Summary
On August 9, 2022, we released a blog post about a phishing campaign where attackers were abusing Google Sites and Microsoft Azure Web Apps to steal cryptocurrency wallets and accounts from different targets, namely Coinbase, MetaMask, Kraken, and Gemini. The attackers were abusing SEO techniques to spread the pages and using advanced techniques to steal data, such as using live chats to interact with victims.
Over the past month, the attackers responsible for the phishing campaign have proven to be resilient to take-downs. Most of the URLs we found in August are still active and the attacker is taking measures to keep the operation online. Furthermore, we found new phishing pages with the same targets disclosed in the initial research, and new phishing pages mimicking Binance, Crypto.com, Gate.io, KuCoin, PancakeSwap, and Shakepay.
We found the following target distribution analyzing the URLs hosted on Google Sites:
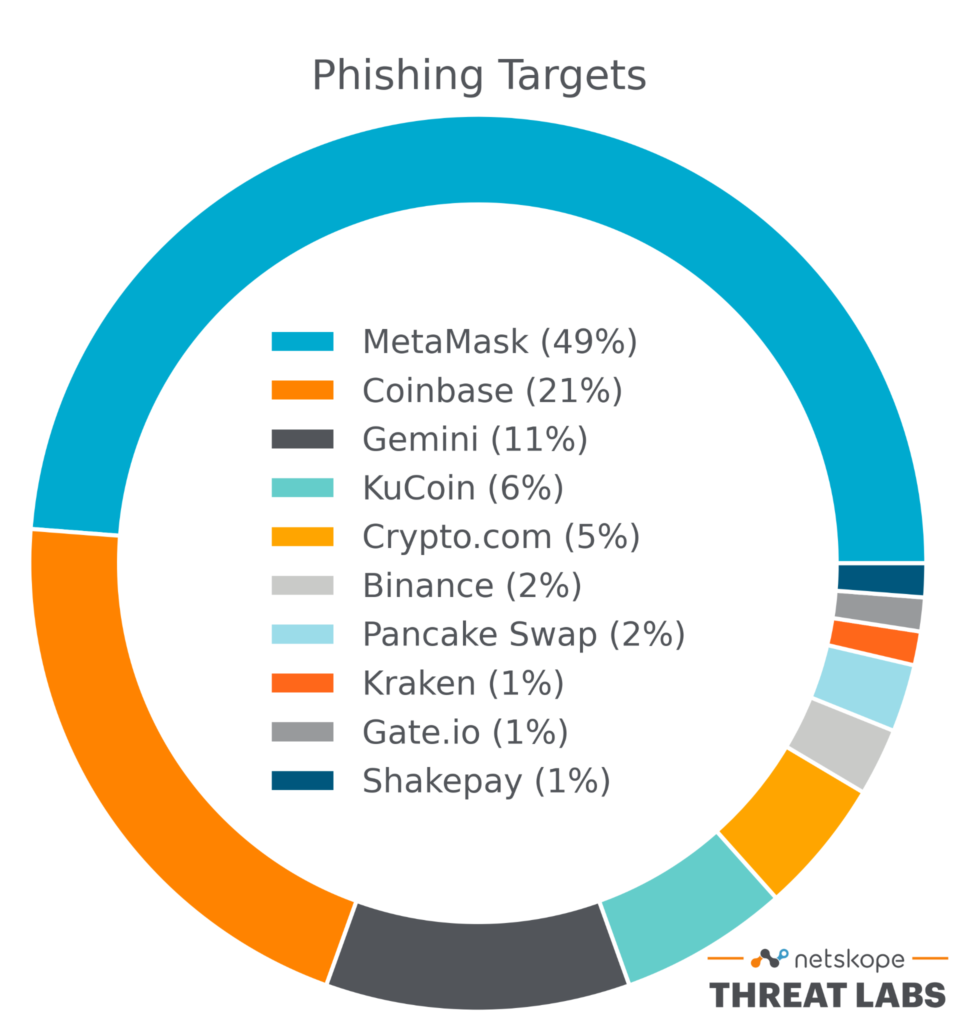
In this blog post, we will provide a follow up to the blog post we released in August, showing what has changed since then.
How the attack works
- The victim searches for a cryptocurrency website using specific keywords (e.g. “have MetaMask account”) and the phishing page is displayed first or among the first results.
- The first phishing page mimics the original website and contains a lot of elements to boost SEO. This stage redirects the victim to another phishing website via links within the page.
- The second phishing page tries to steal sensitive information, such as the cryptocurrency account credentials or secret recovery phrases.
- The last page also comes with a live web chat where the attacker interacts with the victim, likely to steal more sensitive data.
