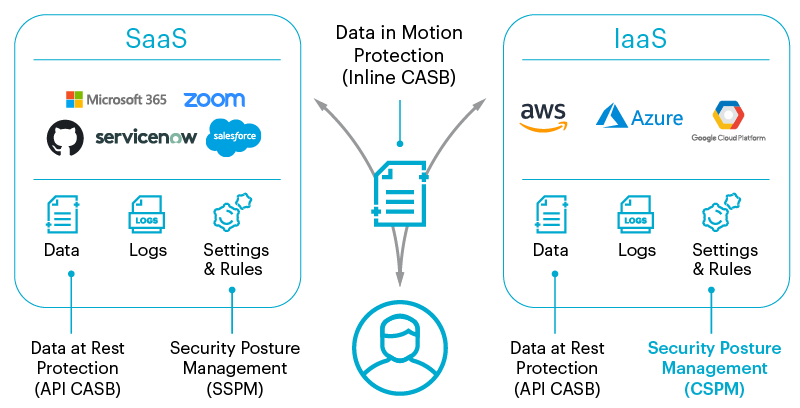
A estratégia de segurança é uma referência à força da segurança cibernética de uma organização, que inclui uma avaliação da sua capacidade de detectar e responder a ameaças à segurança. Logicamente, isso significa que a administração da estratégia de segurança trata da supervisão e do controle da detecção e resposta de uma organização a ameaças por meio de software de administração da estratégia de segurança.
Uma estratégia de segurança inclui uma série de ferramentas e estratégias usadas para proteger redes, dispositivos, usuários e dados de todos os tipos de ameaças, inclusive:
- Credenciais comprometidas/roubadas
- Violações
- Perda de dados
- Ataques de desempenho da rede
- Má configuração/Desvio de configuração
- Malware
- Spyware
- Ransomware
- E muitos outros
Quanto melhor uma organização for em minimizar seu perfil de risco, responder a possíveis ameaças e aderir aos padrões de conformidade de segurança, mais robusta sua estratégia de segurança será.




 Voltar
Voltar