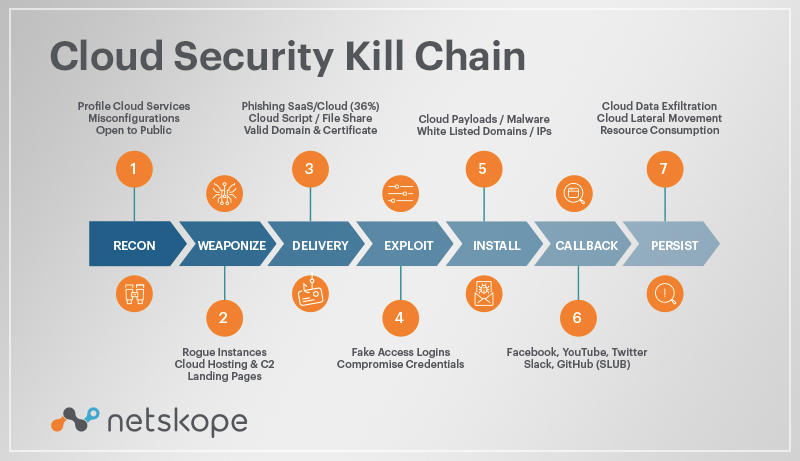
Sie sollten jetzt ein rudimentäres Verständnis der üblichen Kill-Chain-Phasen haben, mit denen Ihr Unternehmen konfrontiert ist. Es liegt an Ihnen, die Lücken in Ihrer Sicherheitsstrategie zu schließen. Obwohl diese Phasen ursprünglich mit Blick auf die traditionelle, perimeterbasierte Sicherheit entwickelt wurden, werden viele davon auch von Insiderangreifern verwendet. Hier kommen Techniken wie Rechteausweitung, Schulter-Surfen, SQL-Injections und viele andere zum Einsatz.
Es gibt alle möglichen Gründe für Angriffe, etwa finanzielle und politische – aber auch nur zum Spaß und zur Anerkennung. Wenn Sie verstehen, welche Motivationen ein Angreifer haben könnte, der Ihr Unternehmen ins Visier nimmt, können Sie Maßnahmen gegen potenzielle Angriffsvektoren planen.
Bei der Entwicklung Ihrer Verteidigungsstrategien ist es wichtig, alle möglichen Schwachstellen zu berücksichtigen, von Ihrem Netzwerk bis zur Cloud. Die gute Nachricht ist, dass Netskope ideal positioniert ist, um alle Arten von Insider- und Outsider-Bedrohungen für Ihre Benutzer, Anwendungen, Daten und Ihre Cloud-Infrastruktur zu bekämpfen. Erfahren Sie mehr darüber, wie Netskope Ihnen helfen kann, Datenverlust zu verhindern und anomale Bewegungen von Cloud-Daten zu überwachen.





 Zurück
Zurück