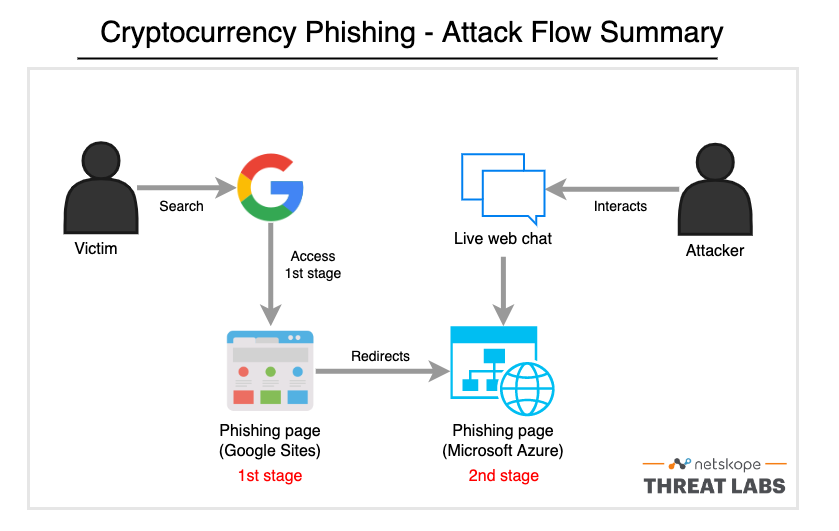
Attacker’s resilience
Analyzing the URLs we found in August, we noticed that over the past month:
- All of the URLs used in the second stage were taken down;
- 75% of the first stage URLs remain online, and for those URLs the attacker either:
- Removed the second stage URL;
- Added a new online second stage URL.
The Google Sites information banner indicates that the attacker is constantly updating the first stage pages.
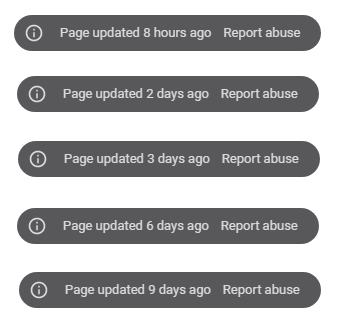
In summary, the attacker is replacing the Microsoft Azure URLs with new ones to remain operant. Also, in some cases the attacker just removed the offline URL instead of adding a new one, likely to avoid the user being redirected to an offline page that was flagged as phishing while they are working to get another page online.
New targets
Aside from the companies we have previously identified, we found new Google Sites URLs for Binance, Crypto.com, Gate.io, KuCoin, PancakeSwap, and Shakepay.
These new URLs all follow the same attack pattern, using Google Sites to mimic the original website. However, only the Crypto.com phishing page contains a second stage URL at this point. All of the other pages were either redirecting the user to the original website being mimicked or not redirecting anywhere. It’s unclear whether the attacker is still developing the second stage for the other targets or if they were already taken down and removed from the page.
Crypto.com
This phishing page works the same as the others, by mimicking the original website in the first stage, created with Google Sites.
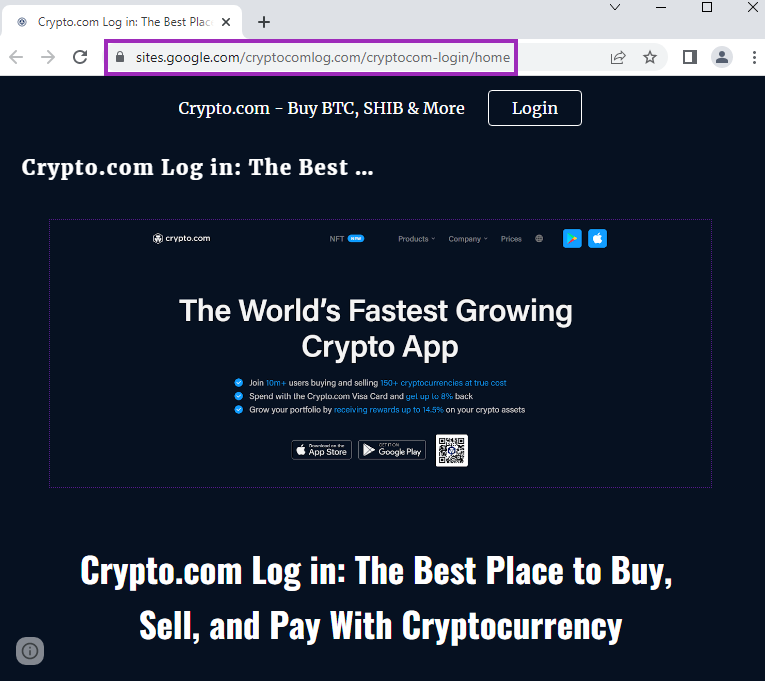
It then redirects the victim to the second stage, hosted with Microsoft Azure Web App, to a page that tries to steal the user’s credentials.
