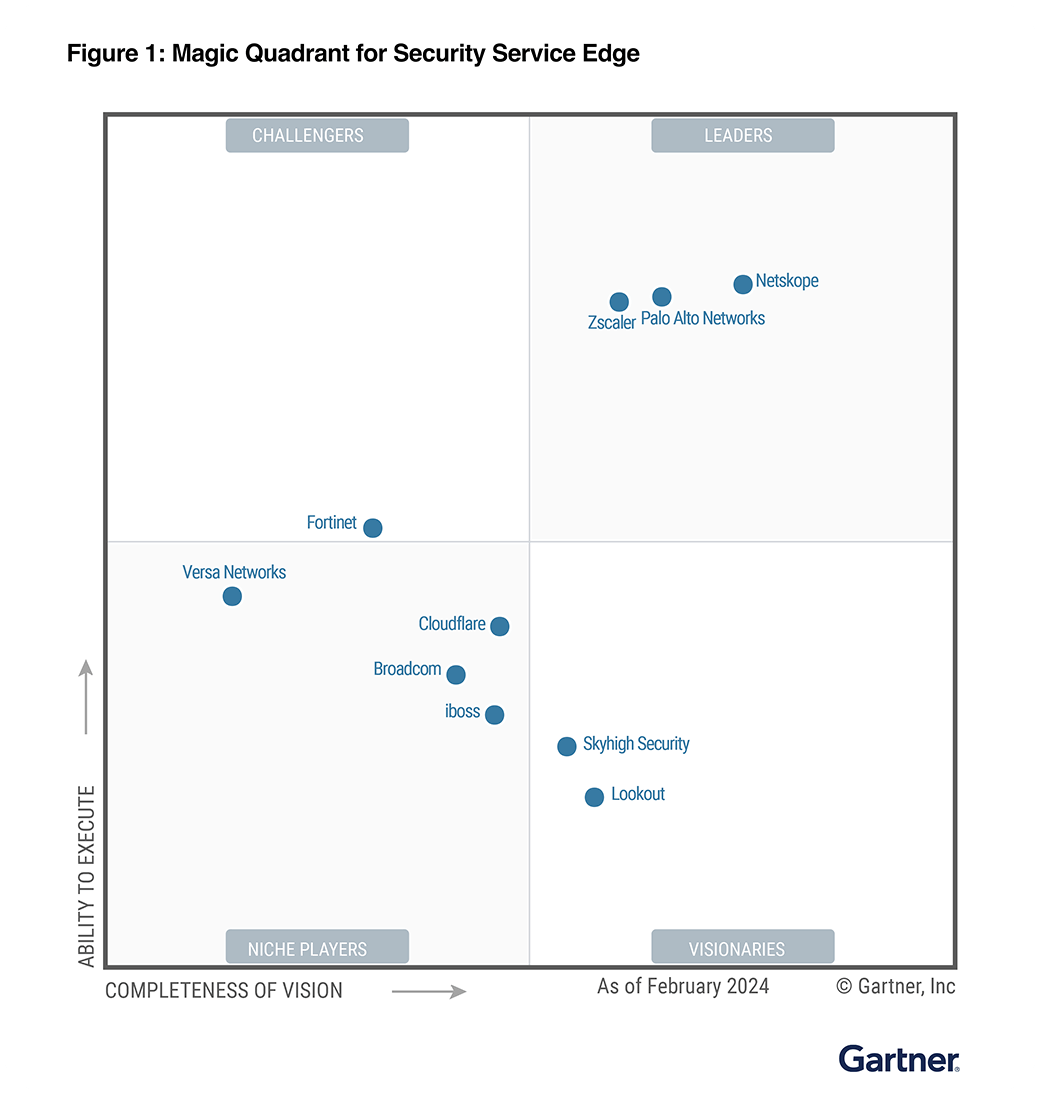
Netskope wurde im Gartner® Magic Quadrant™ 2024 für Security Service Edge als Leader ausgezeichnet. Report abrufen
-
Warum Netskope?
- Warum Netskope?
Warum Netskope?
Verändern Sie die Art und Weise, wie Netzwerke und Sicherheit zusammenarbeiten.
Report abrufenImmer noch am Höchsten in der Ausführung.
Immer noch am Weitesten in der Vision.Erfahren Sie, warum Netskope im Gartner® Magic Quadrant ™ 2024 zum dritten Mal in Folge zum Leader für Security Service Edge ernannt wurde.
