Netskope Threat Research Labs has recently discovered a new technique being used by scammers to reach potential victims: send emails and SMS messages that include links to common services, such as AWS, Azure, Alibaba cloud, and Google Docs. We have seen this technique used for well-known scams, like fake pharmacies, dating sites, and tech support, which seek to steal PII or blackmail victims. This post provides some specific examples of attackers using this technique and explores the reasons why we are seeing it gain popularity.
Tech Support Scams hosted on IaaS Object Storage Services
We have seen tech support scams hosted in Alibaba, AWS, and Azure, with scammers quickly rotating from one object store to another, using seemingly arbitrary names. Figure 1 shows some of the static store URL examples that were hosting these scams at the time of writing. Figure 2 shows an example page hosted at one of these URLs. In this example, a fake Microsoft support page encourages the victim to phone in for support. It would then apply social engineering techniques to gain credit card information. Netskope Advanced Threat Protection detects these attacks as Trojan.Cryxos.1726.
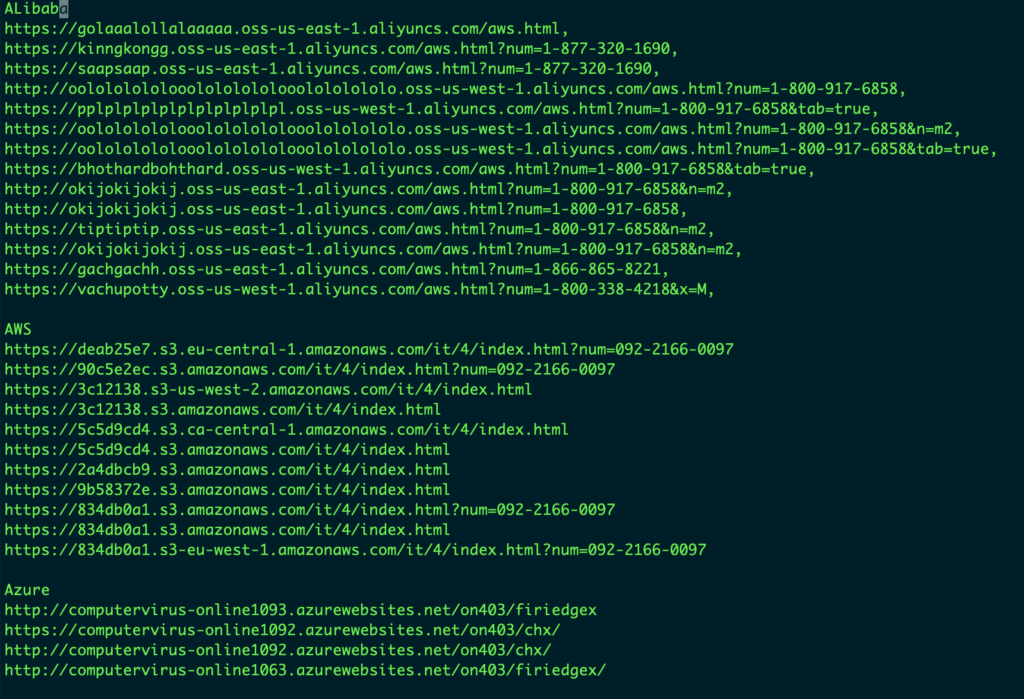
Figure 1: Object store URLs hosting Tech support scamNetskope’s Advanced Threat Protection service detects these attacks as Trojan.Cryxos.1726.
The ease of rapidly switching to new URLs and cheap hosting cost makes services such as Alibaba, AWS, and Azure a viable target for the scammers. The object store names can be randomly generated using a DGA (domain generation algorithm) to make shutting down the scams difficult. Attackers can also use compromised accounts or incorrectly configured object stores to host the payloads.