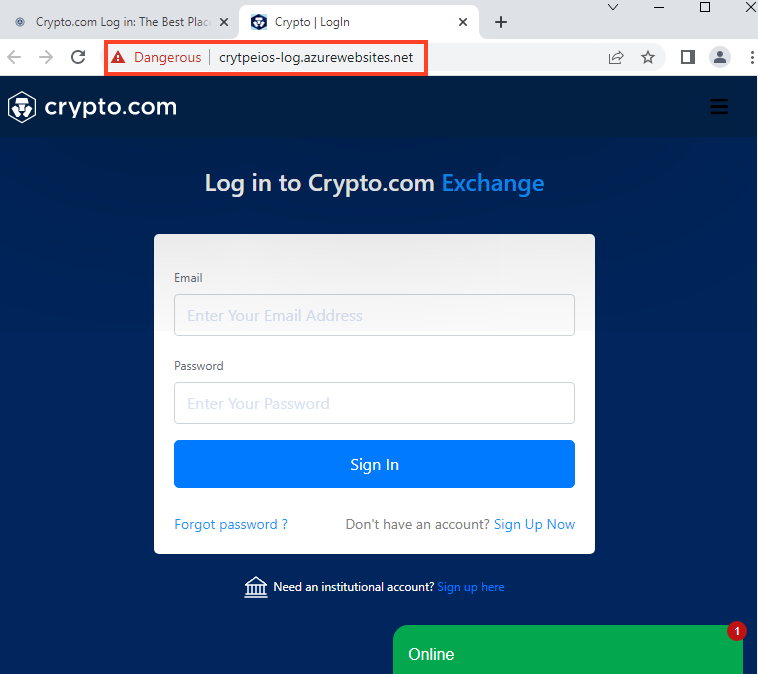
After entering the username and password, the webpage requests the victim’s phone number.
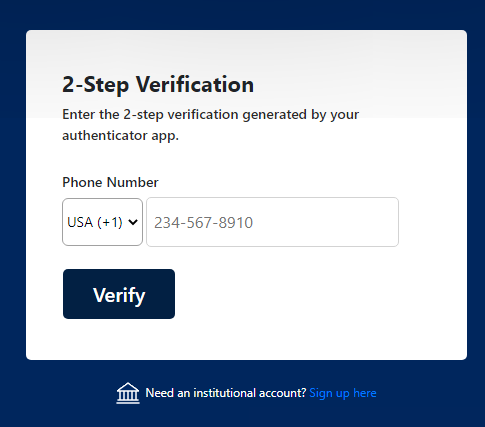
After entering the phone number, the page shows a fake error message and asks the victim to contact them via web chat, which is the same behavior found previously.
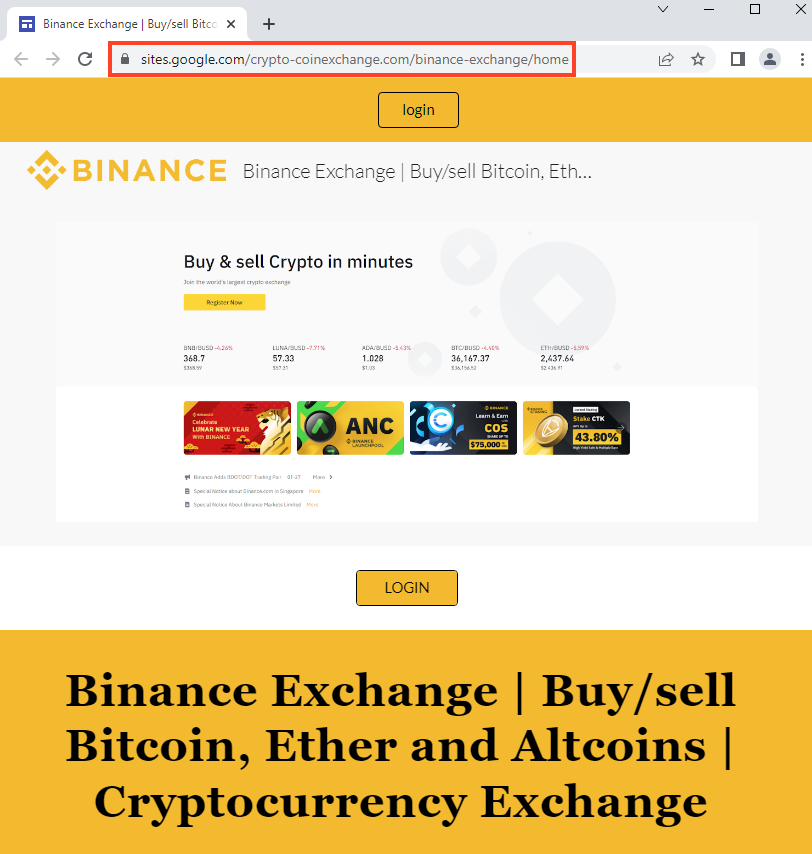
Binance
Below, is an example of a website hosted on Google Sites that mimics Binance.
