Summary
In January 2022, Netskope analyzed a destructive malware named WhisperGate, wiping files and corrupting disks during the aftermath of a geopolitical conflict in Ukraine. On February 24, the conflict escalated with Russian attacks in Ukraine, followed by a series of DDoS attacks against Ukrainian websites.
On February 24, 2022, a new malware called HermeticWiper was found in hundreds of computers in Ukraine. HermeticWiper corrupts disks on infected systems, similar to WhisperGate. However, HermeticWiper is a more complex malware, implementing techniques to avoid detection. In this blog post, we will analyze this new threat to demonstrate how it works.
Analysis
We have analyzed two different HermeticWiper files, both digitally signed with a certificate issued to Hermetica Digital Ltd and valid until April 14, 2022.
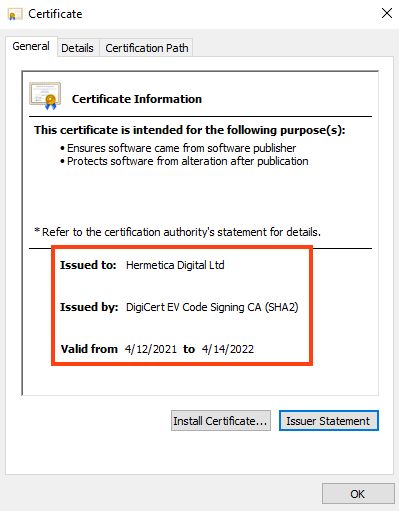
Although this information can be easily changed, the first file was apparently compiled on December 28, 2021, while the second one was compiled on February 23, 2022.
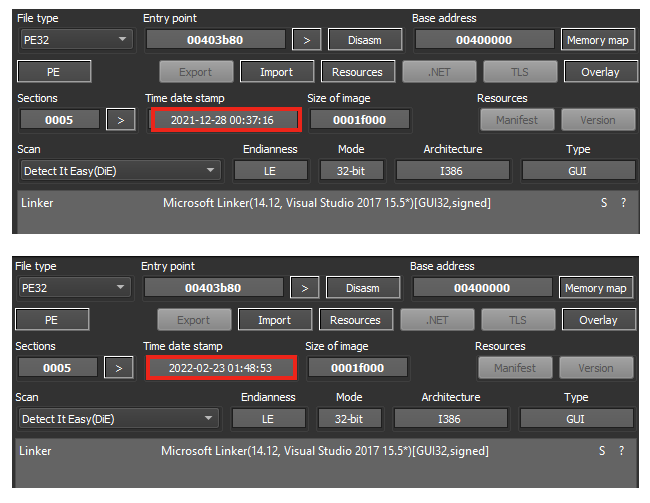
The two samples are 99% equal. The only difference is a small addition to the newer file within the main function.
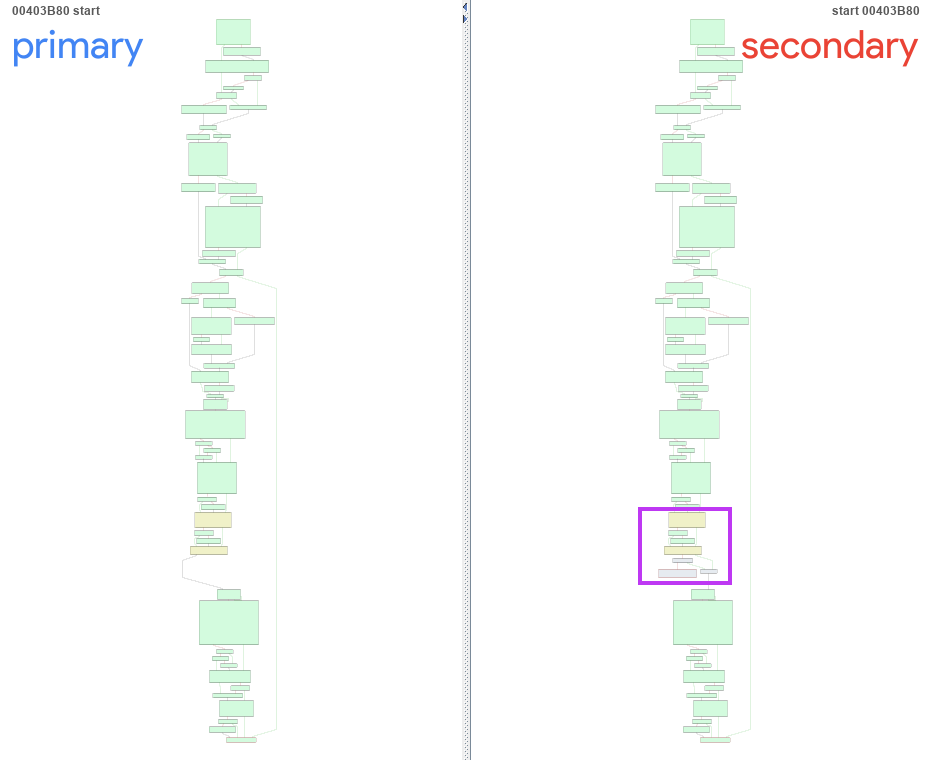
Looking at the code that was added, it’s checking the presence of “C:\Windows\SYSVOL”, which is a folder that exists in every domain controller, containing public files shared across the domain. If the folder exists, the code skips additional steps that reference common folders such as “Desktop” and “AppData”, which we show later in this analysis.
