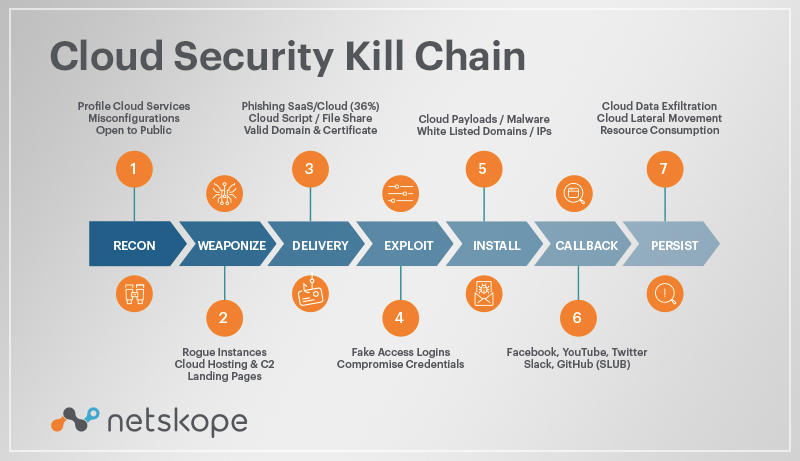
Agora que você tem conhecimentos básicos sobre as etapas comuns de kill chain que sua empresa enfrenta, cabe a você preencher as lacunas da sua estratégia de segurança. Embora essas etapas tenham sido originalmente desenvolvidas considerando a segurança tradicional baseada no perímetro, muitas dessas etapas também são empregadas também por invasores internos, com técnicas como aumento de privilégios, shoulder surfing, SQL injections e muitos outros.
Há todos os tipos de razões para ataques, incluindo financeiros, políticos e até mesmo somente por diversão e reconhecimento. Conhecer quais motivações um invasor pode ter para atacar sua empresa ajudará você a planejar possíveis vetores de ataque.
Ao desenvolver suas estratégias de defesa, é importante observar todos os pontos fracos possíveis, desde sua rede até a nuvem. A boa notícia é que a Netskope está posicionada para assumir o controle contra todos os tipos de ameaças, internas e externas, a seus usuários, aplicações, dados e infraestrutura de nuvem. Saiba mais sobre como a Netskope pode ajudá-lo a impedir a perda de dados e monitorar movimentos anormais dos dados da nuvem hoje mesmo.




 Voltar
Voltar