The common theme across ransomware, insider threats, and data theft is the exfiltration of data. While threat research labs usually publish the process steps of ransomware encryption, keys, and disk clean-up, the parts about accessing the data and exfiltration are often left out. Also, one security solution does not solve the problem itself, making partner integrations vital to the success of security solution stacks. Using the perspective of access and security posture, data protection and policy controls, threat protection, and analytics we can analyze these four pertinent security issues.
First, for access and security posture we know compromised remote access accounts (SSH, RDP, VPNs) are sold in the underground to enable ransomware operations. Netskope Threat Labs (NTL) research shows that 35% of IaaS/PaaS workloads are publicly exposed when the default posture is closed and secure. Enabling Zero Trust Network Access (ZTNA) to increase remote access security, plus federating SSO/MFA to apps and cloud services greatly reduces risk exposure. Adding cloud and SaaS security posture management (CSPM, SSPM) is an easy API-based deployment to add security and configuration checks, plus compliance validation.
Second, for data protection policy controls, NTL research notes a 300% increase in data exfiltration from company app instances to personal app instances in the last 30 days of employment, with 74% of this data flow specifically into personal Google Drive instances. So, your office reopening announcement may spur some of this data exfiltration activity as employees seek new jobs favoring their preferences for continued remote work. Plus, the data flows occur not just when employees are exiting. On average, a user on a managed device copies 20 company files to personal apps per month with source code being the third most popular file type exfiltrated. This makes data protection policy controls between company and personal instances of popular cloud storage apps extremely vital in your security stack. But it’s a capability most legacy allow/deny security defenses lack.
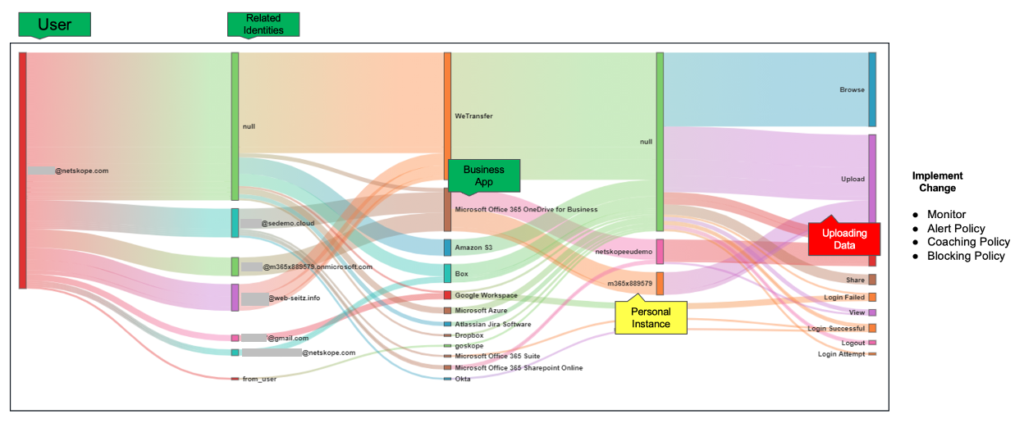
Third, for threat protection, NTL research notes 68% of malware is cloud-delivered, more specifically from personal or rogue app instances of cloud storage apps. While the enterprise-grade version may include malware and ransomware defenses for company-managed apps, the reality is the great unwashed mass of free and personal instances are the primary culprit. While inline defenses for web and cloud traffic inclusive of app instances are required, missing over two-thirds of malware delivery is unacceptable. To further reduce risk exposure, use remote browser isolation (RBI) for risky websites, cloud firewall egress controls on ports and protocols to block exfiltration paths, and leverage behavior analytics to detect anomalies for logins, data activity (bulk downloads, uploads, deletes), company to personal instance data flows, and rare events.
Fourth, with analytics, we can detect unknown data flows and exfiltration given our inline capabilities provide extensive app and cloud visibility and control. We can also see the use of risky apps often freely adopted by business units and users as 97% or more of apps are not IT managed and an average-sized company has more than 800 distinct apps. Reducing the duplication of cloud storage apps and understanding how company data flows into personal instances is key with analytics. This enables a closed-loop process to upgrade and mature policy controls using analytics with real-time coaching to users in alerts and recommending safer alternatives to migrate away from risky activities and apps.
As stated at the beginning, partner integration is key to success here as no one solution solves these issues alone. Netskope provides integration tools with the Cloud Exchange platform at no extra charge to customers in the following ways:
- Cloud Threat Exchange (CTE) enables automated bi-directional IOC sharing within a customer security stack, for example between Netskope and CrowdStrike for the latest ransomware intelligence.
- The Cloud Risk Exchange (CRE) enables the sharing of risk ratings between solutions, for example, Netskope user risk ratings (UCI) or CrowdStrike zero trust assessment scoring for endpoints.
- The Cloud Ticket Orchestrator (CTO) automatically creates service tickets from Netskope alerts within IT service management and collaboration tools including ServiceNow, Jira, PagerDuty, and Slack to automate response workflows.
- For investigation details, the Cloud Log Shipper (CLS) exports Netskope logs to desired SIEMs and data lakes to enable security operations or XDR/MDR services.
The broader perspective across access and security posture, threat and data protection, analytics, and security stack integration is what is required to address ransomware, insiders, and data theft. The narrow perspective also informs us to closely inspect personal app instances for cloud threat delivery and data exfiltration as evidence continues to build making it the high-risk zone.
Learn more in our Cloud Exchange presentation “Leverage the Power of your entire Security Stack with free Cloud Exchange toolset” at SASE Week with David Willis on November 2nd at 2pm for North America and European audiences. For Asia-Pacific and India regions, the presentation is on November 9th at 2pm the following week.




 Retour
Retour 
















 Lire le blog
Lire le blog