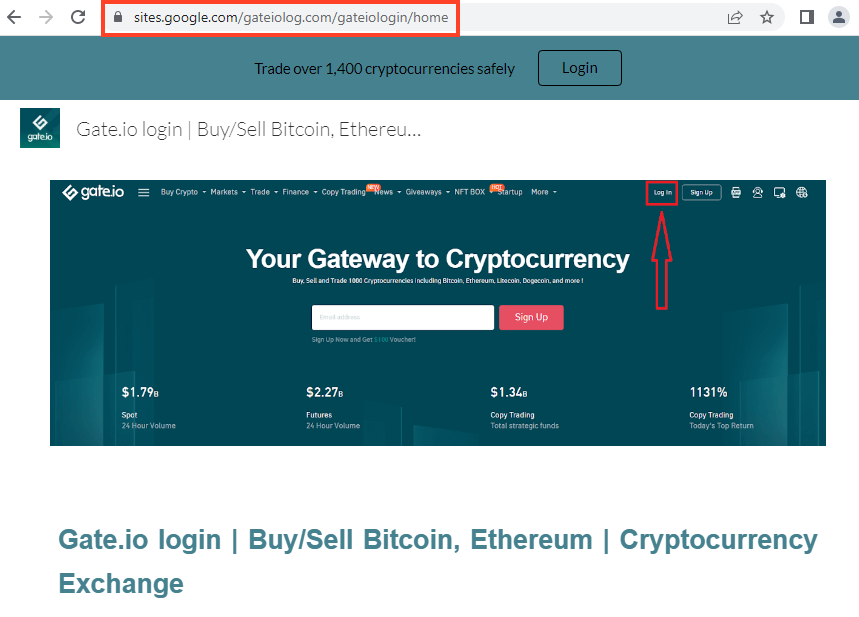
Gate.io
Below, is an example of a website hosted on Google Sites that mimics Gate.io.
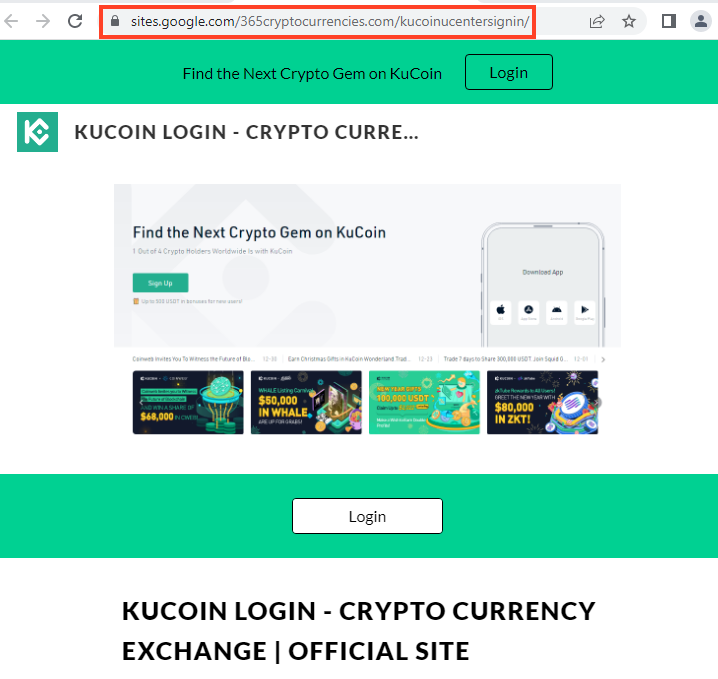
KuCoin
Below, is an example of a website hosted on Google Sites that mimics KuCoin.
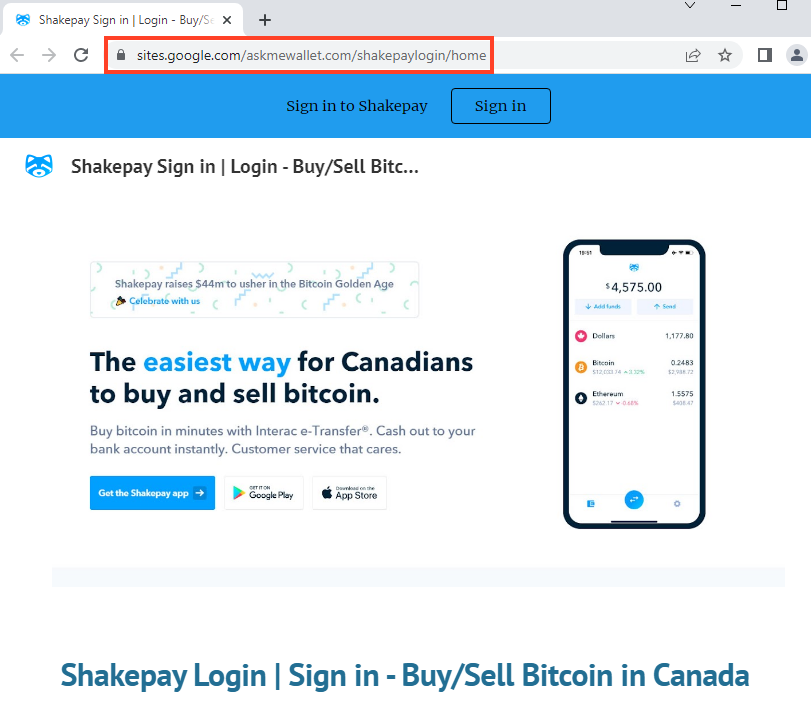
ShakePay
Below, is an example of a website hosted on Google Sites that mimics ShakePay.
