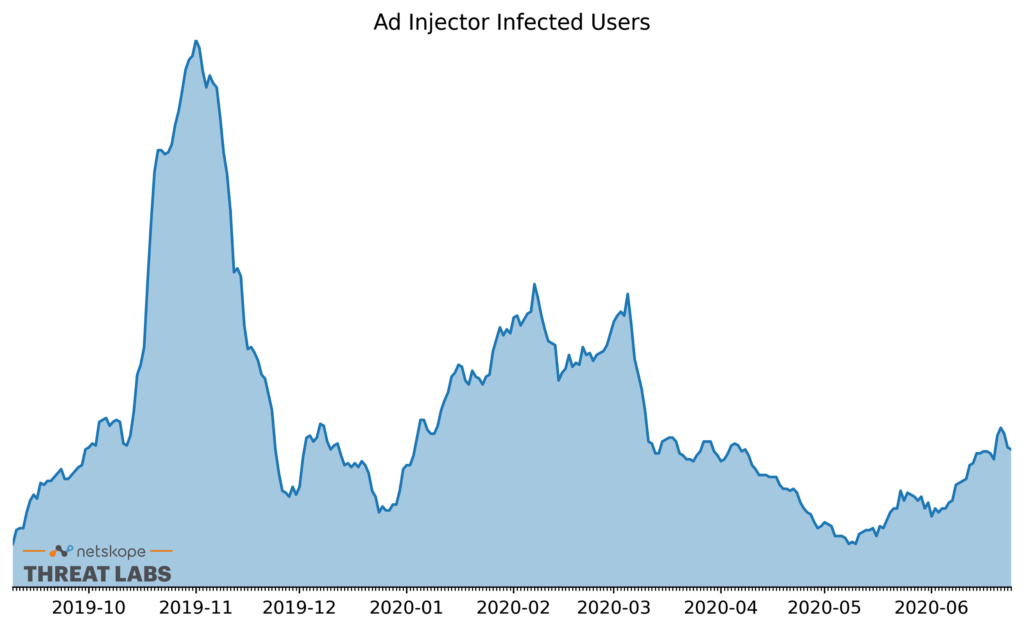
Previously Netskope Threat Labs published a blog post about a Lnkr ad injector campaign launched using Google Chrome extensions. As Figure 1 illustrates, the number of Lnkr infections spiked dramatically in November 2019 and again in the spring of 2020, when Brian Krebs uncovered information about the source of the infected Chrome extensions. Today, we’re revisiting the Lnkr adware because:
- We have observed a rise in the number of Lnkr infections starting in May and continuing through June, indicating that newly infected Chrome extensions are appearing again.
- We have identified new web pages that were infected with Lnkr and identified the root cause to be a form of fanout, where an infected user infects a webpage when they edit it.
- We have identified 155 new domains hosting Lnkr that are associated with these new extensions and infected websites.
Infected users
The latest rise of infected users began in early May and continued through the month of June. As was the case in the previous two spikes, only Google Chrome users were affected. The infected extensions inject trackers and ads into the user’s web traffic, including online banking portals and intranet sites, giving the attackers detailed visibility into an infected user’s browsing habits.
The infection occurs when a user installs an infected extension. This might happen when:
- The user installs a new extension that is infected.
- The user updates to the latest version of an already installed extension that is newly infected.
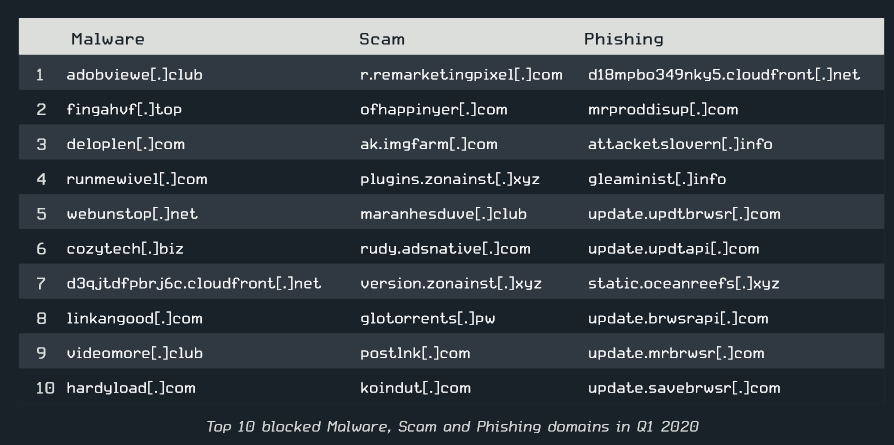
We also have evidence from external sources supporting that Lnkr infections are widespread. ESET’s Q1 Report lists hardyload[.]com as one of the top 10 malicious blocked domains. This Lnkr domain ranks second in our list, behind only brounelink[.]com. An excerpt of this report is shown in Figure 2.