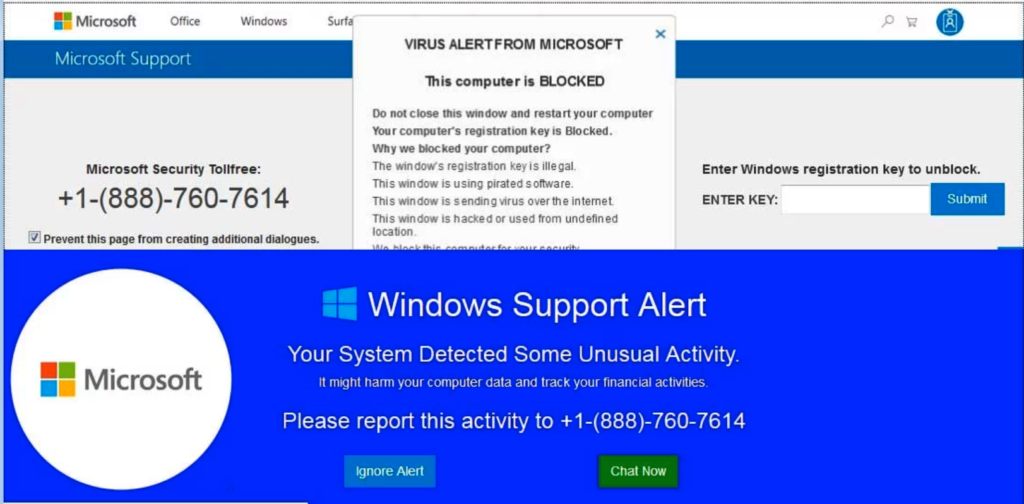
Figure 2: Example of Tech support scam
Use of Google Docs in Smishing and Phishing
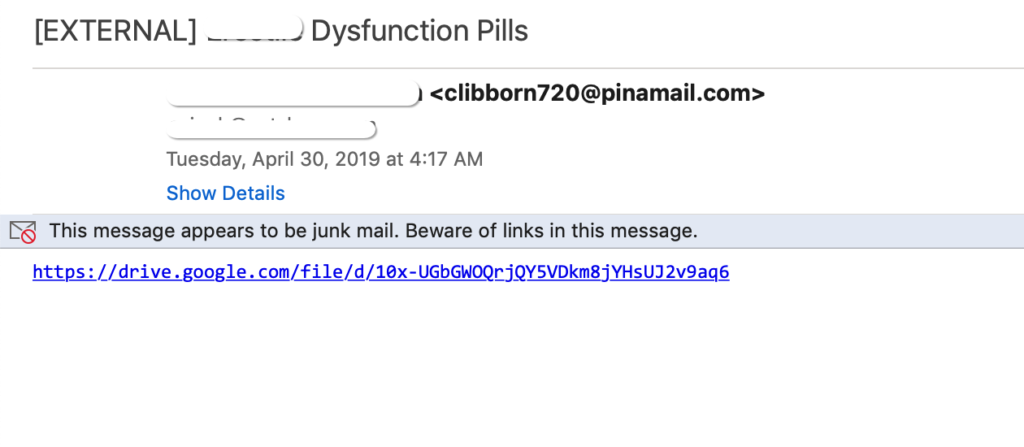
In another example, we noticed scammers abusing Google Docs to create presentations and sharing them through phishing and smishing (SMS text message based Phishing). The presentations serve as a bait to hide a malicious link behind it. Figure 3 shows one such example email and SMS message.
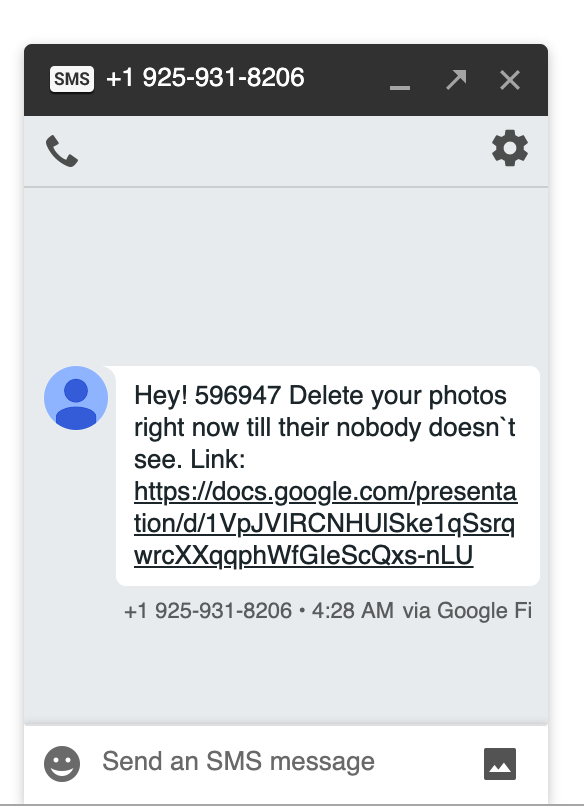
Figure 3: Example of Phishing and Smishing targeting Google Docs.

Figure 3: Example of Phishing and Smishing targeting Google Docs.
Google Docs links help attackers bypass spam filters, which explains their use in phishing emails. Their use in smishing is a bit more curious. Google apps are pre-installed on Android devices and are the most downloaded application in the iOS App store. This means that a Google Docs link on a mobile device likely opens in the native app, where a UX is clean and seamless, and the user might have their guard down. In the examples we have found, the hidden link points to a webpage promising adult content and free dating service. It then asks users to share their information like email and credit card details to validate that they are above the age of 18. Figure 4 shows the difference between the link when viewed on a desktop vs. a mobile device. On the mobile device, the fact that a link is embedded is less obvious.
Why the popularity?
We see three primary reasons for the growing popularity of cloud services for common scams:
Cheap, dynamic hosting
Using Google Drive, AWS, Azure, Alibaba, or any other number of cloud applications give the attackers flexibility to move elsewhere when their links are taken down. Using compromised accounts and open objects stores makes this even more cost effective.
Bypass traditional content filters
Embedding links to trusted services helps attackers bypass traditional content filters, such as spam filters, which might otherwise block the scams.
Looks convincing to the victim
sServices like Google Drive and AWS don’t raise the same red flags as traditional malicious links. Furthermore, the mobile documents make it easier for the attacker to disguise malicious links as legitimate content.
Netskope Protection Stance
Netskope Threat Protection detects the tech support scams as Trojan.Cryxos.1726.
