Summary
Attackers who were previously abusing DigitalOcean to host a tech support scam have expanded the operation, now abusing StackPath CDN to distribute the scam, and are likely to start abusing additional cloud services to deliver the scam in the near future. From February 1 to March 16, Netskope Threat Labs has seen a 10x increase of traffic to tech support scam pages delivered by StackPath CDN. Their end goal remains the same, which is to convince victims that their computer is infected with malware and have them call the “support” hotline.
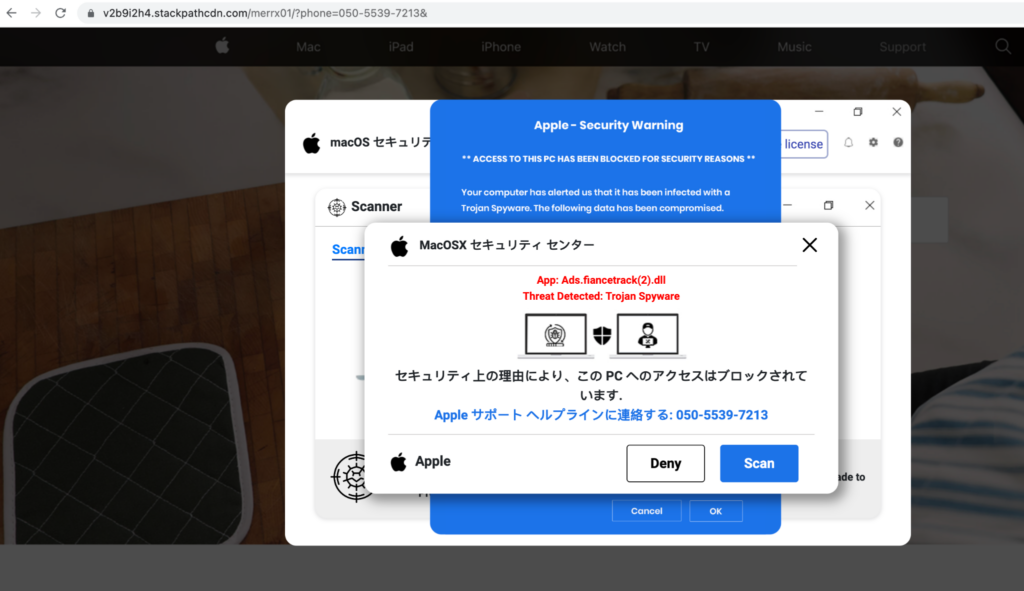
The scammers appear to be shifting their focus from abusing a single cloud service to instead simultaneously abusing multiple services. While traffic to the scam pages on StackPath is on the rise, traffic to the same scam pages hosted on DigitalOcean continues, having decreased only slightly since our previous blog post on this topic. At the same time, the scam pages have also surfaced on Azure Web Apps and Amazon CloudFront. The scammers have been reaching victims mainly in North America, Asia, and Southern Europe.
Netskope Threat Labs continues to report domains hosting the scam to Digital Ocean and have now started reporting domains hosting the scam to StackPath too. We expect that the scammers will likely continue to pivot among cloud services to try to evade detection and takedowns. We will continue monitoring the scam and provide relevant updates.
Recommendations
The scams and phishing pages described in the post are easily recognisable by the URL, as the attacker has made little effort to disguise the URL. Users can easily avoid becoming victims of the types of attacks described in this post by simply checking the URL and making sure it is the legitimate website. Users should always access important pages, like their banking portal or webmail, by typing the URL directly into the web browser instead of using search engines or any other links, as the results could be manipulated by SEO techniques or malicious ads. We strongly recommend immediately closing web pages that say your computer is infected and also never calling the number on the screen.
Netskope Threat Labs recommends that organizations review their security policies to ensure that they are adequately protected against these and similar phishing pages and scams. Other recommendations include:
- Inspect all HTTP and HTTPS traffic, including all web and cloud traffic, to prevent users from visiting malicious websites. Netskope customers can configure their Netskope NG-SWG with a URL filtering policy to block known phishing and scam sites, and a threat protection policy to inspect all web content to identify unknown phishing and scam sites using a combination of signatures, threat intelligence, and machine learning.
