How to measure risk
Ask any security professional how to effectively measure risk and many will give a simple answer…
Risk = Likelihood x Impact
Perhaps some professionals will take it a step further and include a variable to include a weighting on the asset value (that is calculated separately to impact value)…
Risk = Likelihood x Impact x Asset Value
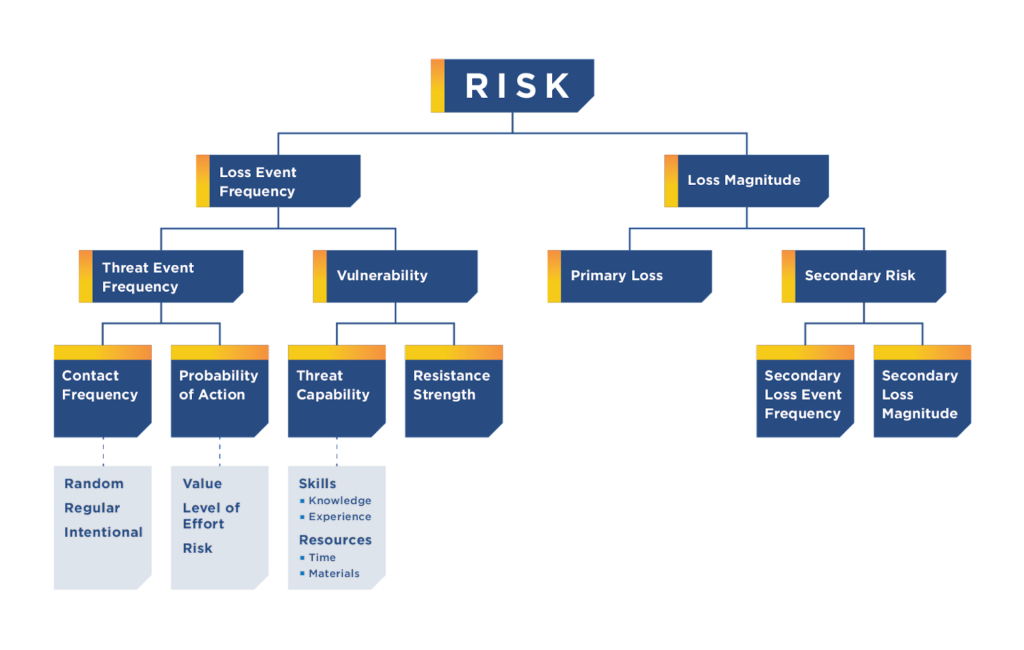
A few might go further and cite FAIR, a well established framework on quantitative risk management, that expands to include many additional variables.
Masters of risk will perhaps even talk about running risk model calculations and risk simulations using empirical data to further understand risk and create more accurate predictions of risk.
However, while any form of risk identification, assessment, and acceptance mitigation / transfer is better than none, still too few organisations have applied this concept to assessing cloud risk. So what is the reasoning for this—is it that cloud risk management is the cloud service providers (CSP) job?…is it that assessing cloud risk is not important?…or is it that assessing cloud risk is too complex? The answer to the above questions typically is No, No, and Perhaps.
How to measure cloud risk
Assessing cloud risk starts by identifying the cloud services your organisation currently uses. With 79% of employees in organisations actively using cloud apps to upload, share, or store data, and the average organisation using more than 1,500 distinct cloud apps each month the need to identify the cloud app and the type of data being processed or stored is key to understanding the risk.
The following six risk variables are common in assessing cloud risks and should form part of the cloud risk management process:
Vendor/Third-party Risk
Identify the vendor and understand their service agreement, terms, and conditions, as well as your organisation’s association and reliance on them and their providers.
Data Risk
Identify the category of data being uploaded, shared, or stored. If the data is personal data, financial data, or intellectual property, ensure that the appropriate controls are in place to protect the data and limit exposure to avoid both data loss risk and regulatory risk. Managing a clear inventory of which vendor is processing what data is critical (and is a regulatory requirement for many types of data).
Technology Risk
Understand the technology, the architecture, and the shared responsibility model. Identify who is responsible for addressing certain risks, such as ensuring correct implementation and configuration of the technology to ensure the service is secure.
Operational Risk
Manage operational risk across the supply chain. In the event of a security incident or an outage, ensure operational risk is managed and communicated. Ensure the provider has a robust incident response programme and can effectively contact their customers in the event of a security incident or a service outage.
Financial Risk
Identify any new financial risks that may affect the operation or even termination of a cloud service the organisation relies on. Cloud service providers can vary wildly in terms of their financial stability.
Geolocation Risk
Identify where the service is operating from and if the organisation is meeting its regulatory and compliance requirements. In addition, with ongoing geopolitical conflict and tensions, these might bring new risks over time. It is critical to understand if you need to move or relocate data to other locations.
Start with WHY, know HOW, then WHAT
In summary, using cloud services will necessarily add additional risk measurements to your risk management programme. With the advancement of many cloud services and the ability to appropriately manage these risks, cloud service providers are making it possible for organisations to effectively tailor and manage these cloud risks. Whatever your level of maturity in risk management, use the approach of Simon Sinek: start with asking WHY measuring cloud risk is important, then HOW to measure for your organisation, and finally WHAT to measure…




 Back
Back 
















 ブログを読む
ブログを読む