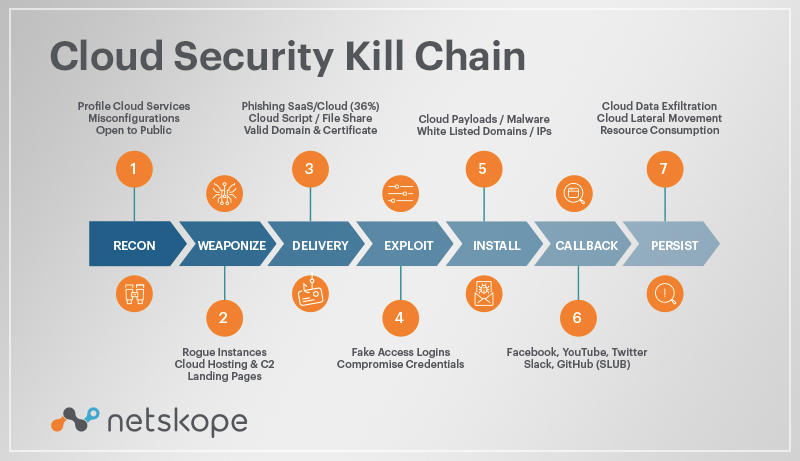
You should now have a rudimentary understanding of the common kill chain stages your company faces, and it’s up to you to fill in the gaps in your security strategy. While these steps were originally developed with traditional, perimeter-focused security in mind, many of these steps are used by insider attackers as well, with techniques including privilege escalation, shoulder surfing, SQL injections, and many others.
There are all kinds of reasons for attacks, including financial, political—even just for fun and recognition. Understanding what motivations an attacker might have for targeting your company will help you plan for potential attack vectors.
When developing your defense strategies, it’s important to look at all possible weak points, from your network to the cloud. The good news is that Netskope is uniquely positioned to take on all kinds of insider and outsider threats to your users, apps, data and cloud infrastructure. Learn more about how Netskope can help you prevent data loss and monitor abnormal movements of cloud data today.




 Back
Back