On February 19, 2017, Tavis Ormandy from Google reported an incident relating to Cloudflare dumping un-initialized memory due to visiting, simply put, malformed HTML pages hosted behind the Cloudflare infrastructure. The matter gained importance due to the fact that the same Cloudflare infrastructure is shared across multiple different customers and the information getting leaked can belong to any of Cloudflare’s customers. Few examples of the leaked information cited in the incident report relate to encryption keys, cookies, passwords of users accessing various applications and many other sensitive PII as well as infrastructure related data. This bug has now been termed as Cloudbleed and was mitigated by Cloudflare on 2017-02-18 as detailed in their blog.
The bottomline, this impacts a large number of customers (their websites and applications) hosted by Cloudflare. Any enterprise using applications (e.g. website, web services, mobile apps, etc.) produced by Cloudflare customers up until 2017-02-18 should assume that sensitive data leaked to the Internet. As a first step towards remediation, enterprises MUST change their user credentials such as usernames/passwords used to access applications behind Cloudflare. If enterprises are hosting their own applications behind Cloudflare it is a MUST to change any infrastructure related data such as encryption keys, etc. Refer to the last section to see full set of recommendations. The Netskope Threat Research Labs team performed an in-depth analysis of the impact of Cloudbleed bug on cloud applications and the risk it poses for enterprises. This blog details this information.
Impact on Cloud Apps
Netskope Threat Research Labs has identified more than 980 cloud apps being hosted behind Cloudflare infrastructure. Amongst the identified cloud apps, the distribution as per the enterprise readiness is shown in Figure 1 below.
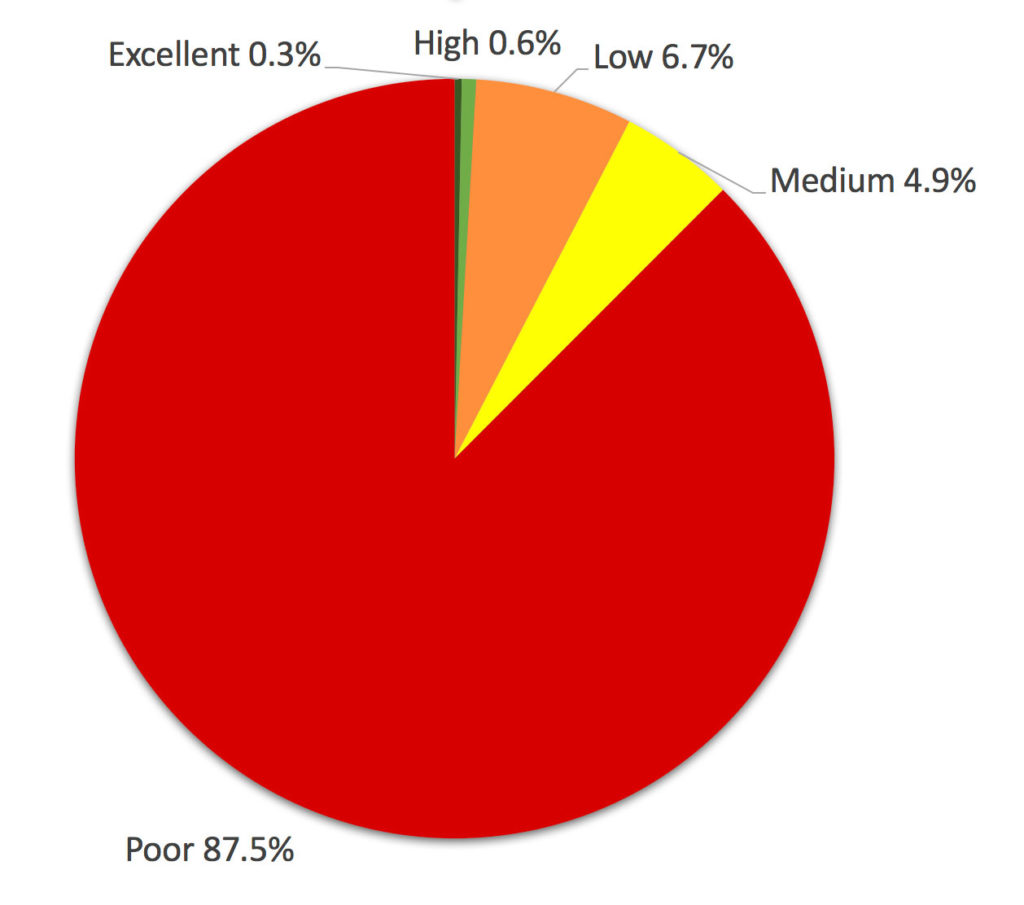
Figure 1. The percentage distribution of Enterprise Readiness ratings of the apps hosted behind Cloudflare.
