The internet is simultaneously the most important productivity tool for a business and its biggest liability due to the wide range of security threats it exposes them to. While it is possible to protect against some web-browsing threats using old techniques like blocking known risky domains, these precautions don’t guard against other exploitations. So, how do organizations protect users, data, and systems from the ever-increasing threats on the web?
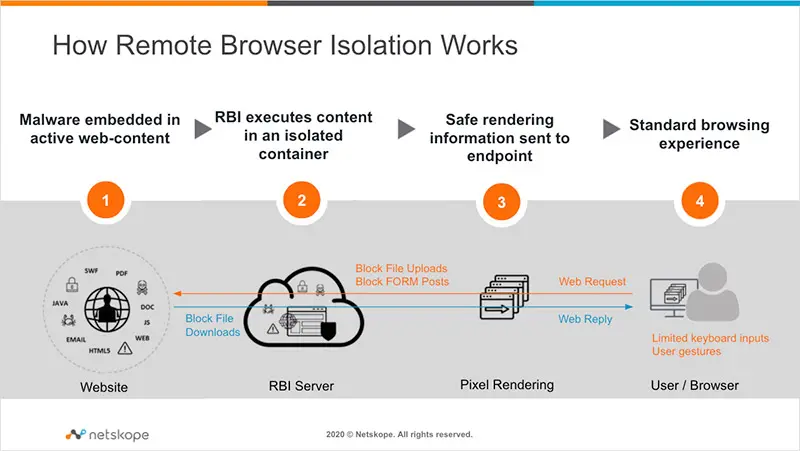
Remote browser isolation (RBI), also known as web isolation, is a security measure that separates users’ devices from the act of internet browsing by hosting and running all browsing activity in a remote cloud-based container. This act of sandboxing internet browsing protects data, devices, and networks from all kinds of threats originating from infected website code, including:
- Web-borne malware and ransomware
- Zero-day exploits
- Browser vulnerabilities, such as plug-ins
- Infected file downloads
- Malicious web links in phishing emails
- And many others





 Back
Back