Netskope can also restrict users from accessing external, untrusted Google Docs (and other similar apps), as shown in Figures 5 and 6 below. Netskope also prevents users from unintentionally saving or resharing malicious content
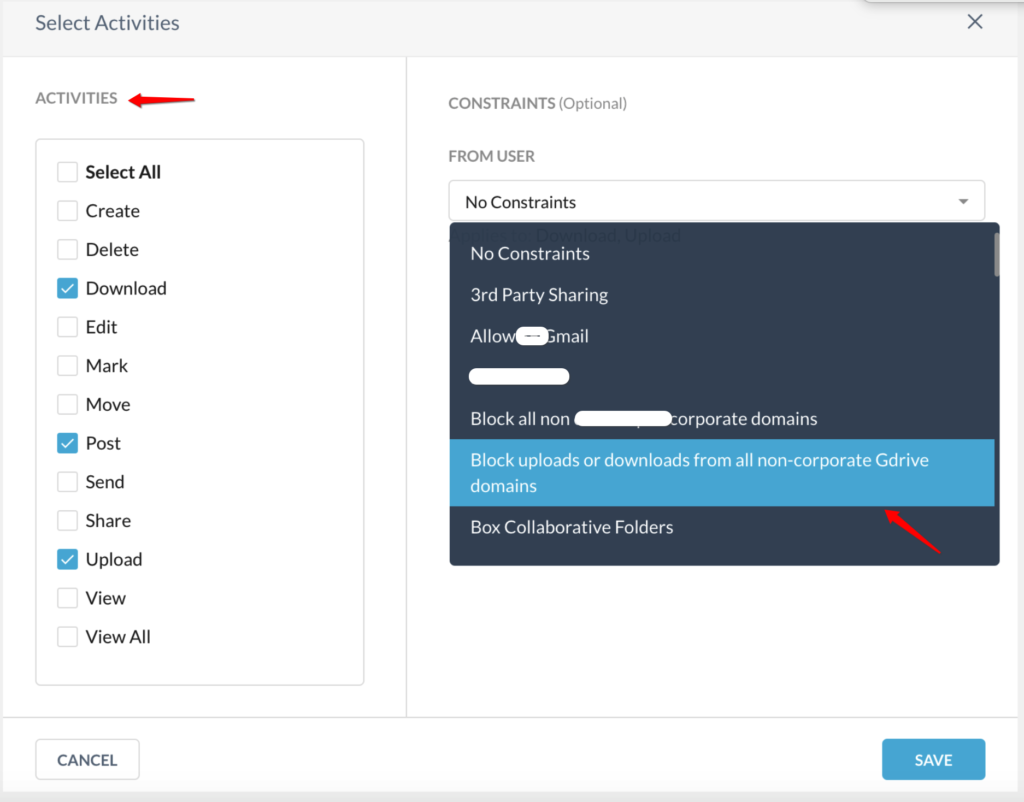
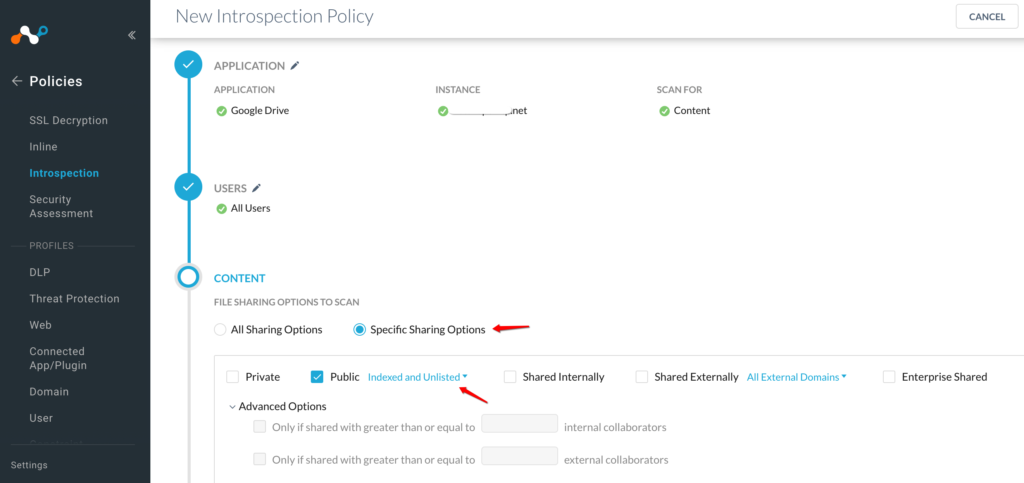
Figure 6: Netskope Policy builder to restrict access to certain files for SaaS applications
Conclusión
Scammers adopting cloud services was inevitable — it provides them scale, helps them avoid content filtering, and gives them a new channel where users might have their guard down. While currently only being used for long-running scams targeting individuals, these techniques could also be used to target business who use services such as Google Drive. We should begin educating users and putting controls in place to protect ourselves against the onslaught of attackers abusing cloud services.




 Back
Back 






















 Lea el blog
Lea el blog