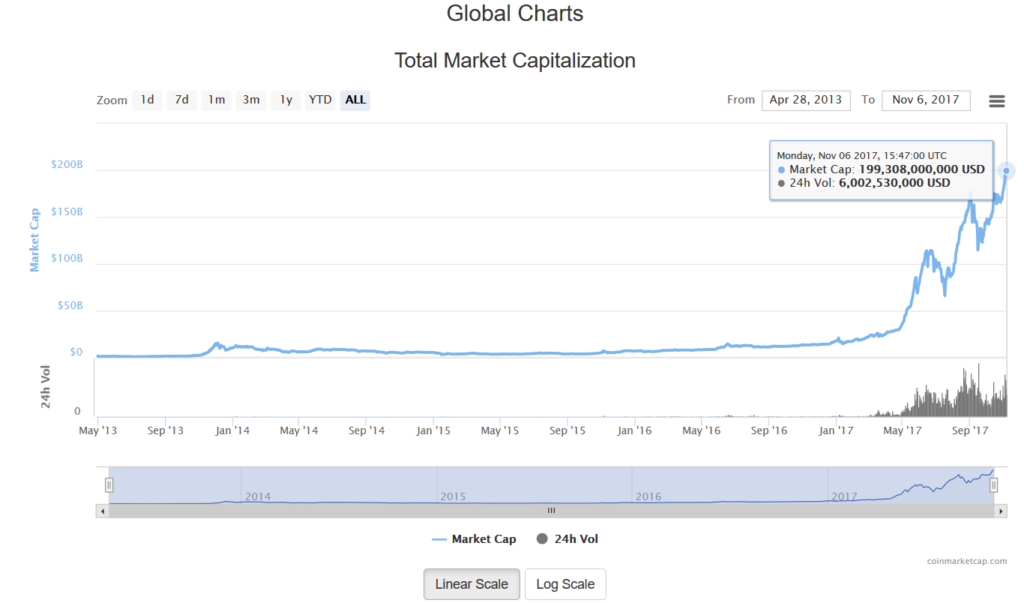
Figure 1: Cryptocurrency market cap
Discovery
Earlier this month, Netskope Threat Protection detected a file named coinhive.min.js in Microsoft Office 365 OneDrive for Business. We examined the functionality and found that it is a browser-based plugin coin miner. Using Netskope Discovery and additional details from the Netskope Active Introspection alert, we found the presence of the Coinhive miner in a website named https://www.sky-future[.]net.
An excerpt of the Coinhive code seen in the website is shown in Figure 2.
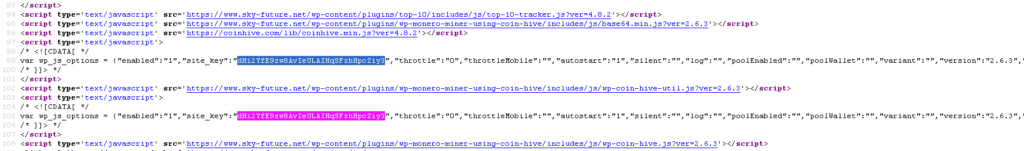
Figure 2: Coinhive miner in the website, https://www.sky-future[.]net
Overview of Coinhive
Coinhive is a JavaScript library launched in 2017. It allows a website to use the client computer to mine Monero cryptocurrency offering site owners an alternative to online advertising. The money mined by the browser-based hosted scripts is credited from Coin Hive to the website Owners/Administrators. Using Coinhive, one can get the number of hashes solved for a user account, withdraw hashes, verify tokens and programmatically create short links.
Unlike popular miners, Coinhive does not provide any specific information about the account owner as per the privacy terms.
The mining options provided by the Coinhive constructor is shown in Figure 3.
