Phishing is a well known threat that users are constantly being warned about, but as we are in Cybersercurity Awarenss Month though, some may still be wondering what exactly phishing is and how to prevent it. In this blog, I am going to dig into how you can recognize phishing and how enabling multi-factor authentication can help keep you safe.
Quick basics on phishing
For those who need a refresher, phishing is a form of social engineering where an attacker tries to trick a user into sharing sensitive information passwords, credit card information, or other sensitive data, by using emails or websites that look like they are coming from a trusted, reputable source.
While phishing is often performed through email, other forms of phishing may occur through different means of communication such as text messages called smishing and voice calling which is called vishing. No matter the medium used, the end goal is the same: tricking the victim into performing an action that allows an attacker to access a person’s computer or sensitive data. Attackers can then use this access to further compromise the victim’s device, or exfiltrate user data to sell or launch additional phishing attacks. Whether it’s through professional or personal communications, phishing attempts will make it to your inbox one way or another, and being aware of the indicators helps protect you from falling victim.
How to recognize and report phishing
The best way to protect yourself from phishing is through awareness, which means reporting suspected phishing when you come across it. Here are a some key indicators to consider when you receive a message you think might be phishing:
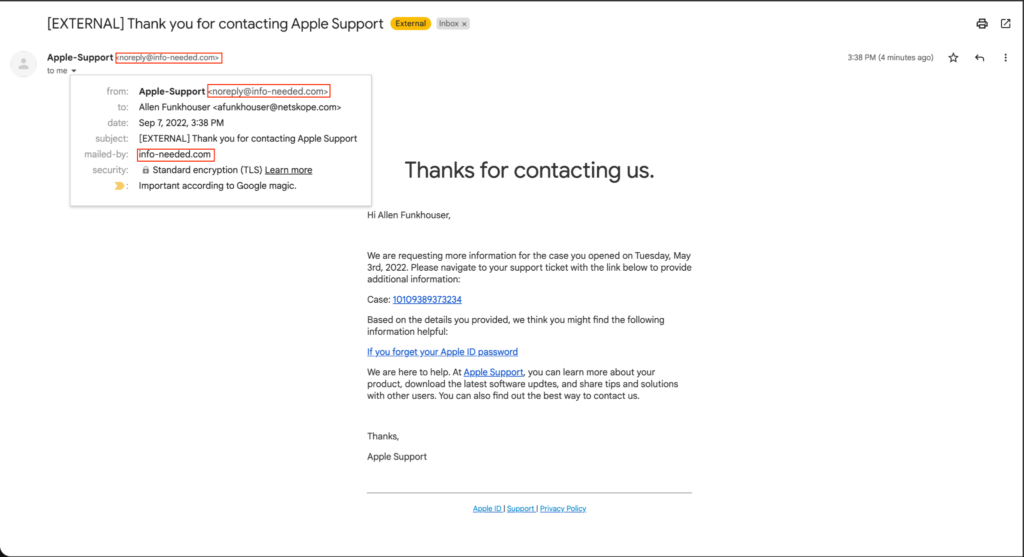
- Is the email expected?
- Do you recognize their email address?
- Does the message contain a sense of urgency?
- Are there errors within the email that shouldn’t be present?
- Is this form of communication normal for the sender?
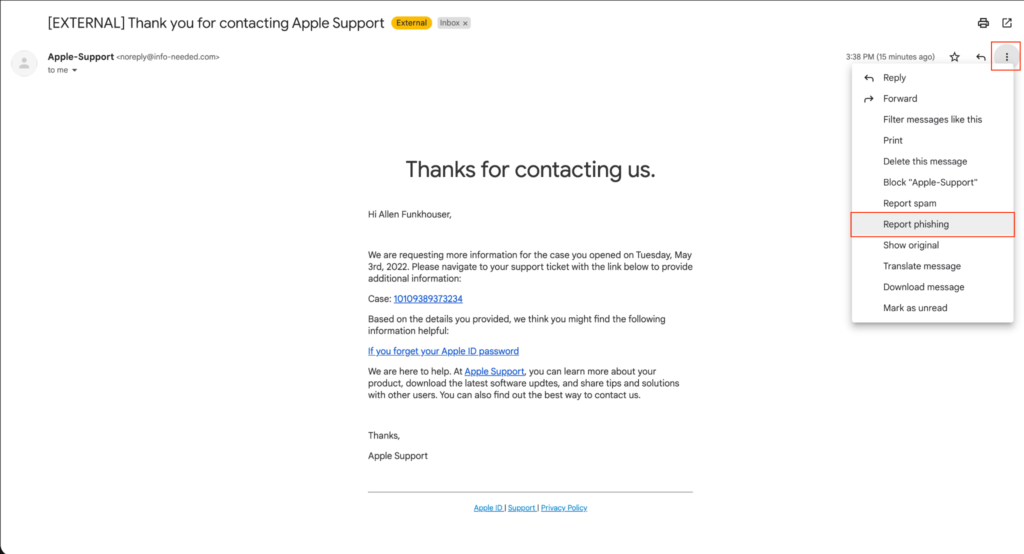
Once you see indicators that a message may be phishing the next step is reporting it. All major email providers allow users to report phishing, whether in a corporate or personal environment. To report a phishing email simply select the “more” tab, typically represented by three dots, then report as phishing. In a corporate setting, this alerts the security team to potential phishing campaigns being deployed against the company. Outside of a business setting, reporting lets the email provider know and allows them to better detect future phishing campaigns.
Multi-factor authentication makes a difference
Multi-factor authentication is also a helpful tool when it comes to protecting yourself from phishing, as it requires you to authenticate your identity in additional ways, beyond just a password, to access your accounts. As a result, multi-factor authentication can be a reasonable second line of defense against phishing. If a person falls victim and gives the attacker their credentials, there is a second barrier that the attacker must get through. However it is worth noting that while multi-factor authentication should always be enabled, attackers can also phish a person for the multi-factor authentication code, so users should always stay alert when being contacted for ways into their accounts.
It’s human nature to want to trust the people you’re communicating with on and offline, but phishing and social engineering inherently preys on this trust. As good digital citizens, we need to pause and think about the message we receive and ask, Does the context around this message make sense? Have you received this kind of message before? Does something seem off about it? Typically any of these warning signs warrant further investigation. Anyone can email, call, or text you, but it is up to you to verify the legitimacy of a message before providing any potentially sensitive information.
Keep an eye out for other Cybersecurity Awareness Month blogs from my colleagues Sean Salomon and John Khotsyphom.




 Atrás
Atrás
















 Lea el blog
Lea el blog