- Use Remote Browser Isolation (RBI) technology to provide additional protection when there is a need to visit websites that fall into categories that can present higher risk, like newly observed and newly registered domains.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Threat Protection
- Document-HTML.Trojan.TechScam
- Document-HTML.Trojan.Cryxos
- Trojan.GenericKD.65753936
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Malware.Detect.By.Sandbox indicates a sample that was detected by our cloud sandbox
IOCs
Below are the IOCs related to the web pages analyzed in this blog post.
Domains:
a4a2r9q8[.]stackpathcdn[.]com
a5q2c2k7[.]stackpathcdn[.]com
b3n4c8r7[.]stackpathcdn[.]com
b3x6d2v5[.]stackpathcdn[.]com
b5h9h6d4[.]stackpathcdn[.]com
b6c9x3b7[.]stackpathcdn[.]com
b7d3s6s3[.]stackpathcdn[.]com
b7j5t2j8[.]stackpathcdn[.]com
c3c5i7q7[.]stackpathcdn[.]com
c5m8g6b6[.]stackpathcdn[.]com
c6c5i6r3[.]stackpathcdn[.]com
c9y9t7u6[.]stackpathcdn[.]com
d2i2v3t9[.]stackpathcdn[.]com
d4f8s8i9[.]stackpathcdn[.]com
d4p6n2k2[.]stackpathcdn[.]com
d4x5v5y3[.]stackpathcdn[.]com
d9b6m2w5[.]stackpathcdn[.]com
e3r2y5v6[.]stackpathcdn[.]com
e6n6m5w2[.]stackpathcdn[.]com
e7j8k3s8[.]stackpathcdn[.]com
f4i3y4t6[.]stackpathcdn[.]com
f6d4c9p8[.]stackpathcdn[.]com
f6f4p3t9[.]stackpathcdn[.]com
f9c8b5d7[.]stackpathcdn[.]com
g2d4n7b2[.]stackpathcdn[.]com
g4k3t3m4[.]stackpathcdn[.]com
g5c9z2i2[.]stackpathcdn[.]com
g5t9r7y3[.]stackpathcdn[.]com
g5z9x5e4[.]stackpathcdn[.]com
h6j7v2n3[.]stackpathcdn[.]com
h7j4x7z8[.]stackpathcdn[.]com“
h7j4x7z8[.]stackpathcdn[.]com
h7r7m4v7[.]stackpathcdn[.]com
i2p8s4r3[.]stackpathcdn[.]com
i3h5k7b7[.]stackpathcdn[.]com
i4h3k4s6[.]stackpathcdn[.]com
i8w8n4d7[.]stackpathcdn[.]com
i9n5z4q2[.]stackpathcdn[.]com
j3j4e7b4[.]stackpathcdn[.]com
j5a4s9g2[.]stackpathcdn[.]com
j7s7b2r9[.]stackpathcdn[.]com
k3a7e8k4[.]stackpathcdn[.]com
k4p5j5a7[.]stackpathcdn[.]com
k4s2n9w9[.]stackpathcdn[.]com
k4s2y2j4[.]stackpathcdn[.]com
k4z5u6h8[.]stackpathcdn[.]com
k5c2j4v6[.]stackpathcdn[.]com
k6n5u8e5[.]stackpathcdn[.]com
k9g2w7s9[.]stackpathcdn[.]com
m3r3t6c8[.]stackpathcdn[.]com
m4v5h7d8[.]stackpathcdn[.]com
m6j9g5t6[.]stackpathcdn[.]com
m7c8r9u6[.]stackpathcdn[.]com
n3v5m2g8[.]stackpathcdn[.]com
n5s9f4w2[.]stackpathcdn[.]com