- Warum Netskope?
Unsere Kunden
Netskope bedient mehr als 3.000 Kunden weltweit, darunter mehr als 25 der Fortune 100
Unsere KundenWir helfen unseren Kunden, auf alles vorbereitet zu sein - Warum Netskope?
Unsere Partner
Unsere Partnerschaften helfen Ihnen, Ihren Weg in die Cloud zu sichern.
Erfahren Sie mehr über Netskope-PartnerDie partnerorientierte Markteinführungsstrategie von Netskope ermöglicht es unseren Partnern, ihr Wachstum und ihre Rentabilität zu maximieren und gleichzeitig die Unternehmenssicherheit an neue Anforderungen anzupassen.
-
Plattform
- Plattform
Netskope One-Plattform
Netskope One ist eine konvergierte Sicherheits- und Network-as-a-Service-Plattform.
Whitepaper lesenIhr Netzwerk von morgenPlanen Sie Ihren Weg zu einem schnelleren, sichereren und widerstandsfähigeren Netzwerk, das auf die von Ihnen unterstützten Anwendungen und Benutzer zugeschnitten ist.
- Plattform
Funktionen der Netskope One-Plattform
Netskope One ermöglicht eine größere wirtschaftliche Agilität mit Blitzgeschwindigkeit und zuverlässiger Ausfallsicherheit.
Erfahren Sie mehr über Netskope OneVorstellung der Netskope One-PlattformNetskope One ist eine cloudnative Plattform, die konvergierte Sicherheits- und Netzwerkdienste bietet, um Ihre SASE- und Zero-Trust-Transformation zu ermöglichen.
- Plattform
NewEdge
NewEdge ist die weltweit größte und leistungsstärkste private Sicherheits-Cloud.
Mehr über NewEdge erfahrenNutzen Sie eine Secure Access Service Edge (SASE)-ArchitekturNetskope NewEdge ist die weltweit größte und leistungsstärkste private Sicherheits-Cloud und bietet Kunden eine beispiellose Serviceabdeckung, Leistung und Ausfallsicherheit.
- Plattform
Technologiepartner und Integrationen
Netskope arbeitet mit den stärksten Unternehmen im Bereich Unternehmenstechnologie zusammen.
Erfahren Sie mehr über Cloud ExchangeNetskope Cloud ExchangeCloud Exchange (CE) von Netskope gibt Ihren Kunden leistungsstarke Integrationstools an die Hand, mit denen sie in jeden Aspekt ihres Sicherheitsstatus investieren können.
-
Produkte
- Produkte
Edge-Produkte von Security Service
Schützen Sie sich vor fortgeschrittenen und cloudfähigen Bedrohungen und schützen Sie Daten über alle Vektoren hinweg.
Netskope ProduktübersichtDie Plattform der Zukunft heißt NetskopeIntelligent Security Service Edge (SSE), Cloud Access Security Broker (CASB), Cloud Firewall, Next Generation Secure Web Gateway (SWG) und Private Access for ZTNA sind nativ in einer einzigen Lösung integriert, um jedes Unternehmen auf seinem Weg zum Secure Access Service zu unterstützen Edge (SASE)-Architektur.
- Security Service Edge (SSE)
- Next Gen Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- ZTNA Next
- SkopeAI
- Public Cloud Security
- Advanced Analytics
- Cloud Firewall
- Data Loss Prevention (DLP)
- Proaktives Digital Experience Management
- Geräteintelligenz
- Remote Browser Isolation
- SaaS Security Posture Management
- Security Service Edge (SSE)
- Produkte
Borderless SD-WAN
Stellen Sie selbstbewusst sicheren, leistungsstarken Zugriff auf jeden Remote-Benutzer, jedes Gerät, jeden Standort und jede Cloud bereit.
Erfahren Sie mehr über Next Gen SASE BranchNext Gen SASE Branch ist hybrid – verbunden, sicher und automatisiertNetskope Next Gen SASE Branch vereint kontextsensitives SASE Fabric, Zero-Trust Hybrid Security und SkopeAI-Powered Cloud Orchestrator in einem einheitlichen Cloud-Angebot und führt so zu einem vollständig modernisierten Branch-Erlebnis für das grenzenlose Unternehmen.
