We’d like to think of our coworkers as trusted team members, collaborating on a shared mission to make positive contributions to the well being of the company. For the most part, this is true, but we must also recognize that our coworkers are individuals who may conduct themselves in ways that are detrimental to the company. Sometimes these actions are not malicious in nature, such as a person who, in the course of their work day, might accidentally share a file in a manner that lets the entire world see the contents. Other times an actor is perfectly aware that they are acting against the organization’s interests, with disregard to the consequences of their actions.
Understanding the difference between insider threat and insider risk
What makes insider threats like this particularly difficult for security teams to stop stems from the fact that insiders already have access to applications and data. It’s a matter of the user’s actions and their unseen motivations that cause the insider to become a threat. Limiting access to only the resources that are necessary to a person’s role is a good first step, but organizations struggle to define what the right policies are. How many different types of users are there? What actions could they possibly take? What circumstances raise concerns? There are an endless number of permutations to consider.
How can you defend yourself against what seems to be an insurmountable problem? The answer is to change your perspective. Instead of looking at the threats the user could possibly pose (of which there are many), start by mitigating risk. Why start with risk? You can identify the data you must protect, and establish controls that make the permutations of threats manageable.
Addressing insider risk
At Netskope, we address insider rIsk using protections across three key technologies: data protection, contextual risk-based access controls, and analytics, as capabilities of Netskope Intelligent SSE. This blend of protection helps organizations take control over the risk that insiders pose in a manner which no combination of point solutions could possibly do. That’s because with Netskope Intelligent SSE our protections work together, with single-pass policy enforcement and the capabilities to visualize, understand, and control insider risk.
Risk reduction starts with Netskope Data Protection. Organizations immediately shave off risk by taking control of what happens to their data, and the circumstances by which specific actions should be permitted to happen.
Next, by applying risk-adjusted access controls and behavioral analytics, you can start to build policies that adapt to behavioral changes, using a combination of heuristics and AI/ML models. The ability to apply such context helps organizations build protections that account for the risk situation in contextual decisions, rather than relying purely on allow/block decisions that are either too permissive or too restrictive.
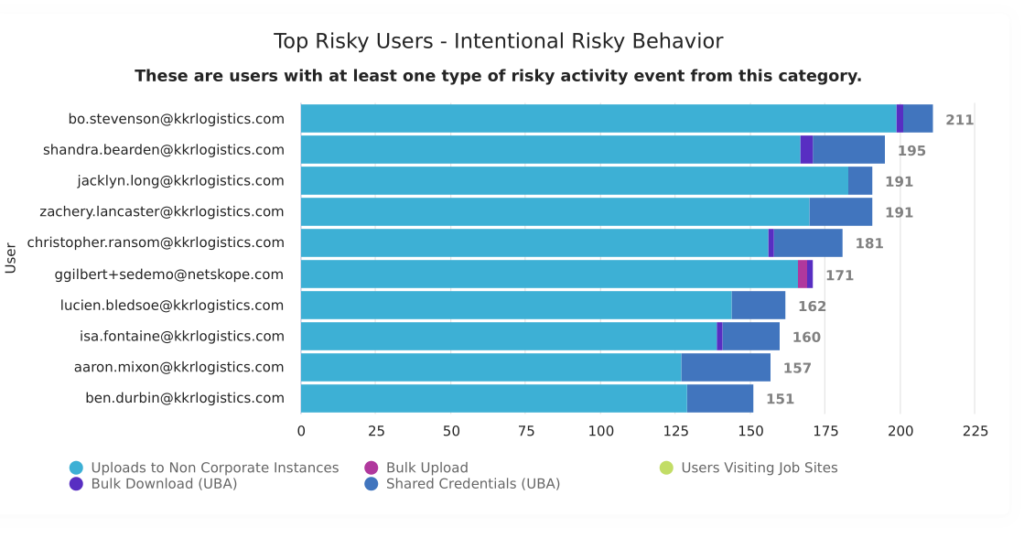
Finally, with Netskope Advanced Analytics the organization’s user, application, and data movement activity is automatically logged for analysis. Organizations can go directly to the Insider Threat dashboard within the library to get views that surface risky activity in order to help security teams prioritize which users require further scrutiny. These views can be further investigated, either with pre-built or custom dashboards tailored to address your specific investigation’s needs.
Coaching the accidental insider
It’s understandable that many organizations place an emphasis on the intentionally malicious insider, as such users are taking active steps to cause harm. However, it’s also notable that Netskope can help organizations address the accidental insider, where a user may not have known their actions are detrimental.
By using inline coaching and real-time controls, organizations can help individuals avoid mistakes from becoming a breach. For example, many security teams do not know what to do with medium risk activity, given both the volume of incidents and the relatively lower severity compared to a high risk alert. These are frequently caused by users who are inadvertently doing the wrong thing, such as using an unmanaged application with company data when there are better alternatives that IT supports. By applying coaching policies, the organization can choose to guide the user to make better decisions by being told what the correct behavior is supposed to be. These measures help users become better digital citizens and go beyond the conventional practices of either blocking or ignoring activity that could be better handled if the user knew what to do instead.
There’s a lot to take in on how Netskope can help tackle the security challenges that your organization faces. To get a better understanding of how Netskope addresses the problem of insider risk and see how key metrics are exposed through Advanced Analytics, check out this video overview of the Advanced Analytics insider risk dashboard.




 戻る
戻る 















 ブログを読む
ブログを読む