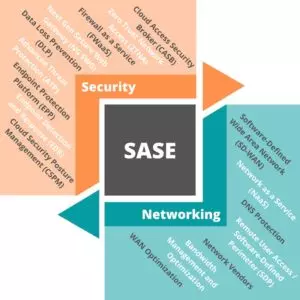
Secure Access Service Edge (SASE), pronunciado "sassy", es una arquitectura basada en la nube que ofrece servicios de red y seguridad destinados a proteger a los usuarios, las aplicaciones y los Datos.
Este término fue acuñado por Gartner en 2019 y ha ascendido rápidamente hasta convertirse en uno de los principales conceptos de seguridad aspiracionales de la década actual hasta ahora. Dado que muchos usuarios y aplicaciones ya no viven y operan en una red corporativa, el acceso y las medidas de seguridad no pueden depender del hardware convencional Appliance en el centro de datos corporativo.
La seguridad de SASE promete brindar las capacidades de red y seguridad necesarias en forma de servicios en la nube. Realizado correctamente, un modelo SASE elimina los dispositivos basados en el perímetro y las soluciones heredadas. En lugar de enviar el tráfico a un dispositivo por motivos de seguridad, los usuarios se conectan al servicio en la nube de SASE para acceder y utilizar de forma segura los servicios web, las aplicaciones y los datos con la aplicación constante de la política de seguridad.
¿Dónde está el borde («edge») en el Secure Access Service Edge?
El borde o perímetro («edge») en SASE se refiere a los sistemas globales del proveedor de nube que existen en su hardware (centros de datos y dispositivos). Los usuarios acceden a servicios en la nube iniciando sesión y autenticando su identidad, desde cualquier lugar, y atraviesan este borde para acceder al entorno de la nube.

Libro blanco: SASE y las siete fuerzas que conforman la transformación de la seguridad
Blog: El punto de vista de un CISO sobre SASE




 Atrás
Atrás



















 Lea el blog
Lea el blog