- Borderless SD-WAN
- SASE-Zweig der nächsten Generation
- Sicheres SD-WAN
- Endpoint SD-WAN
- Micro Branch
- Wireless WAN
- Multi-Cloud Networking
- Intelligenter IoT-Zugriff
- Borderless SD-WAN
- Produkte
Secure Access Service Edge
Netskope One SASE bietet eine Cloud-native, vollständig konvergente SASE-Lösung eines einzelnen Anbieters.
Jetzt das E-Book lesenEntwerfen einer SASE-Architektur für DummiesHolen Sie sich Ihr kostenloses Exemplar des einzigen Leitfadens zum SASE-Design, den Sie jemals benötigen werden.
-
Lösungen
- Lösungen
Netzwerktransformation
Erreichen Sie Agilität und Effizienz durch digitale Transformation.
Netskope LösungsübersichtMehr über NewEdge erfahrenSteigen Sie auf marktführende Cloud-Security Service mit minimaler Latenz und hoher Zuverlässigkeit um. - Lösungen
Modernisierung der Sicherheit
Meistern Sie die Sicherheitsherausforderungen von heute und morgen.
Erfahren Sie, wie wir den Einsatz generativer KI sichernErmöglichen Sie die sichere Nutzung generativer KI-Anwendungen mit Anwendungszugriffskontrolle, Benutzercoaching in Echtzeit und erstklassigem Datenschutz.- Advanced Threat Protection
- Data protection
- Hybrides Arbeiten
- Insider-Risiken
- Aufrechterhaltung der Cloud-Compliance
- Ersetzen Sie VPNs
- ChatGPT und Generative AI sicher aktivieren
- Managed Cloud-Anwendungen sichern
- Unmanaged Cloud Services sichern
- AWS, Azure und GCP
- Advanced Threat Protection
- Lösungen
Frameworks
Regulatorische Rahmenbedingungen für die Cybersicherheit berücksichtigen.
Netskope LösungsübersichtErfahren Sie mehr über Zero TrustZero-Trust-Lösungen für SSE- und SASE-Deployments - Lösungen
Regierung und Industrie
Netskope hilft den größten Agenturen und Unternehmen der Welt, ihren Weg in die Cloud zu sichern.
Erfahren Sie mehr über Netskope GovCloudNetskope erhält die FedRAMP High AuthorizationWählen Sie Netskope GovCloud, um die Transformation Ihrer Agentur zu beschleunigen.
- Finanzdienstleistungen und Versicherung
- Gesundheitswesen und Biowissenschaften
- High Technology
- Hochschuleinrichtungen
- K12
- Recht
- Fertigung
- Öffentlicher Sektor
- Einzelhandel und Tourismus
- Dienstleistungsunternehmen
- Versorgungsunternehmen
- Finanzdienstleistungen und Versicherung
-
Ressourcen
- Ressourcen
Ressourcen
Erfahren Sie mehr darüber, wie Netskope Ihnen helfen kann, Ihre Reise in die Cloud zu sichern.
Podcast abspielenSecurity Visionaries PodcastHow to Use a Magic Quadrant and Other Industry Research
In dieser Folge analysieren Max Havey, Steve Riley und Mona Faulkner den komplizierten Prozess der Erstellung eines Magic Quadrant und erklären, warum es sich dabei um viel mehr als nur ein Diagramm handelt. - Ressourcen
Blog
Erfahren Sie, wie Netskope die Sicherheits- und Netzwerktransformation durch Security Service Edge (SSE) ermöglicht
Den Blog lesenNeueste BlogsLesen Sie, wie Netskope die Zero Trust- und SASE-Reise durch Security Service Edge (SSE)-Funktionen ermöglichen kann.
- Ressourcen
Events und Workshops
Bleiben Sie den neuesten Sicherheitstrends immer einen Schritt voraus und tauschen Sie sich mit Gleichgesinnten aus
Entdecken Sie SitzungenSASE Week 2023: Ihre SASE-Reise beginnt jetzt!Wiederholungssitzungen der vierten jährlichen SASE Week.
- Ressourcen
Security Defined
Finden Sie alles was Sie wissen müssen in unserer Cybersicherheits-Enzyklopädie.
Erfahren Sie mehr über Security Service EdgeWas ist Security Service Edge?Entdecken Sie die Sicherheitselemente von SASE, die Zukunft des Netzwerks und der Security in der Cloud.
