Introduction
The AWS root account can do anything in your account, and it follows that it should be protected with tight security controls:
- Do not use the root account
- Do not create API/access keys in the root account
- Enable MFA on the root account
However, while analyzing root account configuration and use in 915 accounts from 153 production environments over four months, we found that:
- Root account use is widespread. Root account use is common and widespread, occurring in 143 (16%) accounts and in 65 (43%) organizations.
- Root account use occurs repeatedly. 50% of accounts were repeat offenders who accounted for over 86% of the total 517 uses.
- Large environments are exposed: Over 29% of the accounts are medium-sized with 50 to 250 total assets, and 15% are large with over 250 assets.
- Root API keys exist in 54 (6%) accounts.
- Root API keys are used for 13% of all root access.
- Root API keys are not rotated with 96% having keys older than 90 days.
- There is nearly a 2 out of 3 chance that a root access is not protected by MFA.
We will now look at the data in more detail to understand more of the nuances and learnings, including the tradeoffs and the presumed “why’s” behind the problems. We’ll then cover what concrete steps can be taken to reduce the probability and impact of root account compromise.
Root Account Usage
We started with the goal of assessing how much or how often the root account was used in real-world production environments. An average of 915 root accounts were analyzed over a four-month period from September 13, 2020, to January 24, 2021. Credential report data was analyzed using LastLoginTime for the root account. To minimize the skew from newly provisioned accounts (where we would expect the root account to be used for initial configuration), we ignored any root accounts that were created within the past 30 days of the date of audit.
The number of accounts that used the root account at least once in the week preceding the time of audit is shown in the following table:
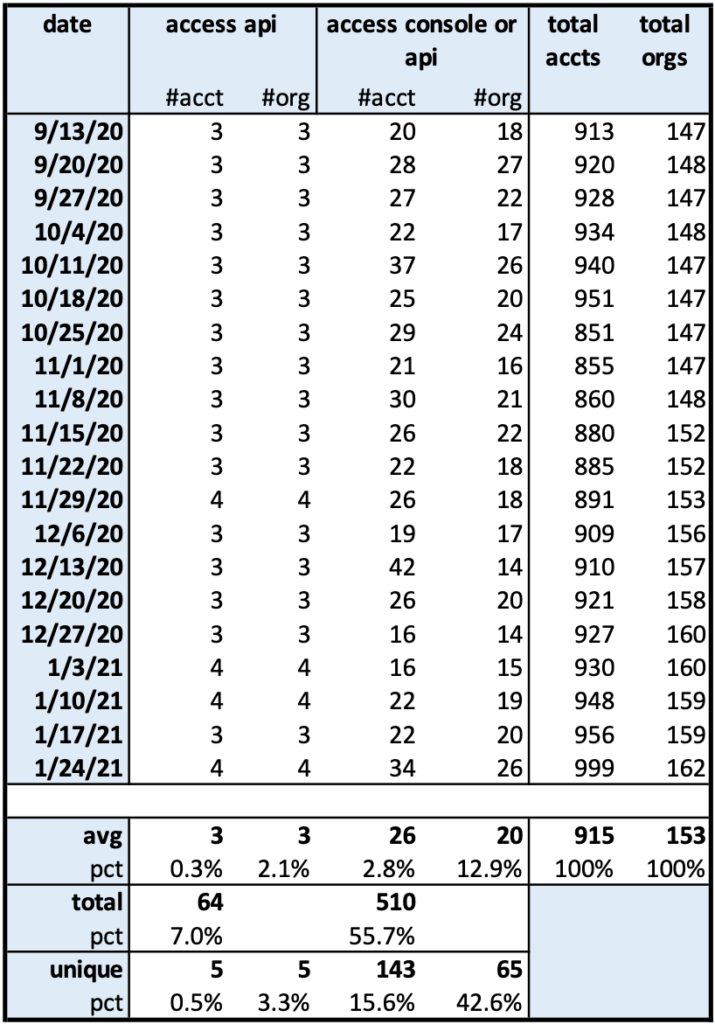
Some key observations:
Root accounts are being used regularly: On a weekly basis, an average of 26 accounts (2.8% of the total 915 accounts) from an average of 20 organizations (13% of the total 153 organizations) used the root account at least once during that week. Since we expect this to be zero, this should be concerning:
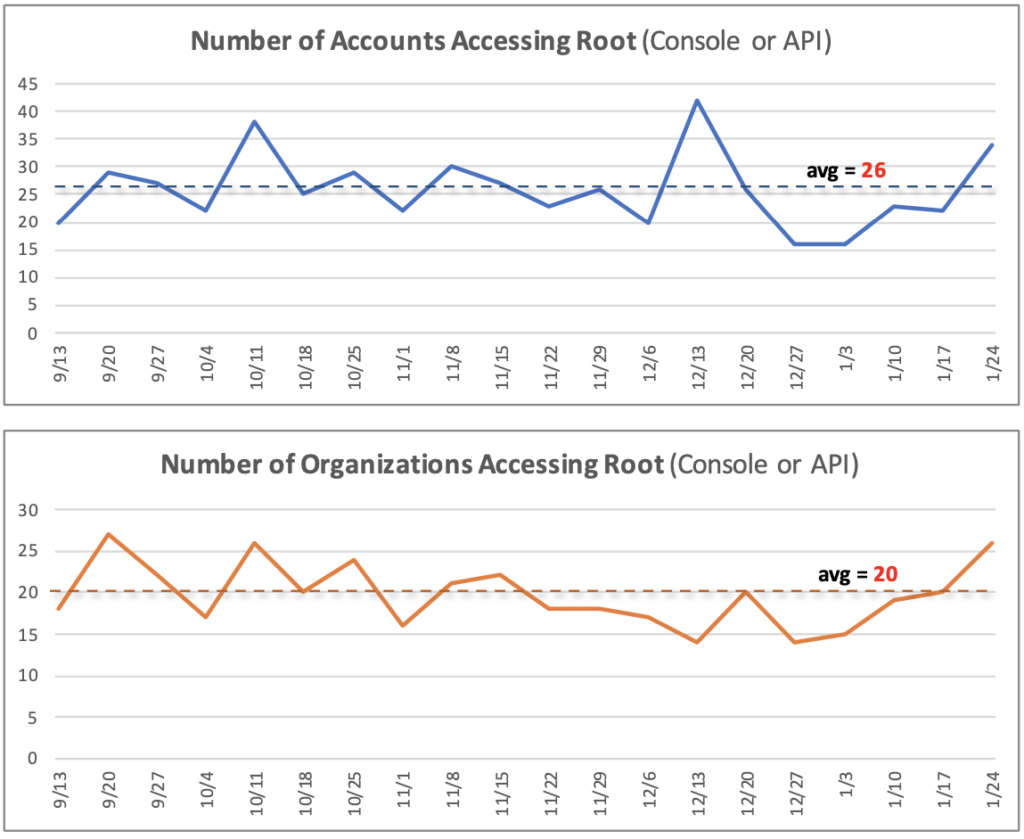
Widespread use: It is not all the same 26 accounts or 20 organizations that repeat this behavior week-to-week. Over the four-month period, 143 accounts (~17% of 915 accounts) and 65 organizations (43% of 153 orgs) accessed the root account at least 517 times. 517 is a high enough number (when it should be zero), that it warrants serious attention. We also had broad participation within organizations (43% or almost 1 out of 2) as well as accounts (16% or 1 out of 6 accounts):
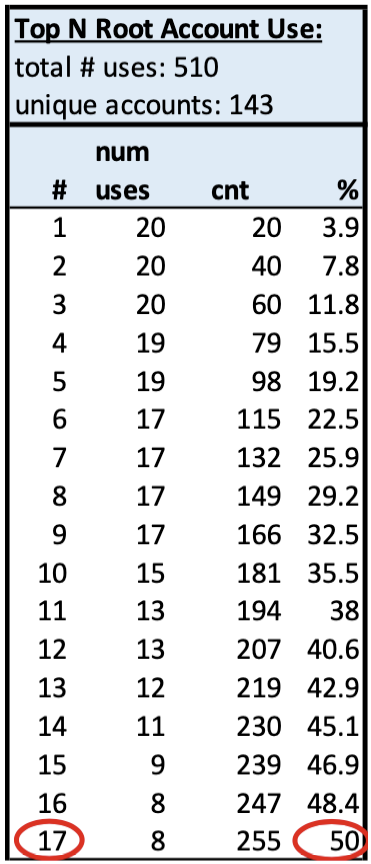