Once running, HermeticWiper adjusts its privileges by enabling SeBackupPrivilege and SeShutdownPrivilege tokens via AdjustTokenPrivileges API. With both enabled tokens, the malware can access any file in the system, bypassing the access control list (ACL), and can shut down the system.
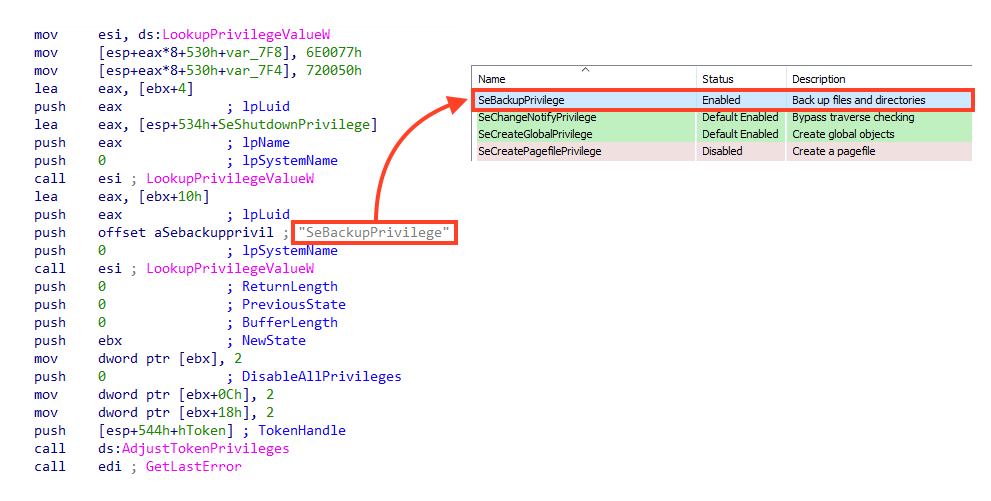
Then, it dynamically resolves three APIs from “kernel32.dll” using a common technique via GetModuleHandle and GetProcAddress.
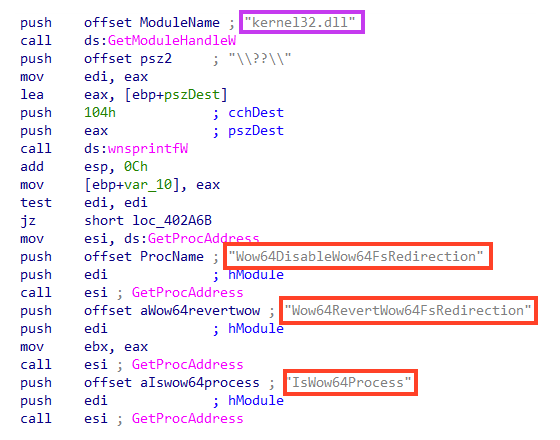
These APIs are then used to verify whether the process is 32- or 64-bit. Also, HermeticWiper checks the OS version as a condition to load a compressed non-malicious driver named “empntdrv.sys” from its resources, which belongs to the EaseUS software, abused throughout the wiping process to access drives and partition information.
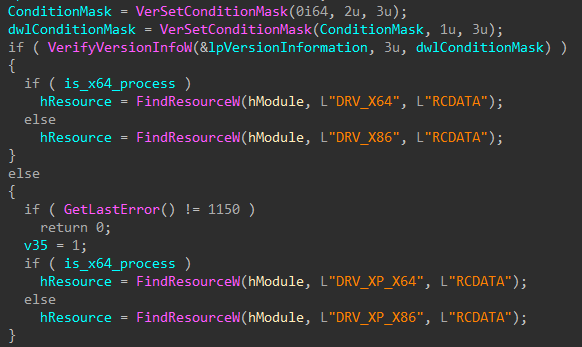
The usage of drivers was already observed in other wiping malware, such as Shamoon. HermeticWiper is likely using this driver to stay under the radar, as many operations are executed through DeviceIoControl, avoiding other API calls.