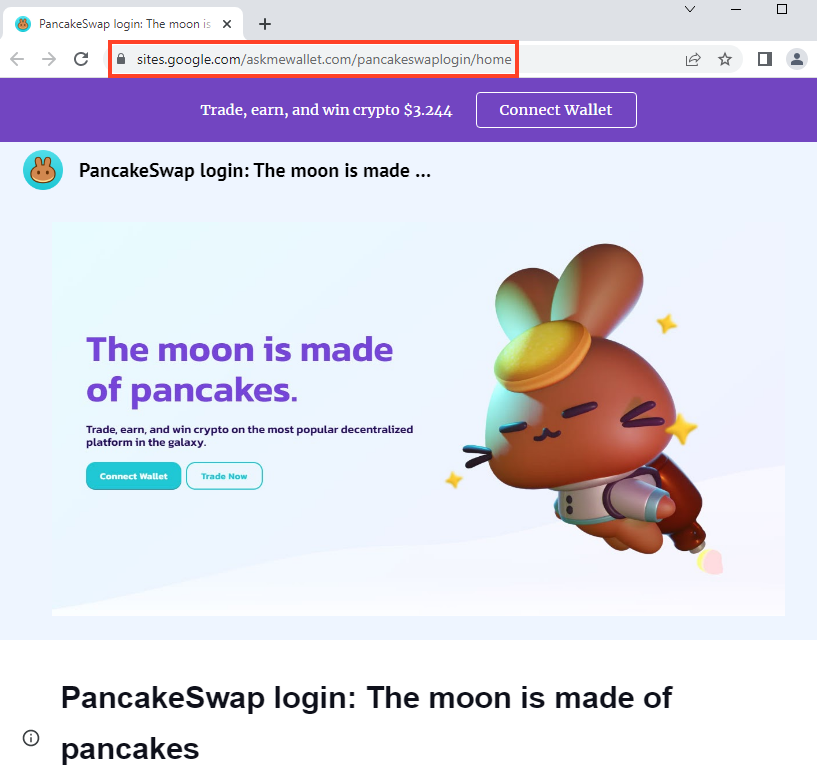
PancakeSwap
Below, is an example of a website hosted on Google Sites that mimics PancakeSwap.
New URLs, Same Targets
Additionally, we found 66 new Google Sites URLs with the same targets disclosed in the first research, which are Coinbase, MetaMask, Kraken, and Gemini.
We also found a new template used for MetaMask phishing.
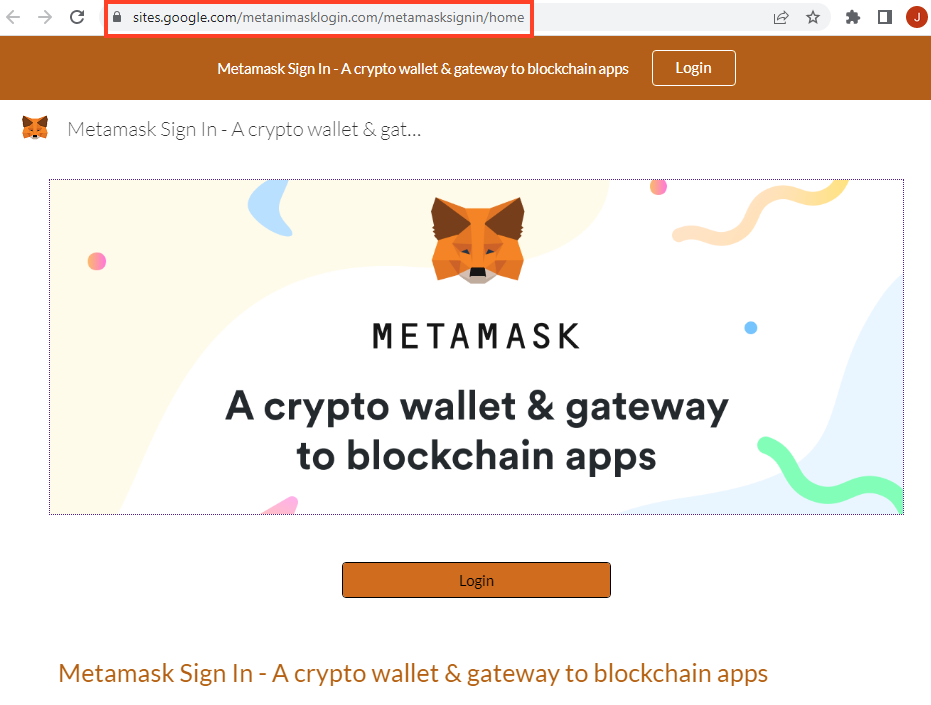
The second stage works exactly like the ones we spotted previously, but it’s using a new template as well.
