Netskope has discovered a malware campaign that takes advantage of multiple cloud apps throughout the kill chain. The campaign, which we have dubbed “CloudSquirrel,” has been in operation since June 2016 and has the intention of stealing and exfiltrating user data within the Outlook address book and, more importantly, usernames and corresponding passwords for email accounts configured in any of the email clients.
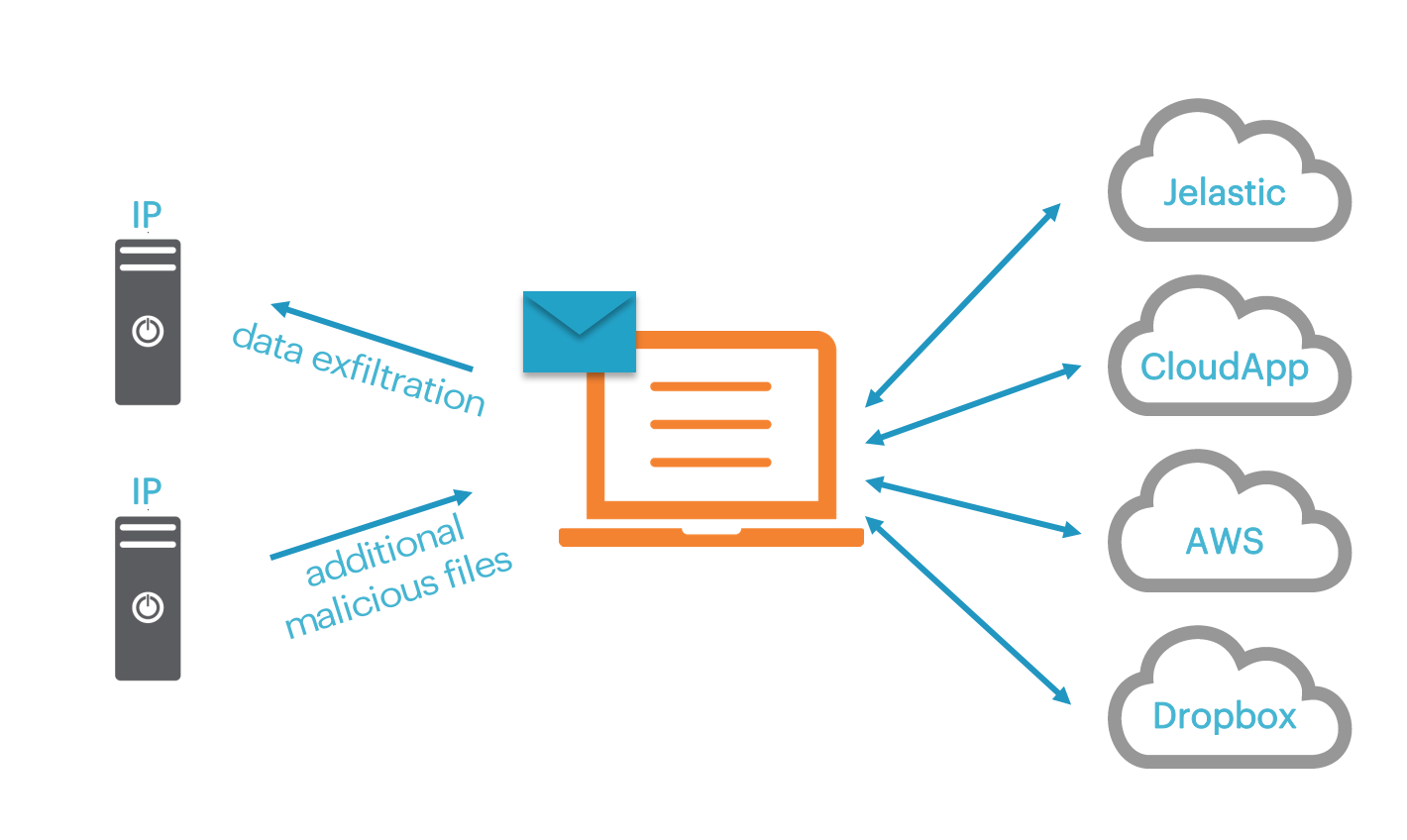
Likely originating in Brazil (based on names and parameters), CloudSquirrel is written in Java and is being distributed using ServInt’s Jelastic platform-as-a-service(PaaS). Jelastic redirects to the CloudApp collaboration platform which, in turn, uses Amazon AWS for its backend cloud services. This cloud malware actively uses Dropbox for its command and control communications.
We have observed the CloudSquirrel attack arriving via an email phishing attack. This attack email attempts to trick its victim into opening it with a “tax invoice” or other important-sounding link. Once open, CloudSquirrel infects users by downloading additional malicious encrypted payloads via a JAR file. Those can include information and password stealers. Once the malware establishes a connection with its command and control hosted in Dropbox, it’s commands masquerade as plain text files with fake extensions like .mp4, .wmv, .png, .dat, and .wma.
At this point, CloudSquirrel receives instructions to find and exfiltrate information both about users’ machines as well as account data such as usernames and passwords configured in native email clients.
Here is the redirect path that CloudSquirrel uses.
Summary Observations
Our observation is that CloudSquirrel and other malware authors are aggressively using cloud applications in various stages of the malware attack kill chain. The CloudSquirrel campaign highlights the use of cloud applications for hosting drive-by-download files and, most importantly, to host command and control configuration data. A significant motivation for malware authors to use cloud applications (especially mainstream ones) is that many enterprises lack visibility into SSL traffic by traditional perimeter security vendors like firewalls and proxies. Enterprises – many of whom need to offer access to popular cloud services – are between a rock and a hard place, and often forced to allow these services in the first place, or at least make exceptions for them if blocked. This makes popular cloud services especially susceptible to use by malicious actors in the malware kill chain.
What Should You Do?
Netskope detects CloudSquirrel and other malware in and en route to cloud services. We recommend doing the following:
- Detect and remediate all malware in sanctioned cloud apps
- Detect and remediate all malware being downloaded from unsanctioned cloud apps
- Actively track usage of unsanctioned instances of trusted cloud apps and enforce cloud DLP policies to control files and data entering and leaving your corporate environment
- Regularly back up and turn on versioning for critical content in cloud apps
- Disable macros in all Microsoft Office programs
- Administrators should block macros by default via a group policy
- Warn users to avoid opening untrusted attachments regardless of their extension or filename
- Keep systems and antivirus updated with the latest releases and patches
We have also worked with the cloud application providers to take down the necessary data related to the malicious user accounts and files. We will be publishing a detailed technical blog on CloudSquirrel soon.




 Atrás
Atrás
















 Lea el blog
Lea el blog