n7a8p7i6[.]stackpathcdn[.]com
n8u7v5y9[.]stackpathcdn[.]com
p4d2t2k3[.]stackpathcdn[.]com
p5g8e7k3[.]stackpathcdn[.]com
p6x9i4n9[.]stackpathcdn[.]com
p7n3p2v5[.]stackpathcdn[.]com
p7p5x6n6[.]stackpathcdn[.]com
p8r8c4j3[.]stackpathcdn[.]com
p9a6a3m4[.]stackpathcdn[.]com
q2i8u2c3[.]stackpathcdn[.]com
q4v2f3i9[.]stackpathcdn[.]com
q5g9u9e2[.]stackpathcdn[.]com
r2m7f5q2[.]stackpathcdn[.]com
r6t7n6e6[.]stackpathcdn[.]com
r9g5z5h7[.]stackpathcdn[.]com
s6h6b8v7[.]stackpathcdn[.]com
s7z2s5d8[.]stackpathcdn[.]com
s9f4f2w8[.]stackpathcdn[.]com
t6q9p3i3[.]stackpathcdn[.]com
t8y3t7p8[.]stackpathcdn[.]com
u5y6h8c5[.]stackpathcdn[.]com
u6z2m2f8[.]stackpathcdn[.]com
u9i3m7v3[.]stackpathcdn[.]com
v2a4u6k7[.]stackpathcdn[.]com
v2h6y6a2[.]stackpathcdn[.]com
v3p8b7e8[.]stackpathcdn[.]com
v7z9s3n4[.]stackpathcdn[.]com
v9u5y7v7[.]stackpathcdn[.]com
w2e2t2w8[.]stackpathcdn[.]com
w3n9g9u2[.]stackpathcdn[.]com
w5g2q7h9[.]stackpathcdn[.]com
w6h4i9z2[.]stackpathcdn[.]com
w6m3b5j2[.]stackpathcdn[.]com
w6w7g8s5[.]stackpathcdn[.]com
x3n4x7b6[.]stackpathcdn[.]com
x4d8p9y6[.]stackpathcdn[.]com
x5x4p3x2[.]stackpathcdn[.]com
y2d7s2v4[.]stackpathcdn[.]com
y2k3z7v8[.]stackpathcdn[.]com
y3m5w4d6[.]stackpathcdn[.]com
y4j4p9m5[.]stackpathcdn[.]com
y4x5u9z7[.]stackpathcdn[.]com
y8e7p3a2[.]stackpathcdn[.]com
Z2t6c7e8[.]stackpathcdn[.]com
dvjqy1l7irdg2[.]cloudfront[.]net
d1s98hip5j3dzq[.]cloudfront[.]net
dxes4wias20ld[.]cloudfront[.]net
system-016-019er[.]azurewebsites[.]net
dvjqy1l7irdg2.cloudfront[.]net
d1npxgc1ym10zi.cloudfront[.]net
daz2h6cu9chu5.cloudfront[.]net
dhv4m5g45rhzm.cloudfront[.]net
dhv4m5g45rhzm.cloudfront[.]net
d17gt83l4396ww.cloudfront[.]net
d2czbgohmm4jte.cloudfront[.]net
dc4gtt6hwb29v.cloudfront[.]net
d3tqm3ifwns1ys.cloudfront[.]net
d290dgxafonnb2.cloudfront[.]net
d290dgxafonnb2.cloudfront[.]net
dxes4wias20ld.cloudfront[.]net
d1s98hip5j3dzq.cloudfront[.]net
d22ygrrc38hkrz.cloudfront[.]net
d2xw8jklbbms7o.cloudfront[.]net
d9suuq7k5cxv5.cloudfront[.]net
d5wsdimfszkh7.cloudfront[.]net
d1wyp227frvq0y.cloudfront[.]net
d1wyp227frvq0y.cloudfront[.]net
d3venglh1axwle.cloudfront[.]net
d1iofhnnxdjpfs.cloudfront[.]net
d1k5bvsoc4ls7g.cloudfront[.]net
d36m63xyh4ddzl.cloudfront[.]net
dsrtpig16ka0u.cloudfront[.]net
d2sf2tbnrq4ee1.cloudfront[.]net
