What is software supply chain and its security?
Software supply chain is anything and everything that contributes to making software functional. This includes code in the developer system, the CICD pipeline, dependencies, binaries, and deployed software in production, as well as people, processes, and the technology space.
With the growing adoption of assembling software from distributed, unmanaged components rather than building it from scratch, more often than not, organizations are not aware whose, or what, code is running within their software. With the ever-growing complexity of the supply chain to deliver software, keeping software secure is becoming more and more challenging.
Netskope methodology
To address this growing issue around software supply chain security, the Netskope internal security team utilizes ReversingLabs’ Software Supply Chain Verification Solution to assess the security posture of client components of the Netskope platform.
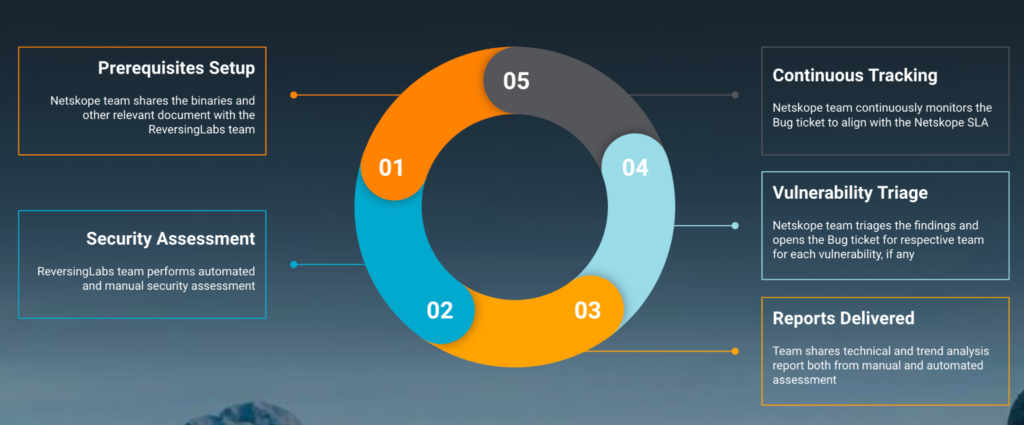
As depicted above, with every major release of the Netskope product suite, we follow a five-step process in a circular way.
- Prerequisites Setup – The Netskope team shares the binaries, testing environment, and other relevant documents with the ReversingLabs team.
- Security Assessment – The ReversingLabs team performs automated and manual security assessment. Here are some additional details about ReversingLabs assessment:

- Reports Delivered – Team shares technical and trend analysis reports both from manual and automated assessment.
- Vulnerability Triage – The Netskope team triages the findings identified during assessment and opens the Bug ticket for the respective team for each vulnerability, if any. Also, the team keeps track of SBoM shared with each assessment.
- Continuous Tracking – The Netskope team continuously monitors the Bug tickets to align with the Netskope SLA, which determines, as per severity, the timeframe within which vulnerabilities need to be fixed.
Additionally, the Netskope team utilizes different solutions to continuously and automatically keep our dependencies secure and up-to-date, dependencies being an integral component of the overall software supply chain. For more information on that, here’s a recent blog I wrote on keeping open-source software dependencies secure.




 Voltar
Voltar
















 Leia o Blog
Leia o Blog