Repeated Use: The 510 total uses occurred in 143 accounts in 65 organizations, so on average each offending account used root over three times. Although there is widespread account participation, there is still some concentration of use. The top 17 (12%) accounts contributed half of the root account usage:
Potential Impact
Root account compromise provides complete control to your account, but the risk can be abstract, especially if organizations believe there is little value regarding the account. However, at a minimum, attackers can abuse your account resources to crypto mine or stage attacks on others, causing significant costs and potential liability.
To characterize the impact better, we further analyzed the assets contained within each account that had root account activity. The goal is to highlight whether the accounts had small, medium, or large value, with value being defined simply as the total count of the following assets: IAM users, databases (RDS instances), buckets, EC2 instances, and CloudTrail instances with: small having 0 to 49 total assets, medium having 50-250 assets, and large having more than 250 assets.
Taking the total root account use on a weekly basis and adding this breakdown of accounts results in:
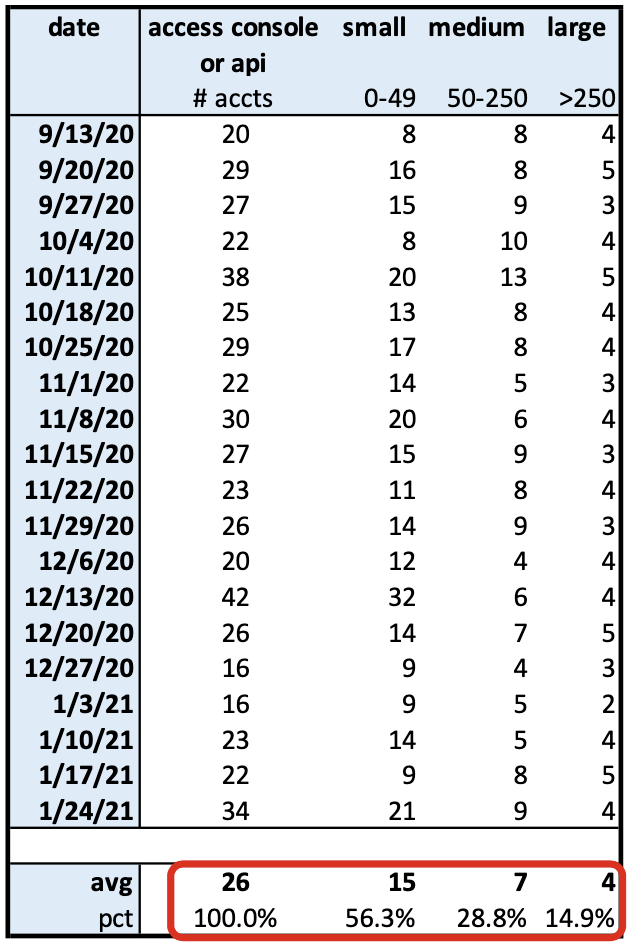
We see that out of the weekly average of 26 root account accesses, 56% of the accounts are small (<50 objects), 29% are medium-sized (50-250), and 15% are large (>250).
This provides a little more color on the type of accounts that would be impacted if the root account were compromised.