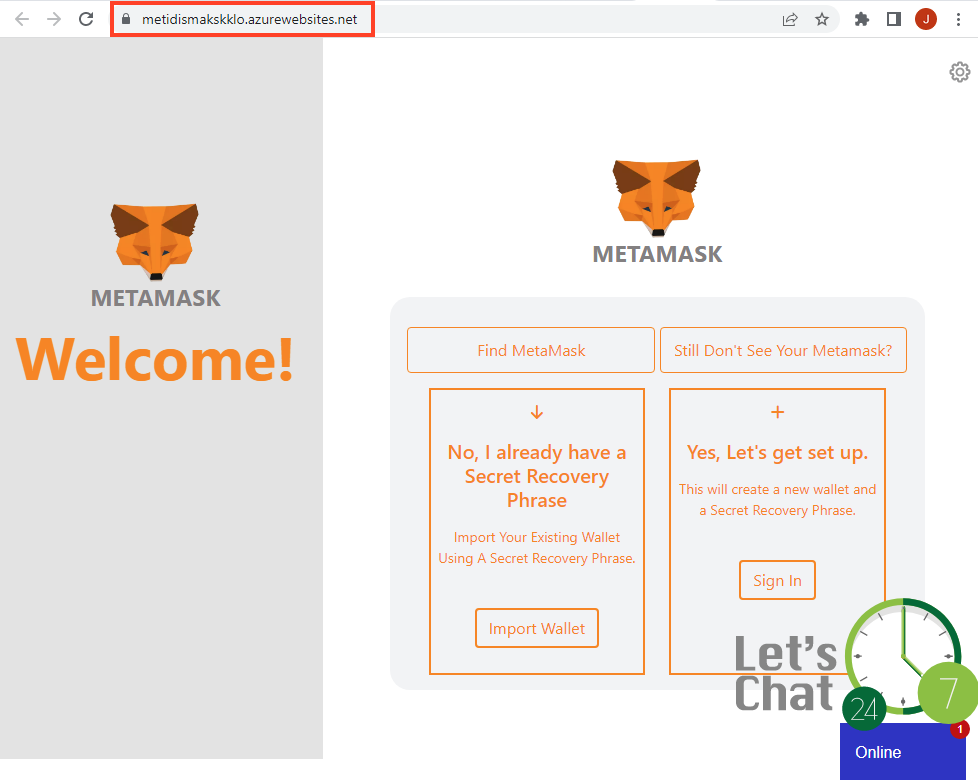
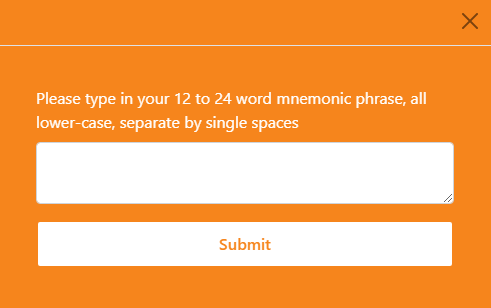
The “Import Wallet” button leads to a modal that asks for the secret recovery phrase for MetaMask.
The “Sign In” option contains some slight differences compared to the phishing we spotted previously, but it has the same goal of stealing the victim’s credentials.
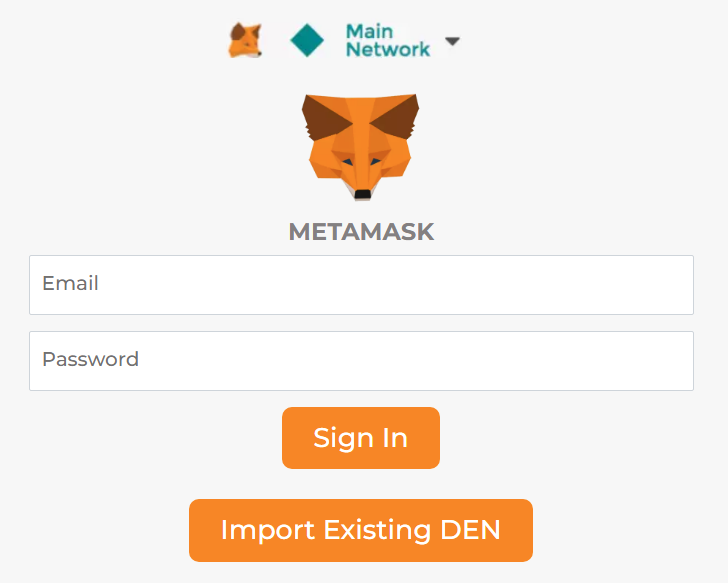
It also comes with the same live chat feature we previously mentioned, but this time it opens in a popup window.