We also found brounelink[.]com to be the primary domain used in a widespread infection affecting school students. A Google Chrome support post stated, “Students were unable to access shared documents, watch embedded videos, save work in Google drive, and use Google Hangouts. Once allow listed, www.brounelink[.]com in Trend, all the problems went away.” An excerpt of the article is shown in Figure 3.
![Screenshot of Google Chrome help section article about brounelink[.]com](https://www.netskope.com/wp-content/uploads/2020/07/Lnkr-3.png)
Infected web pages
Netskope Threat Labs have identified more than 1,500 web pages that were infected with Lnkr. There are several ways a website might become infected with Lnkr. For example, the owner of the website might deliberately include the code for monetization, or a developer might accidentally infect the website if they themselves are infected. We found multiple examples of websites that were accidentally infected. In one example, a Marketo webpage was accidentally infected when an infected user edited the webpage and the infected Chrome Extension injected the Lnkr code into the HTML they were editing. They saved their changes, which included the Lnkr code, and published it to the website.
These accidental infections follow a similar pattern to our October 2019 post showing how GitHub Pages sites became infected with Ramnit. In the Ramnit case, the culprit was a file infector that infected the files in a GitHub repository. In the Lnkr case, an infected Chrome extension injected the Lnkr script into web pages that were being edited in the browser.
This ad’s for us
Netskope Threat Labs analyzed more than 1000 Lnkr ad injector scripts, including the scripts hosted on the 155 new domains we identified, and found that they all referenced the same domain: thisadsfor[.]us, as shown in Figure 4.
![Optional advertisements message template containing the domain thisadsfor[.]us](https://www.netskope.com/wp-content/uploads/2020/07/Lnkr-4-1024x363.png)
As described in Brian Krebs’s article, the domain thisadsfor[.]us is registered to Frank Medison (Email – frankomedison1020@gmail[.]com), who has also been tied to similar websites related to dodgy toolbars, add ons, and extensions. The references to thisadsfor[.]us in all of the new domains we identified indicates that this is either the work of the same actor or a new actor that has borrowed from the earlier work without making any significant changes.
Conclusion
The development of the Lnkr campaign is active and still ongoing. Netskope Threat Labs recommends you:
- Audit the extensions installed in your Chrome browser at chrome://extensions and remove any affected extensions
- Search your website for the domains listed at the end of the post and remove any scripts or links that reference them.
- Block the domains listed at the end of this post.
Indicators of compromise
Updated set of Lnkr Urls( Including the 155 new domains)
thisadsfor[.]us
plusdroop[.]net
coolpagecup[.]com
cooljorrd[.]com
platewolf[.]com
nightroi[.]com
bugdepromo[.]com
tracksmall[.]com
jaramyouk[.]org
marryjoy[.]net
ideafrank[.]com
rayanplug[.]xyz
signagetop[.]org
transmapp[.]com
magictraps[.]com
protrois[.]com
craftprimes[.]com
cilkonlay[.]com
pagescr[.]cool
jobsaddy[.]xyz
mikkymax[.]com
donewrork[.]org
cozytech[.]biz
minisrclink[.]cool
clipsold[.]com
criticalltech[.]com
vildlonger[.]com
dashvintage[.]biz
toolsmagick[.]com
linkpowerapp[.]com
extnetcool[.]com
darkflags[.]net
crisgrey[.]com
peterjonny[.]com
mobiclean[.]xyz
linkojager[.]org
higedev[.]cool
cloffext[.]com
flexylincks[.]com
miniklixk[.]org
protesidenext[.]com
outsource[.]cool
golinkapp[.]com
remaideout[.]com
oilcloze[.]com
roxlock[.]com
dimagesrc[.]com
brounelink[.]com
autroliner[.]com
klarittyjoy[.]com
cdn-mxpnl[.]com
www[.]billyjons[.]net
modelwork[.]org
madelinkapp[.]com
jonysource[.]com
qwentyextext[.]com
loidjony[.]net
miragecall[.]com