Mitigations
API/Access Keys
Root accounts should not have access keys and they shouldn’t be used. Stealing access keys is a common attack vector, whether those keys are stolen from client machines or accidentally committed into source repositories.
Let’s look take another look at API key usage in our data set:
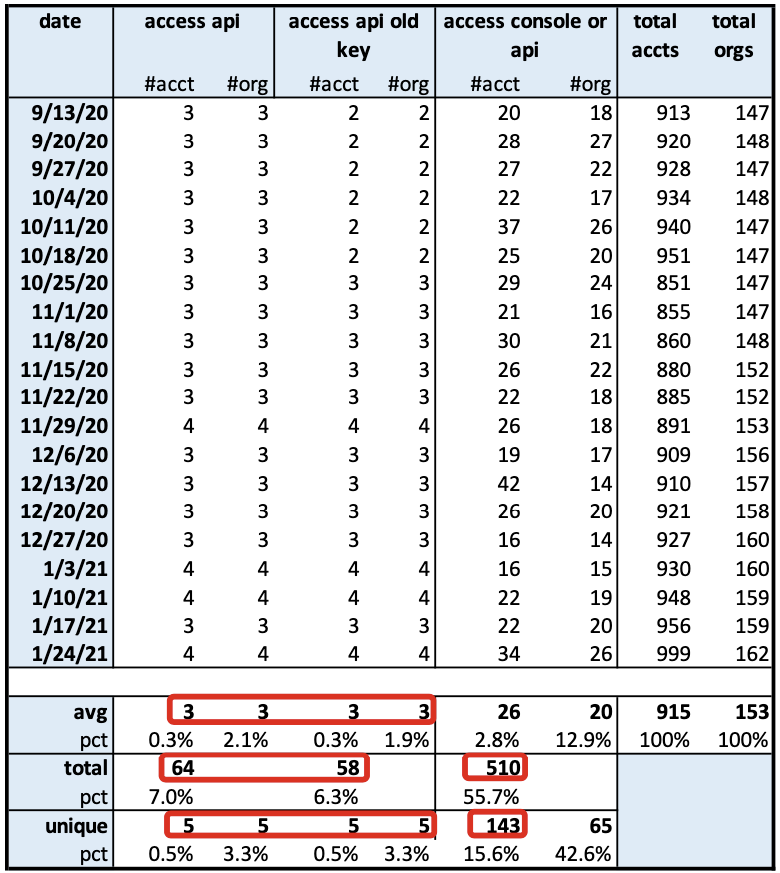
There are several items to note:
- Root API keys are being used. Root API key usage occurs in 13% (64/510) of all root account use over the four-month time period.
- The root API keys are old (>90d since the last rotation) approximately 90% of the time over the four-month period (58/64). Having long or no periods for rotation of keys goes against key management best practices.
We also need to assess the configuration of API keys, even if they have not been used, since the existence of any root API key is a risk for potential compromise:
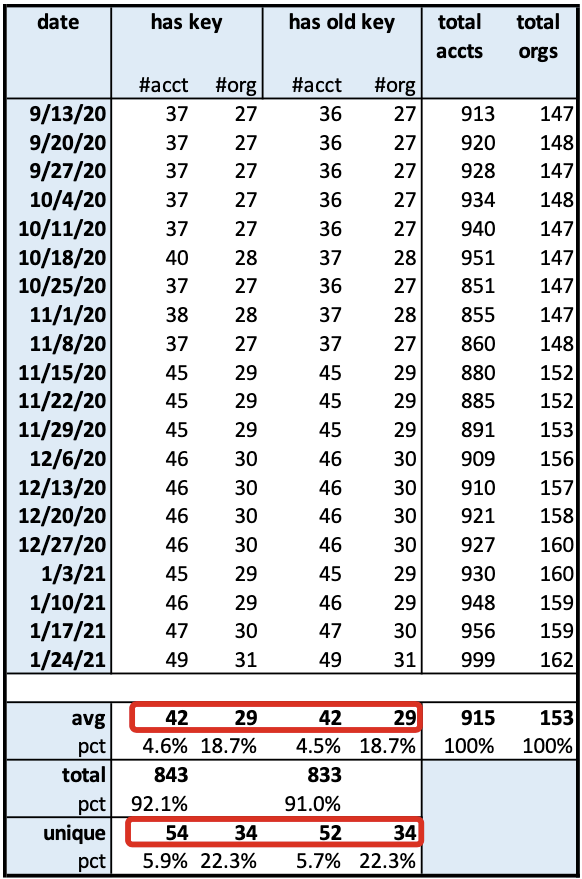
- On average, 6% (54/915) of root accounts have API keys, which is concerning due to the increased chance for compromise.
