The Netskope Internal Security Internship Program started in May of 2019 with four interns. As this program has evolved we have partnered with two different universities that offer a co-op program (Maryville University and University of Advancing Technology), allowing students to spend two college terms with Netskope while earning academic credit hours. Our interns gain invaluable hands-on experience, mentoring, and guidance learning about what a world-class global security program entails, led by Netskope CISO, Lamont Orange. In this program, our interns complete a rotation through many domains, which include:
- Cyber Operations and Incident Response
- Governance, Risk, & Compliance (GRC)
- Architecture
- Business Information Security Engineering
- CSIRT/PSIRT
- Application Security
- and more!
Our interns also get exposure to engineering, operations, ethical hacking, and project management. This helps each student learn what area of cybersecurity they truly are interested in and passionate about.
Netskope has hired over 50% of all internal security interns to date! And we have helped place over 85% of our interns with full time jobs!
Some Netskope interns have also made valuable contributions, such as improving DLP engine efficacy, working with the CTO’s office, creating an Advanced Analytics dashboard for insider threats, and automation in GRC that helped the team scale and meet revenue support targets, to name a few.
Here’s a recent success story from the program:
One of our recent interns, Allen Funkhouser, successfully completed our internship program and earned his Bachelor’s degree in Cybersecurity in April 2022 from Maryville University. During his internship at Netskope, he learned a lot! But the most helpful thing he learned was how cybersecurity departments operate within an organization. Some of the best advice Allen was given during his internship came from Netskope security engineer Todd Khatinha, “Everything is hard until you do it.”
When Allen began his rotation learning about attack surface management he analyzed our current Threat and Vulnerability Management (TVM) workflow. After doing this workflow he realized there was an area for improvement, which would help Netskope expand and automate the enumeration workflow of TVM. Allen was given the opportunity to present the current Netskope workflow and a solution to automate this workflow process. From there, he was encouraged to follow through with building out this automation.
Through Allen’s research, he found that Censys provided attack surface management by scanning externally exposed assets and reporting on suspected vulnerabilities. Project Viper, Allen’s project on workflow automation, is a script framework that performs vulnerability scanning, password testing, and ticket generation based on the Censys scan results to enhance Netskope attack surface management. This now saves our analysts time by increasing efficiency and strengthens our security posture by finding vulnerabilities and weak passwords.
Initial Project Viper Workflow
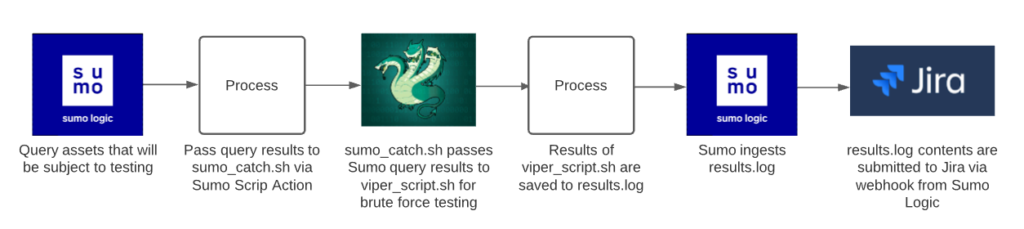
New/Current Workflow

At the end of Allen’s co-op internship with Netskope, we were very impressed with the work that he did as an intern, so we offered him a job! Allen is now a Netskope Security Analyst. The Netskope cybersecurity team truly loves seeing students grow and develop their passion for this industry. Netskope is able to give them opportunities through our co-op to not only experience the different avenues of cybersecurity but also get one-on-one mentorship and guidance through this program. Do you know a student that might be interested in the Netskope Internal Security Internship program? If so, please reach out to me, Erica McMillen, at [email protected], as I am running the logistics for this program.
Additionally, what are some practical things that have worked for you in your company’s internship program? I would love to have a conversation about where to start or how to further develop your program.




 Retour
Retour
















 Lire le blog
Lire le blog