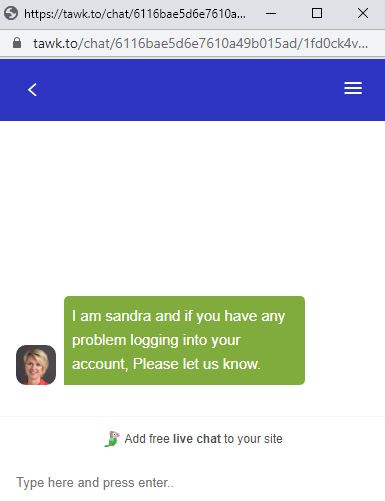
According to the information button provided by Google Sites, this page was likely changed on August 23, 2022.
Conclusions
Based on this additional research, we believe attackers will continue to use this pattern, as they can create multiple accounts in these cloud services and easily replicate the phishing templates using different URLs. Also, by dividing this phishing in two stages (Google Sites and Microsoft Azure), the attackers are creating more resilience, since they can simply replace an offline URL to another one to keep the operation online.
Netskope strongly recommends users to directly access the website they are trying to reach instead of searching or clicking on any links throughout the internet. For organizations, we also recommend the usage of a secure web gateway, capable of detecting and blocking phishing in real time.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators. Netskope Next Gen SWG inspects all HTTP and HTTPS traffic, using a combination of threat intelligence, signatures, heuristics, and machine learning to identify and block phishing pages in real time.
IOCs
First stage URLs
hxxps://sites.google[.]com/crypto-coinexchange.com/geminiexchangee/home
hxxps://sites.google[.]com/cryptocomlog.com/crypto-com-login/home
hxxps://sites.google[.]com/365cryptocurrencies.com/coinbasewallet/home
hxxps://sites.google[.]com/365cryptocurrencies.com/kucoin-logi/
hxxps://sites.google[.]com/365cryptocurrencies.com/kucoinucentersignin/
hxxps://sites.google[.]com/askmewallet.com/binancewalletextension/home
hxxps://sites.google[.]com/askmewallet.com/geminilogin/home
hxxps://sites.google[.]com/askmewallet.com/pancakeswaplogin/home
hxxps://sites.google[.]com/askmewallet.com/shakepaylogin/home
hxxps://sites.google[.]com/askscryptous.com/coinbaselogin/home
hxxps://sites.google[.]com/askscryptous.com/coinbasewallet/home
hxxps://sites.google[.]com/askscryptous.com/geminisignin/home
hxxps://sites.google[.]com/askscryptous.com/metamask-login/home
hxxps://sites.google[.]com/askscryptous.com/metamasklogin/home
hxxps://sites.google[.]com/askscryptous.com/metamasksignin/home
hxxps://sites.google[.]com/askscryptous.com/metamaskwalletlogin/home
hxxps://sites.google[.]com/bitcoinbasepro.com/coinbaselogincom/
hxxps://sites.google[.]com/coinbasecom.org/coinbaselogin/home
hxxps://sites.google[.]com/coinbaseloginn.com/coinbaseloginn/home
hxxps://sites.google[.]com/coinbselogin.com/coinbaselogin/home
hxxps://sites.google[.]com/coindesklogin.com/coinbase-wallet/home
hxxps://sites.google[.]com/coinlogins.com/coinbase-down/home
hxxps://sites.google[.]com/coinsprologin.com/coinbasewallet-login/home
hxxps://sites.google[.]com/crypto-coinexchange.com/binance-exchange/home
hxxps://sites.google[.]com/crypto-coinexchange.com/coinbaseexchange/home
hxxps://sites.google[.]com/crypto-coinexchange.com/krakenexchange/home
hxxps://sites.google[.]com/crypto-coinwallet.com/coinbase-wallet/home
hxxps://sites.google[.]com/crypto-coinwallet.com/coinbasewallet/home
hxxps://sites.google[.]com/crypto-coinwallet.com/geminiwallet/home
hxxps://sites.google[.]com/crypto-coinwallet.com/metamask-wallet/home
hxxps://sites.google[.]com/cryptobitwallets.com/metamasksignin/home
hxxps://sites.google[.]com/cryptobitwallets.com/metamaskwallet/home
hxxps://sites.google[.]com/cryptocom-login.com/cryptocomloginin/home
hxxps://sites.google[.]com/cryptocomlog.com/cryptocom-login/home
hxxps://sites.google[.]com/cryptologn.com/coinbaseprologin