- These root accounts with keys exist in 22% (34/153) of the organizations, which is a broad penetration within the 153 organizations.
- Organizations are using root API keys but do not rotate them—96% (52/54) of accounts have old API keys in the 34 organizations using access keys.
MFA
MFA should be enabled for the ”root” account, preferably using a hardware key rather than a virtual device. However, we can see from the data, that many accounts and organizations still are not using MFA:
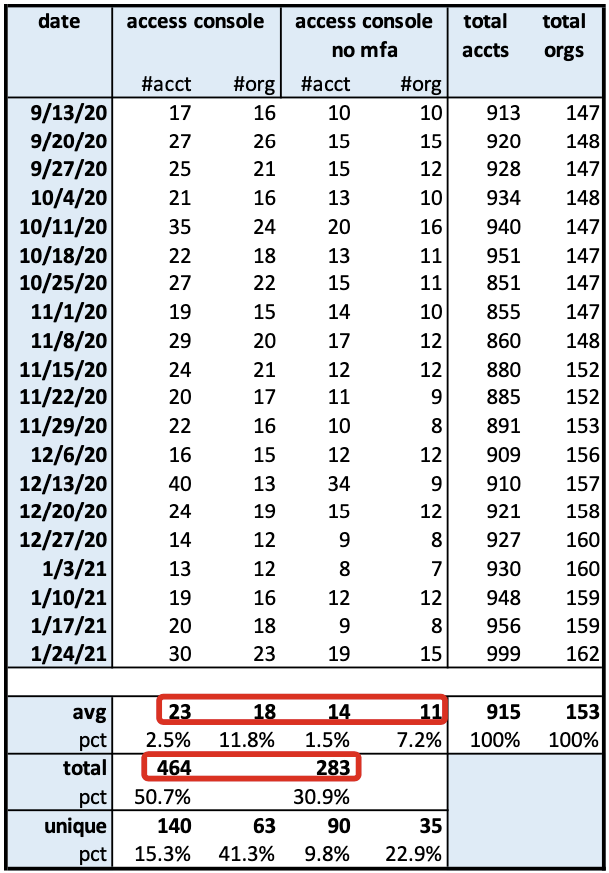
Since MFA does not apply to API key usage, we only look at console access. Over the four-month period, of the 464 Console accesses with root accounts, 283 of those account accesses did not have MFA enabled or 61% of the time, consistent with the weekly averages. There is nearly a 2 out of 3 chance that a root access is not protected by MFA.
This activity or lack of MFA is not concentrated in a smaller set of organizations since 56% (35/63) organizations used root accounts without MFA enabled.
Other Mitigations
Other common mitigations of credential compromise, such as IAM policies or IP deny lists, do not apply, as IAM policies of any kind cannot be applied to the root account. Similarly, a custom password policy also does not apply to the root account.
Addressing the Problem
How can organizations address the above problems and improve their root account security?
- Immediately delete or deactivate any root account API keys and provision an API key under a specific IAM user with appropriate privileges.
- Enable MFA on the root account, immediately with a virtual device (software) but preferably with a hardware key. The root account should not be used often, and the number of people who are authorized to use it should be very small, so turning on MFA should not require a lot of overhead.
