Considering the forensic-level attention to data residency that was paid in the early days of cloud, it’s interesting how little regard is now given to the matter. Explaining the many pitfalls of certain data residency challenges to fellow CISOs (and key stakeholders) and why real-time visualisations of data flow matter, is often an interesting exercise. The emergence of GDPR at around the same time that cloud adoption was accelerating gave organisations a clear imperative to understand data flows, but as we all became familiar with cloud I think many found a misplaced assurance with the challenge of data residency and/or data sovereignty. Today’s global disruption is bringing us back to this challenge; as an example, I have had a significant number of conversations in the past 10 days on the matter of data being transferred to or originating from certain jurisdictions.
So what exactly are we talking about when we reference data flows? Put simply, it’s understanding that just because the cloud service provider you have contracted is a US-based company—and your team is all working from Germany—that does not mean that your data flows will only involve the US and Germany. For regulatory reasons, as well as internal data protection reasons, IT and information security teams need to identify the additional countries where data is stored, processed, archived, and understand by whom. In the world of cloud data processors and sub-processors, organisations need to understand and apply context, especially during times of geopolitical unrest.
An example:
The image below shows data flows from/to user location on the left, from/to cloud applications and website locations on the right. Throughout, you can see where policies have triggered and have been proactively applied. These policies range from user education (e.g. “[Web] policy coaching users about non-business site use”) to blocking (e.g. “[RProxy OneDrive] block Downloads to Unmanaged Device from OneDrive”).
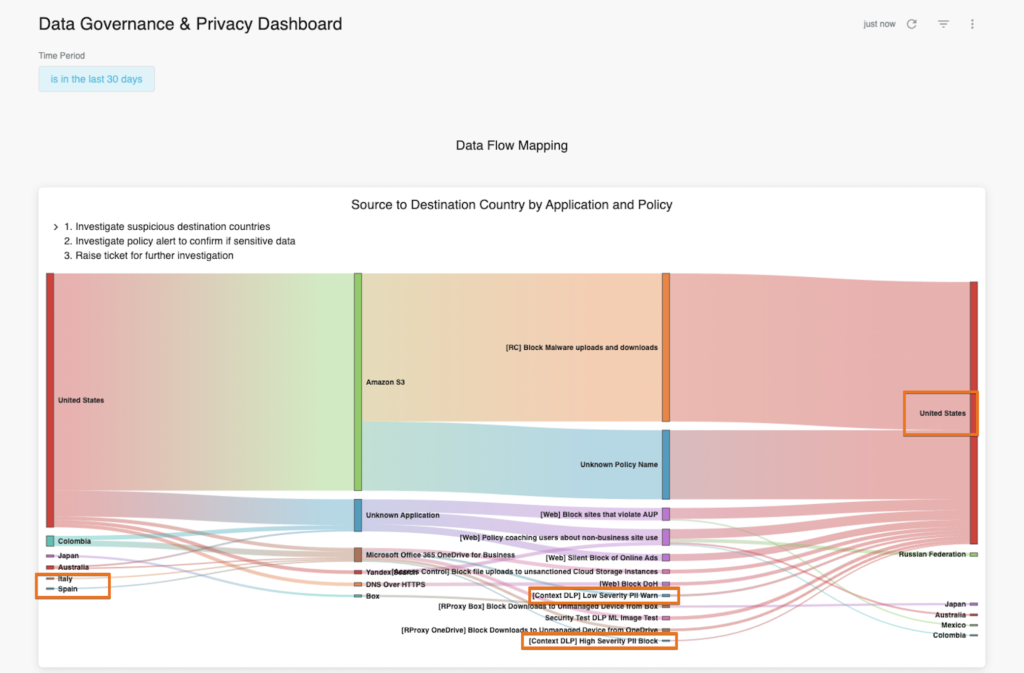
From this visualisation, you can also observe that malware is attempting to propagate from AWS S3 instances in the US. You will also note that web and cloud traffic and data is routing to other parts of the world (Japan, Mexico, Colombia, Australia, and the Russian Federation). This contextual intelligence is incredibly important for both information security professionals and data protection officers, and where it is deemed to be problematic, enforcement and education policies can be applied.
Because Netskope’s approach to security is cloud-native and data-centric, Netskope’s security capabilities allow Netskope customers to have a clear picture of the jurisdiction their data touches. And of course, Netskope customers can do this for both managed cloud applications and shadow IT (or business-led cloud applications).
So whether your marketing team is using WeTransfer to share files with agency partners, or your sales team is collaborating with channel partners across multiple continents using authorised M365 tools, Netskope customers can identify where that data is travelling from/to. This insight is proving incredibly useful for customers who want automated, up-to-date, and real-time data flow mapping.
Our Community team has provided some recommendations for customers and partners on where to find this information within the Netskope Advanced Analytics dashboard.




 戻る
戻る
















 ブログを読む
ブログを読む