Out of more than 100 excellent enterprise ready rated cloud apps, only three apps had some services hosted behind Cloudflare infrastructure while more than 800 apps with a poor enterprise readiness rating, hosted some of their services behind Cloudflare infrastructure.
Between the excellent rated cloud apps and highly rated cloud apps, we found nine cloud apps had some services hosted behind Cloudflare infrastructure. There were more than 60% of customers across different verticals who had more than one user using these apps. Based on the types of services these nine cloud apps had running behind the Cloudflare infrastructure, there is a greater probability of enterprise sensitive data leakage.
If this is extended further to all of the 980+ cloud apps, any enterprise could find significant number of users who might have accessed the applications behind Cloudflare infrastructure. If you are a Netskope customers our customer success team is actively reaching out to provide additional details specific to your enterprise.
Assessing Enterprise Risk
Understand the data involved
By now, you’re likely asking, “How are we affected by this?” Assessing the damage can be a long, drawn out process. But with the right tools, from a Cloud Access Security Broker, your IT team can make decisions quickly. Netskope Discovery can turn what would have been a costly fact-finding exercise into a 30 second actionable report.
There is a correlation between how enterprise-ready a cloud app is and the potential damage from new vulnerabilities. Enterprise-readiness signifies how secure a cloud app is with enterprise data. The Netskope Cloud Confidence Index rates an app’s enterprise readiness based on 40+ attributes over eight business categories.
Protect the data at risk
Cloudbleed is different from most other vulnerabilities since there is a sole infrastructure vendor which has caused this. Vulnerabilities like Heartbleed are more of a characteristic of an underlying technology design or implementation (TLS). The patch and remediation was executed within hours at that single point compared to the few days it took to ramp down the services that were vulnerable to Heartbleed. While this can be seen as a mitigating factor, the fact that this vendor serves millions of requests and is a key player in the Internet has a multiplier effect. There is no definitive method to figure out what data has been lost.
The absence of application specific information about data loss should prompt CISOs and their teams to look for ways to raise the overall protection levels of the cloud for the entire enterprise. There are several methods through which organizations can provide step-up authentication for applications that have enterprise data — Netskope is one such vendor. This is to ensure that employees who might have lost data due to Cloudbleed, including passwords that are being reused, will have one more level of authentication and effectively prevent misuse of the stolen passwords. CISOs and security teams should also look for tools that track compromised credentials so that they can be alerted when a user’s credentials are part of a known breach, even with a non-corporate account.
If the Cloudbleed vulnerability were to be exploited for any of the sanctioned applications of an enterprise, it is highly likely that the stolen credentials will be used for corporate data theft. Look for tools that allow you to quickly identify applications that do not provide SSO and native multi-factor authentication.
Evolved cloud security for tomorrow’s issues
Whether it is vendor-specific vulnerabilities like Cloudbleed or technology specific ones like HeartBleed, the next vulnerability is never too far. While the specifics vary, the generally accepted criteria for cloud governance that includes visibility, data protection and fine-grained control will always hold good. CASBs are naturally aligned to these requirements and should rank high in your considerations.
Recommendations
To recap, protect your enterprise from this vulnerability and others that may occur in the future by taking the following actions:
- Use the Netskope CCI to identify the apps that were vulnerable because of Cloudbleed
- Change your user credentials for those apps as well as other critical infrastructure services
- Use the Netskope CCI to identify the apps that support single sign-on (SSO) and multi-factor authentication (MFA) and ensure that SSO and MFA are enabled for those apps
- Take advantage of the Netskope Cloud Risk Assessment (CRA) to assess your Risk




 Back
Back















 Read the blog
Read the blog