- Work with users so that the root account is not used at all or only in very specific exceptions. Provision as needed more limited IAM administrator accounts or roles.
- Implement regular and frequent automated auditing of the root account configuration in all accounts by checking the credential report.
- Detect root account use by detecting CloudTrail log events (e.g. using a SIEM).
For step #4, fortunately, the CIS Benchmark for AWS provide good detail and guidance, and you could even implement your own checks using API/CLI scripts or by using Netskope Public Cloud Security.
As an example, one can generate and download the credential report using the CLI, converting from base64 to ascii:
$ aws iam generate-credential-report
$ aws iam get-credential-report --query 'Content' --output text | base64 --decode > aws_cred_report.csvThen some basic shell scripting could be used to check the .csv file for the <root_account> configuration line, extract the appropriate column containing the setting of interest and compare it against the expected.
Netskope’s Public Cloud Security platform also has built-in rules implementing the CIS Benchmark for AWS, as well as provides a language to implement custom checks:
| CIS Control | Netskope Configuration Check Rule |
|---|---|
| CIS 1.4: Ensure no 'root' account access keys exist | IAMUser where RootUser eq True should not have AccessKey with [ Active eq True ] |
| CIS 1.5: Ensure MFA is enabled for the 'root' account | IAMUser where RootUser eq True should have MFAActive eq true |
| CIS 1.7: Avoid the use of the 'root' account | IAMUser where RootUser eq True should not have Password . LastUsedTime isLaterThan ( -1, "days" ) |
Conclusion
Use and misuse of the AWS root account is occurring in the real-world at higher than expected rates, widespread among many organizations and accounts, and without common use of mitigating controls such as MFA, deletion of API access keys, and/or key rotation.
The risk is high due to the super admin privileges of the root account, with the impact at a minimum including:
- financial loss (e.g., use of your environment for crypto mining),
- liability (e.g., use of your environment for illegal acts like malware delivery, storage of stolen property, hosted cyber attacks)
- direct loss of data
- adverse impact on users and your business
Organizations should review their own usage and configuration to ensure that they are following best practices:
- the root account should not be used for regular tasks
- root API keys should not be created
- MFA should be enabled for the root account
The CIS Foundation Benchmark for AWS provides specific guidance on auditing and remediating your configurations in these areas.
Additionally, Netskope’s Public Cloud Security platform also can automate configuration checking of your AWS environment, implementing both standards, such as the CIS benchmarks, as well as custom configuration checks.
Dataset and Methodology
Time Period: Data was sampled/analyzed at weekly intervals from September 13, 2020, until January 24, 2021.
Source: The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
Scope: The data included an average of 153 organizations, 915 accounts, and 15,660 IAM user accounts. Month to month fluctuations in these counts are expected due to product usage and normal AWS provisioning changes.
Data Entities: The data was composed of AWS entities including IAM users, credential report, password policy, buckets, databases, CloudTrail, and compute instances.
Logic: The analysis followed the logic of core root account security checks found in the IAM section of the CIS AWS Foundations Benchmark v1.3:
- CIS 1.7: Avoid the use of the ‘root’ account
- CIS 1.4: Ensure no ‘root’ account access key exists
- CIS 1.5: Ensure MFA is enabled for the ‘root’ account
with a few adjustments for the dataset and methodology:
- CIS recommends looking for a last logged in time within the past 24 hours to determine whether the root account has been used recently. Since our sampling was once a week we looked at root use within the past 7 days prior to the audit date, as that adjusted for the weekly audit time period.
- To reduce possible false positives for root account use, we ignored root account use with new root accounts, i.e., accounts that were created within the past 30 days.
Caveats: The usage numbers very likely undercount the real root account usage because the analysis uses the LastUsedTime timestamp from the AWS credential report, sampled on a weekly basis. This only records the last use, so multiple uses within the same week will count only as one “use.”




 Zurück
Zurück
















 Den Blog lesen
Den Blog lesen