A new cloud phishing campaign is abusing Microsoft Azure’s Static Web Apps service to steal credentials from multiple services including Microsoft 365, Outlook, and Yahoo Mail.
Hosting phishing pages on Azure is not a novelty, however, the Static Web Apps service lets attackers build and deploy static or dynamic web apps on Azure from external repositories like GitHub which, in turn, allows them to build convincing landing pages like the one shown in the example below. This aspect, combined with the fact that hosting the landing page on Azure means that the victim is presented with a legitimate and familiar URL (*.1.azurestaticapps.net) and an equally legitimate certificate signed by Microsoft, makes the chance of a successful attack much higher.
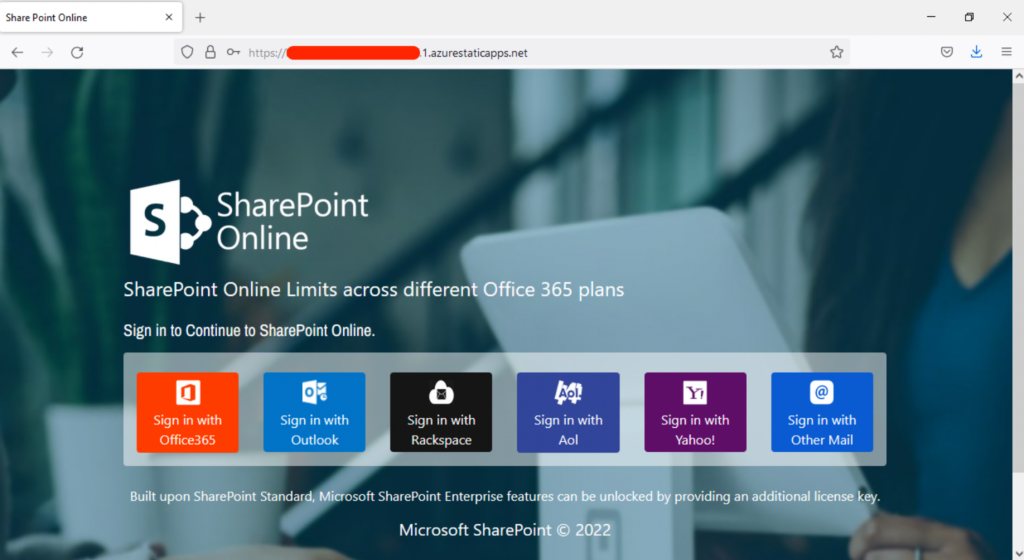
How Netskope mitigates the risk of cloud phishing
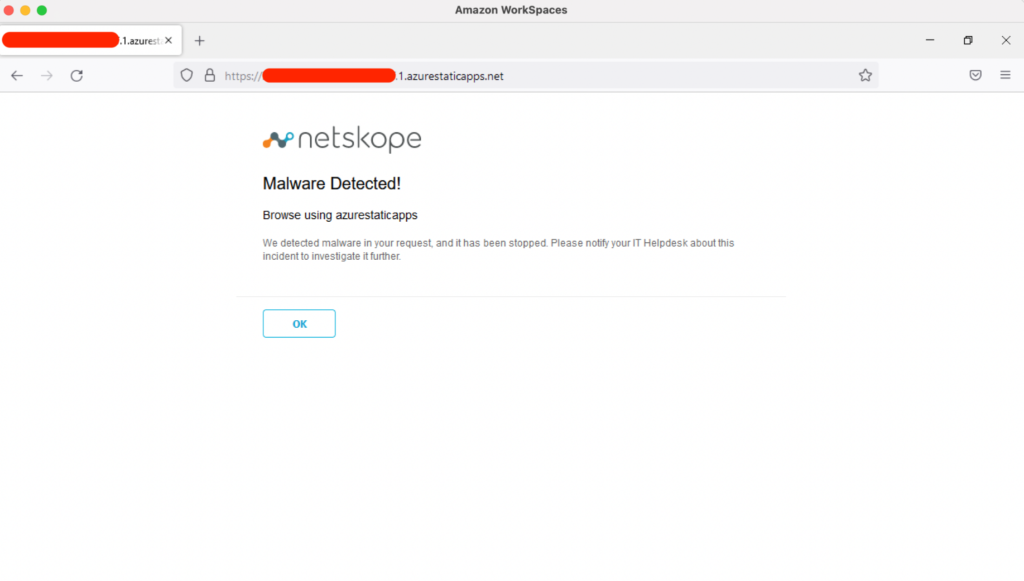
Netskope Threat Protection, a core component of the Next Gen Secure Web Gateway, is the first line of defense. The landing page shown above is known and detected by Netskope threat intelligence in the “Security Risk – Phishing/Fraud” category, even if it’s hosted in Azure, so any attempt to browse it is immediately blocked even before the user can select the fake service to log in. Additionally, the on-browser Netskope AV detects the static HTML page as ”JS:Trojan.Cryxos.8405.”
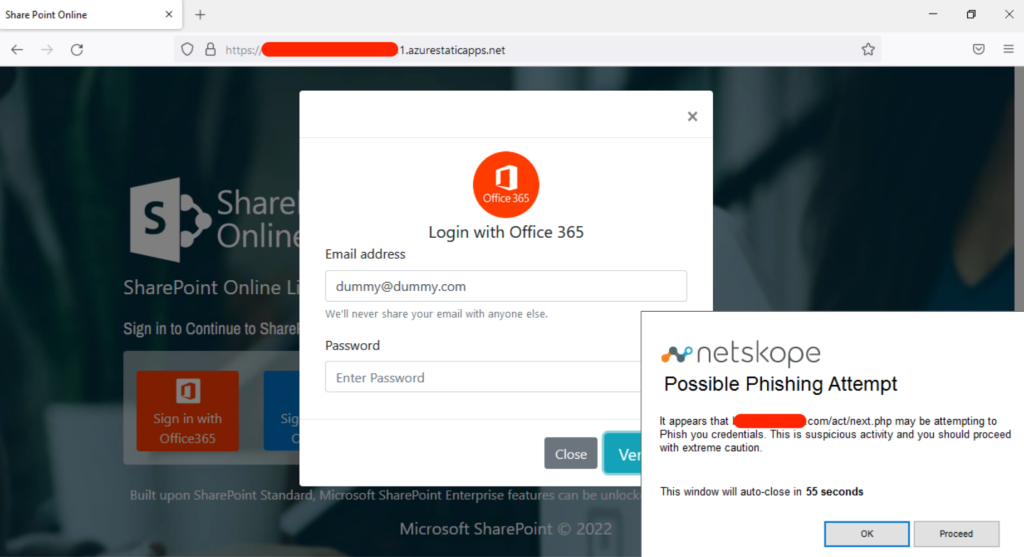
Another layer of protection is provided by the Netskope DLP engine which scans the FormPost activity preventing the submission of corporate credentials (an identifier as simple as the corporate email domain may suffice provided the needed exceptions for corporate apps are in place). In the above example (after disabling the threat protection policy just for the purposes of this illustration), the submission of a corporate credential on the phishing page is prevented (note that the landing page hosted in Azure redirects the victim to an external domain).
A specific threat dashboard of Netskope Advanced Analytics allows real-time monitoring of the risk exposure of the organization, and identification of the most risky apps and the most targeted users, ultimately supporting the incident response and remediation process.
Stay safe!




 Voltar
Voltar
















 Leia o Blog
Leia o Blog