hxxps://sites.google[.]com/cryptologn.com/coinbasewallet/
hxxps://sites.google[.]com/cryptologn.com/metamasksignin
hxxps://sites.google[.]com/cryptowalletbit.com/blockfi-wallet/home
hxxps://sites.google[.]com/cryptowalletsusa.com/metamasklogin/home
hxxps://sites.google[.]com/cryptowalletts.com/pancake-swap/home
hxxps://sites.google[.]com/csscrypton.com/crypto-login/home
hxxps://sites.google[.]com/ecryptowalletpay.com/coinbase-wallet-login/home
hxxps://sites.google[.]com/gateiolog.com/gateiologin/home
hxxps://sites.google[.]com/kucoin-log.com/kucoinlogini/home
hxxps://sites.google[.]com/kucoinguide.com/kucoinlogin/
hxxps://sites.google[.]com/kucoinguide.com/kucoinloginsignin/
hxxps://sites.google[.]com/metaipmasklogin.com/metamasklogin/home
hxxps://sites.google[.]com/metamamk.com/metamask-log-in/home
hxxps://sites.google[.]com/metamask-ios.com/metamask-extensions/home
hxxps://sites.google[.]com/metamask-ios.com/metamask-login/home
hxxps://sites.google[.]com/metamask-ios.com/metamaskextension/home
hxxps://sites.google[.]com/metamask-ios.com/metamaskloginin/home
hxxps://sites.google[.]com/metamask-ios.com/metamasksigninn/home
hxxps://sites.google[.]com/metamask-log.com/metamask-login/home
hxxps://sites.google[.]com/metamask-log.com/metamask-signin/home
hxxps://sites.google[.]com/metamask-log.com/metamasklogin/home
hxxps://sites.google[.]com/metamask-log.com/metamasksignin/home
hxxps://sites.google[.]com/metamaskexts.com/metamasklogin/home
hxxps://sites.google[.]com/metamaskexts.com/metamaskloginn/home
hxxps://sites.google[.]com/metamaskios.com/metamask-login/home
hxxps://sites.google[.]com/metamaskios.com/metamasksignin/home
hxxps://sites.google[.]com/metamaskios.com/metamaskwallet/home
hxxps://sites.google[.]com/metanimasklogin.com/metamasklogin/home
hxxps://sites.google[.]com/metanimasklogin.com/metamasksignin/home
hxxps://sites.google[.]com/metmasklogin.com/metamask-extension/home
hxxps://sites.google[.]com/metmasklogin.com/metamask-login/home
hxxps://sites.google[.]com/metmasklogin.com/metamaskio-wallet/home
hxxps://sites.google[.]com/metmsk-logi.com/metamasksignin/home
hxxps://sites.google[.]com/meutmask-log.com/metamaskwallet/home/
hxxps://sites.google[.]com/mynewcoins.com/metamasklogin/home
hxxps://sites.google[.]com/myprowallets.com/metamask-extension/home
hxxps://sites.google[.]com/usacoinlogin.com/metamasksignin/home/
hxxps://sites.google[.]com/view/coinbasewallett/home
hxxps://sites.google[.]com/view/gemini-login-usa/
hxxps://sites.google[.]com/view/gemini-login-usa/home
hxxps://sites.google[.]com/view/geminiexchangee/
hxxps://sites.google[.]com/view/geminiwallet/
hxxps://sites.google[.]com/view/metamask-extention/home
hxxps://sites.google[.]com/view/metamaskloginwallet
hxxps://sites.google[.]com/view/metamaskwalletloginus/
hxxps://sites.google[.]com/view/metamaskwallt/home
Second stage URLs
hxxps://caerytos-log.azurewebsites[.]net/
hxxps://cetryeyptos-log.azurewebsites[.]net/
hxxps://coainasbe-log.azurewebsites[.]net/
hxxps://coianasbe-wkalle.azurewebsites[.]net/
hxxps://coinasnbe-walle.azurewebsites[.]net/
hxxps://coinnbass-log.azurewebsites[.]net/
hxxps://crytpeios-log.azurewebsites[.]net/
hxxps://gemnminin-log.azurewebsites[.]net/
hxxps://krakaken-log.azurewebsites[.]net/
hxxps://maataamaask.azurewebsites[.]net/
hxxps://mamametamask-walle.azurewebsites[.]net/
hxxps://metidismakskklo.azurewebsites[.]net/
hxxps://mmetatasamask-log.azurewebsites[.]net/
hxxps://mmetatsamasks-walle.azurewebsites[.]net/




 Zurück
Zurück
















 Den Blog lesen
Den Blog lesen