Last week researchers discovered an OpenSSL vulnerability (CVE-2014-0224) that could result in a man-in-the-middle attack exploiting some versions of OpenSSL. Called the OpenSSL Change Cipher Spec (CCS) Injection, this vulnerability requires that both a server and a user’s client be vulnerable and enables an attacker to modify traffic from the server and client and subsequently decrypt the entire communication between the server and client.
All client versions are vulnerable. Affected server versions include OpenSSL 0.9.8, 1.0.0, and 1.0.1. It is recommended that all users of OpenSSL servers 1.0.1 or earlier upgrade their systems as a precaution:
- OpenSSL 0.9.8 SSL/TLS users (client and/or server) should upgrade to 0.9.8za
- OpenSSL 1.0.0 SSL/TLS users (client and/or server) should upgrade to 1.0.0m
- OpenSSL 1.0.1 SSL/TLS users (client and/or server) should upgrade to 1.0.1h
Netskope has been researching the enterprise cloud apps in our Cloud Confidence Index database for this vulnerability starting with 4,837 apps across 44,572 domains, and found that, as of June 6, 2014, there were 1,832 cloud apps vulnerable. On June 11, there were 1,732; on June 13, there were 1,656; and on June 16, there were 1,416.
As of today, there are 3,421 apps that are not vulnerable.
Enterprise Cloud Apps That Remain Vulnerable
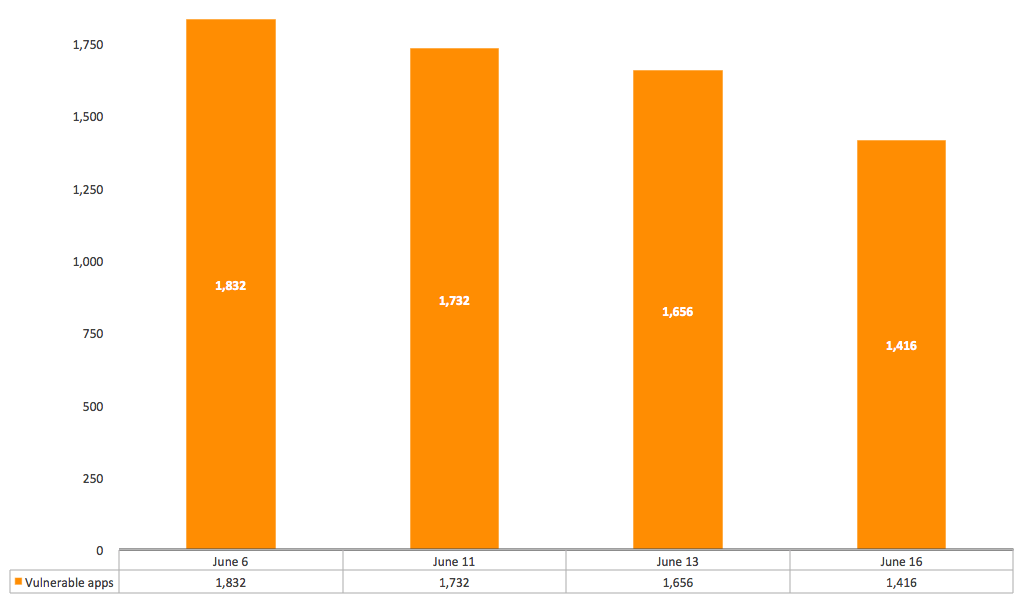
What Should You Do?
To protect yourself from this and future vulnerabilities, you should:
- Discover all of the cloud apps running in your environment.
- Measure the apps’ enterprise-readiness against an objective yardstick (CSA’s Cloud Controls Matrix is a great starting point, and there are also vendors, including Netskope, who perform this service free of charge).
- Compare the discovered apps against the list of remaining vulnerable apps and take steps to curtail usage or introduce countermeasures.
- Beyond the apps affected by the OpenSSL CCS Injection vulnerability, review all of the low-scoring apps and determine whether they’re business-critical.
- For non-critical apps, help users migrate to more appropriate apps.
- For critical apps, work with your app vendor to introduce enterprise capabilities and develop a plan to remediate vulnerabilities.
- Adopt a process to continuously discover and gain visibility into the cloud apps in your environment, including the unsanctioned ones, as they change frequently.
Learn more
Netskope Researcher, Ravi Balupari, has recorded a Netskope Movie Line Monday about the OpenSSL CCS Injection Vulnerability and what it means to you. Watch it here.
We’ll be updating this status every three days or as major developments occur, and counting down the apps that remain vulnerable. Please check back with us or reach out to us at [email protected] if you have a specific question about this OpenSSL CCS Injection Vulnerability or any cloud security topic.




 Zurück
Zurück















 Den Blog lesen
Den Blog lesen