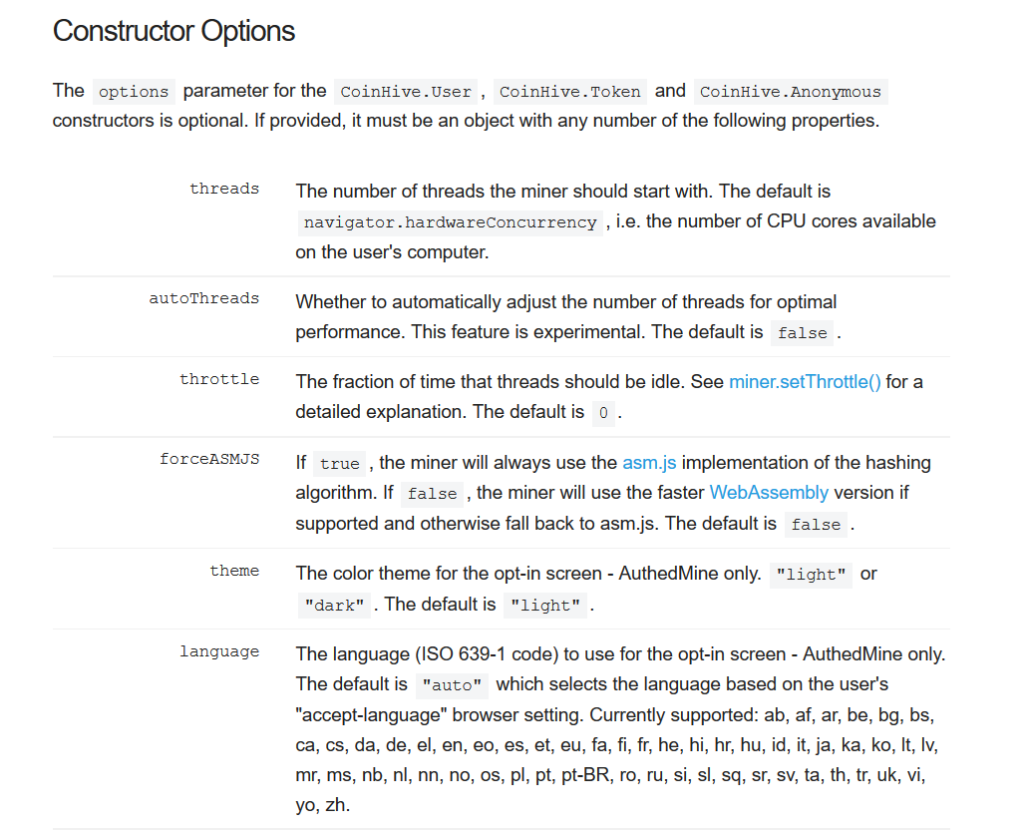
Figure 3: Coinhive Constructor options
Authedmine
Coinhive miner browser plugin is simple and easy to install. This plugin has been lately adopted by several websites, thus raising concerns about the usage of CPU power and resources without the user’s consent. Approximately, 2.2 percent of the top 100,000 websites on the Alexa list have been reported to be mining through user PCs. To address this, Coinhive launched Authedmine, which enforces an explicit opt-in consent from the end user to run the miner. If the user approves the permission, an opt-in token is stored in a cookie to perform the mining operation. However, this is not a mandatory implementation, thus making all previous solutions to continue to work without the explicit opt-in consent as shown in Figure 4.
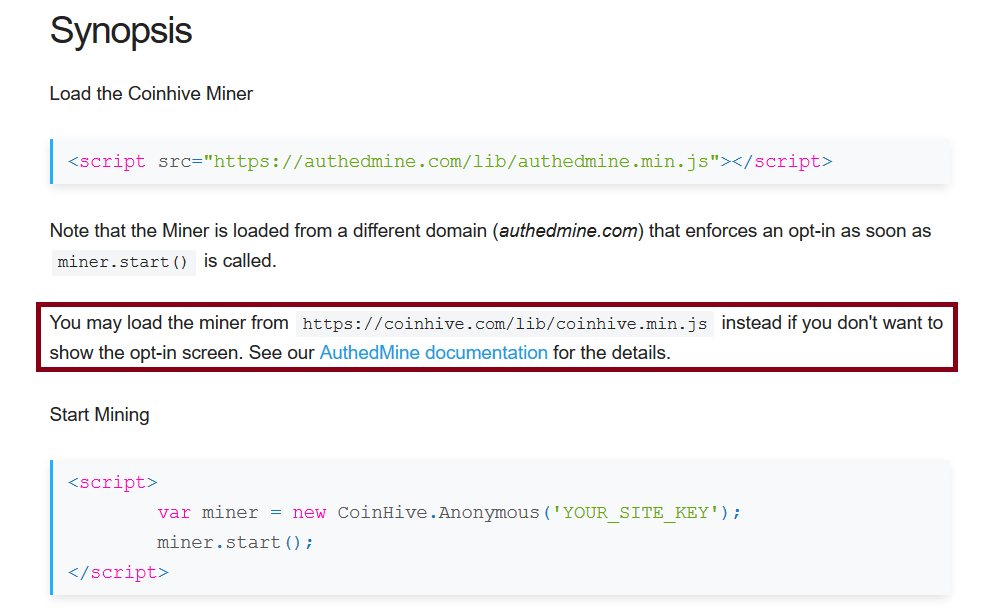
Figure 4: Loading the Coinhive miner
Analysis of the Coinhive miner
On visiting the website, https://www.sky-future[.]net, a GET request was called to the Coinhive miner plugin from the browser as shown in Figure 5.
