A Netskope foi reconhecida como líder novamente no Quadrante Mágico do Gartner®™ para plataformas SASE. Obtenha o relatório

Sua Rede do Amanhã
Planeje seu caminho rumo a uma rede mais rápida, segura e resiliente projetada para os aplicativos e usuários aos quais você oferece suporte.

Coloque a mão na massa com a plataforma Netskope
Esta é a sua chance de experimentar a plataforma de nuvem única do Netskope One em primeira mão. Inscreva-se em laboratórios práticos e individualizados, junte-se a nós para demonstrações mensais de produtos ao vivo, faça um test drive gratuito do Netskope Private Access ou participe de workshops ao vivo conduzidos por instrutores.

Líder em SSE. Agora é líder em SASE de fornecedor único.
A Netskope estreia como líder no Quadrante Mágico™ do Gartner® para Single-Vendor SASE

Protegendo a IA generativa para leigos
Saiba como sua organização pode equilibrar o potencial inovador da IA generativa com práticas robustas de segurança de dados.

Prevenção Contra Perda de Dados (DLP) Moderna para Leigos
Obtenha dicas e truques para fazer a transição para um DLP fornecido na nuvem.

Compreendendo onde estão os riscos
O Advanced Analytics transforma a maneira como as equipes de operações de segurança aplicam insights orientados por dados para implementar políticas melhores. Com o Advanced Analytics, o senhor pode identificar tendências, concentrar-se em áreas de preocupação e usar os dados para tomar medidas.

Os 6 casos de uso mais atraentes para substituição completa de VPN herdada
O Netskope One Private Access é a única solução que permite que o senhor aposente sua VPN definitivamente.

A Colgate-Palmolive protege sua “propriedade intelectual "” com proteção de dados inteligente e adaptável

Netskope obtém alta autorização do FedRAMP
Escolha o Netskope GovCloud para acelerar a transformação de sua agência.

Vamos fazer grandes coisas juntos
A estratégia de comercialização da Netskope, focada em Parcerias, permite que nossos Parceiros maximizem seu crescimento e lucratividade enquanto transformam a segurança corporativa.

Netskope Cloud Exchange
O Netskope Cloud Exchange (CE) oferece aos clientes ferramentas de integração poderosas para alavancar os investimentos em toda a postura de segurança.

Suporte Técnico Netskope
Nossos engenheiros de suporte qualificados estão localizados em todo o mundo e têm diversas experiências em segurança de nuvem, rede, virtualização, fornecimento de conteúdo e desenvolvimento de software, garantindo assistência técnica de qualidade e em tempo hábil.

Treinamento Netskope
Os treinamentos da Netskope vão ajudar você a ser um especialista em segurança na nuvem. Conte conosco para ajudá-lo a proteger a sua jornada de transformação digital e aproveitar ao máximo as suas aplicações na nuvem, na web e privadas.

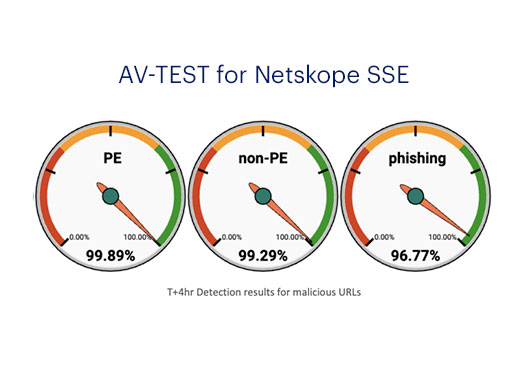
Obtenha valor comercial com o Netskope One SSE
O Netskope One Security Service Edge (SSE) permite que as empresas obtenham um valor comercial considerável ao consolidar serviços de segurança essenciais aos negócios na plataforma do Netskope One




 Voltar
Voltar 

)
)




