Be the first to receive the Cloud Threats Memo directly in your inbox by subscribing here.
Dark Pink (also known as Saaiwc Group) is an advanced threat actor that has been operating since mid-2021, mainly in the Asia-Pacific region and to a lesser extent in Europe, leveraging a range of sophisticated custom tools within a sophisticated kill chain relying on spear-phishing emails. The group has been quite active since 2021, attacking at least 13 organizations in Vietnam, Bosnia and Herzegovina, Cambodia, Indonesia, Malaysia, Philippines, Belgium, Thailand, and Brunei.
A recent analysis by researchers at Group-IB has shed light on the new victims, and the new tools and techniques deployed by the advanced threat actor. In particular, the kill chain starts with a spear-phishing email delivering an ISO disk image containing several items including a signed file, a decoy document, and a malicious DLL. When the decoy document is open, it ends up installing KamiKakaBot, a tool designed to read and execute commands from a threat actor-controlled Telegram channel. The tool also uses a Telegram chat as a drop zone to exfiltrate data, and this aspect represents a change compared to the previous attack chain where the data was exfiltrated using email or publicly available cloud services such as DropBox.
But if DropBox is not part of the latest attack chain, there is another well-known cloud service that played an important role in the recent campaigns: GitHub is exploited by the attackers along with TextBin.net, an additional less-known cloud service, to host additional payloads used during the attack chain.
GitHub is a very flexible cloud service that is being increasingly exploited by state-sponsored threat actors, and this is just the latest example. Despite this, Dark Pink has not been tied to any country or known group in particular.
How Netskope mitigates the risk of legitimate cloud services exploited by threat actors
GitHub (and Dropbox) are just two of the thousands of cloud services, where the Netskope Next Gen SWG can provide granular access control, threat protection, and DLP capabilities, and also two of the hundreds of apps for which instance detection is also available.
To give you an idea of the difference between Netskope Next Gen SWG and a legacy SWG, in the case of GitHub the app connector is able to recognize and govern the following activities: “Create”, “Delete”, “Download”, “Edit”, “Login Attempt”, “Login Failed”, “Login Successful”, “Logout”, “Share”, “Upload”, “View”, “Invite”, and “Post”. DLP and Threat Protection can be applied to “Download and Upload”, whilst “Create”, “Edit”, and “Post”, support DLP. That’s definitely much more than a simple “Allow” or “Block”.
Similarly, in the case of Dropbox, the Next Gen SWG has visibility of the following activities: “Create”, “Delete”, “Download”, “Edit”, “Login Attempt”, “Login Failed”, “Login Successful”, “Logout”, “Share”, “Unshare”, “Upload”, “View”, “View All”, “Invite”, “Post”, “Rename”, and “Preview”. Similarly, DLP and Threat Protection can be applied to “Download and Upload”, whilst “Create”, “Edit”, and “Post”, supports DLP.
And in the case of TextBin.net (and in general other less familiar cloud services potentially exploited by attackers)? By default this domain belongs to the “Utilities” category, but if a more granular control is needed, it is possible to build a custom app in a few seconds (the domain is the only information needed) and govern the following activities: “Download”, “Upload”, “Login Attempt”, “Login Failed”, “Login Successful”, “Logout”, “FormPost” with “Download and Upload” that support both DLP and Threat Protection, and FormPost that additionally supports DLP.
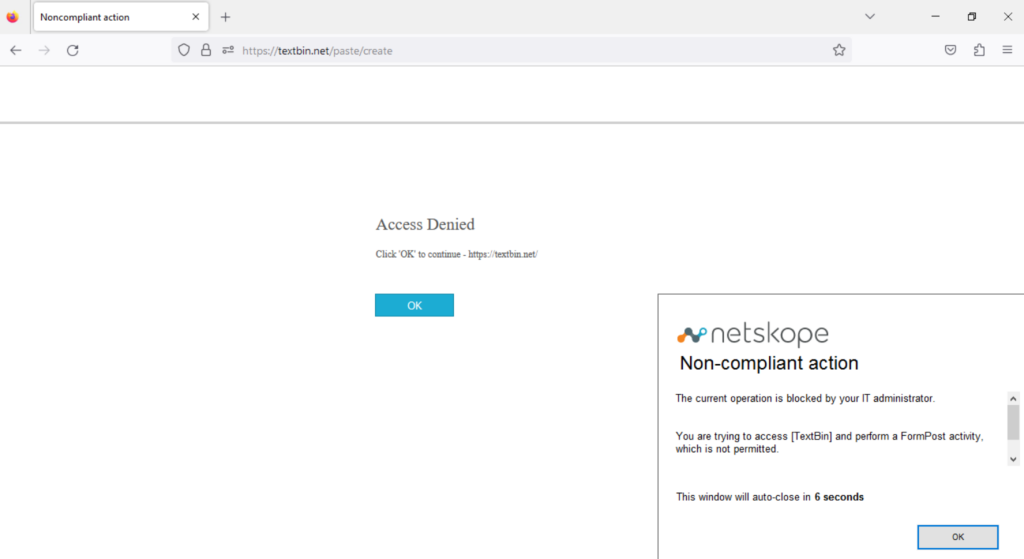
Organizations might decide to completely block access to the unneeded cloud storage service, or simply prevent specific, potentially dangerous activities (such as “Download” or “Upload”).
For services like DropBox or GitHub where instance detection is also available it is possible to configure a policy that prevents potentially dangerous activities and apply it to non-corporate instances only. This is especially helpful if either app is exploited as a command and control or a malware distribution point.
Netskope customers are also protected against malware distributed from a legitimate cloud service and the web in general by Netskope Threat Protection. Netskope Threat Protection scans web and cloud traffic to detect known and unknown threats with a comprehensive set of engines, including signature-based AV, machine learning-based detectors for executables and Office documents, and sandboxing, including patient zero protection.
Netskope Cloud Exchange provides powerful integration tools to leverage investments across users’ security posture through integration with third-party tools, such as threat intelligence feeds and endpoint detection technologies.
Finally, Netskope Advanced Analytics provides specific dashboards to assess the risk of rogue cloud instances being exploited to deliver malware or the risk of becoming the target of anomalous communications, with rich details and insights, supporting security teams in the analysis and mitigation/remediation process.
Stay safe!




 Retour
Retour
















 Lire le blog
Lire le blog