d1lna25xrn3txs.cloudfront[.]net
d1lna25xrn3txs.cloudfront[.]net
d2k4xldwrzpcl6.cloudfront[.]net
d8ff6dcpwrc73.cloudfront[.]net
system-016-019er.azurewebsites[.]net
d3s950tdvueo0u.cloudfront[.]net
d7koosly5i8xd.cloudfront[.]net
d1cnwizaihmuam.cloudfront[.]net
d1cnwizaihmuam.cloudfront[.]net
d3a935gbvv9i1t.cloudfront[.]net
d3s7gvarwikke8.cloudfront[.]net
d3a935gbvv9i1t.cloudfront[.]net
d4ssnazbaufe9.cloudfront[.]net
myhost.azurewebsites[.]net
d2krwo1pciihak.cloudfront[.]net
d29s84im7e11qz.cloudfront[.]net
d1cqy25ntml88s.cloudfront[.]net
djntaquohwi38.cloudfront[.]net
di1wrks6kf5c1.cloudfront[.]net
d1oxyl9wuao13m.cloudfront[.]net
dq01ys2vigll0.cloudfront[.]net
diuwkr9401rev.cloudfront[.]net
d3i6hd9i6bs6lk.cloudfront[.]net
d3i6hd9i6bs6lk.cloudfront[.]net
d3i6hd9i6bs6lk.cloudfront[.]net
d3i6hd9i6bs6lk.cloudfront[.]net
d141pf34ccamjr.cloudfront[.]net
d3hkc3zqrvjduj.cloudfront[.]net
d13amcvd0y6kvh.cloudfront[.]net
d3t5rz53vujl7y.cloudfront[.]net
d141pf34ccamjr.cloudfront[.]net
dupte5fmywc2b.cloudfront[.]net
d1h9jvngrbkyl4.cloudfront[.]net
d10o9ki4n9sy1c.cloudfront[.]net
dxw6mgbtfq3jm.cloudfront[.]net
dxw6mgbtfq3jm.cloudfront[.]net
dez3j3c7r2tt0.cloudfront[.]net
d141pf34ccamjr.cloudfront[.]net
d1h9jvngrbkyl4.cloudfront[.]net
d323tjzb3nohl2.cloudfront[.]net
d30th3psx45zj1.cloudfront[.]net
d47s7ej5iu80z.cloudfront[.]net
dl5bsg279h83v.cloudfront[.]net
d2t0a1c58b5ifz.cloudfront[.]net
d2n76o5zb6lp21.cloudfront[.]net
d1oam0i4lqmspz.cloudfront[.]net
dgghjxq0d3gzd.cloudfront[.]net
d2vh1shpa4ci7r.cloudfront[.]net
d2oio0vs9s6cn1.cloudfront[.]net
dynbq24pi5qnf.cloudfront[.]net
d379y7gyjip5nt.cloudfront[.]net
dfdk2j6seemcx.cloudfront[.]net
d2vt3bt3oujd03.cloudfront[.]net
d2omkunumxblxl.cloudfront[.]net
dn8xm2tt3fpy9.cloudfront[.]net
d1ehxvsz3favh5.cloudfront[.]net
d2pueb2cid01i8.cloudfront[.]net
d38jqv88x3bzbg.cloudfront[.]net
d1o70c9gcm86xj.cloudfront[.]net
d1lm77uhunttqk.cloudfront[.]net
dkpvou8lfwhip.cloudfront[.]net
dyh0akmku6v9q.cloudfront[.]net
d26hi9ipxjdwyc.cloudfront[.]net
d2bvkt1qubd4ol.cloudfront[.]net
d1rilivdcoea7t.cloudfront[.]net
dmg3poul69eqh.cloudfront[.]net
dkpvou8lfwhip.cloudfront[.]net
dyh0akmku6v9q.cloudfront[.]net
dilofomyx4uw4.cloudfront[.]net
d27967fixifls0.cloudfront[.]net
d1ondm4ljw5fzb.cloudfront[.]net
d20ps7y8e22ar9.cloudfront[.]net