- Übersicht über die definierte Sicherheit
- Was ist SASE?
- Was ist Security Service Edge?
- Was ist ein Cloud Access Security Broker (CASB)?
- Was ist Zero-Trust-Sicherheit?
- Was ist ein Next Gen SWG?
- Was ist Data Loss Prevention (DLP)?
- Was ist SD-WAN?
- Was ist generative KI?
- Was ist Remote Browser Isolation (RBI)?
- Was ist SSPM?
- Was ist FedRamp?
- Übersicht über die definierte Sicherheit
-
Unternehmen
- Unternehmen
Unternehmen
Wir helfen Ihnen, den Herausforderungen der Cloud-, Daten- und Netzwerksicherheit einen Schritt voraus zu sein.
Finde mehr herausUnterstützung der Nachhaltigkeit durch DatensicherheitNetskope ist stolz darauf, an Vision 2045 teilzunehmen: einer Initiative, die darauf abzielt, das Bewusstsein für die Rolle der Privatwirtschaft bei der Nachhaltigkeit zu schärfen.
- Unternehmen
Leadership
Unser Leadership-Team ist fest entschlossen, alles zu tun, was nötig ist, damit unsere Kunden erfolgreich sind.
Lernen Sie unser Team kennenDenker, Architekten, Träumer, Innovatoren. Gemeinsam liefern wir hochmoderne Cloud-Sicherheitslösungen, die unseren Kunden helfen, ihre Daten und Mitarbeiter zu schützen. - Unternehmen
Kundenlösungen
Wir sind für Sie da, stehen Ihnen bei jedem Schritt zur Seite und sorgen für Ihren Erfolg mit Netskope.
Erfahren Sie mehr über professionelle DienstleistungenDas talentierte und erfahrene Professional Services-Team von Netskope bietet einen präskriptiven Ansatz für Ihre erfolgreiche Implementierung.- Professional Services
- Customer Success
- Technischer Support
- Partner für Servicebereitstellung
- Kunden-Community
- Produkt-Dokumentation
- Support-Portal
- Trust Portal
- Professional Services
- Unternehmen
Schulung und Zertifizierung
Netskope-Schulungen helfen Ihnen ein Experte für Cloud-Sicherheit zu werden.
Erfahren Sie mehr über Schulungen und ZertifizierungenMit Netskope-Schulungen können Sie Ihre digitale Transformation absichern und das Beste aus Ihrer Cloud, dem Web und Ihren privaten Anwendungen machen.- Netskope Security Cloud – einführende technische Online-Schulung
- Betrieb und Verwaltung von Netskope Security Cloud (NSCO&A)
- Implementierung und Integration von Netskope Security Cloud (NSCI&I)
- Netskope Cloud Security-Zertifizierungsprogramm
- Netskope Security Cloud – einführende technische Online-Schulung
- Warum Netskope?
Verändern Sie die Art und Weise, wie Netzwerke und Sicherheit zusammenarbeiten.
- Unsere Kunden
Netskope bedient mehr als 3.000 Kunden weltweit, darunter mehr als 25 der Fortune 100
- Unsere Partner
Unsere Partnerschaften helfen Ihnen, Ihren Weg in die Cloud zu sichern.
Immer noch am Weitesten in der Vision.
Erfahren Sie, warum Netskope im Gartner® Magic Quadrant ™ 2024 zum dritten Mal in Folge zum Leader für Security Service Edge ernannt wurde.
