Mergers and acquisitions often sound amazing to the Board, but they can become an operational nightmare for the infrastructure, networking, and security teams. In recent years, I’ve worked with a fair few highly acquisitive organisations and so I have seen firsthand that the practical steps to onboard new users can become hugely challenging–especially when the two organisations are running different technologies.
As a Solutions Engineer, one of my roles is to speak to key stakeholders–ranging from CIOs and CISOs to their architect teams–to understand the pain points of an organisation. Throughout these conversations a common question is always asked: “What are other organisations doing to make M&A easy … and what are the practical steps?”
Our approach is to focus on connecting people to applications and data, not devices to networks. That’s a catchy soundbite, but it informs the way we approach the process in very practical ways across in answer to four areas of consideration:
- Due diligence
- Integration planning
- Transitioning from VPN to ZTNA
- Deployment
Below are practical steps that an organisation can take to help smooth the process of an acquisition. I will also provide key considerations in each phase to ensure that achievable objectives are set:
1. Due Diligence Phase
Key Considerations
- Can you ensure sensitive data is properly handled during the due diligence process?
- Can you monitor data transfers between acquirer and acquiree and detect threats, mitigate vulnerabilities, and ensure both companies are aware of attempted attacks?
The key word in this phase is… DISCOVERY. Discovery is essential as part of an overall cloud security strategy but even more so during an M&A. What do I mean by discovery? I mean identifying users, devices, and applications (both private local apps and SaaS/IaaS) within an organisation. This discovery process allows the parent organisation to understand where potential risks may lurk when onboarding acquired users. An example of discovery within a cloud security platform is using a tool that has a rich library of cloud applications and provides contextual insights into each application determining a confidence level. With this data the organisation can easily define a set of sanctioned and unsanctioned applications which is then reflected in a policy to warn users when accessing unsanctioned apps.
2. Integration Planning
Key Considerations
- Can you proactively educate users during the acquisition?
- Can you determine where you have duplicate technologies implemented?
- Can you identify and manage third party integrations?
We’ve all been there, trying to access an application or perform an activity which isn’t permitted within our organisation and receiving a frustrating error message, then having to log a ticket with IT. This can become more of a pain during an acquisition when users aren’t aware of the acceptable usage policy (AUP ) set by the parent company.
Using a tool such as user coaching within the Netskope One platform allows security administrators to create policies and templates which will provide coaching messages to inform and educate the user when they have violated policy (e.g. accessing a personal instance of Google Drive). It also provides the user with an opportunity to enter a justification which can hugely benefit the security admins, as it can help them understand the specific use cases and needs among their new colleagues, as well as significantly reducing the number of tickets logged.
Determining where technologies may be duplicated across the two organisations is another key to achieving a smooth M&A process – especially when we’re talking about software that could either overlap in terms of functionality or conflict when bringing a device into the parent org. For all the aspirational talk of consolidation gains, the reality is that very often security and network teams are not in a position to immediately remove or consolidate all the overlaps they might have in their stack of solutions. Fortunately there are tools available that can leverage the existing investment made without having to compromise on your current architecture. For instance, Netskope Cloud Exchange provides a plug and play solution to enable seamless integrations into technologies such as XDR, SIEM & IAM.
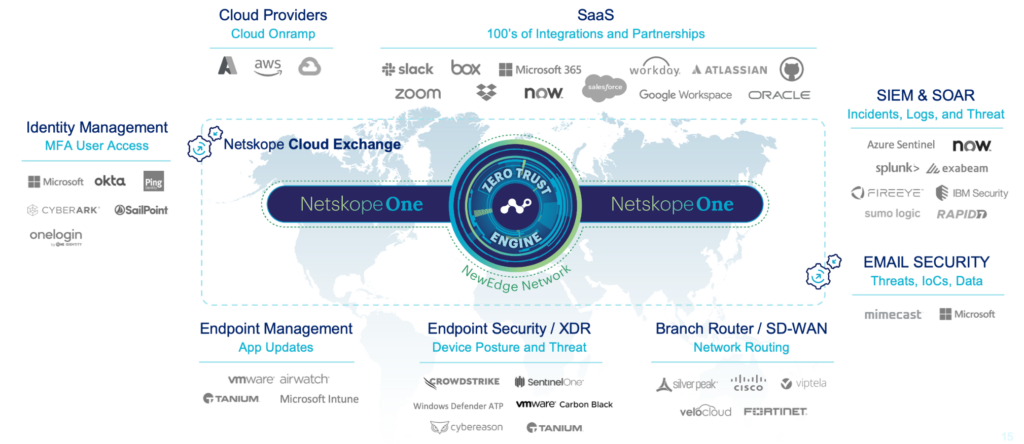
3. Transitioning from VPN to ZTNA
Key Considerations
- Can you efficiently control users’ access to private resources?
- Can you provide seamless network integration to access private applications for both parties?
Zero trust network access (ZTNA) is a hot topic amongst security and networking teams as a result of a number of legacy VPN issues. Alongside the broader questions around the suitability of VPNs, M&As introduce other complexity, such as issues with overlapping networks. Many organisations will run the same Class A or C network ranges but when two organisations are looking to integrate during the acquisition, if both are on the same network range it will either mean a re-architecture or migrating off from one VPN to another which presents its own operational burden.
As ZTNA provides the ability to connect users to applications, and not simply devices to networks, it immediately removes the barrier of overlapping networks and introduces seamless network integration for both parties. As well as eliminating the concern of networks conflicting, the organisation’s security posture is greatly enhanced as security admins can define granular policies to allow users access to specific private resources.
Netskope ZTNA Next meets the promise of a full VPN retirement by combining both ZTNA + Endpoint SD-WAN into the Netskope One Client, modernising connectivity and boosting security. More details can be found here.

4. Ease of Deployment
Key Considerations
- Can you onboard users without interrupting their productivity?
- Can you provide a holistic deployment method across all parties?
One of the biggest challenges in M&A lies in ensuring the seamless deployment of technologies from the parent organisation–with minimal disruption–to facilitate a smooth transition. And the question guaranteed to be asked to any Solutions Engineer is: “How easy is it to deploy your solution?” This question holds broad significance when an organisation is integrating a new solution, yet it carries even more weight in ensuring a seamless implementation of a security platform amidst an M&A.
Fortunately, the unified Netskope One client allows organisations to easily integrate multiple directory services (both from the acquiring and acquired entities) to ensure the software is running from day one. By synchronising various identity sources, security admins can not only establish policies based on user identity (in line with zero trust principles) but also guarantee that the Netskope One Client authenticates the correct user according to the identity parameters set on the endpoint.
Once the Netskope One client is installed, users gain access to sanctioned applications based on the Zero Trust Engine policy configured within the Netskope platform.
Summary
While an M&A can prove to be a challenging time for CIOs and CISOs, the practical steps mentioned in this blog can greatly reduce the exposure of a threat to an organisation and offer a pathway for infrastructure, networking, and security teams to streamline the onboarding process for new entities. All while upholding the essential tenets of zero trust principles.




 Voltar
Voltar
















 Leia o Blog
Leia o Blog