d3brzxdcwur04.cloudfront[.]net
d2q9t6nnbmut3u.cloudfront[.]net
d3hi6e7qrysk6w.cloudfront[.]net
d251zkn3dy06cs.cloudfront[.]net
dwc5xl326l6s8.cloudfront[.]net
d35u2ao4itzlxx.cloudfront[.]net
d2pfuyunshlmrl.cloudfront[.]net
dnhzfbsxo98zl.cloudfront[.]net
dspn4doojwp47.cloudfront[.]net
d3anx15vqq5w01.cloudfront[.]net
d2alidbuwemgyw.cloudfront[.]net
d3g81q5s2fetro.cloudfront[.]net
d3n6kqpkepr7ad.cloudfront[.]net
degjd8qw2xx78.cloudfront[.]net
d38jqv88x3bzbg.cloudfront[.]net
d37emy4kyxynzk.cloudfront[.]net
dqhfjar4vxf8a.cloudfront[.]net
d17rbttfj0q87q.cloudfront[.]net
d1aey0jdn5oh3n.cloudfront[.]net
d185b89ftuiw0x.cloudfront[.]net
d180goonl5c54j.cloudfront[.]net
d3llyrc5i1eh01.cloudfront[.]net
d32799u9xst1yc.cloudfront[.]net
d1ad5od27b7p9c.cloudfront[.]net
d39r6o4bbqhcxd.cloudfront[.]net
d1yyr30i5y7ga.cloudfront[.]net
d3622hoalptvjq.cloudfront[.]net
d1xqod8nf0n1dz.cloudfront[.]net
d2it0ixgjsniq4.cloudfront[.]net
d2bvkt1qubd4ol.cloudfront[.]net
dhm4qlcztqc2u.cloudfront[.]net
d180goonl5c54j.cloudfront[.]net
d2bvkt1qubd4ol.cloudfront[.]net
d185b89ftuiw0x.cloudfront[.]net
d26hi9ipxjdwyc.cloudfront[.]net
d1aey0jdn5oh3n.cloudfront[.]net
d2bvkt1qubd4ol.cloudfront[.]net
d32799u9xst1yc.cloudfront[.]net
d39r6o4bbqhcxd.cloudfront[.]net
d1ad5od27b7p9c.cloudfront[.]net
d3llyrc5i1eh01.cloudfront[.]net
d1xqod8nf0n1dz.cloudfront[.]net
d1yyr30i5y7ga.cloudfront[.]net
d1a1tji0jv4o99.cloudfront[.]net
d3622hoalptvjq.cloudfront[.]net
d2it0ixgjsniq4.cloudfront[.]net
d17rbttfj0q87q.cloudfront[.]net
djfdn4a9qb44c.cloudfront[.]net
d287mfv8asl40.cloudfront[.]net
d1f805pqz5jjq4.cloudfront[.]net
d10jhuegotkb9z.cloudfront[.]net
d1g1llahvw7eon.cloudfront[.]net
d3rooaucotq4li.cloudfront[.]net
d16ezrljoq7f6r.cloudfront[.]net
d217vusgqkeci0.cloudfront[.]net
d7uyih4h9rigv.cloudfront[.]net
dhv4m5g45rhzm.cloudfront[.]net
d217vusgqkeci0.cloudfront[.]net
dhv4m5g45rhzm.cloudfront[.]net
d17gt83l4396ww.cloudfront[.]net
d2rsc0u5hhds7k.cloudfront[.]net
d3usi11zhcyxza.cloudfront[.]net
d1wbr4x4hly1kk.cloudfront[.]net
d17gt83l4396ww.cloudfront[.]net
d2rwyouzes8vg.cloudfront[.]net
d1ze6g6kvyye8u.cloudfront[.]net
dtfo351qz10u4.cloudfront[.]net
d1osgpp6ckndrz.cloudfront[.]net
d2u7l1c057ir48.cloudfront[.]net
d2rsc0u5hhds7k.cloudfront[.]net
d1osgpp6ckndrz[.]cloudfront[.]net