browfileext[.]com
nextextlink[.]com
ciclonrox[.]com
proghage[.]com
peterfire[.]net
mabydick[.]com
cybertransfer[.]net
returnweb[.]org
srctestlink[.]com
linksource[.]cool
acountscr[.]cool
tribedone[.]org
licupexthis[.]com
yourrecovery[.]net
genyhome[.]com
clicksapp[.]net
drivemute[.]net
loudfire[.]net
miragework[.]com
linkproext[.]com
cdnclntr[.]com
lowffdompro[.]com
rockypride[.]com
amptylogick[.]com
petercontry[.]net
vibeclimate[.]com
appslinker[.]net
meextffcon[.]com
contendevff[.]com
printapplink[.]com
smackbolt[.]com
artistickplan[.]com
blinkloide[.]com
hardyload[.]com
www[.]proudflex[.]org
blancfox[.]com
milkpload[.]net
loudsjack[.]com
biglinksrc[.]cool
manextdev[.]com
slickfluide[.]com
polinaryapp[.]com
clarklordy[.]com
wellgolink[.]com
cannotjojeph[.]com
proudflex[.]org
serenityart[.]biz
highmakeext[.]com
permissnew[.]com
mirextpro[.]com
addonfiles[.]com
fourgekross[.]com
lokimtogo[.]xyz
ratexchange[.]net
poligloteapp[.]org
lisegreen[.]biz
cardinaldata[.]net
fileryjon[.]com
caplinkff[.]com
statsrc[.]cool
lifebounce[.]net
proxdevcool[.]com
goldapps[.]org
nowexttype[.]com
dataanalytic[.]biz
shopstorys[.]com
mirakay[.]biz
cloneclicks[.]com
makesure[.]biz
screensrc[.]com
colextidapp[.]com
kellysford[.]com
jsfuel[.]com
simonzody[.]com
srclinkapp[.]biz
brigstoneapp[.]com
foundfax[.]com
www[.]killssource[.]com
linkangood[.]com
joshtower[.]net
treestarys[.]com
taiwanbike[.]com[.]tw
newholynursinghome[.]com
billyjons[.]net
hugoclose[.]com
interjoan[.]com
cosmeticsrc[.]com
lonelyfix[.]com
scrextdow[.]com
dogsamily[.]net
blinkjork[.]com
qualityprimes[.]com
singlactive[.]com
loungesrc[.]net
storysrc[.]com
madeapplink[.]com
windinspext[.]com
icontent[.]us
massehight[.]com
soursejone[.]com
richhamond[.]com
dowlextff[.]com
plankjock[.]com
promlinkdev[.]com
killssource[.]com
clickwoob[.]net
joyshoul[.]com
makesource[.]cool
sysfileff[.]com
worldmodel[.]biz
domtopro[.]com
gullyclock[.]com
jaretsummer[.]com
amytroy[.]com
practiclick[.]xyz
ffpanelext[.]com
untsorce[.]cool
trableflick[.]com
comtakelink[.]xyz
psatgeremy[.]com
singtraff[.]cool
jonyplus[.]com
worksrc[.]cool
frimeduble[.]com
programdiag[.]com
evenffext[.]com
countmake[.]cool
mikkiload[.]com
zoudlogick[.]net
qalitygigant[.]com
extcoolff[.]com
giraslide[.]com
jackyhillty[.]net
workdevapp[.]com
crisdomson[.]com
rasenalong[.]com
browlinkdev[.]xyz
appmakedev[.]xyz
groproext[.]com
countsource[.]cool
profflinkgo[.]com
domclickext[.]xyz
extcuptool[.]com
scrlink[.]cool
cloudesky[.]com
meginaflight[.]com
pingclock[.]net
datapro[.]website
onlinekey[.]biz
netstats[.]space
joyglasses[.]net
mixappdev[.]com
devappstor[.]com
sourcelog[.]cool
actextdev[.]com
primalsuper[.]com
clogitec[.]com
cdnanalytics[.]xyz
extnotecat[.]com
trafficpage[.]cool
statcounter[.]biz
promclickapp[.]biz
clicksource[.]cool
1018433480[.]rsc[.]cdn77[.]org
1480876790[.]rsc[.]cdn77[.]org
blickkeily[.]com
captiontxt[.]com
clonyjohn[.]com
closemike[.]com
dataprovider[.]website
dismagic[.]com
jonyclose[.]com
larickway[.]com
leaderdigital[.]org
longsrc[.]com
masyclick[.]com
pagevalidation[.]space
prilapptime[.]com
renetteapp[.]com
shortyclubs[.]com
skillapp[.]net
sourcebig[.]cool
die-rheinische-affaire[.]de
thrillingos[.]herokuapp[.]com/mozilla/best-ytb-down/content/analytics
s3[.]amazonaws[.]com/cashe-js
s3[.]amazonaws[.]com/js-cache
s3[.]amazonaws[.]com/js-static
s3[.]amazonaws[.]com/jscache
s3[.]amazonaws[.]com/jsfile
s3[.]amazonaws[.]com/jscriptcdn
www[.]klarittyjoy[.]com
pslinker[.]net
transfer[.]net
pmakedev[.]xyz
ribedone[.]org
ngtraff[.]cool
arklordy[.]com
kyhillty[.]net
flinkdev[.]com
clickext[.]xyz
rcuplink[.]xyz
tapplink[.]com
onewrork[.]org
lytics[.]tools
linksrc[.]cool
ftprimes[.]com
eeforced[.]com
licksapp[.]net
fflinkgo[.]com
aplinkff[.]com
rldmodel[.]biz
urcelog[.]cool
olinkapp[.]com
enityart[.]biz
ounelink[.]com
senalong[.]com
powerapp[.]com
ider[.]group
oungesrc[.]net




 Zurück
Zurück
















 Den Blog lesen
Den Blog lesen