Report abrufen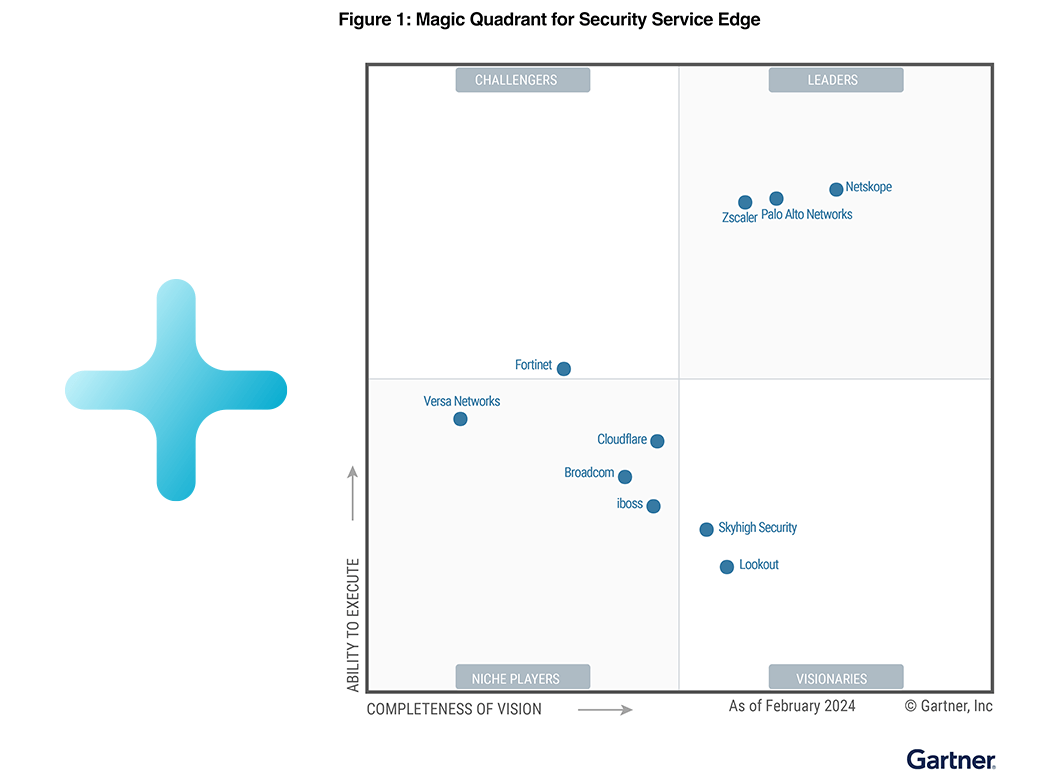

- Netskope One-Plattform
Netskope One ist eine konvergierte Sicherheits- und Network-as-a-Service-Plattform.
- Funktionen der Netskope One-Plattform
Netskope One ermöglicht eine größere wirtschaftliche Agilität mit Blitzgeschwindigkeit und zuverlässiger Ausfallsicherheit.
- NewEdge
NewEdge ist die weltweit größte und leistungsstärkste private Sicherheits-Cloud.
- Technologiepartner und Integrationen
Netskope arbeitet mit den stärksten Unternehmen im Bereich Unternehmenstechnologie zusammen.
Planen Sie Ihren Weg zu einem schnelleren, sichereren und widerstandsfähigeren Netzwerk, das auf die von Ihnen unterstützten Anwendungen und Benutzer zugeschnitten ist.
Whitepaper lesen
Netskope One ist eine cloudnative Plattform, die konvergierte Sicherheits- und Netzwerkdienste bietet, um Ihre SASE- und Zero-Trust-Transformation zu ermöglichen.
Erfahren Sie mehr über Netskope One
Netskope NewEdge ist die weltweit größte und leistungsstärkste private Sicherheits-Cloud und bietet Kunden eine beispiellose Serviceabdeckung, Leistung und Ausfallsicherheit.
Mehr über NewEdge erfahren
Cloud Exchange (CE) von Netskope gibt Ihren Kunden leistungsstarke Integrationstools an die Hand, mit denen sie in jeden Aspekt ihres Sicherheitsstatus investieren können.
Erfahren Sie mehr über Cloud Exchange
- Edge-Produkte von Security Service
Schützen Sie sich vor fortgeschrittenen und cloudfähigen Bedrohungen und schützen Sie Daten über alle Vektoren hinweg.
- Borderless SD-WAN
Stellen Sie selbstbewusst sicheren, leistungsstarken Zugriff auf jeden Remote-Benutzer, jedes Gerät, jeden Standort und jede Cloud bereit.
- Secure Access Service Edge
Netskope One SASE bietet eine Cloud-native, vollständig konvergente SASE-Lösung eines einzelnen Anbieters.
- Security Service Edge (SSE)
- Next Gen Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- ZTNA Next
- SkopeAI
- Public Cloud Security
- Advanced Analytics
- Cloud Firewall
- Data Loss Prevention (DLP)
- Proaktives Digital Experience Management
- Geräteintelligenz
- Remote Browser Isolation
- SaaS Security Posture Management
Intelligent Security Service Edge (SSE), Cloud Access Security Broker (CASB), Cloud Firewall, Next Generation Secure Web Gateway (SWG) und Private Access for ZTNA sind nativ in einer einzigen Lösung integriert, um jedes Unternehmen auf seinem Weg zum Secure Access Service zu unterstützen Edge (SASE)-Architektur.