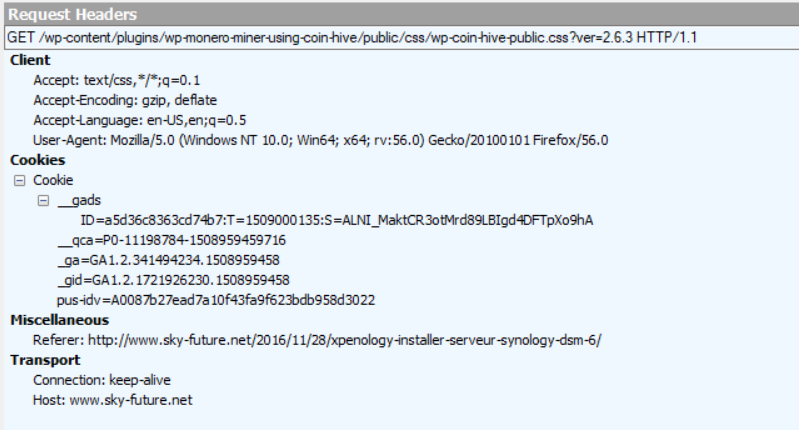
Figure 5: GET request called to the coin hive miner plugin
Since the website owner did not implement the Authedmine option, no explicit opt-in consent is displayed while visiting the website. Hence, any user from the organization is unaware that the corporate machine is used for mining without their knowledge or consent.
The Coinhive config present in the script “coinhive.min.js” contained a list of websocket shards in to perform the mining Figure 6.
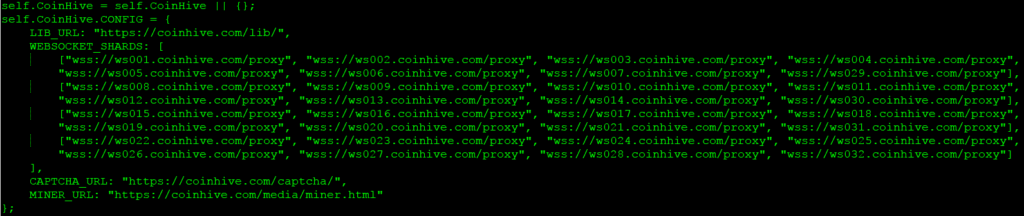
Figure 6: Coinhive websocket shards
Using the user key mentioned in Figure 2, Coinhive begins the worker job as shown in Figure 7.
Figure 7 : Worker job of Coinhive
Since the mining is performed without users’ consent without displaying the explicit opt-in consent, we can give a verdict that the Coinhive miner plugin is carrying out a cryptojacking operation, causing the user’s browser to consume high CPU usage.
Conclusion
Browser-based mining is an innovation and also an alternative revenue generating model. Since the mining operation takes place while visiting the website, we expect an increasing potential of browser miners. This leads to an interesting arena of choosing the option of displaying ads or giving away CPU cycles every time the website is visited. On the same note, this can be a serious concern for organizations who are unaware that the corporate machines are being used for mining without their knowledge or consent. The browser miners can also be abused by malware authors to exploit the victims computing power and resources. As enterprises are rapidly adopting the use of cloud and cloud services, the need for a threat-aware solution and defensive mechanism for SSL inspection is required. After the initial analysis and reporting, the website, https://www.sky-future[.]net removed the Coinhive plugin from the website. We will continue to monitor the trends of the coin miners and update accordingly.
General Recommendations
Netskope recommends the following to combat cloud malware and threats:
- Detect and remediate cloud threats using a threat-aware CASB solution like Netskope and enforce policy on usage of unsanctioned services as well as unsanctioned instances of sanctioned cloud services
- Sample policies to enforce:
- Scan all uploads from unmanaged devices to sanctioned cloud applications for malware
- Scan all uploads from remote devices to sanctioned cloud applications for malware
- Scan all downloads from unsanctioned cloud applications for malware
- Scan all downloads from unsanctioned instances of sanctioned cloud applications for malware
- Enforce quarantine/block actions on malware detection to reduce user impact
- Block unsanctioned instances of sanctioned/well known cloud apps, to prevent attackers from exploiting user trust in cloud. While this seems a little restrictive, it significantly reduces the risk of malware infiltration attempts via cloud
- Enforce DLP policies to control files and data en route to or from your corporate environment
- Regularly back up and turn on versioning for critical content in cloud services
- Enable the “View known file extensions” option on Windows machines
- Warn users to avoid executing unsigned macros and macros from an untrusted source, unless they are very sure that they are benign
- Administrators can create firewall rules to block bitcoin pools documented in the Wikipedia article
- Warn users to avoid executing any file unless they are very sure that they are benign
- Warn users against opening untrusted attachments, regardless of their extensions or filenames
- Keep systems and antivirus updated with the latest releases and patches




 Retour
Retour 
















 Lire le blog
Lire le blog