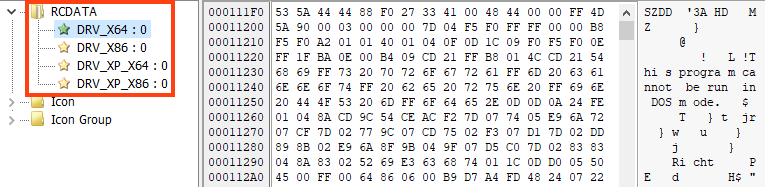
After loading the resource, the malware disables crash dumps by changing the registry key value of “CrashDumpEnabled” to 0. Then, it drops the abused driver to “C:\Windows\System32\Drivers\<random_2_characters>dr.sys”.
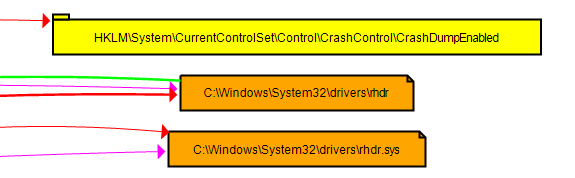
It also creates a pipe that will be used to interact with the abused driver.
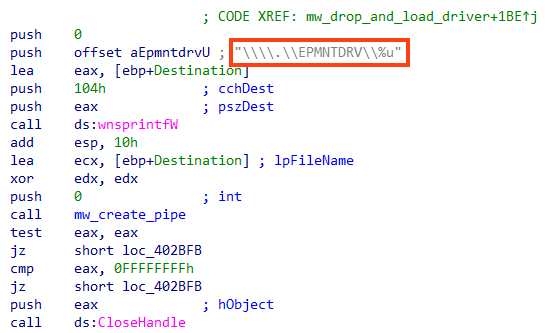
To prevent any file from being restored, it also disables the volume shadow copy service.
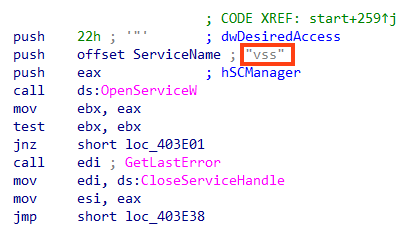
HermeticWiper then starts enumerating physical drives in the system in a loop from 0 to 100. For each one of them, the abused driver is called to get the device number via DeviceIoControl API, and the drive’s Master Boot Record (MBR) is corrupted through a bit swapping routine.
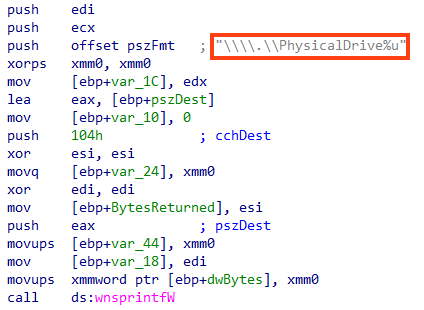
This is quite different from WhisperGate, which replaces the MBR stub with a code that runs when the machine is rebooted. Although this should be enough to prevent the OS from being loaded, the code also enumerates the partitions for the physical drives, differentiating between NTFS and FAT. For NTFS, HermeticWiper parses the Master File Table (MFT) before corrupting files.
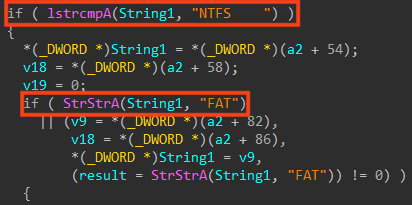
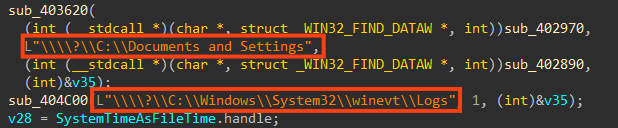
Further code is referencing user folders such as “Desktop” and “My Documents”, as well as the Windows event logs folder. This routine is skipped in the newest binary we analyzed, if the folder “C:\Windows\SYSVOL” exists, as we mentioned earlier.
Conclusion
HermeticWiper is a destructive malware that emerged during attacks in Ukraine, similar to WhisperGate. Netskope Threat Labs is continuously monitoring cyberthreats related to the conflict in Ukraine.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Threat Protection
- Win32.Ransomware.KillDisk
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Malware.Detect.By.Sandbox indicates a sample that was detected by our cloud sandbox
IOCs
A full list of IOCs and a Yara rule can be found in our GitHub repository.




 戻る
戻る
















 ブログを読む
ブログを読む