Netskope Produktübersicht
Netskope Next Gen SASE Branch vereint kontextsensitives SASE Fabric, Zero-Trust Hybrid Security und SkopeAI-Powered Cloud Orchestrator in einem einheitlichen Cloud-Angebot und führt so zu einem vollständig modernisierten Branch-Erlebnis für das grenzenlose Unternehmen.
Erfahren Sie mehr über Next Gen SASE Branch
Holen Sie sich Ihr kostenloses Exemplar des einzigen Leitfadens zum SASE-Design, den Sie jemals benötigen werden.
Jetzt das E-Book lesen
- Netzwerktransformation
Erreichen Sie Agilität und Effizienz durch digitale Transformation.
- Modernisierung der Sicherheit
Meistern Sie die Sicherheitsherausforderungen von heute und morgen.
- Frameworks
Regulatorische Rahmenbedingungen für die Cybersicherheit berücksichtigen.
- Regierung und Industrie
Netskope hilft den größten Agenturen und Unternehmen der Welt, ihren Weg in die Cloud zu sichern.


Wählen Sie Netskope GovCloud, um die Transformation Ihrer Agentur zu beschleunigen.
Erfahren Sie mehr über Netskope GovCloud
- Ressourcen
Erfahren Sie mehr darüber, wie Netskope Ihnen helfen kann, Ihre Reise in die Cloud zu sichern.
- Blog
Erfahren Sie, wie Netskope die Sicherheits- und Netzwerktransformation durch Security Service Edge (SSE) ermöglicht
- Events und Workshops
Bleiben Sie den neuesten Sicherheitstrends immer einen Schritt voraus und tauschen Sie sich mit Gleichgesinnten aus
- Security Defined
Finden Sie alles was Sie wissen müssen in unserer Cybersicherheits-Enzyklopädie.
- Übersicht über die definierte Sicherheit
- Was ist SASE?
- Was ist Security Service Edge?
- Was ist ein Cloud Access Security Broker (CASB)?
- Was ist Zero-Trust-Sicherheit?
- Was ist ein Next Gen SWG?
- Was ist Data Loss Prevention (DLP)?
- Was ist SD-WAN?
- Was ist generative KI?
- Was ist Remote Browser Isolation (RBI)?
- Was ist SSPM?
- Was ist FedRamp?
How to Use a Magic Quadrant and Other Industry Research
In dieser Folge analysieren Max Havey, Steve Riley und Mona Faulkner den komplizierten Prozess der Erstellung eines Magic Quadrant und erklären, warum es sich dabei um viel mehr als nur ein Diagramm handelt.

Lesen Sie, wie Netskope die Zero Trust- und SASE-Reise durch Security Service Edge (SSE)-Funktionen ermöglichen kann.
Den Blog lesen
Wiederholungssitzungen der vierten jährlichen SASE Week.
Entdecken Sie Sitzungen
Entdecken Sie die Sicherheitselemente von SASE, die Zukunft des Netzwerks und der Security in der Cloud.
Erfahren Sie mehr über Security Service Edge
- Unternehmen
Wir helfen Ihnen, den Herausforderungen der Cloud-, Daten- und Netzwerksicherheit einen Schritt voraus zu sein.
- Leadership
Unser Leadership-Team ist fest entschlossen, alles zu tun, was nötig ist, damit unsere Kunden erfolgreich sind.
- Kundenlösungen
Wir sind für Sie da, stehen Ihnen bei jedem Schritt zur Seite und sorgen für Ihren Erfolg mit Netskope.
- Schulung und Zertifizierung
Netskope-Schulungen helfen Ihnen ein Experte für Cloud-Sicherheit zu werden.
Netskope ist stolz darauf, an Vision 2045 teilzunehmen: einer Initiative, die darauf abzielt, das Bewusstsein für die Rolle der Privatwirtschaft bei der Nachhaltigkeit zu schärfen.
Finde mehr heraus



































)