d2u7l1c057ir48[.]cloudfront[.]net
dis3xqo8paisj7[.]cloudfront[.]net
drn0q2m4b8up9[.]cloudfront[.]net
d2grucgxlhv8sz[.]cloudfront[.]net
d2grucgxlhv8sz[.]cloudfront[.]net
dulj77frxsm74[.]cloudfront[.]net
drn0q2m4b8up9[.]cloudfront[.]net
d1nrwfoi0sqof2[.]cloudfront[.]net
d1nrwfoi0sqof2[.]cloudfront[.]net
d1nrwfoi0sqof2[.]cloudfront[.]net
d1nrwfoi0sqof2[.]cloudfront[.]net
d2rwyouzes8vg[.]cloudfront[.]net
d1nrwfoi0sqof2[.]cloudfront[.]net
d2rwyouzes8vg[.]cloudfront[.]net
d1q5gw1saja4cj[.]cloudfront[.]net
d1q5gw1saja4cj[.]cloudfront[.]net
d1q5gw1saja4cj[.]cloudfront[.]net
d1q5gw1saja4cj[.]cloudfront[.]net
d1q5gw1saja4cj[.]cloudfront[.]net
dulj77frxsm74[.]cloudfront[.]net
d2atpbfbg516x2[.]cloudfront[.]net
d19hmt4dc6g6u5[.]cloudfront[.]net
d2atpbfbg516x2[.]cloudfront[.]net
d2atpbfbg516x2[.]cloudfront[.]net
d1h3rrrvnva0zy[.]cloudfront[.]net
d2atpbfbg516x2[.]cloudfront[.]net
d1h3rrrvnva0zy[.]cloudfront[.]net
d2el89krvr62f[.]cloudfront[.]net
dlc8n7oyeqz0p[.]cloudfront[.]net
dlc8n7oyeqz0p[.]cloudfront[.]net
d3kl66qjp9hiqm[.]cloudfront[.]net
d1i8smj0qochm0[.]cloudfront[.]net
d3in5t0wf7a86t[.]cloudfront[.]net
d269gswc8w0wrj[.]cloudfront[.]net
dn8l091pp5cve[.]cloudfront[.]net
d3in5t0wf7a86t[.]cloudfront[.]net
dn8l091pp5cve[.]cloudfront[.]net
d4xtoj4o9s7fc[.]cloudfront[.]net
d269gswc8w0wrj[.]cloudfront[.]net
dn8l091pp5cve[.]cloudfront[.]net
d2uxnrruij015u[.]cloudfront[.]net
d2uxnrruij015u[.]cloudfront[.]net
d2uxnrruij015u[.]cloudfront[.]net
d2uxnrruij015u[.]cloudfront[.]net
d3o05tzunfcls0[.]cloudfront[.]net
d3o05tzunfcls0[.]cloudfront[.]net
d2ns6px8dfzdpy[.]cloudfront[.]net
d3k7bmuqniyn38[.]cloudfront[.]net
d3f1hxx5tqh600[.]cloudfront[.]net
d2ns6px8dfzdpy[.]cloudfront[.]net
d2ns6px8dfzdpy[.]cloudfront[.]net
3jvh44nnn4[.]azurewebsites[.]net
dmuof4466xbq5[.]cloudfront[.]net
keygenfound-errorcode4cnnfd[.]azurewebsites[.]net
dtr6tyw7oh0r1[.]cloudfront[.]net
d1zmjjh6ftwsuq[.]cloudfront[.]net
dtr6tyw7oh0r1[.]cloudfront[.]net
dtr6tyw7oh0r1[.]cloudfront[.]net
dtr6tyw7oh0r1[.]cloudfront[.]net
d1zmjjh6ftwsuq[.]cloudfront[.]net
d3f1hxx5tqh600[.]cloudfront[.]net
d3b8rajl9f61v[.]cloudfront[.]net
d91kwochb6rk0[.]cloudfront[.]net
d2x7yfthty5faz[.]cloudfront[.]net
d1m23icv5kygs4[.]cloudfront[.]net




 Retour
Retour 















 Lire le blog
Lire le blog